This is the fourth in our series of cybersecurity predictions for 2016. Stay tuned for more through the end of the year.
In 2015, the cybersecurity market witnessed the introduction of a slew of new and improved products that promised to enhance the detection and response capabilities of organizations against malware. The prevailing rationale was that an improvement in these tools would help organizations to reduce the impact of malware by becoming better at spotting suspicious activity. Unfortunately, the threat agents also witnessed this trend. Their attacks became more targeted, oftentimes uniquely designed to compromise a given organization’s defenses.
The shift from executable malware to exploits will continue
In 2016, we can expect that well-funded, highly skilled, and patient threat agents will shift their focus toward deploying the types of attacks that are virtually undetectable by current antivirus solutions and much harder to counter by current “detect and respond” tools. These attacks will exploit vulnerabilities in legacy and commonly used applications that are often whitelisted or play a major role in the organization’s business processes; hence, these applications cannot be eliminated without having a negative impact on the organization’s ability to conduct business.
As threat actors become more effective in the reconnaissance of their targets, the exploits will become more highly customized to the specific applications in use by a target organization, and even to the targeted individuals within that organization.
In 2016, software developers will undoubtedly continue to improve the overall security of their applications and operating systems, while threat actors will escalate the perpetual “cops and robbers” game by deploying exploits that are more sophisticated – and often created by professional exploit developers.
Organizations will realize the futility of fighting machines with people
Cyberattacks in 2015 exhibit a massive increase in volume, velocity and variation. The fundamentally asymmetrical nature of cyberattacks, in the sense that small groups of highly skilled individuals have the potential to inflict disproportionately large amounts of damage on an organization, took a turn for the worse as attackers gained increased access to more scalable options, such as Malware-as-a-Service and Exploits-as-a-Service.
While attackers unleashed an army of machines on their targets with a click of a mouse, many organizations continued to commit their scarce resources to the perpetual loop of “detect and respond,” which is to identify, investigate, remediate, recover, and then repeat.
In 2016, we can expect that organizations will finally realize this people-intensive approach is no longer scalable or sustainable. Organizations will recognize that automation and scalability are the keys to matching the asymmetric nature of cyberattacks. And they will come to rely on new tools that can effectively prevent the army of machines from using sophisticated and previously unknown threats, malware, and exploits to compromise the organization’s defenses.
The pendulum will start to swing back from detection and response toward prevention
2015 witnessed the continuing market sentiment that security breaches are inevitable, that organizations should assume a breach has already happened, and that the best course of action is to focus scarce resources on rapid detection and response in order to minimize the impact.
Despite the proliferation of new services and products that focused on helping organizations to improve their ability to detect and respond to malicious activities, organizations will realize that these advancements cannot change the economics of their chosen approach.
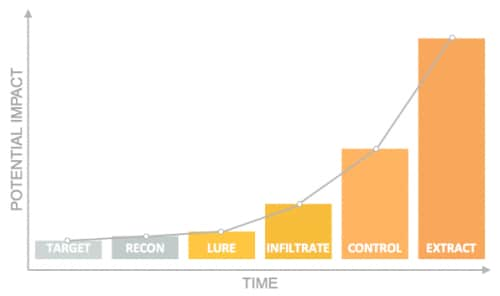
The fact remains that the further along the breach continuum one detects and intercepts an attack, the higher the negative impact, and the costlier it will be to recover and remediate.
In 2016, organizations will begin to realize that breach prevention is not only possible but also more viable and sustainable. Although detection and response capabilities will remain necessary for a balanced security posture, the old adage “an ounce of prevention is worth a pound of cure” will resonate with more and more organizations.
Want to explore more of our top 2016 cybersecurity predictions? Register now for Ignite 2016.