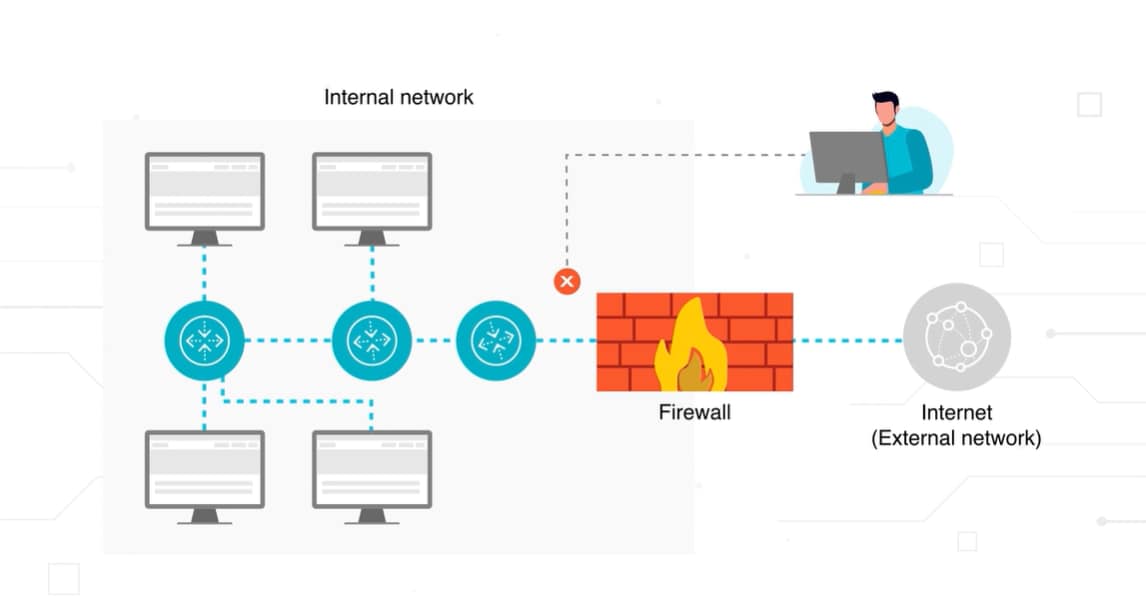
What Is a Network Firewall?
A network firewall is a security device that filters traffic between a trusted internal network and untrusted external networks.
Network firewalls operate by inspecting incoming and outgoing data packets against a set of security rules and permitting or denying passage. This process ensures only safe and authorized data enters or leaves the network, which safeguards the integrity and confidentiality of internal network systems.
Why Are Network Firewalls Important?
Network firewalls are important because they serve as the first line of defense in network security. They actively manage the ingress and egress of network traffic to prevent unauthorized access. By establishing a set of robust security rules, firewalls effectively delineate and protect the boundary between internal corporate resources and the unsecured public internet.
How Does a Network Firewall Work?
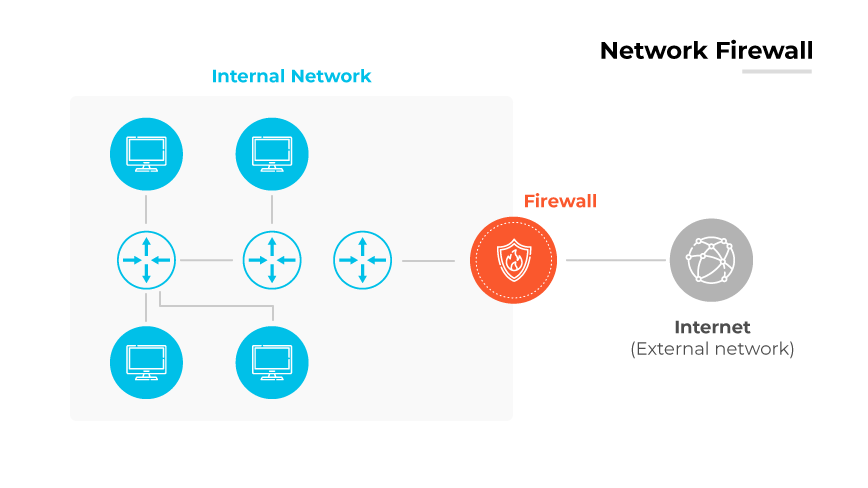
A network firewall operates as the gatekeeper at the boundary between secure internal networks and potentially insecure external networks. Network firewalls are available in software or hardware firewall form factors.
Their primary function is to analyze network packets against a set of established rules, determining which packets can enter or leave the network. Rule-based scrutiny enables the firewall to allow safe data to pass while blocking potentially malicious traffic.
Modern network firewalls have evolved to offer more than just basic packet filtering, often including features like Network Address Translation (NAT), which allows multiple devices on a local network to share a single public IP address. Network firewalls can also prioritize traffic to ensure the smooth functioning of sensitive applications, such as prioritizing VoIP data over email to prevent communication delays.
In addition to managing access based on IP addresses and ports, modern firewalls can inspect the data within packets. Deep packet inspection (DPI) allows firewalls to filter content, thwart malicious data packets, and protect against cyberattacks.
