- 1. How XDR Works
- 2. XDR’s Investigation and Response Workflow
- 3. XDR vs. Traditional Security Solutions
- 4. XDR vs. Other Security Solutions
- 5. The Benefits of XDR
- 6. Unique Features of XDR
- 7. Simplified Security Operations
- 8. Speed of Response and Investigation
- 9. Industry Use Cases of XDR
- 10. Strategies for Effective XDR Implementation
- 11. XDR FAQs
- How XDR Works
- XDR’s Investigation and Response Workflow
- XDR vs. Traditional Security Solutions
- XDR vs. Other Security Solutions
- The Benefits of XDR
- Unique Features of XDR
- Simplified Security Operations
- Speed of Response and Investigation
- Industry Use Cases of XDR
- Strategies for Effective XDR Implementation
- XDR FAQs
What Is Extended Detection and Response (XDR)?
- How XDR Works
- XDR’s Investigation and Response Workflow
- XDR vs. Traditional Security Solutions
- XDR vs. Other Security Solutions
- The Benefits of XDR
- Unique Features of XDR
- Simplified Security Operations
- Speed of Response and Investigation
- Industry Use Cases of XDR
- Strategies for Effective XDR Implementation
- XDR FAQs
Extended Detection and Response (XDR) represents the evolution of traditional cybersecurity solutions, offering a more integrated and automated approach to threat detection and response. As cyber threats become more sophisticated, XDR provides a comprehensive defense mechanism that unifies multiple security layers.
XDR is designed to tackle the complexity of modern threats and the limitations of traditional security measures by offering a unified approach to threat detection, investigation, and response. It integrates data from multiple sources, including endpoints, networks, cloud environments, identity and access management, and applications.
This holistic visibility empowers security teams to identify and neutralize sophisticated, multi-stage attacks efficiently. Key benefits of XDR include:
- Automated threat detection capabilities
- Streamlined security operations
- Reduced response times
- Improved security posture
As cyber threats evolve and regulatory requirements become more stringent, the XDR approach to security becomes increasingly essential.
How XDR Works
XDR aggregates data from various security layers, including endpoints, networks, and cloud environments. It leverages machine learning and AI to analyze this data in real-time, identifying patterns and anomalies that indicate potential threats.
For instance, if an endpoint detects unusual login activity while the network layer registers data exfiltration attempts, XDR correlates these events to trigger an automated response.
XDR’s Investigation and Response Workflow
Understanding XDR's detailed workflow is crucial for leveraging its full potential. This section breaks down the investigation and response workflow, highlighting each step in detecting, analyzing, and responding to security incidents using an XDR platform.
Incident Detection
XDR platforms continuously monitor and aggregate alerts and logs from various security tools across an organization’s IT infrastructure, including endpoints, networks, identity and access management, and cloud environments. The initial detection phase focuses on identifying potential security incidents through:
- Unified data collection: XDR collects data from multiple sources, providing a centralized view of all security events and alerts.
- Threat intelligence integration: Continuous updates from global threat intelligence feeds enhance the platform’s ability to detect known and emerging threats.
- Data enrichment: As data flows into XDR from multiple sources, related events in the data flow are stitched together into combined events, broadening initial context. Stitched data may include IP addresses, domains, file hashes, and threat intelligence data.
- Advanced analytics: Machine learning algorithms analyze enriched data to identify patterns and anomalies that may indicate a security incident.
Incident Analysis and Scoring
Once a potential incident is detected, the next step involves grouping related alerts into a single incident, telling the story of the attack as it has unfolded, and providing comprehensive context. Each incident is then assessed and prioritized by severity.
- Alert grouping: After XDR has analyzed data combined from multiple sources to find new anomalies, it groups these with other alerts from endpoint, cloud, network and other sensors to create a single incident.
- Incident scoring: The combined incident, representing the entirety of the attack story, is then scored by the severity of what XDR has uncovered. Security Analysts can then use this score to prioritize their investigation.
