 We are proud to introduce Cortex XSOAR, an evolution of Demisto, that continues our tradition of raising the bar for the security orchestration, automation and response (SOAR) category.
We are proud to introduce Cortex XSOAR, an evolution of Demisto, that continues our tradition of raising the bar for the security orchestration, automation and response (SOAR) category.
Since Palo Alto Networks acquired Demisto almost a year ago, we have worked tirelessly to scale Demisto's strong offering to every security team in need of automation, while driving the next stage of innovation within the SOAR category.
Take a look at a couple highlights:
- Our platform has more than 270 out-of-the-box playbooks to automate and orchestrate any security use case.
- Our commitment to an open ecosystem couldn’t be stronger; we have over 350 third-party integrations and have added 105 in the last 11 months (read about our newest partner integrations).
At the same time, analysts have expanded their outlook on the future of SOAR. According to Gartner’s Market Guide for Security Orchestration, Automation and Response Solutions, “A large number of security controls on the market today benefit from threat intelligence. SOAR tools allow for the centralized collection, aggregation, deduplication, enrichment of existing data with threat intelligence and, importantly, conversion of intelligence into action.”
If threat intelligence and SOAR were meant to be together, who are we to stop that from happening? Today, we are excited to premiere the first extension of the platform with the addition of native threat intel management. Now, security leaders can take advantage of a new approach to threat intelligence management that uses the power of playbook-driven automation to drive the right response across their entire enterprise.
We expect Cortex XSOAR to be generally available in March 2020. Join us on April 7 for our virtual grand unveiling, where we’ll share all the details about Cortex XSOAR and its new Threat Intel Management capabilities, including a live demo showing how you can use it to automate challenging security workflows.
Why SOAR and Threat Intel Management?
Threat intelligence platforms (TIPs) emerged to help security teams make sense of the overwhelming volume of Indicators of Compromise (IoCs) generated from threat feeds, allowing analysts to manually apply those insights to improve the security of their environment. Good idea, wrong platform. Since TIPs premiered, SOAR has entered the scene, providing the means to bridge external threat intelligence with internal incidents and use playbook-driven automation to take quick, confident action across the enterprise. Tools, processes and teams must be able to collaborate and ultimately act on intel together.
What Our Customers Have to Say:
"We have a treasure trove of data from our threat intelligence feeds,” says Lakhsmi Kaliyaperumal, SVP and Head of Internal Security Operations at Infosys. “If we could map this data to incidents we see in our environment, we can quickly identify and fix the critical ones. The reality is that a good portion of the threat data we get ends up uninvestigated and underutilized. Cortex XSOAR would help teams like ours consume and act on our intel data in an automated and more scalable way."
Here’s a Sneak Peek at the Extended Cortex XSOAR Offering with Native Threat Intel Management:
Take complete control of your threat intelligence feeds by eliminating manual tasks with automated playbooks to aggregate, parse, de-duplicate, score and manage millions of daily indicators across dozens of supported sources.
