What Is Zero Trust Network Access (ZTNA)
What Is ZTNA?
Zero Trust Network Access (ZTNA) is a category of technologies that provides secure remote access to applications and services based on defined access control policies. Unlike VPNs, which grant complete access to a LAN, ZTNA solutions default to deny, providing only the access to services the user has been explicitly granted. It is important to understand the security gaps and benefits ZTNA solutions can provide organizations as more remote users join the network.
How Does ZTNA Work?
With ZTNA, access is established after the user has been authenticated to the ZTNA service. The ZTNA service then provisions access to the application on the user’s behalf through a secure, encrypted tunnel. This provides an added layer of protection for corporate applications and services by shielding otherwise publicly visible IP addresses.
Like software-defined perimeters (SDP), ZTNA leverages the concept of a dark cloud, preventing users from seeing any applications and services that they don’t have permission to access. This introduces protection against lateral attacker movement, where a compromised endpoint or credentials would otherwise permit scanning and pivoting to other services.
ZTNA vs VPN
VPNs were designed to grant complete access to a LAN, offering a private, encrypted tunnel for remote employees to connect to the corporate network. While this may seem like a practical solution, VPN unfortunately lacks the flexibility and granularity to control and see exactly what users can do and which apps they can access. Once a user is granted access, they can access anything on the network, leading to security gaps and policy enforcement problems.
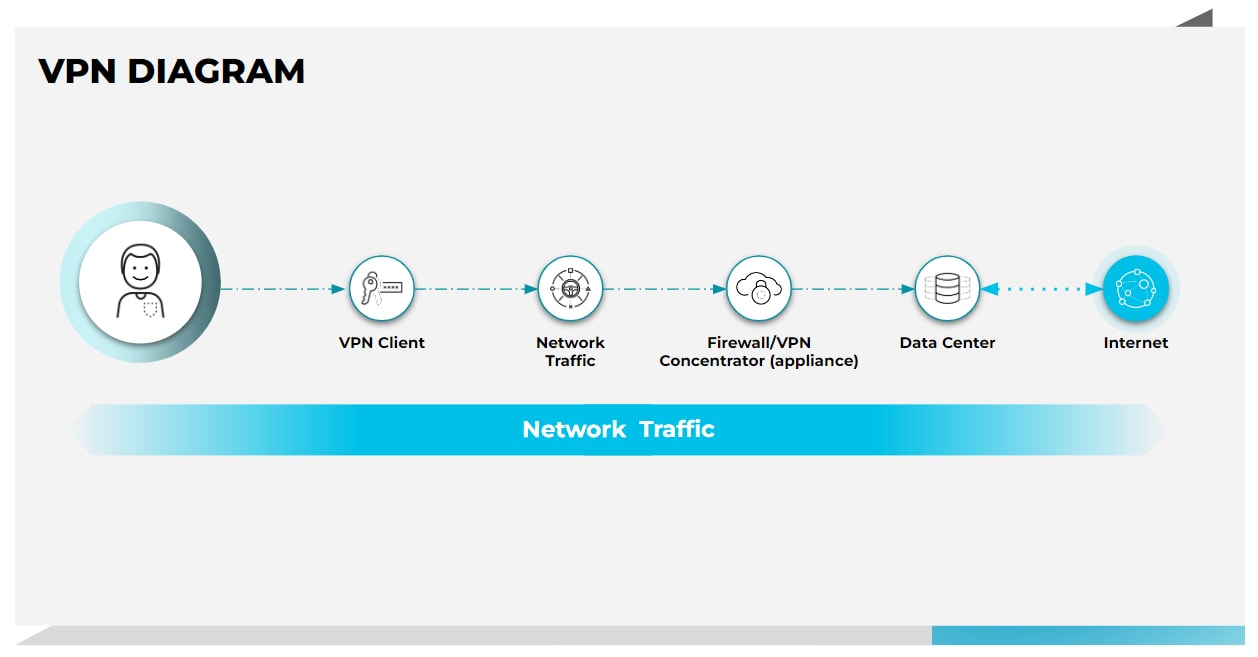
ZTNA, on the other hand, provides secure remote access to applications based on granular access control policies. It offers continuous checks on users as they connect to their apps, instead of the “once verified you are in” approach that VPNs take. Thus, ZTNA provides a “never trust, always verify” least-privelege approach, constantly vetting user, device and app behavior throughout a users session.
