What Is SOAR?
Security orchestration, automation and response (SOAR) technology helps coordinate, execute and automate tasks between various people and tools all within a single platform. This allows organizations to not only quickly respond to cybersecurity attacks but also observe, understand and prevent future incidents, thus improving their overall security posture.
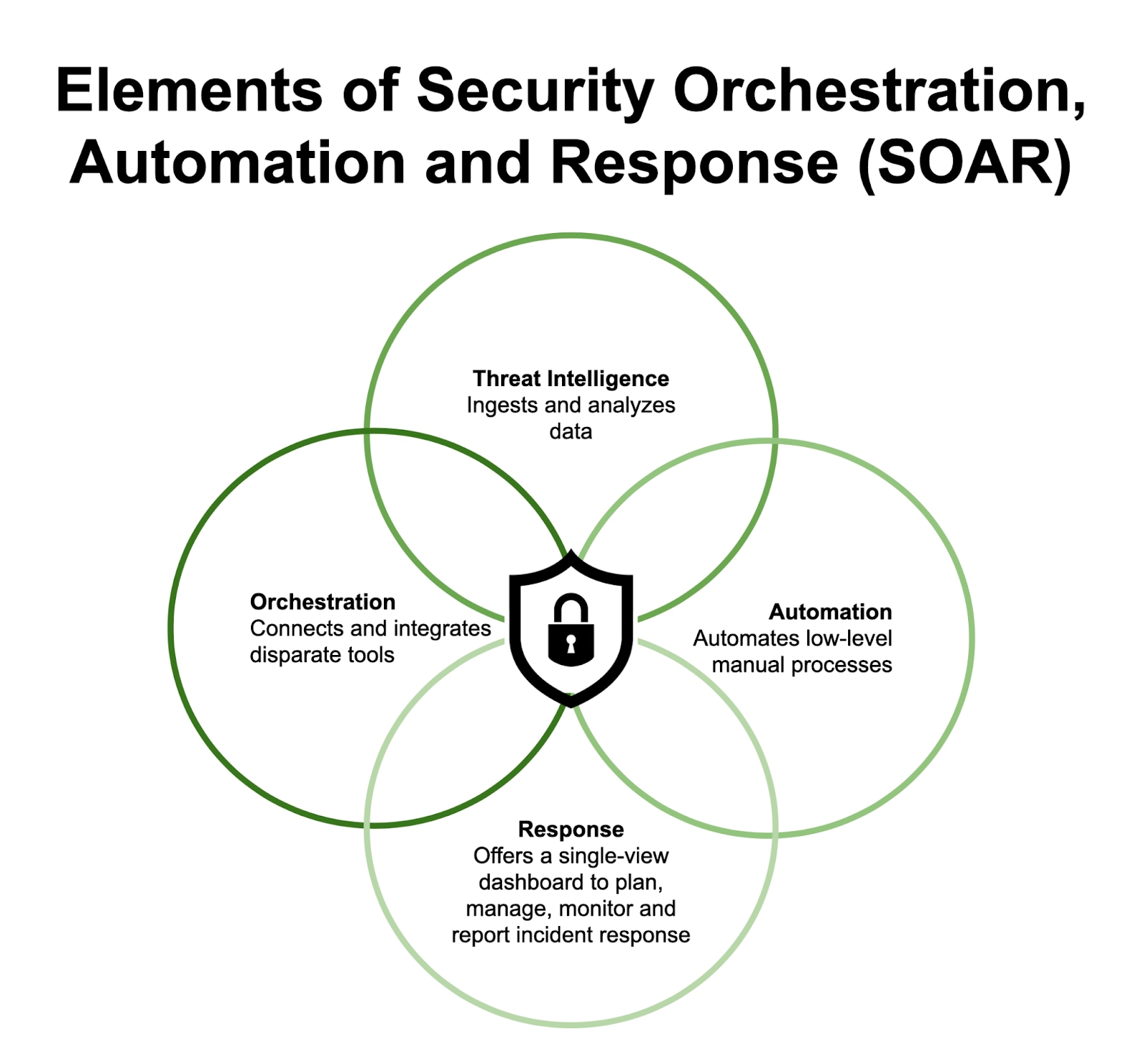
A comprehensive SOAR product, as defined by Gartner, is designed to operate under three primary software capabilities: threat and vulnerability management, security incident response, and security operations automation.
Threat and vulnerability management (orchestration) covers technologies that help amend cyberthreats, while security operations automation (automation) relates to the technologies that enable automation and orchestration within operations.

