Vulnerability management
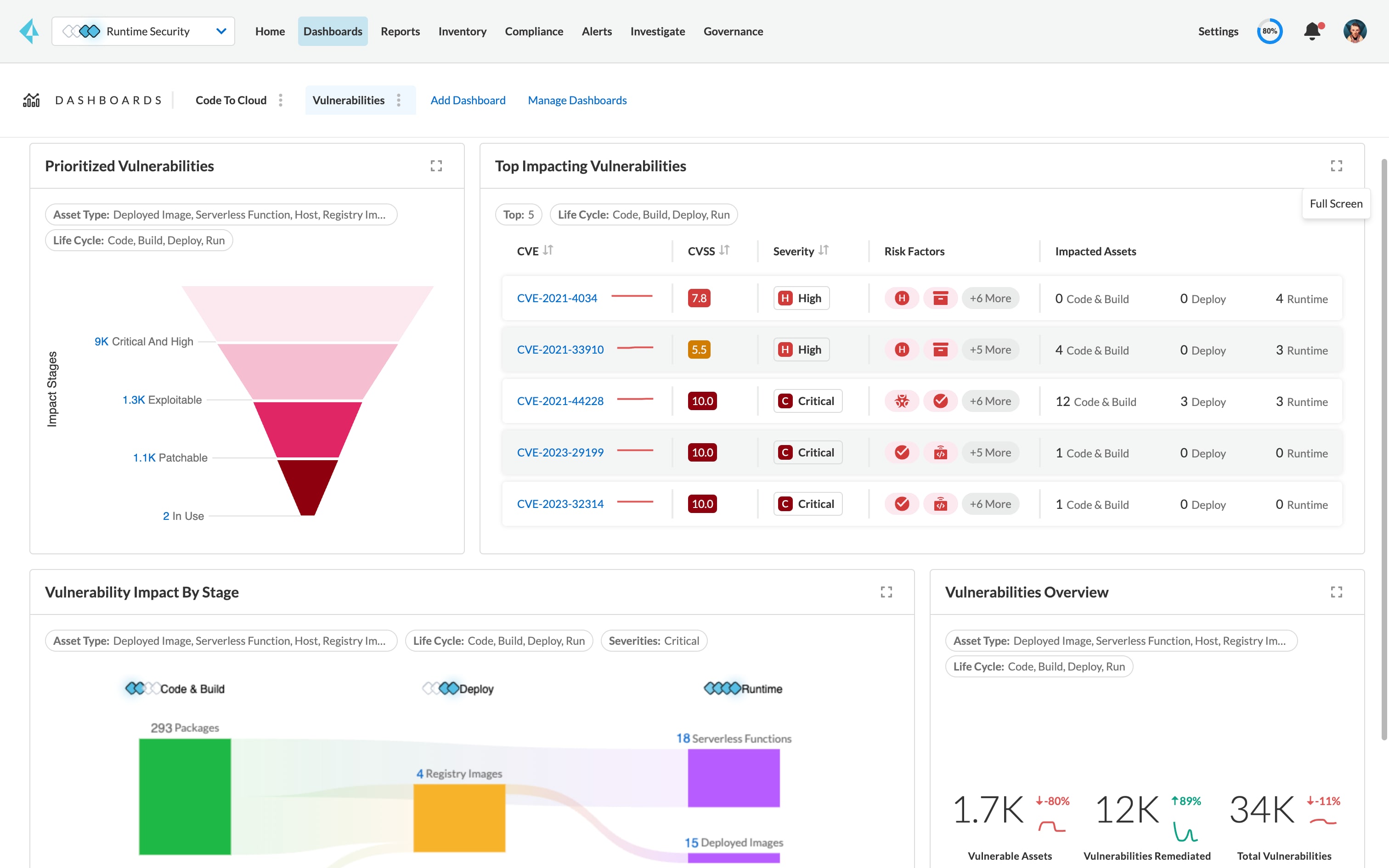
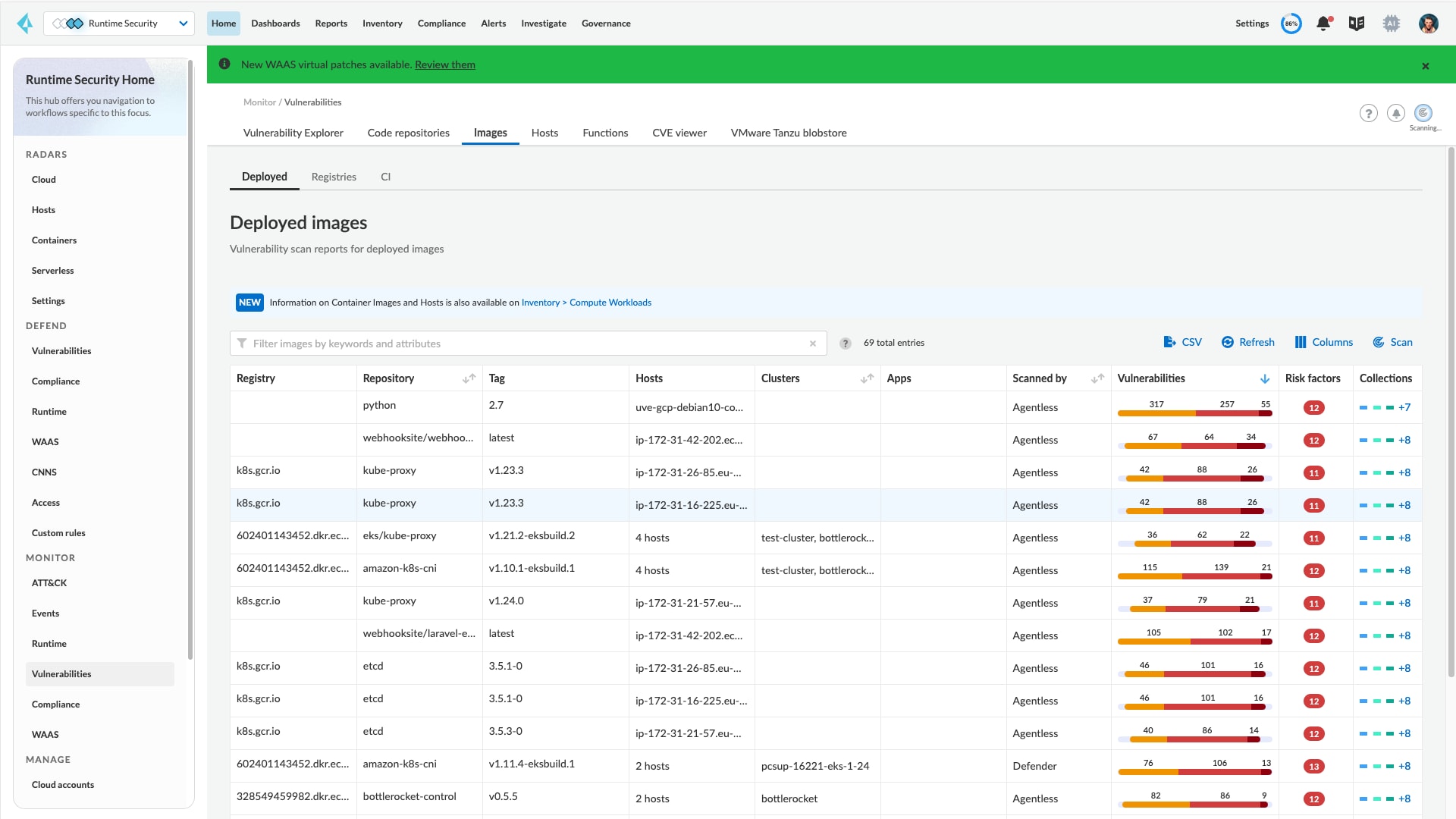
Start with full visibility into all dependencies from containers during the build, deploy and run phases. Prisma Cloud aggregates and prioritizes vulnerabilities continuously in CI/CD pipelines and containers running on hosts or on containers as a service, in public and private clouds.
Prioritize remediation with guidance:
Establish risk prioritization across all known CVEs, remediation guidance and per-layer image analysis with vulnerability Top 10 lists.