VPN Replacement / Secure Remote Access
A key area of focus for many organizations today is replacing outdated VPN technologies that deliver network access to their remote and hybrid workforces with a more modern ZTNA solution that overcomes performance bottlenecks and simplifies management. Typically these VPN replacement initiatives are driven by a number of factors:
- Applications started moving to a hybrid model, taking advantage of on-premises as well as cloud and multicloud environments. As such, legacy VPN technology that trombones or backhauls traffic to an on-premises “concentrator” neither scales nor delivers the best possible user experience.
- The requirements we now have for accessing enterprise apps are also changing. Traditionally users leveraged managed devices, but now we’re seeing more and more unmanaged devices also making their way onto corporate networks and requesting access to corporate applications.
- Finally, organizations want a consistent model of protection and security for all apps, not just web or legacy applications, but all apps universally.
VPN solutions were not designed for the rapid scale, high-performance and consistent delivery of advanced security services now required to securely connect hybrid users to the plethora of applications they now require to get their jobs done. Thus, organizations have started replacing outdated VPN deployments with ZTNA solutions.
Benefits of ZTNA
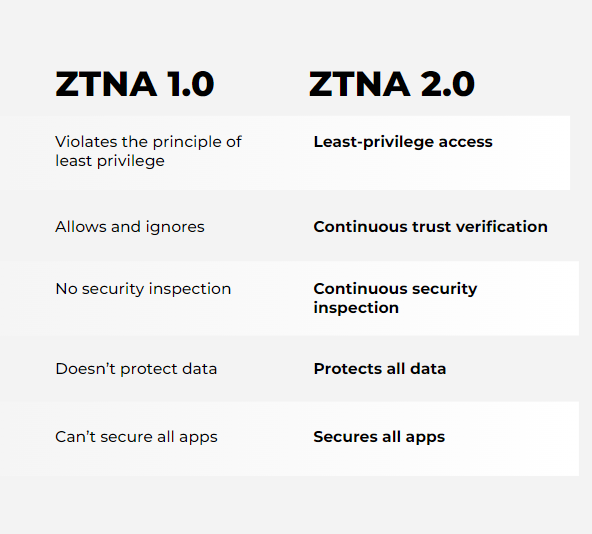
Identity-based authentication and access control found in ZTNA services provide an alternative to IP-based access control typically used with most VPN configurations which help to reduce an organization’s attack surface. ZTNA also allows organizations to implement location or device-specific access control policies to prevent unpatched or vulnerable devices from connecting to corporate services. This alleviates common VPN-related challenges where BYOD remote users are granted the same level of access as users at a corporate office, despite the fact that they often have fewer security controls in place. Some agent-based ZTNA solutions provide a pre-authentication trust assessment of the connecting user and device, including device posture, authentication status and user location. However, the rapid shift to remote and hybrid work, coupled with the rapid rise in cloud adoptions, has exposed significant gaps in initial, or 1.0, iterations of ZTNA.
