What Is an Internal Firewall?
An internal firewall is a network security solution that manages and controls the internal traffic within an organization's network.
It acts as a barrier between different segments of the internal network, enforcing security policies to prevent unauthorized access and potential threats from moving laterally. Internal firewalls focus on the interactions between internal devices to strengthen security against internal breaches.
How Does an Internal Firewall Work?
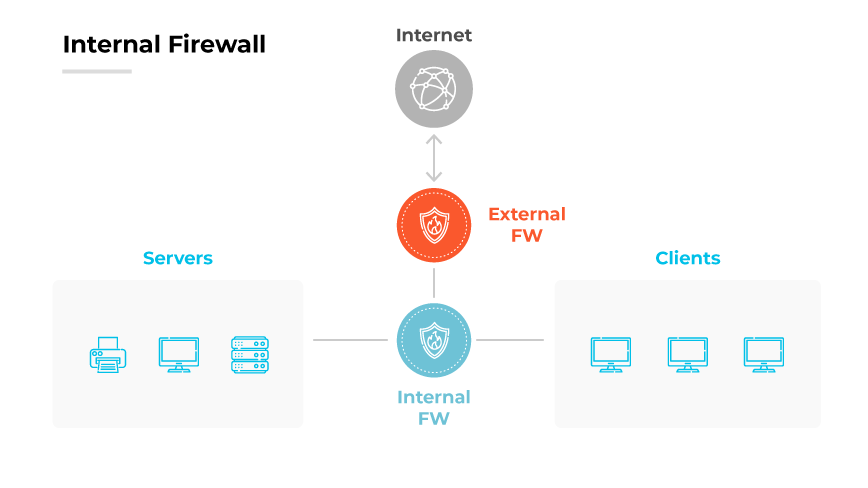
An internal firewall is a type of network firewall that operates by regulating the traffic within an organization's internal network based on security policies. It operates at strategic points within the network infrastructure to monitor and filter the traffic that flows between different segments.
The internal firewall enforces rules which define allowed communications. These rules govern each segment or zone. Rule configuration typically defaults to a deny all stance, allowing only expressly permitted traffic, which upholds the principle of least privilege. The core function of an internal firewall is to apply these security policies to control access and prevent unauthorized data transfers.
An internal firewall often uses packet filtering as one of its primary mechanisms to control traffic between different segments of an organization’s network. It does so by inspecting each data packet's header, which contains information like source and destination IP addresses, port numbers, and the transport protocol. The firewall applies rules to allow or block these packets based on the organization’s security policies. The firewall is also responsible for creating network traffic logs, which aid in the analysis of patterns that might signify a security threat.
To enhance network security, internal firewalls can use advanced techniques like deep packet inspection (DPI) to analyze the payload of packets for signs of malware or policy violations. This enables identification and blocking of sophisticated threats that might otherwise remain undetected.
With the implementation of Zero Trust security models, internal firewalls continuously validate the trustworthiness of devices and users within the network, never assuming any traffic or endpoints to be inherently secure.
Types of Firewalls Defined and Explained
Why Are Internal Firewalls Important?
Internal firewalls are particularly vital in complex networks because they provide fine grained control over traffic to minimize the impact of attacks that have penetrated the network perimeter. They manage east-west traffic, providing protection against threats that have bypassed the external firewall. This layer helps to limit the scope of an attack, confining potential breaches to smaller network segments, which mitigates the overall impact.
Internal firewalls represent a shift from traditional perimeter based security models toward a more segmented, granular approach. Traditional firewall technologies typically monitor and control ingress and egress traffic at the network's boundary, guarding against external threats. Legacy firewalls offer limited protection against internal threats which have already compromised the perimeter.
In enterprises, internal firewalls serve to enforce access policies and prevent unauthorized data flows between different organizational units. They are especially critical as networks grow in complexity, with more endpoints and diverse cloud environments. By monitoring internal traffic, these firewalls can identify and respond to malicious activities initiated from within the network, reducing the risk of data breaches and insider threats.
Internal firewalls support the Zero Trust security model, which operates on the premise that no user or system should be trusted by default, even if they are within the network perimeter. This approach is increasingly important in a landscape where threats are constantly evolving, and the traditional network perimeter is no longer sufficient as the sole line of defense.
Internal Firewall vs. External Firewall
An internal firewall differs from an external firewall, also known as a perimeter firewall, primarily in the orientation and scope of protection. An external firewall sits at the network's edge to monitor and block potentially harmful traffic from outside entities. It acts as the first line of defense, controlling north-south traffic, which consists of data packets moving in and out of the network. The focus is preventing external threats from breaching the network's perimeter.