Response Actions
Based on the determined verdict, appropriate response actions are initiated to mitigate the threat and remediate the affected systems:
Malicious Verdict:
- Blocking indicators: The platform blocks identified malicious indicators such as IP addresses, domains, and file hashes.
- Endpoint isolation: Affected endpoints are isolated from the network to prevent further spread of the threat.
- Session management: User sessions are cleared and revoked, and multi-factor authentication (MFA) is enforced to secure accounts.
- Password reset: User passwords are reset to prevent unauthorized access if needed.
Benign Verdict:
- Incident closure: The incident is closed automatically without further action, minimizing disruptions to normal operations.
Monitoring and Continuous Improvement
Continuous monitoring and regular scans ensure the organization’s security posture remains robust and any new threats are promptly identified and addressed:
- Real-Time Monitoring: Dashboards provide real-time visibility into the state of endpoints and the status of incidents, enabling proactive threat management.
- Dormant Threat Scanning: Periodic scans identify dormant malware that might activate under specific conditions.
- Hygiene and Compliance: The platform monitors endpoint hygiene, ensuring compliance with security policies and minimizing risks from external devices like USBs.
By integrating detection, enrichment, analysis, and automated response into a unified workflow, XDR significantly enhances an organization's ability to detect and respond to security incidents before a breach can occur. Leveraging these capabilities ensures a proactive and comprehensive approach to cybersecurity, safeguarding your organization against evolving threats.
Boost your XDR knowledge: What is Extended Detection and Response (XDR) Security?
XDR vs. Traditional Security Solutions
XDR represents a new approach to cybersecurity, offering a comprehensive and integrated method of threat detection, response, and adaptation to new threats. By collecting and correlating data from various sources across an organization's IT ecosystem, XDR provides security teams with a complete view of potential threats and their context, facilitating better identification and faster response to sophisticated attacks.
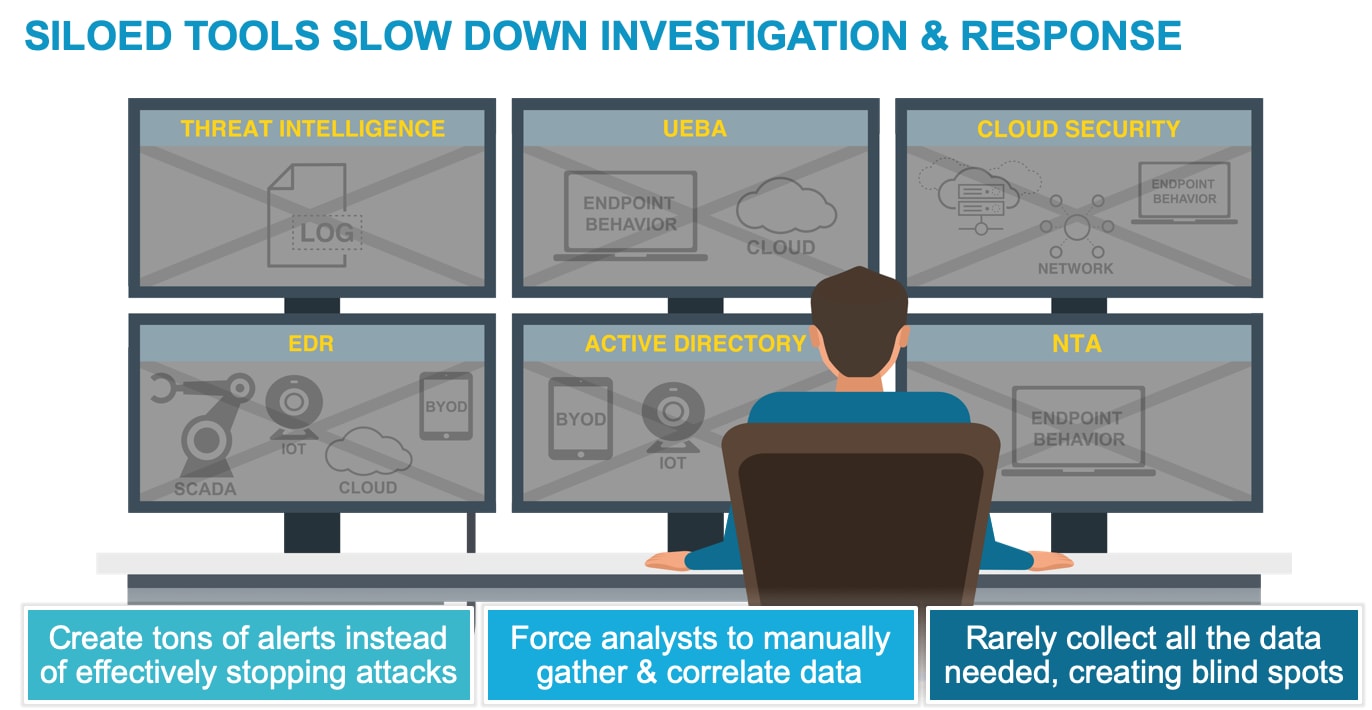
Siloed tools slow down investigation and response
Scope and Data Integration
Traditional solutions often operate in silos, focusing on specific layers of defense like endpoint, network, or application security. This fragmentation limits their ability to effectively detect and respond to coordinated multi-stage attacks. XDR integrates data from multiple sources, providing a broader perspective on threats and enabling the correlation of data across various vectors, helping uncover complex attack patterns.
Contextual Understanding