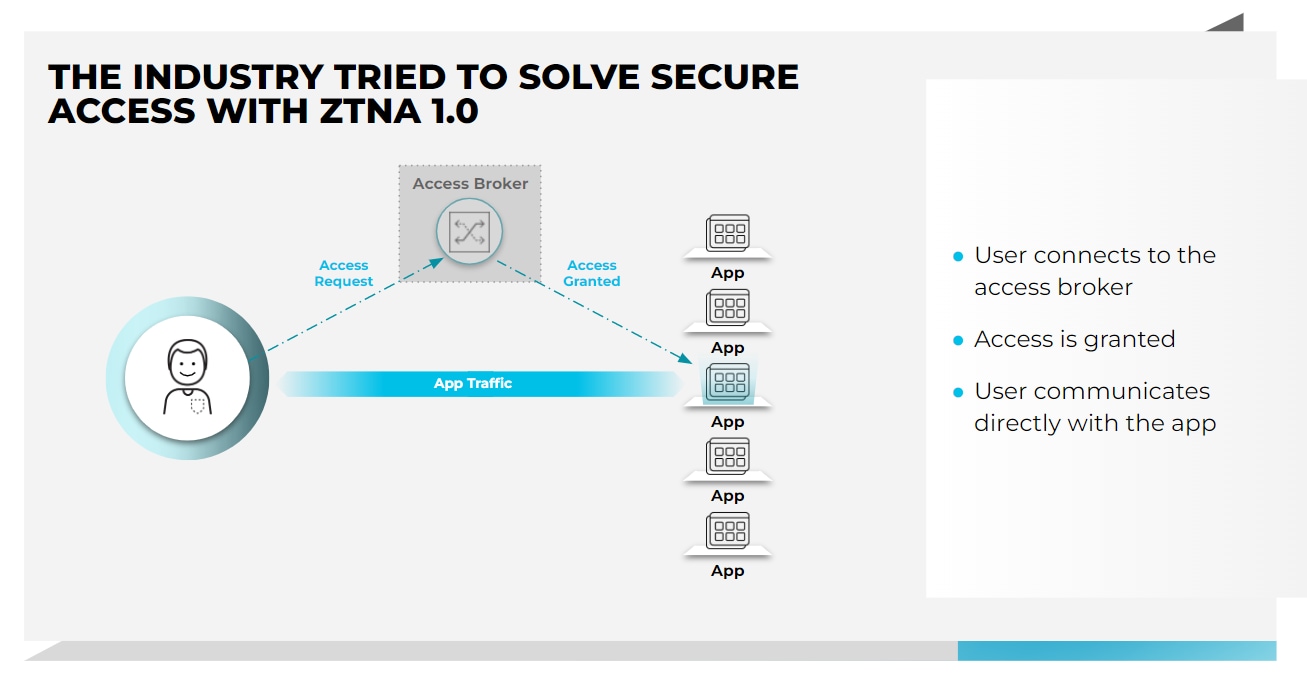
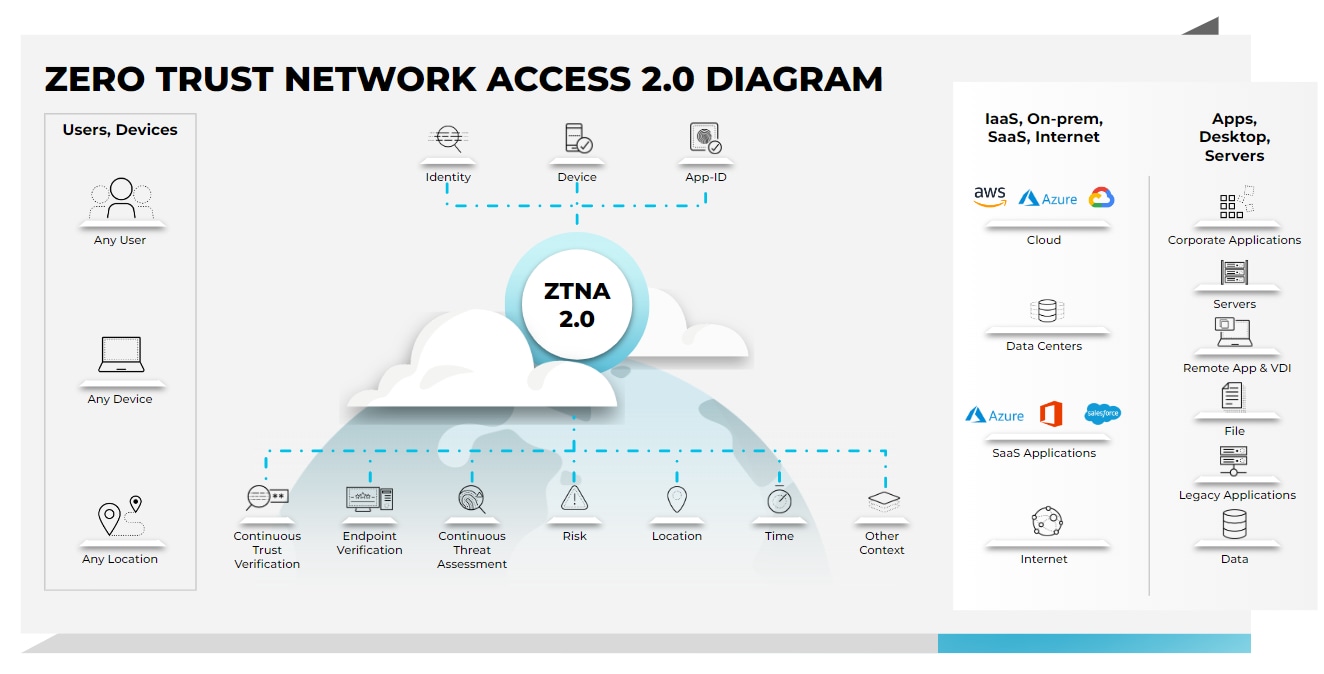
ZTNA 2.0
Zero Trust Network Access 2.0 overcomes the limitations of legacy ZTNA solutions, providing secure connections to deliver better security outcomes for businesses with hybrid workforces. ZTNA 2.0 delivers:
- True least-privileged access: Identify applications based on App-IDs at Layer 7. This enables precise access control at the app and sub-app levels, independent of network constructs like IP and port numbers.