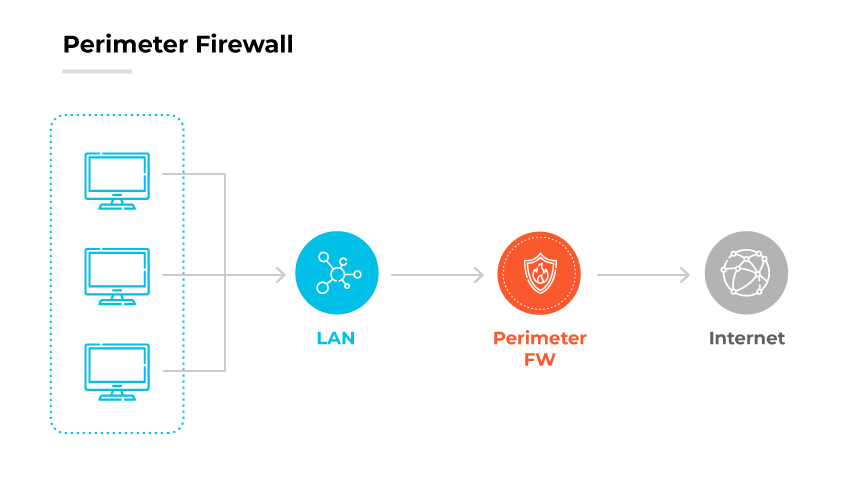
In contrast, an internal firewall scrutinizes traffic moving within the network, known as east-west traffic, which may include data transfers between servers, storage systems, and other internal devices. This traffic does not typically pass through the perimeter defenses, so the internal firewall's role is to secure this internal network space. It operates on the assumption that threats could exist within the network, hence its approach is not solely preventive but also detective, monitoring for unusual patterns or policy violations that could indicate a threat.
While external firewalls may often rely on predefined port and protocol rules to filter traffic, internal firewalls require a more sophisticated approach to identify and manage internal threats. This may involve more advanced techniques such as behavioral analysis and automatic policy adjustments based on a baseline of "known good" behavior. Internal firewalls need to be adept at understanding the normal operational patterns of the enterprise’s network to effectively distinguish and mitigate risks from within.
How to Set Up an Internal Firewall
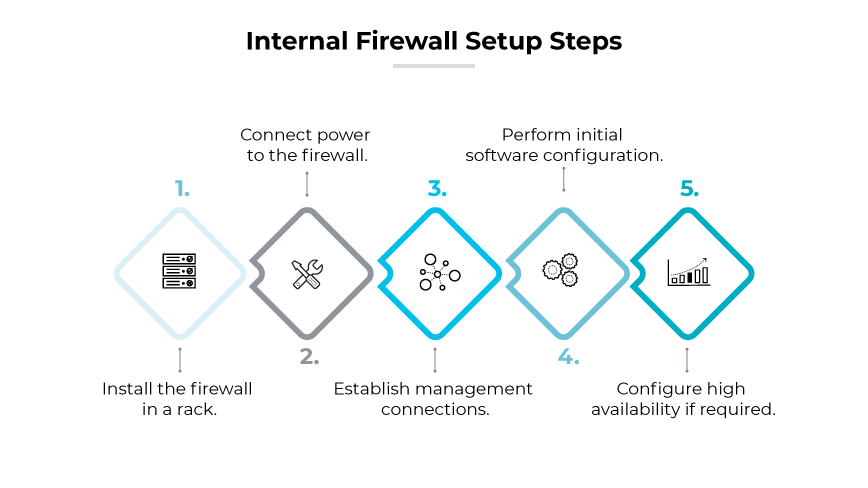
The internal firewall setup process includes installing the hardware in a rack, connecting power, and setting up the initial software configuration.
Installation and configuration steps can vary significantly based on the product and platform. While the steps provided offer a general overview of the process, they may not apply universally to every internal firewall. For a complete and detailed setup process, refer to manufacturer reference guides and technical documentation.
Install the Firewall in a Rack
Secure the firewall in a standard equipment rack. This step is crucial for ensuring the stability of the device and setting the stage for wiring and power connections.Connect Power to the Firewall
Supply power to the firewall, making use of redundant power supplies if available. This ensures continuity in power delivery and increases reliability for the network’s security infrastructure.Establish Management Connections
Configure the connections that will be used for managing the firewall, typically involving dedicated management or console ports. These ports allow for direct interaction with the firewall for setup and ongoing administration.Perform Initial Software Configuration
Power up the firewall and proceed with initial software setup. Assign IP addresses, establish administrative credentials, and complete the device registration process to bring the firewall into operation.Configure High Availability if Required
If implementing a high availability setup, configure the appropriate ports and settings based on whether an active/passive or active/active configuration is needed, ensuring failover capabilities and service continuity.
Internal Firewall Best Practices
Document Rules and Purposes
Maintaining clear records of firewall rules and the rationale behind each ensures continuity in security policy management. Documentation aids in revisiting and revising rules to maintain relevance and effectiveness over time.
Conduct Regular Audits of Event Logs
Routine examination of event logs helps identify active and dormant rules. This practice facilitates the refinement of security measures and assists in eliminating redundant or outdated rules.
Implement Automation for Rule Management
Automation serves to update firewall rules consistently and helps in preventing rule bloat. It reduces the manual workload and enhances response to emerging security threats.
Enforce Zero Trust Principles
Adopting a Zero Trust framework ensures that trust is never assumed, regardless of whether the source is inside or outside the network. This approach is fundamental in swiftly containing and mitigating the impact of infiltrations.