Traditional solutions lack context, often providing isolated alerts that require manual investigation and correlation to understand the full scope of an attack. XDR provides contextual insights by analyzing data across different layers of the IT environment. This context helps security teams understand attackers' tactics, techniques, and procedures (TTPs), allowing for a more informed response.
Automated Threat Detection and Response
Traditional solutions rely heavily on manual intervention for threat analysis, investigation, and response, leading to delays in detecting and mitigating attacks. XDR employs automation and machine learning to identify and respond to threats rapidly. Automated playbooks can execute predefined actions based on threat severity, reducing response time and allowing security teams to focus on more strategic tasks.
Real-time Monitoring
Traditional solutions often lack real-time monitoring capabilities, making detecting and responding to threats as they unfold challenging. XDR provides real-time monitoring and continuous threat detection across the entire IT ecosystem. This proactive approach helps identify and thwart threats early, minimizing potential damage.
Adaptability and Scalability
Traditional solutions may need help to adapt to new attack techniques and the dynamic nature of evolving threats. Scaling these solutions can be complex and resource-intensive. XDR solutions are designed to adapt to new threats and attack vectors. They can scale to accommodate growing IT infrastructures, ensuring consistent protection even as an organization's digital footprint expands.
Cloud and Remote Work Support
Traditional solutions might not be well-suited to securing cloud environments and remote work scenarios, which have become increasingly prevalent. XDR is built to handle diverse environments, including cloud-based systems and remote devices. This flexibility enables organizations to maintain security across distributed and evolving infrastructures.
XDR vs. Other Security Solutions
As cybersecurity threats become increasingly sophisticated, organizations explore various solutions to enhance their security posture. XDR stands out among these solutions by providing a comprehensive, integrated approach to threat detection, response, and mitigation.
XDR Vs. EDR
XDR solutions should always contain at least one built-in sensor, which is most frequently an Endpoint agent, performing threat prevention, detection and response. This is also known as endpoint detection and response (EDR). XDR expands the scope of EDR beyond endpoints to multiple vectors, integrating data from networks, clouds, identity and access management, and applications. This broader perspective allows for more effective threat hunting, faster incident response times, and improved overall security posture.
Delve into the differences between XDR and EDR: What is EDR vs. XDR?