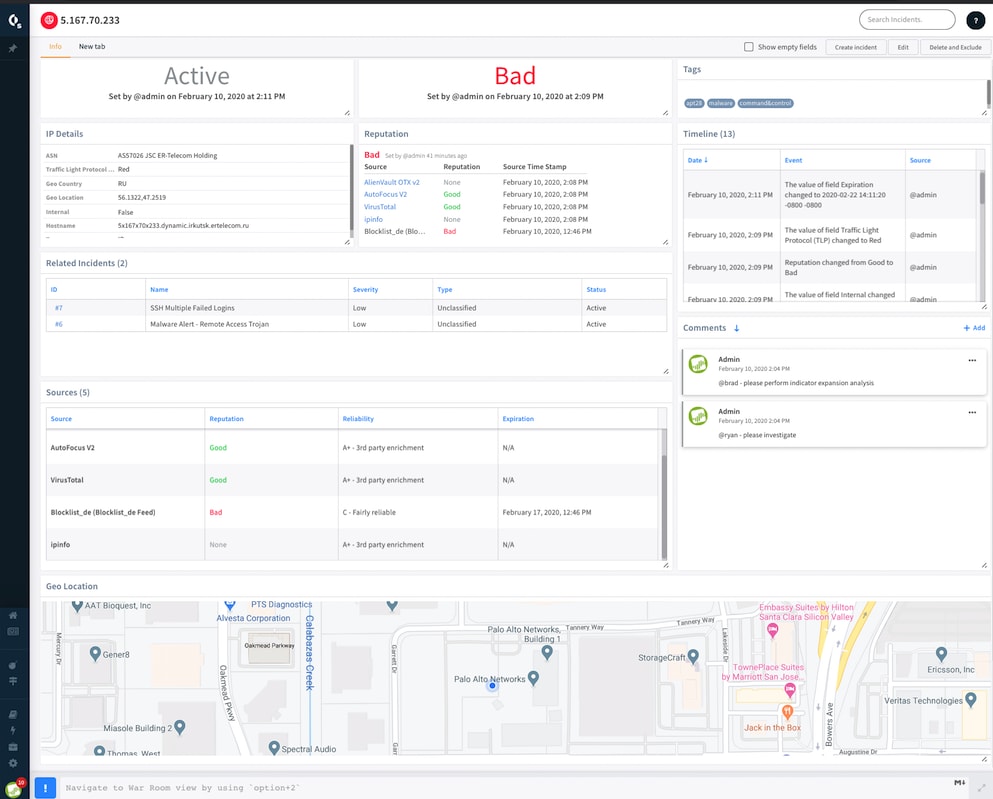
Make smarter incident response decisions by enriching every tool and process. Cortex XSOAR accomplishes this by layering third-party threat intel with internal incidents to prioritize alerts and make smarter response decisions. Teams can gain confidence in their actions by enriching any detection, monitoring or response tool with context from curated threat intelligence.
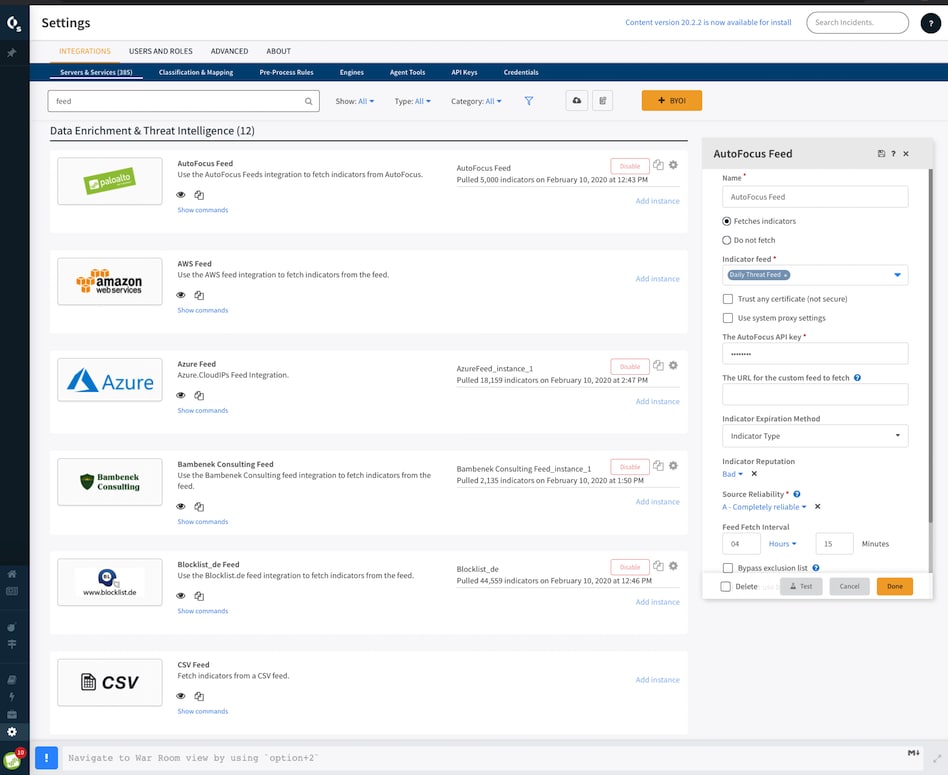
Close the loop between intelligence and action with playbook-driven automation to shut down threats across your enterprise based on proven SOAR capabilities.