SOARs ingest alert data, and these alerts then trigger playbooks that automate/orchestrate response workflows or tasks. Then, using a combination of human and machine learning, organizations are able to analyze this diverse data in order to comprehend and prioritize automated incident response actions to any future threats, thus creating a more efficient and effective approach to handling cybersecurity and improving security operations.
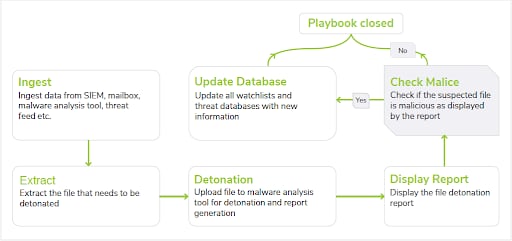
Figure 1: Sample SOAR playbook for malware analysis
What Is SIEM?
SIEM stands for security information and event management. It is an arrangement of services and tools that help a security team or security operations center (SOC) collect and analyze security data as well as create policies and design notifications. A SIEM system uses the following to manage security information and events: data collection, consolidation, and correlation, as well as notifications once a single event or an arrangement of events triggers a SIEM rule. Organizations also set up policies such as rules, reports, alerts and dashboards that align with their specific security concerns.
SIEM tools enable IT teams to:
- Use event log management to consolidate data from several sources
- Attain organization-wide visibility in real time
- Correlate security events collected from logs using if-then rules to effectively add actionable intelligence to data
- Use automatic event notifications that can be managed via dashboards
SIEM combines the management of security information and security events. This is accomplished using real-time monitoring and the notification of system administrators.
SOAR vs. SIEM
Many define SOAR and SIEM as similar products since both detect security issues and collect data regarding the nature of the problem. They also deal with notifications that security personnel can use to address concerns. However, there are significant differences between them.
SOAR collects data and alerts security teams using a centralized platform similar to SIEM, but SIEM only sends alerts to security analysts. SOAR security, however, adds in automation and response to the investigation path by using automated playbooks or workflows and artificial intelligence (AI) to learn pattern behaviors, thus enabling it to predict similar threats before they happen.
Because SOARs, such as Cortex XSOAR, typically ingest alerts from sources that SIEMs do not cover - for example vulnerability scan findings, cloud security alerts, and IoT device alerts - it's easier to deduplicate alerts and in fact, this is a typical use case for SOAR and SIEM integrations. This reduces the amount of time it takes to manually handle alerts, making it easier for IT security staff to detect and address threats.
Deep dive into the essential characteristics of SOAR vs SIEM to learn how these platforms strengthen security: SOAR vs SIEM: What is the Difference?
SOAR vs SIEM vs XDR
SOAR, SIEM and Extended Detection and Response (XDR) each serve a different purpose in the cybersecurity landscape. They are often utilized together to provide a more comprehensive security strategy. SIEM focuses on log analysis and threat detection, XDR expands detection across multiple layers, and SOAR automates and orchestrates the response.
Dig into the differences between SOAR, SIEM and XDR: What is SOAR vs SIEM vs XDR?
What is Security Orchestration and Automation?
Security automation is the machine-based execution of security actions with the power to detect, investigate and remediate cyberthreats, without the need for manual human intervention. It does much of the rote work for the SOC team, so they no longer need to weed through and manually address every alert as it comes in. Security automation can:
- Detects threats in your environment.
- Triage potential threats.
- Determine whether to take action on the incident.
- Contain and resolve the issue.
All of that can happen in seconds, without any involvement from human staff. Security analysts don't have to follow the steps, instructions and decision-making workflow to investigate the event and determine whether it is a legitimate incident. Repetitive, time-consuming actions are taken out of their hands so they can focus on more important, value-adding work.
Security orchestration is the machine-based coordination of a series of interdependent security actions, including incident investigation, response and ultimately resolution, all across a single, complex infrastructure. It ensures that all of your security and non-security tools are working together in unison whether automating tasks across products and workflows or manually alerting agents on important incidents that need more attention.
Security orchestration can:
- Provide better context around security incidents. A security orchestration tool aggregates data from different sources to offer deeper insight. As such, you gain a comprehensive view of the entire environment.
- Allow for deeper, more meaningful investigations. Security analysts can stop managing alerts and start investigating why those incidents are occurring. Additionally, security orchestration tools typically offer highly interactive and intuitive dashboards, graphs and timelines; and those visuals can be highly useful during the investigative process.