Network Firewall Features
Access Control
Network firewalls enforce access privileges, a fundamental aspect of maintaining a secure network environment. By adopting a 'deny by default' approach, modern network firewalls typically align with Zero Trust security models that assume no traffic is trusted, which significantly reduces risk.
Data Protection
Data protection limits access to sensitive information. They prevent unauthorized entities from reaching critical data, safeguarding confidential information such as financial records and personal data against unauthorized disclosure.
Traffic Monitoring
Traffic monitoring is another fundamental feature of network firewalls. By monitoring data transfers, network firewalls can identify and neutralize risks, allowing network administrators to adjust security settings in response to observed traffic patterns.
Intrusion Prevention System (IPS)
The role of firewalls in preventing system hijacking is critical. They serve as a deterrent to cybercriminals by blocking access to network resources.
Threat Prevention
Network firewalls act as a crucial line of defense against malware, spyware, adware, etc. As technological complexity increases, so do the potential entry points for these threats, which network firewalls help to seal off.
Types of Network Firewalls
Packet Filtering Firewall
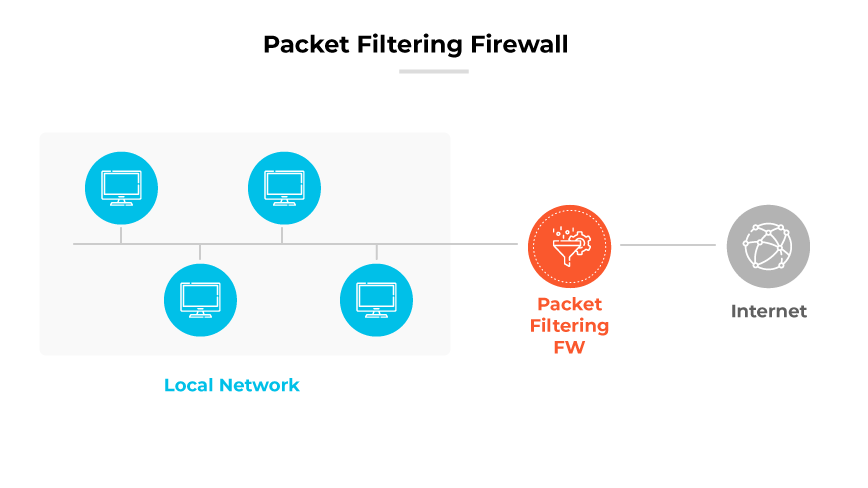
Packet filtering firewalls operate at the network layer to control access to data based on a set of rules. These rules are applied to data packets and their attributes such as IP addresses and ports, determining whether the packets are allowed through the network.
Stateful Inspection Firewall
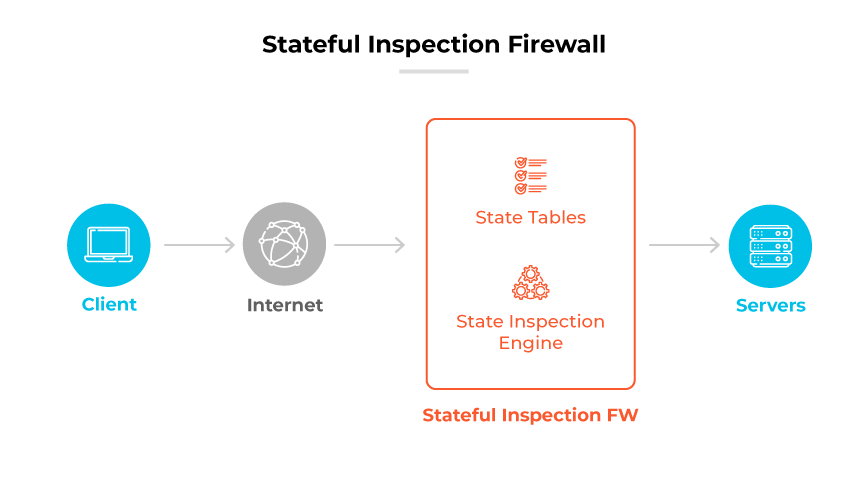
Stateful inspection firewalls provide a more sophisticated level of protection by monitoring the state of active network connections. They inspect both the header information and the state of packets, enabling them to make more informed decisions about which traffic to allow or deny.
