-
- Multifactor Authentication Explained
- Why Multifactor Authentication Is Crucial
- How Multifactor Authentication Works
- Authentication Factors and Methods
- MFA vs. Two-Factor Authentication (2FA)
- Implementing Multifactor Authentication: Best Practices
- MFA Deployment Considerations
- Common MFA Security Weaknesses and Mitigations
- MFA Policy, User Experience, and Compliance
- Advanced MFA Concepts: Adaptive and AI-Enhanced Authentication
- Real-World MFA Examples
- The Future of MFA: Emerging Trends and Innovations
- Multifactor Authentication FAQs
Table of Contents
-
What Is Identity Visibility and Intelligence (IVIP)?
- The Identity Visibility Crisis
- Understanding IVIP: Definition and Core Concepts
- Why IVIP Emerged Now
- What IVIP Actually Does
- IVIP Within the Identity Fabric Architecture
- IVIP vs. Adjacent Technologies
- Real-World Use Cases and Applications
- Implementation Considerations and Architecture
- Market Maturity and Adoption Roadmap
- Identity Visibility and Intelligence Platforms (IVIP) FAQs
-
What is Identity Security Posture Management (ISPM)?
- What Identity Security Posture Management Is and Why It Emerged
- The Identity Attack Surface in Modern Enterprises
- Core Capabilities of ISPM Platforms
- How ISPM Differs from Adjacent Technologies
- ISPM Architecture and Technical Implementation
- Key Use Cases and Operational Workflows
- ISPM Implementation Strategy
- Common Identity Posture Risks ISPM Addresses
- Measuring and Improving Identity Security Posture
- The Future of Identity Security Posture Management
- ISPM FAQs
- What are MFA Examples and Methods?
What Is Multifactor Authentication?
5 min. read
Table of Contents
Multifactor authentication (MFA) requires users to provide two or more verification factors to access a resource. This security measure adds layers of defense beyond a simple password, significantly increasing protection against unauthorized access to accounts and systems. It combines different authentication methods for stronger identity assurance.
Key Points
-
MFA is a crucial security layer: It requires two or more distinct verification factors to access accounts and systems, going beyond just a password for significantly enhanced protection. -
Combats common cyber threats: MFA effectively mitigates credential-based attacks (like phishing, brute-force, and credential stuffing) by requiring an additional, separate form of verification. -
Three core authentication categories: MFA relies on combining factors from "something you know" (e.g., password), "something you have" (e.g., phone, security key), and "something you are" (e.g., fingerprint). -
Stronger than 2FA: While all Two-Factor Authentication (2FA) is MFA, MFA is a broader term, allowing for three or more distinct factors for even higher security. -
Phishing-resistant methods are key: For the strongest protection, prioritize MFA methods like FIDO2 hardware security keys, which are highly resilient to sophisticated phishing and man-in-the-middle attacks. -
Essential for compliance and modern security: Implementing MFA is no longer optional; it's a fundamental control for protecting sensitive data, meeting regulatory requirements, and establishing a robust security posture, especially in remote and hybrid work environments.
Multifactor Authentication Explained
MFA fortifies digital security by demanding multiple pieces of evidence to verify a user's identity. Instead of relying solely on one credential—like a password—MFA mandates a combination of distinct authentication factors. This approach creates a significantly stronger barrier against cyber threats. Even if an attacker compromises one factor, they still need to overcome at least one more to gain access.
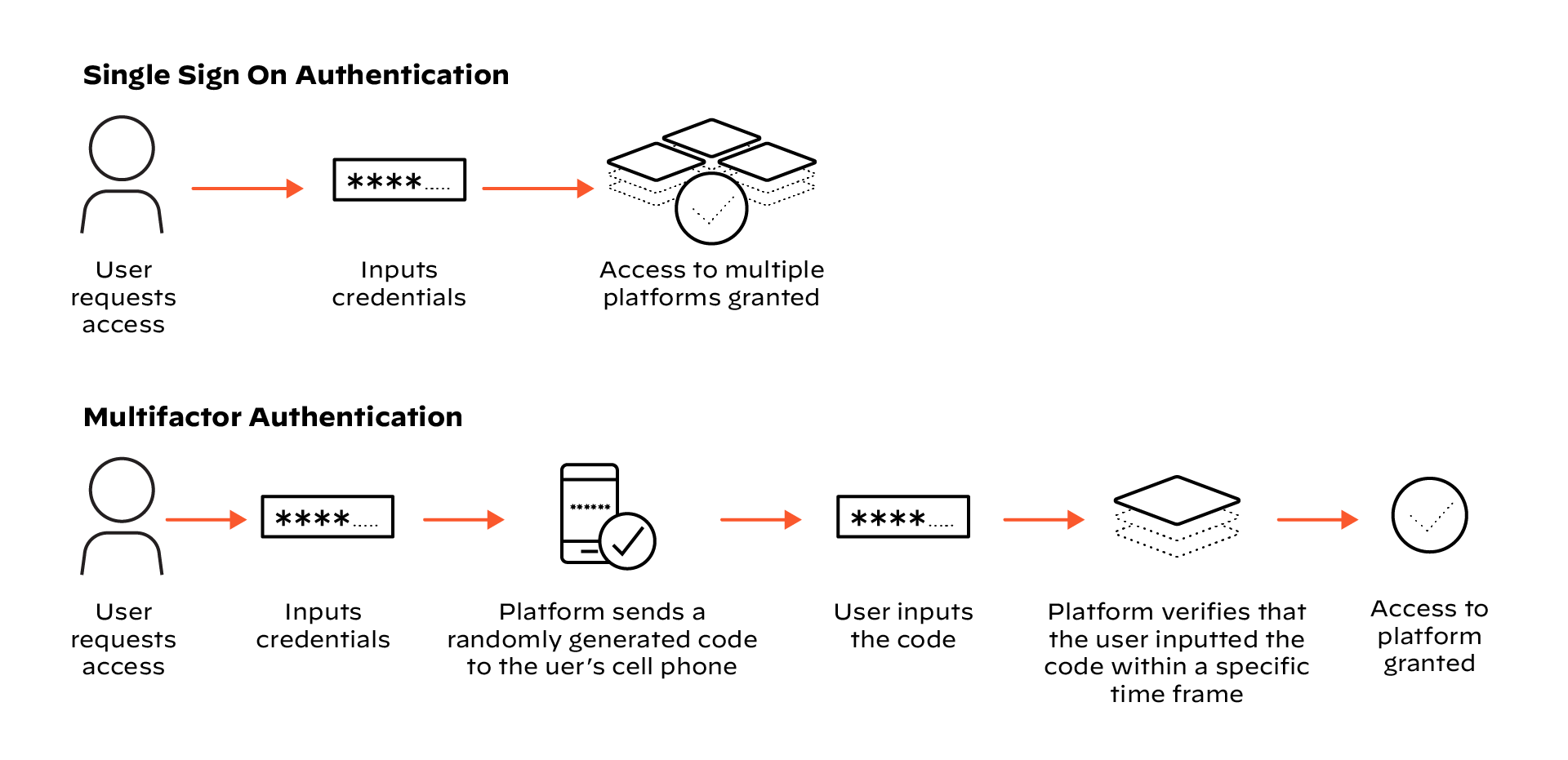
Figure 1: A comparison of single sign-on and multifactor authentication examples
MFA is vital to modern cybersecurity because it directly addresses the weaknesses of single-factor authentication. Passwords, for instance, are susceptible to phishing, brute-force attacks, and credential stuffing. A stolen or weak password often provides an attacker with complete access to an account.