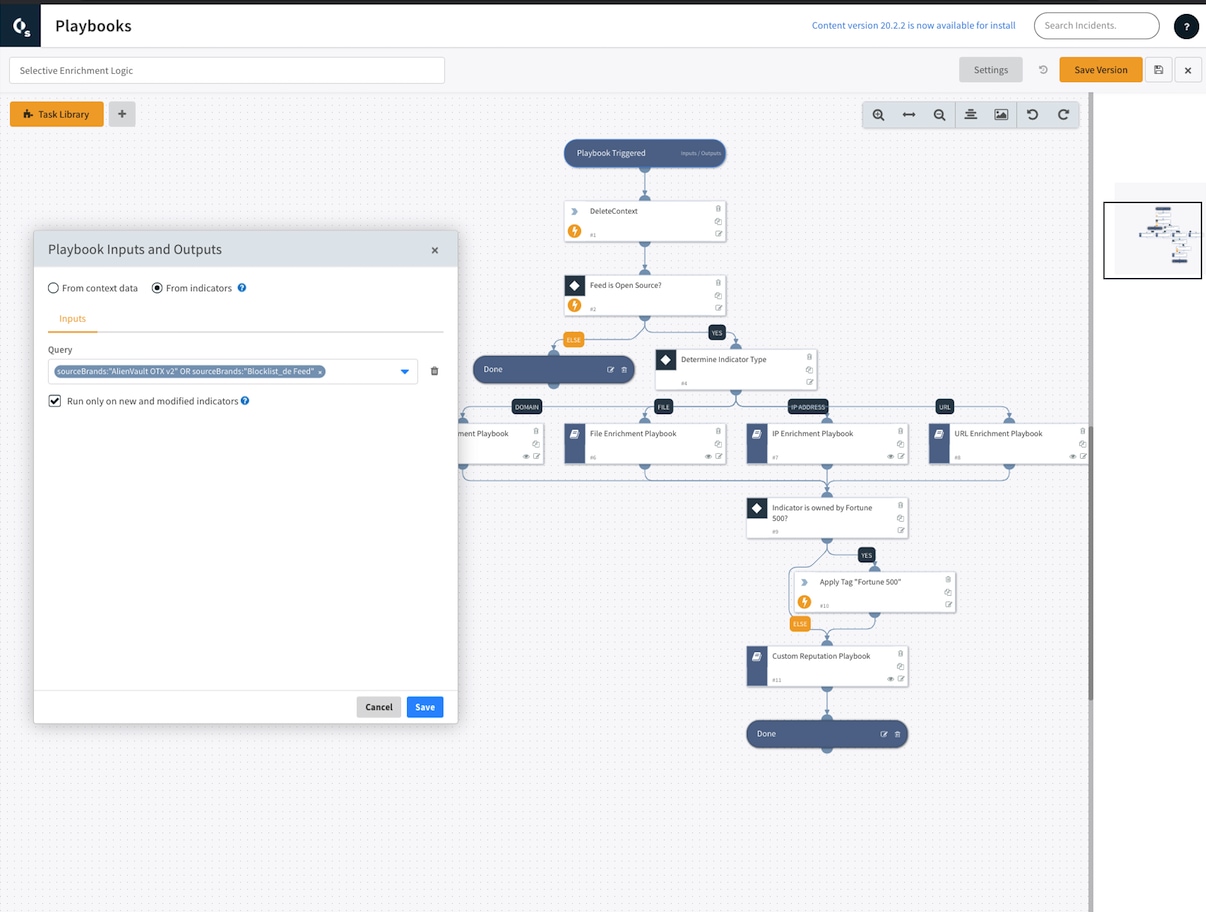
Cortex XSOAR is expected to be generally available in March 2020. We can’t wait to share more, so don’t miss our live virtual event, “Introducing Cortex XSOAR.”
1 Gartner, Market Guide for Security Orchestration, Automation and Response Solutions by Claudio Neiva, Craig Lawson, Toby Bussa, Gorka Sadowski, June 27, 2019.
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, express or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.