Secure your connected, distributed environments
Thousands of oil and gas industry enterprises worldwide count on Palo Alto Networks to prevent successful cyberattacks, safeguard data and optimize operations.
Embrace the possibilities of the digital age


Oil and gas asset owners are seeing increasing digitization and integration of operational technology (OT) and third-party support networks. What’s the key to securing highly-connected and distributed IT and OT environments so you can explore new business opportunities?
The Palo Alto Networks® Security Operating Platform prevents successful cyberattacks from disrupting operational and corporate IT environments. Tight integration across the platform and with ecosystem partners delivers consistent security across cloud, network, industrial IoT and mobile devices.
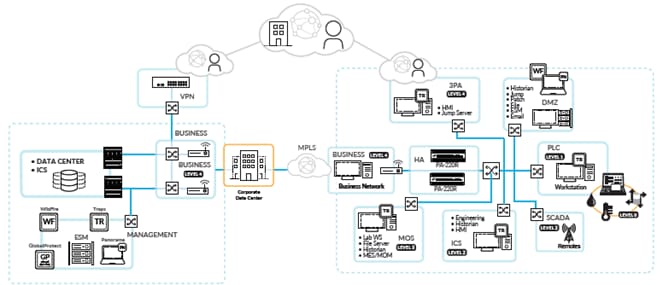
Reference Blueprint for ICS/SCADA systems
Securely modernize and integrate OT networks
Prevent successful attacks across IT and OT infrastructure
Streamline operations to reduce opex