By layering authentication methods, MFA drastically reduces the likelihood of a successful breach. It’s a fundamental control that protects sensitive data, intellectual property, and critical systems from unauthorized entry. Implementing MFA is no longer optional; it's an essential defense for any organization serious about securing its digital assets and maintaining trust.
Why Multifactor Authentication Is Crucial
MFA provides essential layers of security, significantly reducing the risk of unauthorized access and safeguarding sensitive information in an increasingly threat-filled digital landscape.
Mitigating Credential-Based Attacks
Cybercriminals frequently target usernames and passwords through various means, including dictionary attacks, brute force attempts, and credential stuffing. MFA immediately invalidates these stolen credentials by requiring an additional, separate verification form. Even if attackers obtain a user's password, they cannot access the account without the second factor, drastically limiting the efficacy of common credential-based attacks.
Protecting Against Phishing and Social Engineering
Phishing campaigns trick users into divulging their login credentials, often through fake websites or deceptive emails. While security awareness training helps, MFA acts as a critical failsafe. If a user falls victim to a phishing attempt, the attacker still cannot complete the login process without the user's second authentication factor. This significantly reduces the success rate of such deceptive attacks.
Reducing the Impact of Data Breaches
Credential theft remains a primary cause of data breaches across industries. When an organization suffers a breach and user credentials are exposed, MFA minimizes the damage. It prevents attackers from using those stolen credentials to compromise individual accounts or pivot deeper into a network. This containment capability limits the overall impact of a breach.
Enhancing Overall Security Posture
Implementing MFA across an organization's accounts and systems elevates its entire security posture. It introduces a strong, standardized layer of protection that strengthens defenses against a broad spectrum of cyber threats. This consistent application of MFA reduces the attack surface and fortifies access controls. Organizations demonstrate a proactive commitment to security by making MFA a foundational requirement.
Meeting Compliance and Regulatory Requirements
Many industry regulations and compliance frameworks now mandate or strongly recommend multifactor authentication for accessing sensitive data. Regulations like HIPAA, PCI DSS, GDPR, and various government mandates often specify MFA as a critical control. Adopting MFA helps organizations meet these stringent requirements, avoid penalties, and build trust with customers and partners. It also demonstrates due diligence in protecting sensitive information.
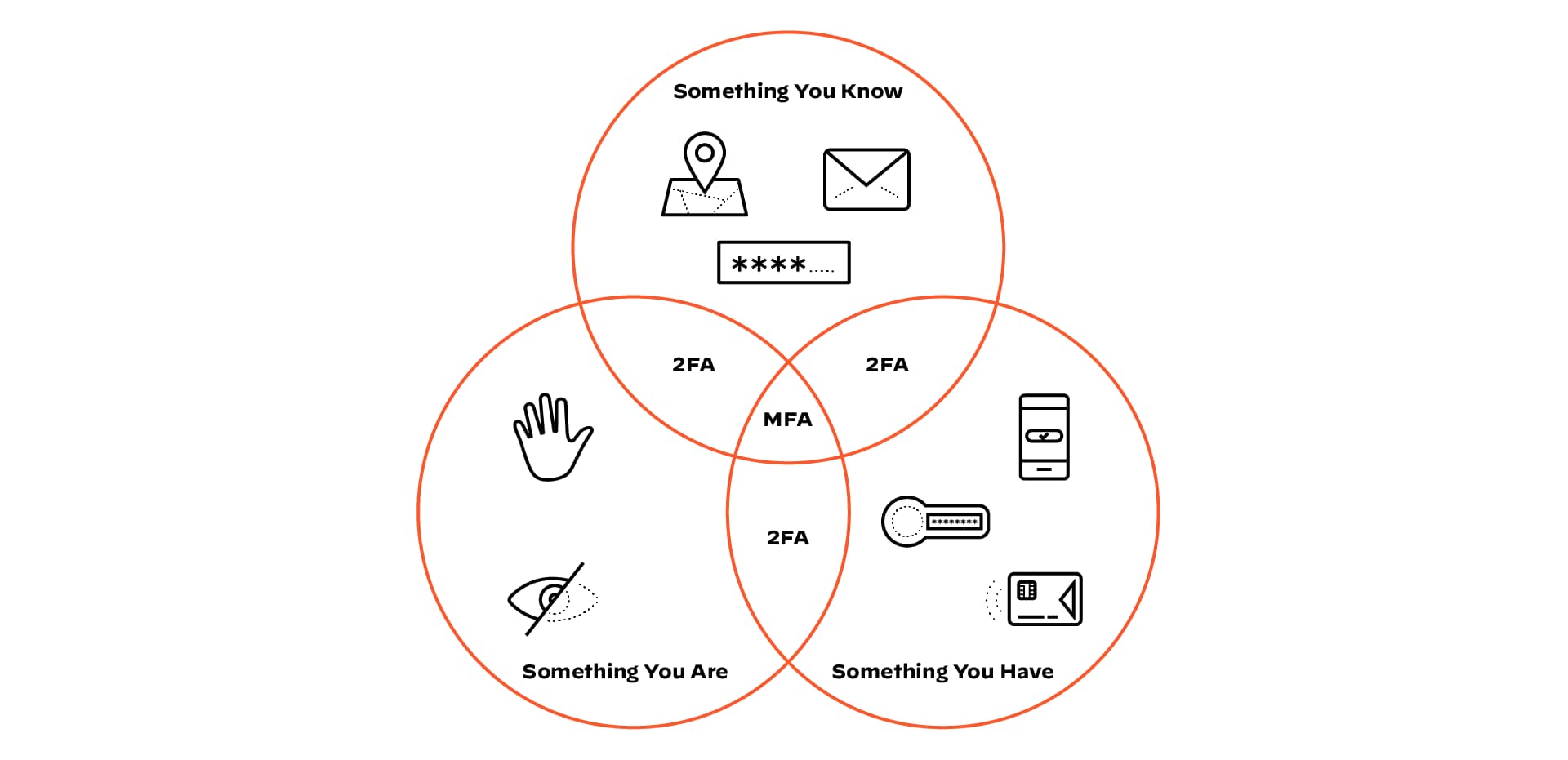
Figure 2: Different verification methods are categorized as Something You Know, Something You Are and Something You Have
How Multifactor Authentication Works
MFA functions by requiring a user to present a combination of independent verification methods from different categories, confirming their identity through diverse channels.