- Improve collaboration. Additional parties, including analysts at different tiers, managers, the CTO and C-suite executives, legal teams, and HR, may also need to get involved with certain types of security incidents. Security orchestration can put all the necessary data at everyone's fingertips, making collaboration, problem solving and resolution more effective.
Ultimately, security orchestration increases the integration of your defenses, allowing your security team to automate complex processes and maximize the value you receive from your security staff, processes and tools.
What Is the Difference Between Automation and Orchestration?
While security automation and security orchestration are terms that are often used interchangeably, the two platforms serve very different roles:
- Security automation reduces the time it takes to detect and respond to repetitive incidents and false positives, so alerts don't linger unaddressed for long periods of time:
- Frees security analysts' time to focus on strategic tasks, like investigative research.
- Each automated playbook addresses a known scenario with a prescribed course of action.
- Security orchestration allows you to share information easily, enabling multiple tools to respond to incidents as a group, even when the data is spread across a large network and multiple systems or devices:
- Security orchestration uses multiple automated tasks to execute a complete, complex process or workflow.
- The strength of a SOAR solution lies in its breadth of pre-built integrations that speed and ease deployment of security operations use cases.
Security automation is all about simplifying and making security operations run more efficiently because it deals with an array of single tasks, whereas security orchestration connects all of your different security tools so that they feed into one another, creating a fast and efficient workflow process from beginning to end. They work best when paired together and security groups can maximize their efficiency and productivity when they adopt both.
Explore the steps to follow for deploying SecOps automation effectively to ensure a smooth integration of SOAR into your existing operations: Guide to Deploying SecOps Automation.
What Is Threat Intelligence Management (TIM)?
In conjunction with security orchestration, automation and response, a SOAR Platform may also include the addition of Threat Intelligence Management, or TIM. Threat intelligence management (TIM) enables organizations to better understand the global threat landscape, anticipate attackers' next moves and take prompt action to stop attacks.
There is a significant difference between threat intelligence and threat intelligence management. While threat intelligence is data and information about threats, threat intelligence management is the collection, normalization, enrichment and actioning of data about potential attackers and their intentions, motivations and capabilities. This information can help organizations make faster, more informed security decisions, and thus be better prepared for cyberthreats.
Why Is SOAR Important?
In an ever-growing and increasingly digital world, organizations today face numerous challenges when it comes to cybersecurity. The more complex and malicious threats there are, the more companies need to develop an efficient and effective approach to the future of their security operations. Because of this need, SOAR is revolutionizing the way security operations teams manage, analyze and respond to alerts and threats.