Add guardrails with alerts and blocks for severity levels:
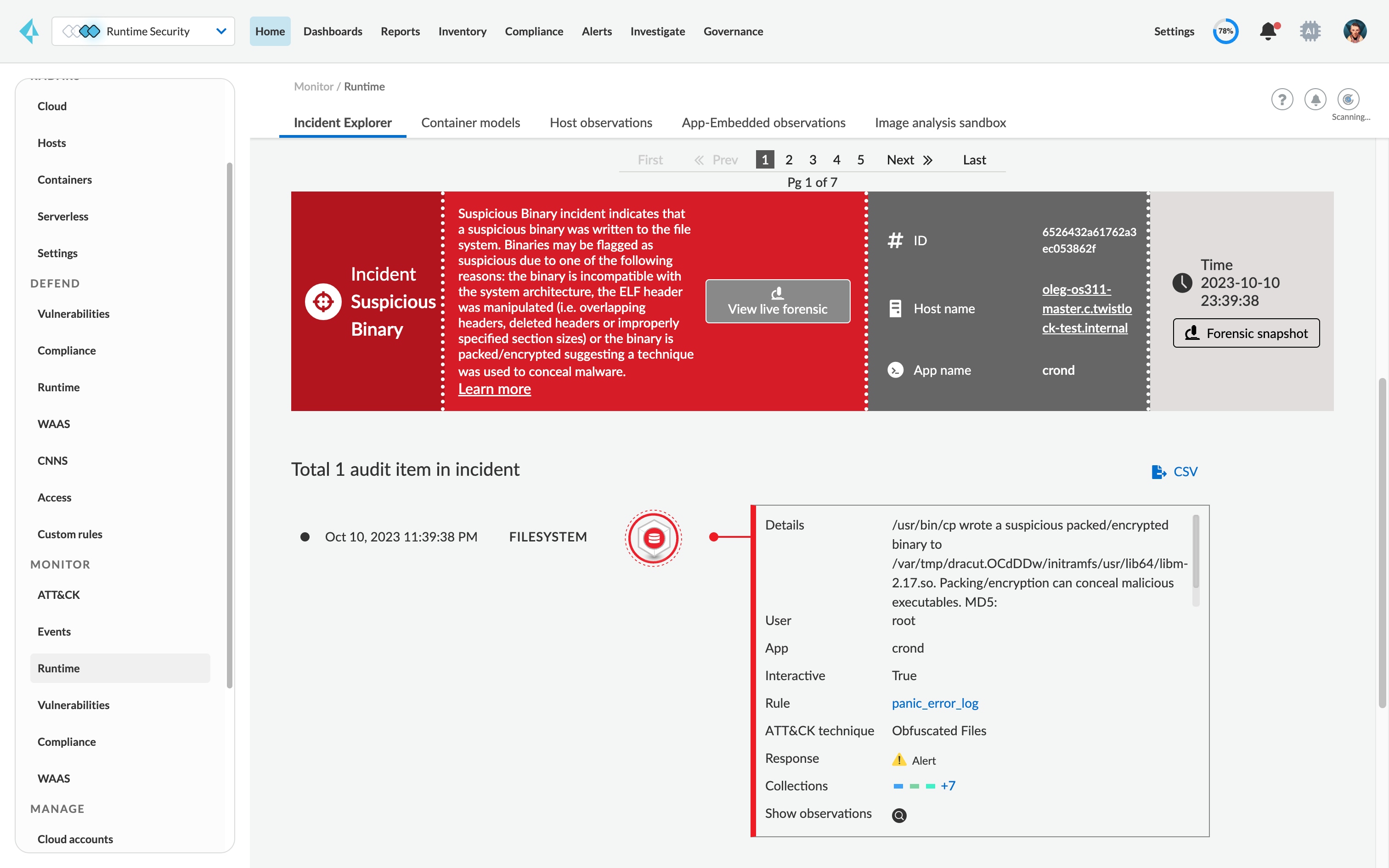
Control the alert and blocking severity level for individual and groups of services during build time and runtime.
Leverage unmatched accuracy:
Minimizing false positives with more than 30 upstream data sources. Prisma Cloud is focused on providing only accurate vulnerability information back to developers and security teams.