The Three Authentication Factor Categories
MFA relies on at least two distinct authentication factors, each belonging to a different category, to verify a user’s identity. This layering of disparate factors ensures that compromising one doesn't automatically compromise the others. These three categories form the foundation of strong authentication.
Something You Know (Knowledge Factor)
This category includes information only the legitimate user should possess, such as a password, PIN, or security questions. Knowledge factors are the most common and vulnerable to guessing, cracking, or phishing. While often the first factor, they require reinforcement from other categories for true MFA.
Something You Have (Possession Factor)
Possession factors involve a physical item that only the authorized user holds, like a smartphone running an authenticator app, a hardware security key, or a smart card. This factor proves possession of a specific device. Attackers typically need to steal the device to compromise this factor physically.
Something You Are (Inherence Factor)
Inherent factors are unique biological attributes of the user, such as fingerprints, facial scans, iris scans, or voice patterns. These biometric identifiers are difficult to replicate and provide a high level of assurance. Biometric data often undergoes cryptographic hashing or encryption for storage, never revealing the raw biometric itself.
The Authentication Flow
The system initiates an MFA challenge when a user attempts to access a protected resource. First, it prompts for the primary factor, typically a password. Upon successfully verifying the first factor, the system then requests verification of the second, distinct factor. Only after both factors are successfully validated does the system grant access to the user.
Session Management and Re-authentication
After initial MFA validation, systems often establish a secure session, allowing users to access resources for a defined period without constant re-authentication. However, security policies may require re-authentication for sensitive actions or after a certain time limit.
This ensures continued protection, even if a session becomes compromised or prolonged inactivity occurs. Organizations configure session timeouts based on risk tolerance and compliance needs.
Authentication Factors and Methods
MFA Method |
Security Level |
User Convenience |
Cost |
Vulnerability to Common Attacks |
Deployment Complexity |
|---|---|---|---|---|---|
Hardware Security Keys (e.g., FIDO2) |
Phishing Resistant |
Moderate |
Medium-High |
Very Low (resistant to phishing, MiTM, SIM swap) |
Moderate |
Authenticator Apps (TOTP) |
High |
High |
Low |
Low (resistant to phishing, SIM swap) |
Simple |
Push Notifications |
Moderate-High |
High |
Low |
Moderate (MFA fatigue, accidental approval) |
Simple |
Biometrics |
High |
Very High |
Medium |
Low (spoofing attempts, but improving liveness detection) |
Moderate |
SMS OTP |
Low |
High |
Low |
High (SIM swap, interception, phishing) |
Simple |
Email OTP |
Very Low |
Moderate |
Low |
Very High (email account compromise, phishing) |
Simple |
A variety of authentication factors and methods exist, each offering different levels of security, convenience, and deployment considerations for organizations.
Organizations can select from numerous MFA methods, each leveraging one or more of the "something you know, have, or are" factors. The choice of method often balances security strength with user convenience and organizational cost. Evaluating the specific threat model helps determine the most appropriate methods for different user groups or applications.
Password/PIN and One-Time Passwords (OTP)
Password/PIN and OTP combine a static secret—the password or PIN—with a dynamically generated one-time password (OTP). OTPs are temporary, valid for a single login session, or expire after a short time. They are typically generated via algorithms like HMAC-based One-Time Password (HOTP) or Time-based One-Time Password (TOTP) through authenticator apps.
Hardware Security Tokens (FIDO2, U2F)
Hardware tokens are physical devices that generate codes or respond to cryptographic challenges. FIDO2 (Fast Identity Online 2) and U2F (Universal 2nd Factor) keys represent a highly secure form of possession factor. These keys leverage public-key cryptography to resist phishing and man-in-the-middle attacks, as they cryptographically verify the origin of the login request. Users simply insert the key into a USB port or tap it to a device.
Software Authenticator Apps (TOTP)
Authenticator apps like Google Authenticator or Microsoft Authenticator generate time-based one-time passwords (TOTP) directly on a user's smartphone. These apps provide a convenient and generally secure possession factor. They do not rely on cellular networks, making them resilient to SIM-swapping attacks. Users simply type the rotating code into the login prompt.
Biometric Authentication (Fingerprint, Facial, Voice)
Biometric methods verify identity based on unique physical or behavioral characteristics of the user. Fingerprint scans, facial recognition, and voice biometrics offer a convenient and intuitive identification factor. While highly convenient, the irreversibility of biometric data necessitates robust security measures for its storage and processing. These methods often pair with a knowledge factor or possession factor for true MFA.