XDR vs. MDR
Managed detection and response (MDR) is a service external security experts provide, while XDR is a technology solution for threat defense. MDR services manage various implementations of detection and response, from EDR to NDR or XDR. Using an MDR service allows organizations to quickly ramp up to a technology like XDR, immediately gaining expert implementation and operation.
Discover how XDR and MDR are different approaches to threat detection, used in tandem: What is XDR vs. MDR?
XDR vs. NDR
Network Detection and Response (NDR) specializes in monitoring and analyzing network traffic to identify and respond to potential security threats. XDR encompasses network data analysis and integrates endpoint, cloud, identity and access management, and application telemetry, providing a more comprehensive and interconnected security approach.
XDR vs. ITDR
Identity Threat Detection and Response (ITDR) focuses on identifying and mitigating identity and compromised credentials threats. XDR incorporates identity data into its broader data collection and analysis scope, enabling it to detect and mitigate a wide range of security threats, including those pertaining to identity. ITDR is increasingly built as an integrated function of XDR solutions.
XDR Vs. SIEM
Security information and event management (SIEM) systems aggregate and analyze log data across the IT environment. They provide real-time analysis of security alerts and support compliance reporting and incident response.
However, SIEM can be reactive and rely on predefined rules. XDR unifies control points, security infrastructure, and threat intelligence, automatically correlating data from multiple security products to facilitate proactive threat detection and improved incident response.
Understand how the differences between XDR vs. SIEM inform your cybersecurity strategy: What is the Difference Between XDR vs. SIEM?
The Benefits of XDR
Beyond improving detection and response times, XDR significantly reduces the workload on security teams by automating routine tasks. For example, in a retail environment, XDR can quickly identify and mitigate a point-of-sale malware attack, ensuring minimal disruption to business operations.
Improved Visibility and Detection Capabilities
Visibility and detection are critical for threat mitigation. If you can’t see a threat, you can’t identify or investigate it and certainly can’t stop it. Threat actors leverage the cloud and AI to wage massive, multifaceted attacks that allow them to establish persistence and exfiltrate valuable data and intellectual property. This means XDR must have powerful visibility and detection capabilities.
Broad Visibility and Contextual Understanding
XDR must have visibility and detection capabilities across your entire environment, integrating telemetry from your endpoints, networks, cloud environments, identity and access management, and applications. Moreover, it must be able to correlate these data sources to understand how various events are linked and when a particular behavior is suspicious based on context.
Data Retention
Attackers are patient and persistent. They know they’re harder to detect if they move slowly, waiting out the log retention periods of the detection technologies they’re up against. XDR collects, correlates, and analyzes data from the network, endpoint, cloud and identity and access management, and applications within a single repository, offering custom periods of historical retention.
Analysis of Internal and External Traffic
Traditional detection techniques focus primarily on external attackers, providing an incomplete view of potential threat actors. Detection can’t solely look for attacks coming from beyond the perimeter. It must also profile and analyze internal threats to look for anomalous and potentially malicious behavior and identify credential misuse.
Integrated Threat Intelligence
Detection must leverage threat intelligence gathered across a global network of enterprises. When an organization within the extended network identifies an attack, you can use the knowledge gained from that initial attack to identify subsequent attacks within your environment.
Customizable Detection
Detection systems must be highly customizable based on your environment's particular needs. These challenges require an XDR solution that supports both custom and predefined detections.
Machine Learning–Based Detection
Attacks not detected by sensors at the endpoint, network, or cloud must be uncovered within the telemetry data collected from these sources and beyond. Machine learning is the only way to process the vast volume of data from an enterprise organization, expanding the capabilities of human security analysts with machine power and speed.
In an XDR solution, machine learning analytics process all data entering the XDR solution continuously to find anomalies and ongoing attacks.
Customer Story: Learn about the implications of the SolarWinds Supply Chain Attack and how to protect your organization from similar threats.