Security operations teams today are tasked with the responsibility of manually handling thousands of alerts on a daily basis, leaving room for errors and major operational inefficiencies, not to mention inefficient, siloed and outdated security tools, as well as a severe lack of qualified cybersecurity talent.
Many security operations teams are struggling with connecting the noise from disparate systems, resulting in too many error-prone manual processes and lacking the highly skilled talent to solve all of this.
With the growing volume of threats and alerts and the lack of resources to address them all, not only are analysts forced to decide which alerts to take seriously and act on, and which can be ignored, they are often so overworked that they risk missing real threats and end up making an egregious number of errors as they try to respond to threats and bad agents.
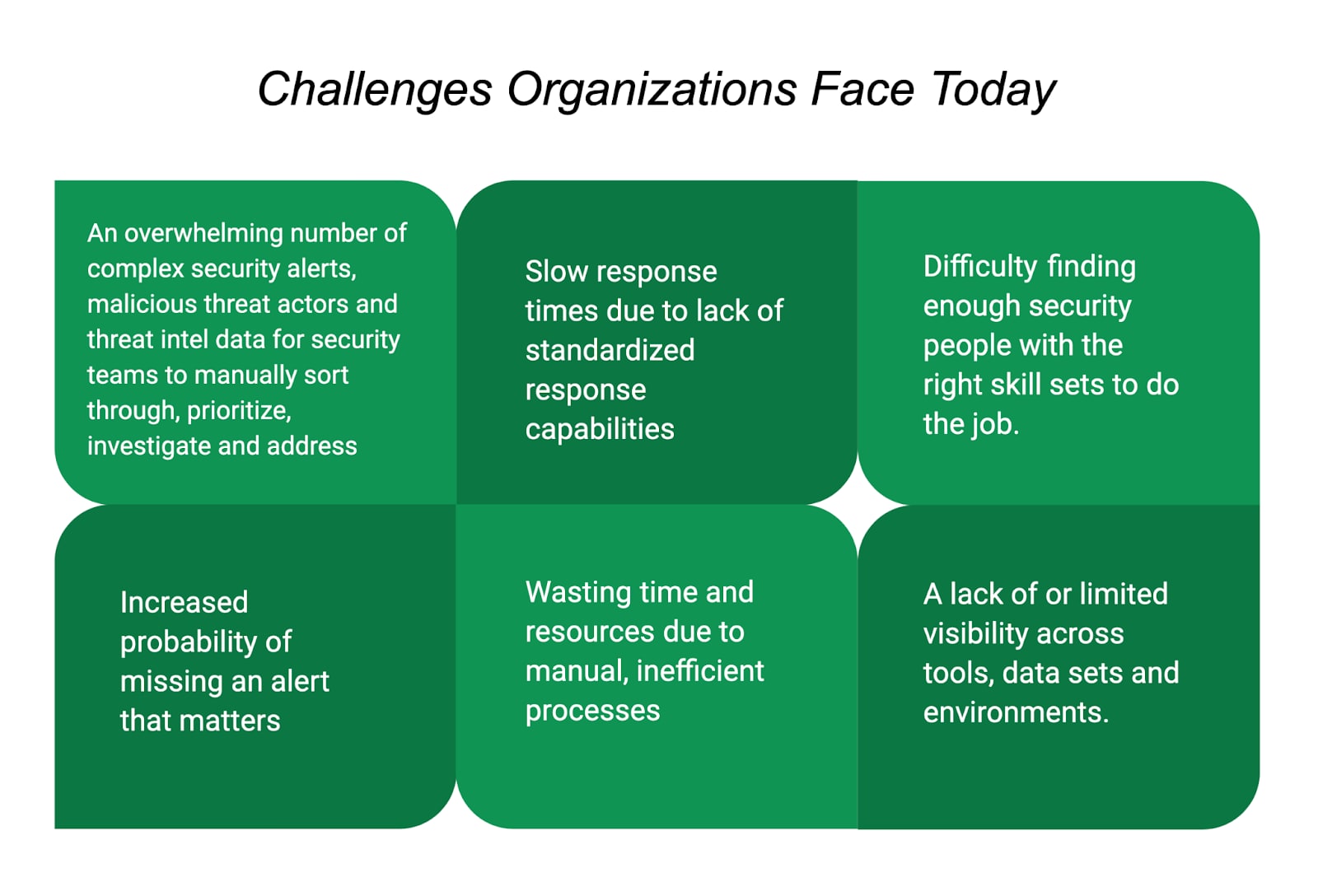
Because of this, it's critical that organizations have systems, such as a SOAR platform, that enable them to systematically orchestrate and automate their alert and response process. By filtering out mundane tasks that are taking up the most time, energy and resources, security operations teams are more effective and productive when handling and investigating incidents and thereby able to vastly improve the organization's overall security posture.
SOAR enables you to:
- Integrate security, IT operations and threat intelligence tools. You can connect all your different security solutions - even tools from different vendors - to achieve a more comprehensive level of data collection and analysis. Security teams can stop juggling a variety of different consoles and tools.
- View everything in one place. Your security team gains access to a single console that provides all the information it needs to investigate and remediate incidents. Security teams can go to one place to access the information they need.
- Speed incident response. SOARs are proven to reduce both the mean time to detect (MTTD) and mean time to respond (MTTR). Because many actions are automated, a large percentage of incidents can be dealt with immediately and automatically.
- Prevent time-consuming actions. SOAR drastically reduces the false positives, repetitive tasks and manual processes that eat up security analysts' time.
- Access better intelligence. SOAR solutions aggregate and validate data from threat intelligence platforms, firewalls, intrusion detection systems, SIEMs and other technologies, offering your security team greater insight and context. This makes it easier to resolve issues and improve practices. Analysts are better able to conduct deeper and broader investigations when problems arise.
- Improve reporting and communication. With all security operations activities aggregated in one place and displayed in intuitive dashboards, stakeholders can receive all the information they need, including clear metrics that help them identify how to make improvements to workflows and reduce response times.
- Boost decision-making ability. SOAR platforms aim to be user-friendly, even for less experienced security analysts, by offering features like pre-built playbooks, drag-and-drop functions to build playbooks from scratch, and automated alert prioritization. Additionally, a SOAR tool can gather data and offer insights that make it easier for analysts to evaluate incidents and take the correct actions to remediate them.