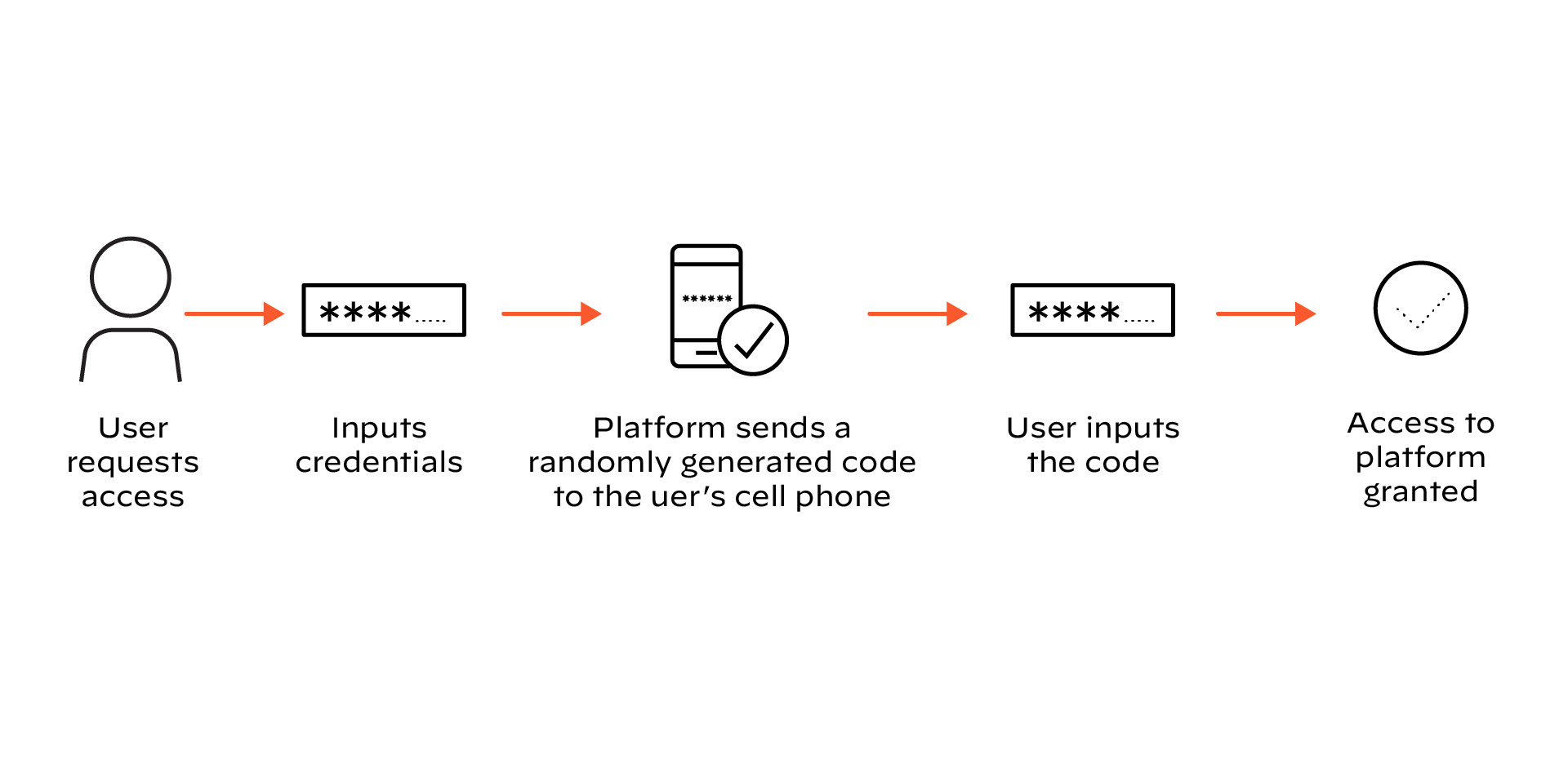
Figure 3: An example of out-of-band authentication through a companion app
Push Notifications
Push notification-based MFA sends a login approval request directly to a registered mobile device. The user simply taps "Approve" or "Deny" within the notification. This method offers high convenience and a strong user experience. However, it can be susceptible to "MFA fatigue" attacks, where attackers bombard users with notifications, hoping for an accidental approval.
SMS and Email-Based Codes
These methods deliver a one-time code to a user's registered phone number via SMS or email. While widely adopted due to ease of implementation, they represent weaker possession factors. SMS is vulnerable to SIM-swapping attacks and interception, while email can be compromised through account takeover. Organizations should consider stronger alternatives where possible.
Strengths and Weaknesses of Each Method
Each MFA method presents a unique balance of security, usability, and cost. Hardware tokens and biometric-backed FIDO2 keys generally offer the highest security against phishing and sophisticated attacks. Software authenticator apps provide a good balance of security and convenience. Conversely, SMS and email OTPs are the least secure due to their susceptibility to interception or social engineering.
When selecting MFA methods, organizations must carefully weigh these characteristics against their specific risk profile and user population. A layered approach, offering different strategies for different risk levels, often proves most effective. Prioritizing phishing-resistant options for critical accounts significantly enhances security.
Selecting the Right Factor for Specific Use Cases
Choosing the appropriate MFA factor depends on the specific use case, data sensitivity, and the application or system's threat model. For high-value accounts, such as administrative access, strong, phishing-resistant methods like FIDO2 security keys are paramount. For general user access to less critical applications, authenticator apps or even push notifications might suffice. Consider user convenience against the required level of assurance.