Unique Features of XDR
Unified Data Integration
Unlike traditional solutions that operate in silos, XDR integrates data from multiple security layers, including endpoints, networks, email, and cloud environments. For example, XDR breaks down data silos by aggregating and correlating information from various sources, providing a unified view of the security landscape. This holistic approach allows for more accurate threat detection and faster response times."
Automated Threat Detection and Response
XDR leverages advanced machine learning and artificial intelligence to automate the detection and response processes. Using AI and machine learning algorithms, XDR can automatically identify patterns and anomalies indicative of cyber threats, triggering automated responses without the need for manual intervention. This reduces the workload on security teams and ensures quicker mitigation of threats.
Advanced Analytics and Correlation
XDR employs advanced analytics to correlate events across different security layers, identifying complex attack patterns that traditional solutions might miss.
Traditional security solutions might detect isolated events but fail to connect them as part of a larger attack. To uncover sophisticated multi-vector attacks, XDR's advanced analytics can correlate seemingly unrelated events, such as unusual login attempts and network traffic anomalies.
Behavioral Analysis
XDR utilizes behavioral analysis to establish baselines for normal activity and detect deviations that could indicate a threat. By continuously monitoring and analyzing user and entity behavior, XDR can establish what constitutes 'normal' activity. Any deviation from these baselines, such as unusual data access patterns, triggers an alert, enabling early detection of potential threats.
Cross-Layer Visibility
XDR provides comprehensive visibility across all security layers, allowing for better context and understanding of threats. With cross-layer visibility, security teams can view and analyze data from endpoints, networks, and cloud environments in a single interface. This comprehensive view provides a better context for understanding the scope and impact of threats, leading to more effective threat hunting and incident response.
Proactive Threat Hunting
XDR supports proactive threat hunting, enabling security teams to search for potential threats that may not have triggered automated alerts.
For example, XDR's advanced capabilities facilitate proactive threat hunting by enabling security analysts to query and analyze data across the entire security infrastructure. This proactive approach identifies latent threats that automated systems might miss, ensuring a more robust defense.
Integrated Response Capabilities
XDR detects threats and orchestrates and automates response actions across different security components. When a threat is detected, XDR can automatically initiate response actions such as isolating infected endpoints, blocking malicious IP addresses, and alerting the security team. This integrated response capability minimizes the time to mitigate threats and reduces potential damage.
Scalability and Flexibility
XDR solutions are designed to scale and adapt to the evolving threat landscape and organizations' growing needs. XDR platforms are built to handle data's increasing volume and complexity as organizations grow. Their flexible architecture allows for easy integration with existing security tools and technologies, ensuring that the security posture can evolve alongside the organization.
Simplified Security Operations
As organizations grapple with an ever-expanding threat landscape and increasingly complex IT ecosystems, XDR offers a streamlined approach to managing security by consolidating and automating various tasks.
One key way XDR simplifies security operations is through centralized visibility. Traditional security solutions often generate alerts from different sources, inundating security teams with a sea of data to sift through.
XDR addresses this challenge by aggregating data from endpoints, networks, applications, and cloud environments into a unified platform. This single-pane view provides security teams comprehensive insight into the organization's security posture, eliminating the need to navigate disparate tools and interfaces.
This streamlined visibility accelerates threat detection and facilitates quicker decision-making, as security professionals can grasp the broader context of an incident and assess its severity in real time.
Moreover, XDR's automation capabilities significantly enhance the efficiency of security operations. Instead of triaging every alert, XDR solutions group related alerts into a single incident, representing the entirety of an attack, and scores these incidents based on severity. Analysts can set up automated responses, investigate these incidents, and execute response actions independently.
This automation expedites the response process and minimizes the risk of human error, freeing up security personnel to focus on more strategic initiatives. Routine and repetitive tasks such as triaging alerts, isolating compromised endpoints, and initiating incident response workflows are seamlessly executed by the XDR platform, allowing security teams to allocate their expertise where it matters most.