Surface vulnerability information throughout the lifecycle:
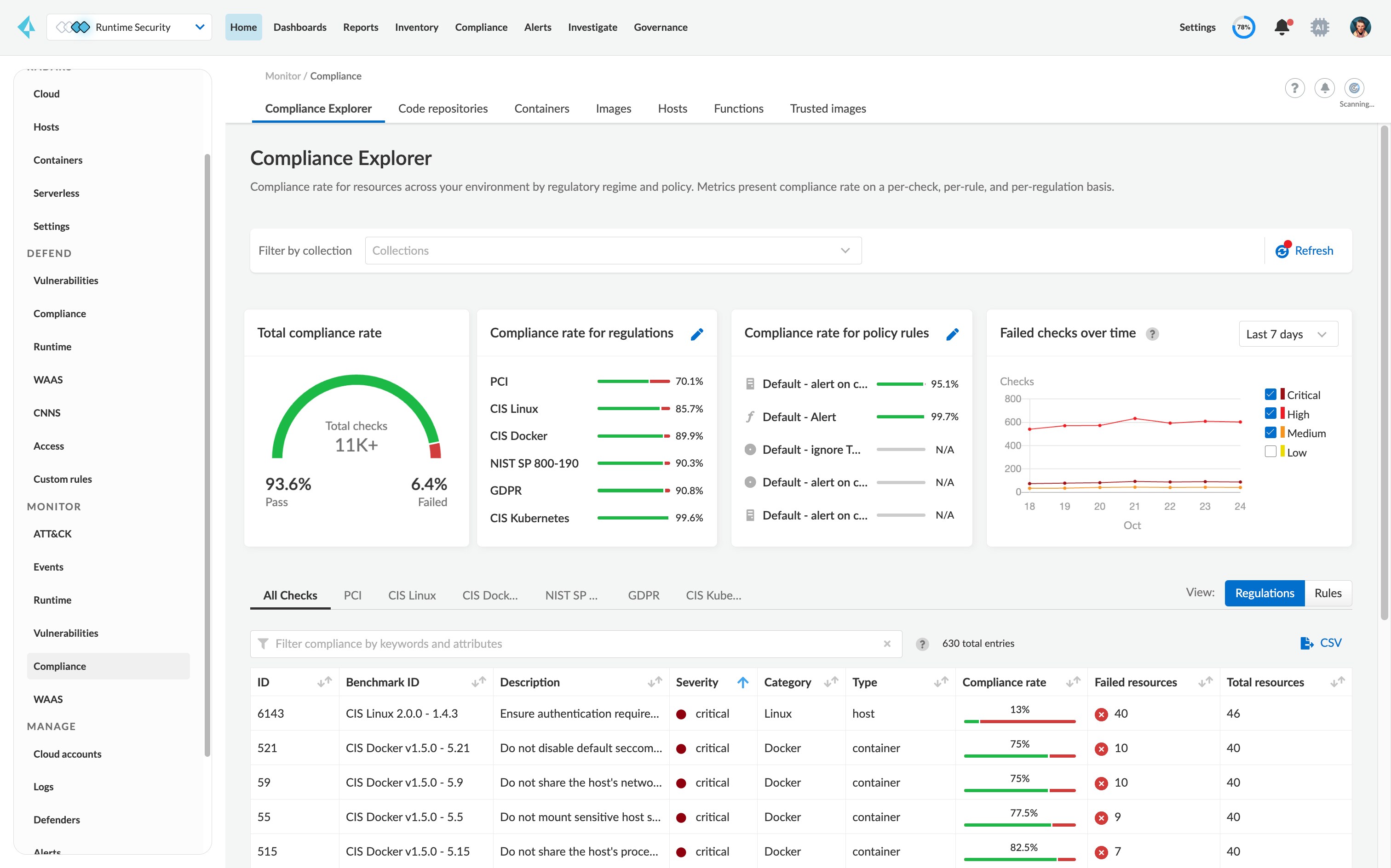
Integrate vulnerability management to scan repositories, registries, CI/CD pipelines and runtime environments.