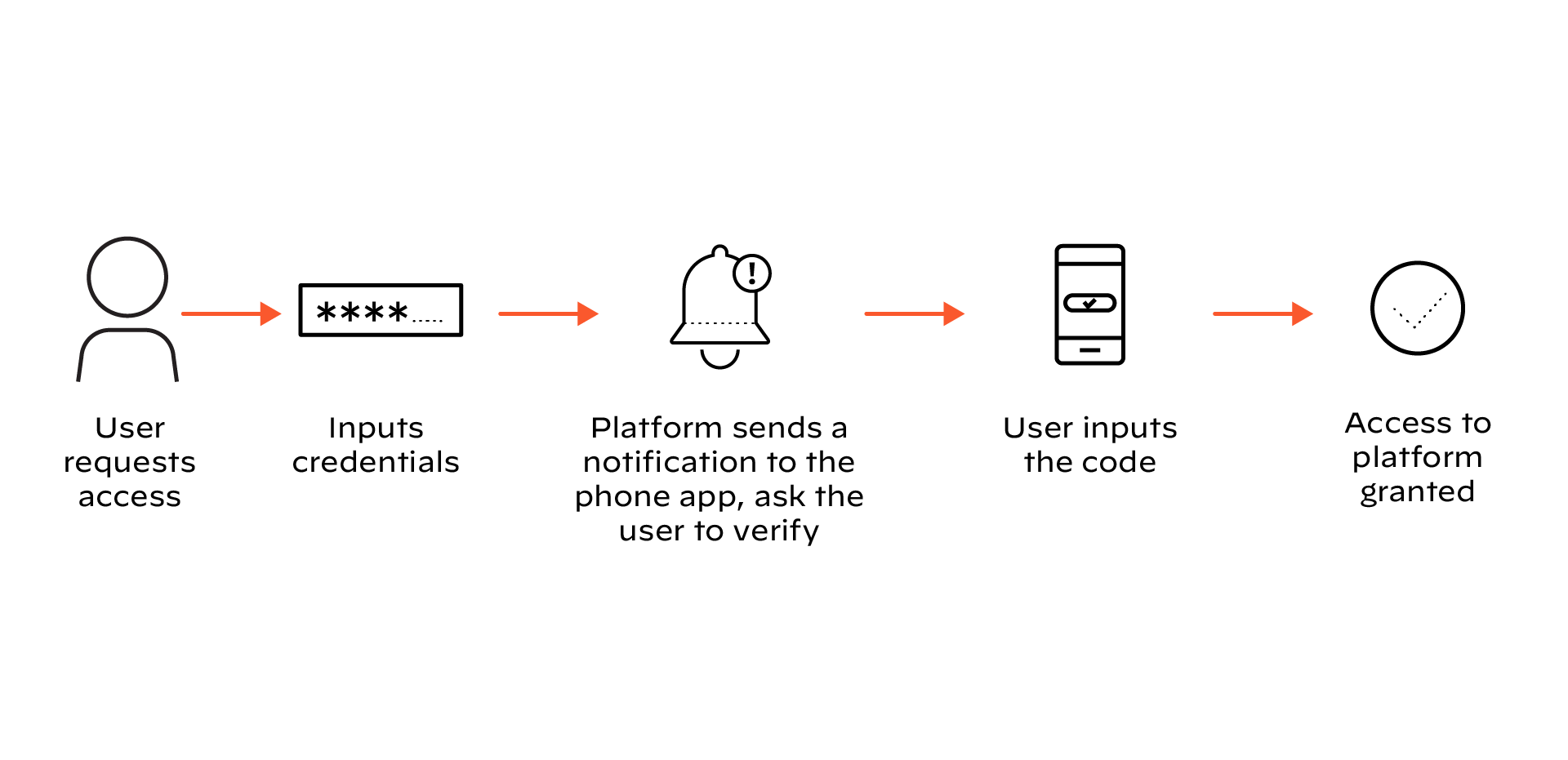
Figure 4: An example of two-factor authentication
MFA vs. Two-Factor Authentication (2FA)
While often used interchangeably, multifactor authentication is a broader category encompassing two-factor authentication, distinguishing itself by the number and distinctness of the authentication factors used.
Defining 2FA: A Specific Subset of MFA
Two-factor authentication (2FA) requires two distinct authentication factors from different categories. For example, a password (something you know) combined with an OTP from an authenticator app (something you have) constitutes 2FA. All 2FA implementations are by definition MFA, but not all MFA implementations are 2FA—MFA can involve three or more factors.
The Nuance of "Factors" vs. "Methods"
The distinction between "factors" and "methods" is important. A single authentication method might involve multiple factors, or multiple methods might rely on the same underlying factor category. MFA emphasizes using multiple factors from different categories, ensuring independent verification. For instance, requiring two different passwords would not constitute MFA, as both are "something you know" factors.
When 2FA Suffices and When MFA is Necessary
For many common applications and user accounts, 2FA provides a substantial security upgrade over single-factor authentication. It effectively blocks the vast majority of automated and opportunistic attacks. However, for highly sensitive systems, privileged access accounts, or environments facing advanced persistent threats, true multifactor authentication with three or more distinct factors can provide an even higher level of assurance. Organizations must assess their risk appetite.
Implementing Multifactor Authentication: Best Practices
Successful MFA deployment involves careful planning, technical integration, and a strong focus on user adoption and ongoing management to maximize security benefits.
Strategic Planning and Assessment
Before deploying any MFA solution, organizations must conduct a thorough strategic planning and assessment phase. This initial work lays the groundwork for a successful and secure implementation. Proper planning ensures the chosen solution aligns with business needs and security objectives.
Identifying Critical Assets
Organizations must first identify their most critical assets, including sensitive data, key applications, and privileged accounts. These assets typically require the strongest MFA methods and should be prioritized for rollout. Understanding which assets are high-value guides the strength of authentication required.
Risk Assessment and Policy Definition
A comprehensive risk assessment helps determine the specific threats MFA aims to mitigate and informs policy development. Define clear MFA policies outlining who needs MFA, for which resources, and which methods are permissible. Policies should balance security requirements with usability needs.
Phased Rollout Approaches
Implementing MFA across an entire organization at once can prove disruptive and complex. A phased rollout approach, starting with a pilot group or high-risk users, allows for testing, adjustments, and user feedback. This incremental deployment minimizes friction and enhances the overall success rate. Gradual expansion to broader user groups helps manage change effectively.
Technical Integration and Configuration
Seamless technical integration of the MFA solution with existing identity systems and applications is paramount. Proper configuration ensures MFA functions correctly and enhances the user experience. Technical teams must account for compatibility and scalability.
Identity Provider (IdP) Integration
Integrate MFA directly with your organization's primary Identity Provider (IdP), such as Azure Active Directory, Okta, or Ping Identity. Centralizing MFA through the IdP ensures consistent enforcement across all connected applications and simplifies user management. This consolidates authentication logic.
