Palo Alto Networks is proud to announce the public release of a Python client library for interacting with our AutoFocus API.
AutoFocus was released last year to provide actionable threat intelligence and prioritized alerts for organizations by combining data collected from thousands of WildFire customers, Unit 42 threat research, and other cyber security intelligence feeds drawn from vendor and other third party partnerships.
For many of you currently subscribed to AutoFocus, previous interaction with the service may have been purely through our user interface and alert notifications. However, it is important to remember that data is also exposed via an API. After our own internal research usage of querying the API, we realized the importance of creating an object-oriented library to simplify querying the data and work with the results, which led to the creation of this library. It provides a quick way to begin interacting with the AutoFocus API without requiring a detailed understanding of the API service calls, response formats and parsing, error handling, or other steps.
Here’s how to get started with the API so you can easily integrate AutoFocus intelligence into your own systems and applications.
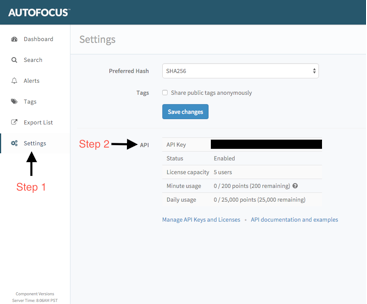
First, you will need an API key. You can find and manage your AutoFocus API key by logging in and clicking ‘Settings’ from the navigation menu.
Figure 1 Identifying your AutoFocus API key from the UI
|
1 2 |
[autofocus] apikey=<your_api_key> |
You can alternatively add your API key within any script you write rather than loading from a configuration file.
|
1 2 |
from autofocus import AutoFocusAPI AutoFocusAPI.api_key = “<your_api_key>” |
Finally, install the library and you are all set.
|
1 2 3 |
git clone https://github.com/PaloAltoNetworks/autofocus-client-library cd autofocus-client-library python setup.py install |
We will demonstrate usage through a simple but fully working Python example utilizing the client. This example will begin by querying for a specific sample using the sample’s SHA256 hash. It continues to provide information about the file, such as the file type, WildFire verdict, and DNS queries made by the sample within the WildFire sandbox. Finally, a very simplistic search is performed to identify malicious samples found within AutoFocus.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 |
from autofocus import AutoFocusAPI, AFSample, AFSampleAbsent, AFDnsActivity AutoFocusAPI.api_key = "<your_api_key>" # Query for a sample and pull DNS activity associated with it try: sample = AFSample.get("7f38fd3e55a4139d788a4475ab0a5d83bf7686a37ef5e54a65364a0d781b523c") # Print some data that's available print sample.sha256 print sample.file_type if sample.malware: print "This is a malicious file" # Extract any DNS queries seen across WildFire analysis jobs for sample for dns in sample.get_analyses(AFDnsActivity): print "Query: {0}".format(dns.query) except AFSampleAbsent: print "That sample wasn't found." # Run AutoFocus search to discover samples matching criteria # See AF documentation for query format, or export a query via UI to get started query = '{"operator": "all", "children": [{"field": "sample.malware", "operator": "is", "value": 1}]}' for sample in AFSample.search(query): print sample.sha256 |
This is a basic example, but it demonstrates the ease of using the API and working with the results. Through the library, you can also search AutoFocus session data (AFSession object) just as easily using a similar syntax. Behind the scenes, the library will handle authenticating to the web service, parsing responses into objects, creation of exceptions, and more. More examples and details on the library can be found on GitHub.
We invite you to begin using the tool to further automate your own internal processes and usage of the AutoFocus API.
For more information, please visit the AutoFocus website.