Speed of Response and Investigation
XDR solutions can dramatically improve the triaging and investigating threats with enhanced investigation and response capabilities.
Correlation and Grouping of Related Alerts and Telemetry Data
When a threat alert is received, the attacker is already active within your environment. It's essential to comprehend the attack and its entire chain of events quickly. XDR tools reduce noise by automatically grouping related alerts and prioritizing the most urgent events. Subsequently, the tool must be capable of creating a timeline of the attack by consolidating activity logs from your network, endpoint, and cloud environments.
XDR uses advanced analytics and machine learning algorithms to correlate data across different sources. It looks for patterns, anomalies, and relationships between events that might indicate a security threat. For instance, it can correlate an unusual login attempt with suspicious network traffic and endpoint activity to identify a coordinated attack.
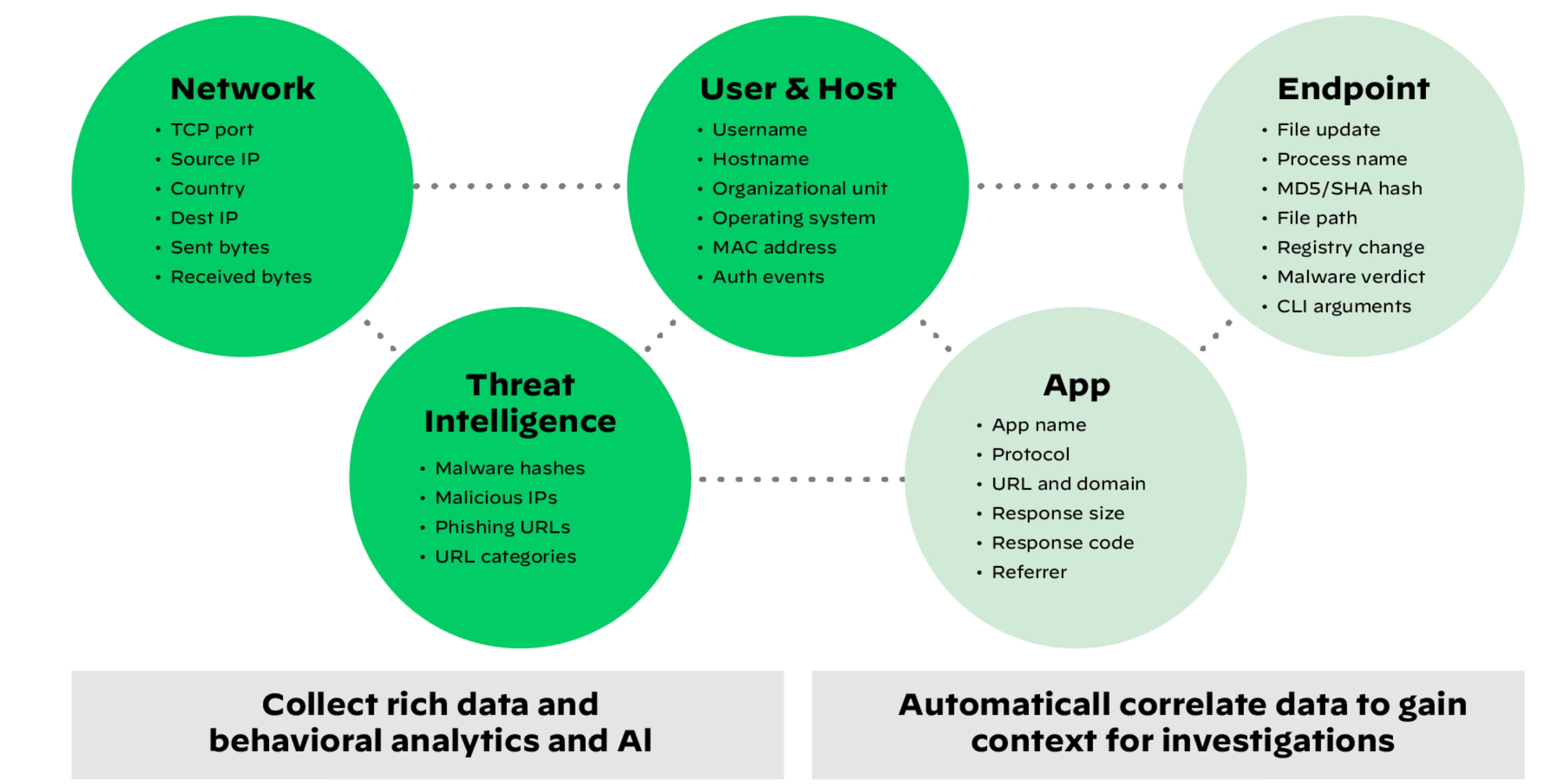
XDR collects data from any source, correlating and stitching it together for better detection and hunting.