Proxy Firewall
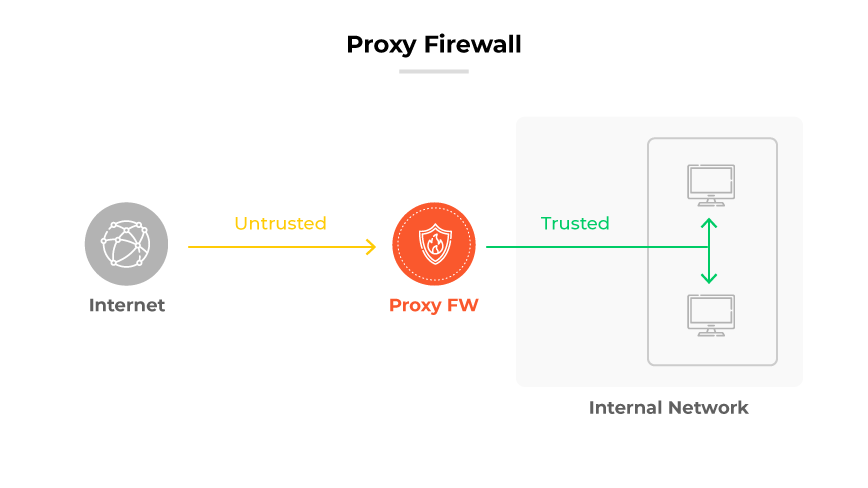
Proxy firewalls act as intermediaries between users and the services they access. By handling requests on behalf of users, they provide a high level of data security and privacy, filtering messages at the application layer and preventing direct connections from outside the network.
Circuit-Level Gateway
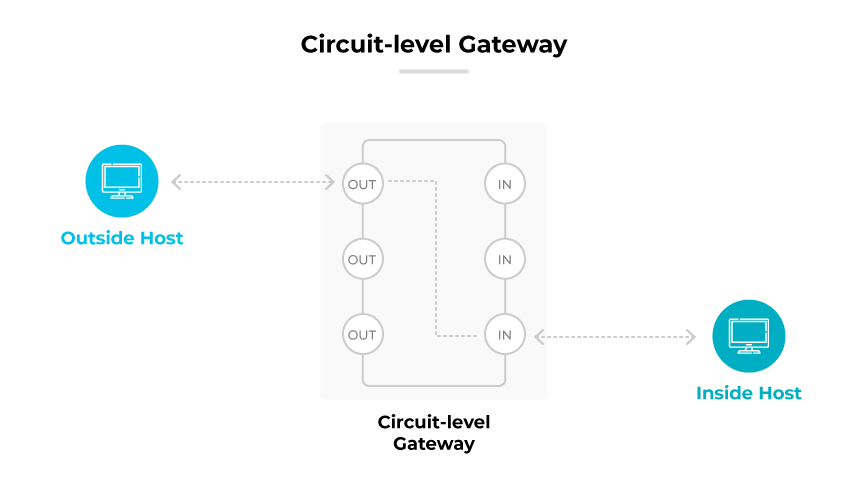
Circuit-Level Gateway
Circuit-level gateways operate at the session layer, establishing a secure connection or circuit before allowing traffic through. They verify the legitimacy of a session's initiation without inspecting the actual content of data packets, making them efficient for managing and validating connections quickly.
Next-Generation Firewall (NGFW)
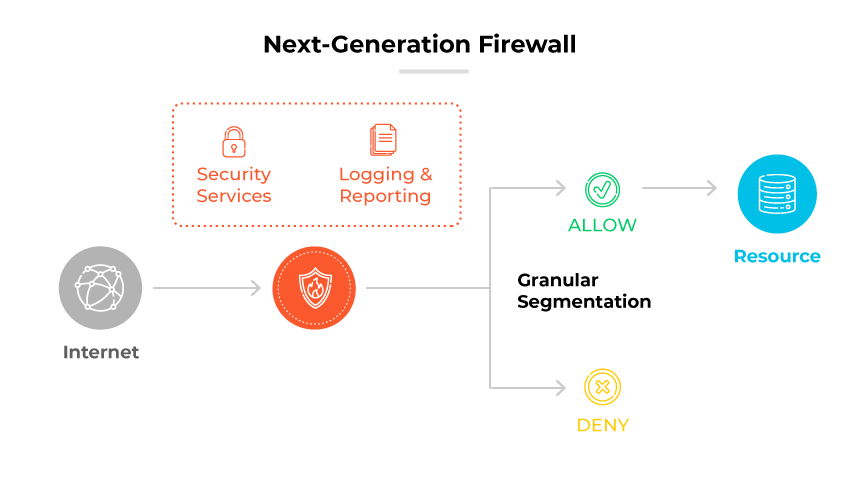
Next-Generation Firewalls (NGFWs) offer comprehensive security features that go beyond traditional firewalls by incorporating advanced inspection capabilities, application awareness, and threat intelligence. They analyze traffic at a deeper level to protect against complex, modern threats.
Types of Firewalls Defined and Explained
Network Firewalls vs. Host-Based Firewalls
Network firewalls are designed to shield the network by filtering traffic that enters or leaves through network borders. They enforce security policies across network infrastructure, assessing data packets at various levels to prevent unauthorized access. These firewalls are often placed at strategic points within the network to inspect and manage the flow of traffic, detecting and preventing external threats.
Host-based firewalls, on the other hand, are installed on individual devices within the network. They provide granular control over the incoming and outgoing network traffic of their host device. Unlike network firewalls that protect the perimeter, host-based firewalls offer a second layer of defense, managing traffic at the device level and preventing the execution of harmful applications or the exploitation of vulnerabilities within individual systems.
The integration of both network and host-based firewalls in an enterprise setting offers a layered network security solution. While network firewalls serve as the first line of defense against attacks that target the network at large, host-based firewalls add depth to security protocols by securing internal traffic and providing endpoint protection.