Application-Specific MFA
For applications that don't integrate directly with the central IdP, configure MFA on an application-specific basis. This often involves using built-in MFA features within the application or deploying an MFA proxy. Ensure consistency where possible to avoid user confusion.
Leveraging Conditional Access Policies
Implement conditional access policies to dynamically enforce MFA based on context—like user location, device health, or access attempts from suspicious IPs. These policies allow for granular control, prompting MFA only when the risk warrants it. This balances security with user convenience.
User Enrollment and Training
User adoption is critical for MFA success; therefore, a streamlined enrollment process and comprehensive training are essential. Users must understand how to enroll and why MFA benefits them. Effective communication fosters a positive reception.
Streamlining the Enrollment Process
Make the MFA enrollment process as simple and intuitive as possible. Provide clear, step-by-step instructions and offer self-service options. A complex enrollment flow can lead to user frustration and low adoption rates. Automate enrollment where feasible.
Educating Users on MFA Importance and Usage
Conduct thorough training sessions and provide clear documentation explaining why MFA is necessary and how to use it effectively. Emphasize the security benefits to individual users and the organization. Address common questions and concerns proactively. Reinforce the message through various communication channels.
Providing Robust Support Channels
Establish clear and accessible support channels for users encountering MFA issues. Quick resolution of problems ensures user confidence and prevents workaround behaviors. A dedicated help desk or accessible IT support team is crucial for success.
Ongoing Monitoring and Auditing
MFA implementation is not a one-time task; ongoing monitoring, auditing, and refinement are necessary to maintain its effectiveness. Regular review identifies potential weaknesses and ensures continuous security improvement. This proactive approach adapts to evolving threats.
Logging and Alerting for Anomalous Activity
Configure logging to capture all MFA events and integrate these logs with your Security Information and Event Management (SIEM) system. Set up alerts for anomalous MFA activity—such as numerous failed attempts, login attempts from unusual locations, or MFA fatigue attempts. Prompt detection allows for rapid response.
Regular Review of MFA Policies
Periodically review and update MFA policies to reflect changes in organizational risk, new threats, or the availability of more secure MFA methods. Adjust policies as the organization evolves and technology advances. This iterative process ensures continued relevance.
Incident Response Planning for MFA Bypasses
Develop and practice incident response plans specifically for scenarios where MFA might be bypassed or compromised. Knowing how to react quickly minimizes potential damage. Include procedures for account lockout, credential rotation, and user notification.
MFA Deployment Considerations
Organizations must choose deployment models that align with their existing infrastructure, security requirements, and operational capabilities, whether cloud-based, on-premises, or hybrid.
On-Premises MFA Solutions
On-premises MFA solutions involve deploying and managing the MFA infrastructure within an organization's own data center. This model offers maximum control over data and configuration, often appealing to organizations with strict compliance requirements or legacy systems. It typically demands significant upfront investment in hardware, software, and dedicated IT resources.
Cloud-Based MFA Services
Cloud-based MFA services, delivered by third-party providers, offer a flexible and scalable alternative. These services offload infrastructure management and maintenance to the vendor, reducing operational overhead for the organization. They often provide rapid deployment, automatic updates, and pay-as-you-go pricing models. Integration typically occurs via standard protocols like SAML or OpenID Connect.
Hybrid MFA Architectures
Many large enterprises adopt a hybrid MFA architecture, combining elements of both on-premises and cloud solutions. This approach allows organizations to secure sensitive on-premises applications with existing infrastructure while leveraging cloud MFA for SaaS applications and remote users. A hybrid model offers flexibility, balancing control with scalability and ease of use. It requires careful planning for seamless integration and consistent policy enforcement.
Integration with Existing Identity Systems (Active Directory, LDAP)
Regardless of the deployment model, seamless integration with existing identity management systems like Active Directory or LDAP is crucial. This integration synchronizes user identities, simplifies provisioning, and ensures a consistent authentication experience. It avoids the creation of disparate identity silos and streamlines administration. Choose MFA solutions that natively support your current IdP.
Scalability and Performance Requirements
Consider the scalability and performance requirements of the MFA solution. The system must handle the organization's current user base and accommodate future growth without degradation in performance or user experience. Assess the solution's ability to process concurrent authentication requests efficiently. Latency during login can frustrate users.
Common MFA Security Weaknesses and Mitigations
Despite its strength, MFA is not infallible; specific attack vectors and user-related challenges can compromise its effectiveness, requiring proactive mitigation strategies.
Phishing and Adversary-in-the-Middle (AiTM) Attacks
Traditional MFA methods, particularly those relying on codes or push notifications, can still fall victim to sophisticated phishing and adversary-in-the-middle (AiTM) attacks.
In an AiTM attack, attackers set up a proxy website that intercepts credentials and MFA codes in real-time. They pass these stolen details to the legitimate login page, effectively bypassing MFA. Users unknowingly enter their credentials and approve the MFA request on the attacker's proxy.
MFA Fatigue/Bombing Attacks
MFA fatigue, also known as MFA bombing, involves attackers repeatedly sending MFA push notifications to a user's device. They hope the user will eventually approve a request out of annoyance, distraction, or confusion. This social engineering tactic preys on human error rather than technical vulnerability. It can be particularly effective against users who are not well-trained or are under pressure.
SIM Swapping
SIM swapping attacks involve an attacker convincing a mobile carrier to transfer a victim's phone number to a new SIM card controlled by the attacker. Once successful, the attacker receives all SMS messages and phone calls intended for the victim, including SMS-based MFA codes. This bypasses any MFA relying on SMS or voice calls. It highlights the inherent weakness of SMS for authentication.
Session Hijacking and Cookie Theft
After a user successfully authenticates with MFA, a session cookie is typically issued, allowing continued access without re-authentication. Attackers who steal this session cookie can bypass MFA entirely, as they inherit the authenticated session. This can occur through malware, cross-site scripting (XSS), or insecure Wi-Fi networks. MFA protects the initial login, but not necessarily the session itself.
Weak MFA Methods (e.g., SMS OTP Vulnerabilities)
Some MFA methods, like SMS-based one-time passwords (OTPs) and email-based codes, inherently possess lower security. Their reliance on cellular networks or email systems introduces vulnerabilities beyond the control of the user or organization. These methods are more susceptible to interception, social engineering, or compromise of the underlying delivery mechanism. Organizations should phase out these weaker methods.