- Continuous trust verification: Once access to an app is granted, trust is continually assessed based on changes in device posture, user behavior and app behavior. If any suspicious behavior is detected, access can be revoked in real time.
- Continuous security inspection: Deep and ongoing inspection is conducted on all traffic, even for allowed connections to prevent all threats, including zero-day threats. This is especially important in scenarios where legitimate user credentials are stolen and used to launch attacks against applications or infrastructure.
- Protect all data: Consistent control of data is applied across all apps used in the enterprise, including private apps and SaaS, with a single DLP policy.
- Secure all apps: Consistently secures all applications used across the enterprise, including modern cloud native apps, legacy private apps and SaaS apps as well as apps that use dynamic ports and those that leverage server-initiated connections.
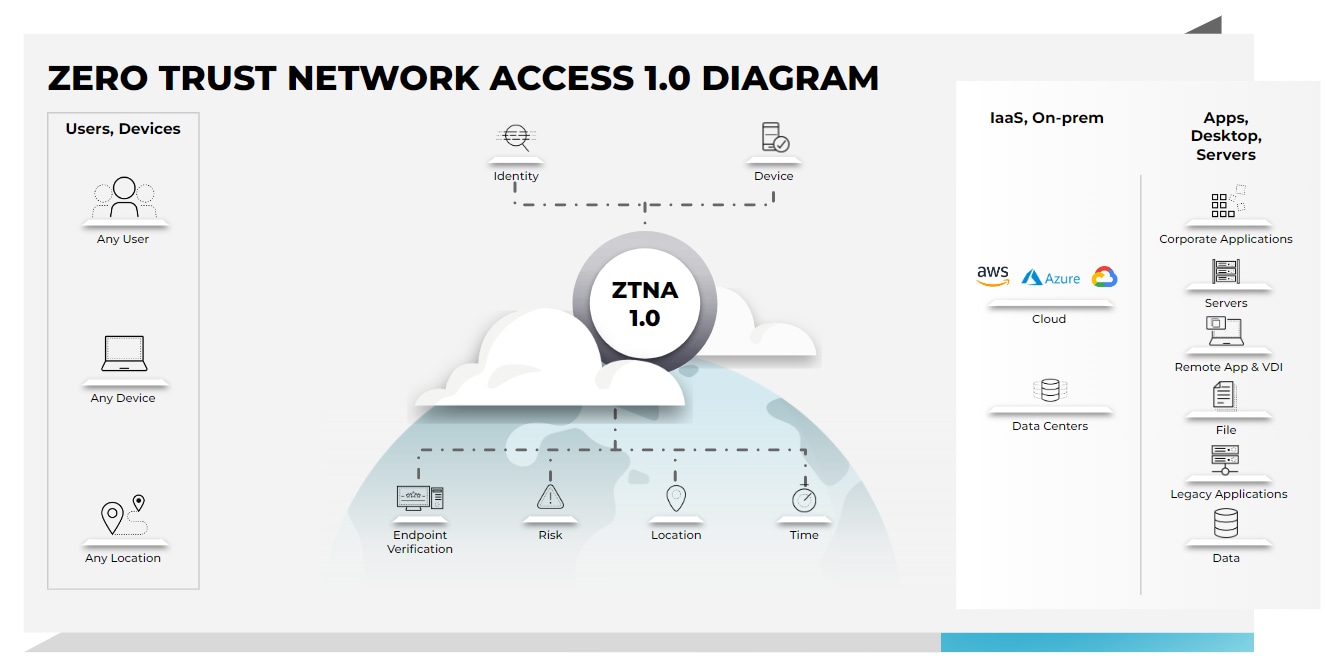
ZTNA 1.0 vs. ZTNA 2.0
The biggest shift seen in networking and security over the past 24 months has been that work is no longer a place we go to but rather an activity we perform. Hybrid work is our new normal, which means our apps and users are now everywhere and anywhere, dramatically increasing our attack surface. In parallel, we’ve also seen an increase in the sophistication and volume of cyberattacks attempting to take advantage of this massively increased attack surface.