Swift Investigation Into Incidents
XDR allows for swift investigation, with instant access to all forensic artifacts, events, and threat intelligence in one location. XDR solutions connect this information into a causality chain, showing the root cause of an alert and the impacted assets so security analysts can pinpoint response action.
Consolidated User Interfaces with the Ability to Pivot Quickly
Security analysts need a streamlined work environment that enables them to understand the root cause of alerts from any source with a single click. Analysts shouldn’t have to waste time switching between multiple tools.
Manual and Automated Threat Hunting
Supporting threat hunting requires powerful search capabilities to look for evidence to prove attack hypotheses and integrated threat intelligence to search for activity already seen within the extended intelligence network.
Coordinated Response
After threat activity has been detected and investigated, the next step is efficient and effective remediation and policy enforcement. Your system must be able to coordinate a response to active threats and prevent future attacks across your network, endpoint, and cloud environments. This includes communication between prevention technologies and the ability for an analyst to take response actions directly through the XDR interface.

Example of a Multi-stage Attack
Industry Use Cases of XDR
Extended Detection and Response (XDR) is revolutionizing cybersecurity across various industries by providing comprehensive threat detection, investigation, and response capabilities.
Protecting Large Enterprises
Large enterprises often receive numerous alerts from different monitoring solutions, which can be overwhelming. XDR integrates detection technologies and sophisticated analytics to analyze endpoint, network, cloud, identity and access management, and application data and identify adversary activities.
XDR provides centralized visibility, enabling security teams to identify and respond to complex threats that traverse multiple areas, enhancing the overall security posture of large organizations.
Defending Against Advanced Persistent Threats (APTs)
XDR is highly effective in defending against advanced persistent threats (APTs) and sophisticated, stealthy attacks to gain prolonged access to systems for data theft, espionage, or disruption.
The XDR approach makes it a powerful defense mechanism against APTs by aggregating data from networks, endpoints, cloud, identity and access management, and application environments. It enables the detection of subtle signs of APTs, uses machine learning and behavioral analysis for advanced threat detection, enables automated response, and integrates various security tools for comprehensive understanding and more targeted responses.
XDR for Regulatory Compliance
XDR is crucial in helping organizations meet regulatory compliance requirements such as GDPR, HIPAA, and FINRA. Here’s how XDR assists in maintaining compliance:
- Data protection and privacy monitoring: XDR’s centralized visibility and data aggregation capabilities allow organizations to monitor data flows and access, preventing unauthorized access to sensitive data and ensuring compliance with data protection regulations.
- Threat detection and incident response: XDR’s advanced threat detection identifies potential breaches or unauthorized activities. Rapid incident response and automated actions help contain breaches swiftly, minimizing data exposure and ensuring compliance with breach notification requirements.
- Risk management and vulnerability assessment: XDR analyzes and correlates data to identify vulnerabilities, aiding in proactive risk management and compliance with regulations requiring robust security practices.