Mitigating Vulnerabilities with Phishing-Resistant MFA
The most effective mitigation against many MFA bypass techniques involves adopting phishing-resistant MFA methods. Standards like FIDO2 (e.g., security keys like YubiKeys) use public-key cryptography, cryptographically binding the authentication to the legitimate site.
These methods ensure that even if a user is tricked into visiting a phishing site, the security key will not authenticate to an incorrect domain, thus preventing the bypass. Organizations should prioritize these stronger methods, especially for high-risk accounts.
MFA Policy, User Experience, and Compliance
Effective MFA implementation balances stringent security policies with a positive user experience, all while adhering to relevant industry regulations and compliance frameworks.
Crafting Resilient MFA Policies
Well-defined MFA policies are the backbone of a successful security strategy, outlining who needs MFA, for what resources, and under what conditions. These policies must be clear, enforceable, and adaptable to changing security landscapes. They form the basis for automated enforcement.
Granular Access Control and Contextual Policies
Implement granular access control to enforce MFA based on specific user roles, resource sensitivity, and contextual factors. Use policies that trigger MFA when a user attempts to access highly sensitive data or logs in from an unknown device or suspicious location. This allows for flexible security.
Managing Exceptions and Edge Cases
While aiming for universal MFA adoption, organizations often encounter legitimate exceptions or edge cases. Establish clear, documented processes for managing these exceptions, ensuring they undergo proper risk assessment and approval. Avoid widespread exemptions that could weaken the overall security posture. Each exception should be logged and periodically reviewed.
Enhancing User Experience (UX)
User experience significantly influences MFA adoption and compliance. A cumbersome or frustrating MFA process can lead to user workarounds or complaints. Strive for a balance between strong security and seamless usability.
Minimizing Friction and Complexity
Design the MFA process to minimize friction and complexity for end-users. Opt for methods that are intuitive and quick to use, such as push notifications or biometrics. Avoid overly complicated enrollment or frequent, unnecessary challenges. A smooth experience encourages compliance.
Self-Service Options for Account Recovery
Provide comprehensive self-service options for MFA account recovery. Users should be able to reset their MFA device or recover access independently, reducing reliance on IT support. Secure recovery mechanisms, like backup codes or trusted device verification, are crucial. This empowers users and reduces administrative overhead.
The Role of Passwordless Authentication
Passwordless authentication is an emerging trend that significantly enhances user experience while maintaining strong security. Methods like FIDO2 keys or Windows Hello eliminate the need for traditional passwords, replacing them with a single, phishing-resistant MFA factor. This removes a major source of user frustration and a common attack vector.
Regulatory and Industry Compliance
Adhering to various regulatory and industry-specific compliance standards is a critical driver for MFA adoption in many organizations. MFA helps demonstrate due diligence in protecting sensitive information. Compliance often carries significant legal and financial implications.
Meeting Standards (e.g., NIST, ISO 27001)
Implement MFA to meet widely recognized security standards like NIST (National Institute of Standards and Technology) guidelines and ISO 27001 (Information Security Management Systems). These frameworks often prescribe strong authentication controls as part of their comprehensive security requirements. Aligning with these standards helps validate an organization's security posture.
Industry-Specific Regulations (e.g., HIPAA, PCI DSS, GDPR)
Many industries have specific regulations that mandate or strongly recommend MFA. HIPAA (Health Insurance Portability and Accountability Act) for healthcare, PCI DSS (Payment Card Industry Data Security Standard) for credit card data, and GDPR (General Data Protection Regulation) for personal data all require or suggest strong authentication. MFA helps organizations achieve and maintain compliance.
Audit Trails and Reporting for Compliance
Ensure your MFA solution generates comprehensive audit trails of all authentication events, including successful logins, failed attempts, and MFA challenges. These logs are vital for demonstrating compliance during audits and for forensic analysis in case of a security incident. Robust reporting capabilities are also essential for demonstrating adherence to regulatory requirements.
Advanced MFA Concepts: Adaptive and AI-Enhanced Authentication
Modern MFA solutions leverage advanced techniques like adaptive authentication and artificial intelligence to dynamically assess risk and enhance security without sacrificing user convenience.
Adaptive/Context-Aware MFA
Adaptive MFA, also known as risk-based authentication, dynamically adjusts the authentication requirements based on the context of a login attempt. It analyzes various risk signals to determine if additional authentication is necessary. This approach provides strong security when needed while minimizing friction for low-risk access.
Risk-Based Authentication
Risk-based authentication evaluates factors such as location, device type, network, time of day, and typical user behavior. If a login attempt deviates from the established norm, the system prompts for a second factor. For instance, a login from an unusual country would trigger an MFA challenge, even if the password is correct.
Behavioral Analytics and User Profiling
Advanced adaptive MFA solutions employ behavioral analytics to build profiles of typical user activity. They learn patterns related to login times, access locations, typing speed, and mouse movements. Any significant deviation from this learned behavior can flag a login attempt as suspicious, prompting an MFA challenge. This continuous monitoring strengthens security.
Step-Up Authentication
Step-up authentication is a key component of adaptive MFA. It means the system requests an additional, stronger authentication factor only when a user attempts to access a highly sensitive resource or perform a high-risk transaction. For example, a user might access general documents with a password, but require a FIDO2 key to access financial records. This balances convenience with security.
AI and Machine Learning in MFA
Artificial intelligence (AI) and machine learning (ML) are increasingly integrated into MFA solutions to enhance their capabilities beyond static rules. These technologies enable more intelligent risk assessment and proactive threat detection. AI-driven MFA learns and adapts to evolving threats.
Anomaly Detection
AI algorithms continuously analyze authentication data to detect anomalies that might indicate a compromise or attack. This includes spotting unusual login patterns, rapid failed attempts across multiple accounts, or attempts to bypass MFA mechanisms. Machine learning models can identify subtle deviations from normal behavior more effectively than human analysts.
Predictive Risk Scoring
Machine learning models can assign a real-time risk score to each authentication attempt. This score considers numerous data points, including historical login behavior, IP reputation, and known threat intelligence. Based on the predictive risk score, the system either allows access, prompts for MFA, or denies access outright. This proactive risk assessment optimizes security.