Current ZTNA 1.0 solutions only solve some of the problems associated with direct-to-app access. In particular, ZTNA 1.0 solutions:
ZTNA & SASE
Like SDP, however, ZTNA does not provide inline inspection of user traffic from the application after the user establishes a connection. This can lead to potential security issues when a user’s device or credentials become compromised or in the case of a malicious insider who uses their access to a resource to disrupt the application or host.
Secure access service edge (SASE) is the convergence of wide area networking, or WAN, and security services in a cloud-delivered services “edge” designed to help organization modernize their networking and security infrastructures to accommodate the needs of hybrid environments and hybrid workforces. SASE solutions consolidate multiple point products, including ZTNA, Cloud SWG, CASB, FWaaS, and SD-WAN, into a single integrated service, reducing network and security complexity while increasing organizational agility.
There are many ways to start the SASE journey, and ZTNA is one of them. Secure access service edge (SASE) solutions that incorporate ZTNA 2.0 identity-based authentication and granular access control capabilities provide a more complete, holistic approach.
Learn more about the evolution of ZTNA in this blog.
Zero Trust Network Access FAQs
ZTNA differs from traditional Virtual Private Networks (VPNs) in several ways:
- Granular Access Control: ZTNA provides more precise access controls, granting access only to specific applications or resources rather than the entire network.
- Continuous Verification: ZTNA continuously verifies the identity and security posture of users and devices, whereas VPNs typically authenticate users only at the point of connection.
- Reduced Attack Surface: ZTNA limits exposure by providing access on a need-to-know basis, minimizing the attack surface compared to VPNs, which often provide broad network access.
The key components of a ZTNA solution include:
- Identity and Access Management (IAM): Ensures proper authentication and authorization of users and devices.
- Device Security: Assesses the security posture of devices before granting access.
- Microsegmentation: Divides the network into smaller, isolated segments to limit lateral movement of threats.
- Continuous Monitoring: Monitors user and device activity to detect and respond to anomalies in real time.
- Policy Enforcement: Applies security policies consistently across all access requests and network segments.
The benefits of implementing ZTNA include:
- Enhanced Security: Provides robust protection against unauthorized access and insider threats.
- Improved Visibility: Offers comprehensive insights into user and device activities.
- Reduced Attack Surface: Limits exposure by granting access only to specific resources.
- Flexibility: Supports secure remote work by allowing users to access resources from anywhere.
- Compliance: Helps organizations meet regulatory and industry standards by enforcing strict access controls.
Organizations can transition to a Zero Trust Network Access model by following these steps:
- Assess Current Security Posture: Evaluate existing security measures and identify gaps.
- Define Security Policies: Establish clear access policies based on user roles and device security.
- Implement IAM and MFA: Deploy identity and access management solutions with multi-factor authentication.
- Deploy ZTNA Solutions: Choose and implement ZTNA technologies that fit organizational needs.
- Educate and Train: Ensure employees understand the principles and practices of Zero Trust security.
- Monitor and Adjust: Monitor network activity and adjust policies to address emerging threats.