The Value of Having and Using SOAR
Companies and organizations find value in SOAR because it minimizes the impact of security incidents of all types, while maximizing the value of existing security investments, and reduces the risk of legal liability and business downtime overall. SOAR helps companies address and overcome their security challenges by enabling them to:
- Unify their existing security systems and centralize data collection to gain full visibility, thus greatly improving the company's security posture and operational efficiency and productivity.
- Automate repetitive manual tasks and manage all aspects of the security incident lifecycle, therefore increasing analyst productivity and freeing up analysts to focus on improving security instead of on performing manual tasks.
- Define incident analysis and response procedures as well as leverage security playbooks to prioritize, standardize and scale response processes in a consistent, transparent and documented way.
- Engage in faster incident response as analysts are able to quickly and accurately identify and assign incident severity levels to security alerts, reducing alerts and alleviating alert fatigue.
- Streamline processes and operations to better identify and manage potential vulnerabilities both proactively and reactively.
- Supports real-time collaboration and unstructured investigations by routing each security incident to the analyst best suited to respond to it while providing functions that support easy communication and tracking between teams and team members.
Evaluate your potential operational efficiency gains: Download your comprehensive report.
SOAR Use Cases
The table that follows offers examples of common use cases for SOAR.
Use Case |
What Orchestration Helps With (High-Level Overview) |
Handling security alerts |
Phishing enrichment and response - ingesting potential phishing emails; triggering a playbook; automating and executing repeatable tasks, such as triaging and engaging affected users; extracting and checking indicators; identifying false positives; and priming the SOC for a standardized response at scale. Endpoint malware infection - pulling in threat feed data from endpoint tools, enriching that data, cross-referencing retrieved files/hashes with a security information and event management (SIEM) solution, notifying analysts, cleaning endpoints, and updating the endpoint tool database. Failed user logins - after a predefined number of failed user login attempts, assessing whether a failed login is genuine or malicious by triggering a playbook, engaging users, analyzing their replies, expiring passwords and closing the playbook. Logins from unusual locations - identifying potentially malicious virtual private network (VPN) access attempts by checking VPN and cloud access security broker (CASB) presence, cross-referencing IPs, confirming a breach with the user, issuing a block and closing the playbook. |
Managing security operations |
Secure Sockets Layer (SSL) certificate management - checking endpoints to see which SSL certificates have expired or will soon be expiring, informing users, rechecking the status a few days later, escalating an issue to the appropriate people and closing the playbook. Endpoint diagnostics and kickstart - checking connectivity and agent connectivity, enriching context, opening a ticket, kickstarting agents, and closing the playbook. Vulnerability management - ingesting vulnerability and asset information, enriching endpoint and common vulnerabilities and exposures (CVE) data, querying for vulnerability context, calculating severity, turning over control to security analysts for remediation and investigation, and closing the playbook. |
Hunting for threats and responding to incidents |
Indicators of compromise (IOC) hunting - taking in and extracting IOCs from attached files, hunting IOCs across threat intelligence tools, updating databases and closing the playbook. Malware analysis - ingesting data from multiple sources, extracting and detonating malicious files, generating and displaying a report, checking for malice, updating the database, and closing the playbook. Cloud-aware incident response - consuming data from cloud-focused threat detection and event logging tools, unifying processes across cloud and on-premises security infrastructures, correlating with a SIEM, extracting and enriching indicators, checking for malice, turning over control to analysts and having them review the information, updating the database, and closing the playbook. |
Automating data enrichment |
IOC enrichment - ingesting data from multiple sources, extracting any indicators that need to be detonated, enriching URLs, IPS and hashes; checking for malice, updating the database, inviting analysts to review and investigate the information, and closing the playbook. Assigning incident severity - checking other products for a vulnerability score and to see whether existing indicators have been assigned a score, assigning severity, checking usernames and endpoints to see if they are on a critical list, assigning critical severity, and closing an incident. |
Read more: Top Security Orchestration Use Cases.
What to Look For in a SOAR Platform
Now that you’re able to define SOAR and understand its different capabilities, how do you know which SOAR product is right for your organization’s needs? What should you be looking for in a SOAR platform?
When comparing different SOAR providers, there are a handful of different factors that you’ll want to consider before making a decision. Aside from the core technology, the buyer’s decision-making process is heavily influenced by the factors and services that follow being offered as a whole. Some factors organizations should consider before implementing any SOAR product include an evaluation of their own maturity, the technology integrations and tool stack needed, existing processes, as well as their chosen method of deployment.