Automated Response to Threats
AI-powered MFA can automate responses to identified threats, such as temporarily blocking suspicious IP addresses, triggering an immediate account lockout, or escalating an alert to security teams. This rapid, automated response minimizes the window of opportunity for attackers. It reduces the manual workload on security operations centers.
Beyond Traditional MFA: Continuous Authentication
Continuous authentication represents the next evolution beyond traditional MFA. Instead of authenticating only at login, it continuously verifies the user's identity throughout their session. This involves ongoing monitoring of various signals, such as biometrics, behavioral patterns, and device characteristics. If the system detects a significant change in the user's behavior or environment, it can trigger re-authentication or restrict access.
Real-World MFA Examples
MFA secures a wide array of applications and services, from common consumer accounts to critical enterprise systems, demonstrating its practical application in various scenarios.
Consumer Applications (Online Banking, Social Media)
Millions of users encounter MFA daily when accessing their online banking portals, email accounts, or social media profiles. Banks often require an OTP sent to a registered phone or a push notification for high-value transactions. Social media platforms use MFA to protect accounts from takeover, especially if a user logs in from an unrecognized device. These implementations protect personal data and financial assets.
Enterprise Access (VPN, SaaS Applications)
Enterprises widely deploy MFA to secure access to their internal networks via Virtual Private Networks (VPNs) and cloud-based SaaS applications. Users typically authenticate with a password and then provide a second factor, such as an authenticator app code or a push notification. This ensures only authorized personnel have access to corporate resources, regardless of their location. It's a cornerstone of zero trust architectures.
Privileged Access Management (PAM)
Privileged accounts, such as administrator accounts or those with access to sensitive systems, represent prime targets for attackers. Organizations often implement stronger MFA methods, like hardware security keys, for these accounts as part of a Privileged Access Management (PAM) strategy. This adds an extra layer of defense around the most critical digital keys to the kingdom. It significantly reduces the risk of privilege escalation.
Remote Work and Hybrid Environments
The proliferation of remote and hybrid work models has made MFA indispensable. Employees accessing corporate resources from diverse locations and personal devices necessitate strong authentication. MFA ensures that only legitimate users can connect to the corporate network and cloud services, regardless of their physical presence. It forms a crucial security boundary for the modern distributed workforce.
Government and Healthcare Applications
Government agencies and healthcare providers handle highly sensitive and regulated data, making comprehensive security essential. MFA is a mandatory or highly recommended control under regulations like HIPAA and various government mandates. It protects patient records, classified information, and critical infrastructure from unauthorized access. These sectors often adopt stringent MFA requirements.
The Future of MFA: Emerging Trends and Innovations
The landscape of authentication is constantly evolving, with new technologies and approaches shaping the next generation of multifactor authentication.
Passwordless Authentication Evolution
The complete elimination of passwords represents a significant future trend in authentication. Passwordless authentication methods, such as those leveraging FIDO2 standards, biometrics, or magic links, aim to simplify the user experience while enhancing security. This shift removes the weakest link in traditional authentication—the password itself. It promises to reduce phishing and credential stuffing attacks.
Decentralized Identity and Blockchain
Decentralized identity solutions, often built on blockchain technology, offer a new paradigm for managing digital identities and authentication. Users control their own verifiable credentials, rather than relying on centralized identity providers. This approach could lead to more secure, private, and portable authentication methods. It shifts power back to the individual.
Quantum-Resistant Cryptography for Authentication
As quantum computing advances, concerns about its ability to break current cryptographic algorithms used in authentication are growing. Research and development are underway to create quantum-resistant cryptographic algorithms. Future MFA solutions will likely incorporate these new algorithms to ensure long-term security against powerful quantum attacks. This is a proactive defense.
Biometrics Advancements and Liveness Detection
Biometric authentication continues to advance, with improvements in accuracy, speed, and the integration of liveness detection. Liveness detection technologies distinguish between a live person and a spoofing attempt (e.g., a photo or mask). These advancements make biometrics an even more robust and convenient MFA factor. They address previous vulnerabilities.
The Convergence of Identity and Security
The future of MFA lies in its deeper convergence with broader identity and security frameworks, such as Zero Trust architectures and Continuous Adaptive Risk and Trust Assessment (CARTA). Authentication will become an integrated part of a holistic security strategy, dynamically adjusting access based on ongoing risk assessments. This integrated approach moves beyond isolated security controls.
Multifactor Authentication FAQs
MFA is a broad term requiring two or more independent authentication factors from different categories. 2FA is a specific subset of MFA, always requiring exactly two factors. All 2FA is MFA, but not all MFA is 2FA.
No, MFA significantly enhances security but is not foolproof. Sophisticated attack techniques like AiTM phishing, MFA fatigue, and SIM swapping can still bypass some MFA methods. Organizations must implement robust MFA methods and user education to mitigate these risks. MFA greatly reduces risk, but doesn't eliminate it.
The most secure MFA methods are generally those that are phishing-resistant, such as FIDO2-compliant hardware security keys. These methods use public-key cryptography to bind the authentication to the legitimate website, making them highly resilient to credential theft and phishing attacks. Software authenticator apps provide a good balance of security and convenience.
Account recovery procedures vary by service, but common methods include using backup codes provided during MFA setup, verifying identity through alternative means like email or security questions, or contacting support. Organizations should implement secure and user-friendly recovery processes. Always store backup codes securely.
Organizations should consider security strength, user experience, ease of integration with existing systems, scalability, cost, and compliance requirements when selecting an MFA solution. Evaluate the specific threat model and the sensitivity of the resources being protected. Phishing resistance should be a high priority.
MFA can introduce some friction into the login process, but modern solutions aim to minimize this. Methods like push notifications and biometrics offer a more seamless experience than typing codes. Organizations should balance security needs with user convenience to ensure high adoption rates. A well-implemented MFA is barely noticeable.
MFA implementation costs vary widely depending on the chosen solution, the number of users, and deployment complexity. Factors include software licenses, hardware tokens (if used), integration efforts, and ongoing management. Cloud-based services often have subscription models, while on-premises solutions involve upfront infrastructure costs.