- Audit trail creation and reporting: XDR generates detailed logs and audit trails of security events, user activities, and system changes, helping organizations demonstrate compliance and provide evidence to regulators.
- Threat intelligence sharing: XDR facilitates the sharing of threat intelligence across security tools, aiding in the early detection of emerging threats and maintaining regulatory standards.
- Documentation and accountability: XDR documents security events, incident responses, and mitigation efforts, ensuring accountability and transparency in compliance practices.
- Continuous improvement and monitoring: XDR’s continuous monitoring helps organizations maintain ongoing security, adapting to new threats and regulatory changes to ensure consistent compliance.
By leveraging XDR, organizations can enhance their cybersecurity posture, effectively defend against sophisticated threats, and meet stringent regulatory requirements, ensuring comprehensive protection of sensitive data and systems.
Strategies for Effective XDR Implementation
Below are specific strategies that organizations can consider to implement XDR effectively:
Assessment and Planning
- Assess current environment: Begin by understanding your organization's existing security infrastructure, including tools, processes, and data sources. This assessment will help identify gaps that XDR can address.
- Define objectives: Clearly define your goals for implementing XDR. Whether it's improving threat detection, incident response, compliance, or overall security, having specific objectives will guide your implementation strategy.
Vendor Selection
- Research and evaluate: Explore different XDR solutions available in the market. Assess their capabilities, features, scalability, integration options, and alignment with your organization's needs and goals.
- Vendor partnerships: Consider vendors with a strong track record, objective third-party evaluations, expertise in your industry, and a commitment to ongoing support and updates.
Data Integration and Collection
- Identify data sources: Determine the data sources you need to integrate with XDR. These may include network logs, endpoint data, cloud activity, etc.
- Data quality and enrichment: Ensure your data is accurate, relevant, and enriched with contextual information to enhance threat detection accuracy.
Consolidation of Existing Tools
- Consolidation strategy: Plan how XDR will consolidate your existing security tools, such EDR, NDR, and others. XDR can be the foundation of your Security Operations platform, on which you can fold in additional technologies, such as SOAR and SIEM.
- APIs and connectors: Explore available APIs and connectors that XDR vendors offer to streamline integration with your existing ecosystem.
Threat Detection and Response Workflows
- Customization: Tailor detection and response workflows based on your organization's unique risks, threat landscape, and compliance requirements.
- Automation: Implement automated responses to specific threats to accelerate incident containment and reduce manual intervention.
Personnel and Training
- Skill development: Train your security team to use and manage the XDR platform effectively. This will ensure that your team can fully leverage the solution's potential. If you do not have the internal resources to operate XDR but still want the outcomes, leverage an MDR service.
- Cross-functional collaboration: Foster collaboration between security, IT, and compliance teams to ensure alignment in implementing XDR strategies.
Continuous Monitoring and Improvement
- Performance metrics: Define key performance indicators (KPIs) that measure the effectiveness of your XDR implementation, such as mean time to detect (MTTD) and mean time to respond (MTTR).
- Regular assessments: Conduct regular assessments of your XDR implementation to identify areas for improvement, adjust configurations, and address emerging threats.
Regulatory Compliance
- Align with regulations: Customize your XDR implementation to align with specific regulatory requirements that your organization must adhere to, such as GDPR, HIPAA, or industry-specific standards.
Vendor Collaboration
- Engage vendor support: Maintain a close working relationship with your chosen XDR vendor. Leverage their expertise for guidance, updates, and troubleshooting.
Effective XDR implementation is a dynamic process that requires ongoing attention and adaptation. Review your strategies regularly, assess their effectiveness, and make necessary adjustments to ensure that your organization maximizes the benefits of XDR in enhancing security, threat detection, and regulatory compliance.
Take a deep dive into the components of XDR, its implementation, and emerging trends: What is Extended Detection and Response (XDR) Security?