After an organization does an internal audit of its state of security, it must then consider the factors pertaining to the SOAR product itself. Considerations such as:
- Ease of use and connectivity to other tools: A security orchestration tool should act as connective fiber between detection, enrichment, response and allied tools.
Organizations should work toward an end-state scenario where the SOAR tool ingests alerts from detection tools that they currently deploy and executes automated playbooks that coordinate actions across enrichment, response and allied tools.
How many commands or actions can be executed from within the platform? Are the integrations able to address the following areas of focus? These include:
- Classification and mapping
- Detection and monitoring
- Data enrichment and threat intelligence feeds
- Enforcement and response
- Custom integration capabilities: Does the platform have a mechanism (for example, an internal SDK) to build custom integrations? Does the platform onboarding period include custom integration support from the services team? Are these services added on or part of the product purchase price?
- Out-of-the-box (OOTB)/Pre-built integrations: How many integrations (breadth of categories and depth in each category) does the platform have? Are new integrations added to the platform with time? At what frequency? Are these updates free or add-on services?
- Incident and case management: Does the platform have native case management or integrate with relevant case management tools? Does the platform enable reconstruction of incident timelines? Does the platform support post-incident documentation and review? Does the platform create audit trails to highlight data flow and maintain accountability?
- Integration with threat intelligence: Threat intelligence is the evidence-based knowledge, including context, mechanisms, indicators, implications and action-oriented advice about an existing or emerging menace or hazard to assets. SOAR platforms with a threat intel integration can use the knowledge gathered to help SOC teams make informed decisions regarding the impact of external threats to their environment. Incident investigations are sped up with the ability to map external threat intel to incidents happening in the network, potentially uncovering previously undetected malicious activity. Automated workflows enable scalable and real-time distribution of relevant threat intel to enforcement points.
- Workflow and playbook capabilities: Does the platform have workflow capabilities (visual task-based processes)? Does the platform show a live run of playbooks for each incident? Does the platform support nesting of playbooks? Does the platform support creation of custom playbook tasks (both automated and manual)? Does the platform support transfer of custom tasks across playbooks?
- Deployment flexibility: Technologies that organizations use to conduct their business and secure their data are constantly in a state of evolution and flux. With all these moving pieces, agility and scalability are essential when choosing a security orchestration tool, which depend heavily on the flexibility of deployment options available and how those options align with other tools and requirements within the organization.
What kind of flexible deployment options does the platform have? Is the platform designed for multitenancy, and does it have the security needed to support network segmentation for communication across organizational networks? Does the platform have horizontal scalability across multiple tenants and a level of guaranteed high availability?
- Pricing: Consider what pricing method fits well with your overall budgeting processes before selecting a security orchestration tool. The prevalent pricing methods in the market today are as follows:
- Pricing per action or automation
- Pricing per node or endpoint
- Annual subscription with add-on prices for additional admin users
- Additional services and features: Besides the core SOAR competencies, what other differentiating resources does the company provide that would benefit your organization?
- Professional services: Does the company provide professional services to their customers, ensuring a successful deployment from start to finish?
- Post-sales support: What kind of support does the company provide after installation? Does the company provide the type of support that you and your organization need?
Finding the best SOAR solution for any security operations requires alignment of the vendor’s offerings and the SOC organization’s need to improve efficiency and efficacy. The right SOAR solution should not only complement and be compatible with the products, playbooks and processes that are already set in place, it should also optimize collaboration, offer flexibility in both deployment and hosting capabilities, and have a pricing model that aligns to the needs of the organization.
SOAR plays a crucial role in modern cybersecurity due to the increasing volume and complexity of security threats. By automating routine tasks and orchestrating responses, SOAR helps organizations:
- Reduce the burden on security teams
- Enhance incident response times
- Ensure a more proactive security posture
A comprehensive SOAR platform typically includes:
- Security Orchestration: Integrates various security tools and processes for streamlined operations.
- Automation: Automates repetitive and manual tasks to improve efficiency.
- Incident Response: Coordinates and manages responses to security incidents.
- Threat Intelligence: Aggregates and analyzes threat data to enhance situational awareness.
SOAR improves incident response by:
- Automating the collection and analysis of threat data
- Coordinating responses across different security tools
- Providing playbooks for standardized procedures
- This leads to faster detection, investigation, and resolution of security incidents, minimizing the impact of threats.
Organizations can reap numerous benefits from implementing a SOAR solution, including:
- Increased efficiency through automation of routine tasks
- Enhanced visibility and control over security operations
- Faster and more effective incident response
- Improved collaboration and communication among security teams
- Better utilization of existing security investments
