Patch Tuesday - not the favorite day of the month for your security team as zero-day threat alerts or newly discovered vulnerabilities invariably lead to a disrupted work schedule that involves multiple teams and a host of time-consuming manual tasks.
The latest disturbance comes from a zero-day remote code execution vulnerability announced, but not patched, along with the new Microsoft Patch Tuesday release. CVE-2023-36884 affects Microsoft Office and Windows and could be exploited using specially crafted documents, but exploitation requires the user to open the file.
According to Microsoft, the vulnerability has been exploited by a threat group targeting defense and government entities in Europe and North America. The initial access attempts have predominantly used phishing campaigns in conjunction with this exploit to target users with specially crafted Microsoft documents on the theme of diplomatic operations.
For more details on the zero-day vulnerability and mitigation, please refer to the Unit 42 threat brief that will be updated as more information on the vulnerability and mitigations become available.
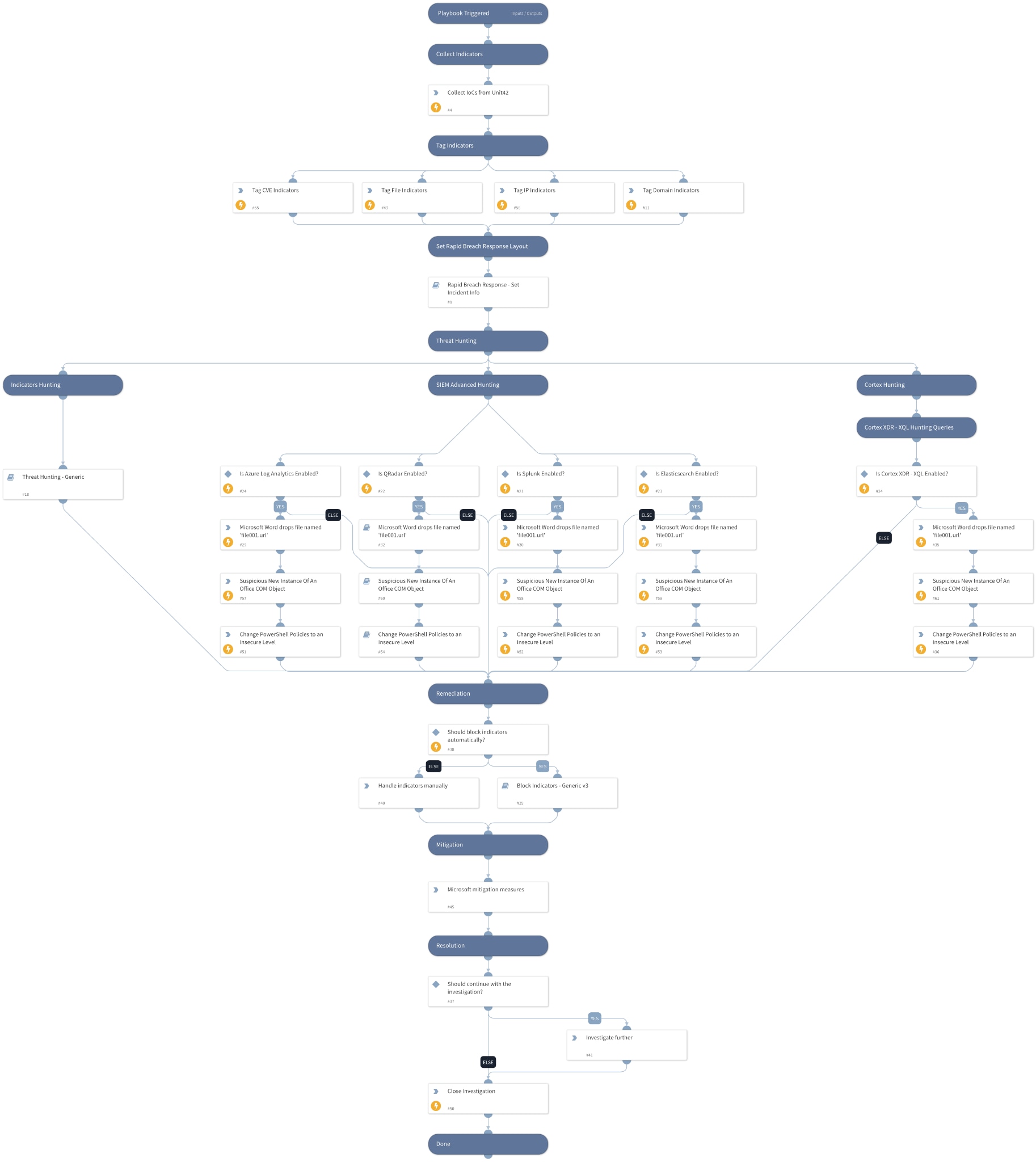
To help your team shorten mitigation time, Cortex XSOAR maintains a library of rapid response content packs. The response pack for CVE-2023-36884 helps you automate the following tasks to speed up response and mitigation actions:
- Automatically collect and update IOCs identified by Unit 42.
- Perform advanced threat hunting queries across Cortex XDR and your SIEM for behavior identified as part of exploitation patterns.
- These behaviors might include suspicious file drops, suspicious new instances of Microsoft Office Component Object Model (COM) objects and changes to the PowerShell execution policy.
- Microsoft mitigation measures such as restricting cross protocol file navigation.
To help protect your organization if you end up the unfortunate recipient of these phishing campaigns, you might want to check out our Phishing automation pack which helps you automate a huge part of your phishing incident response workflows. With this pack, you can choose to fully automate your phishing response or strategically eliminate the more repetitive, manual tasks:
- Retrieves emails from user inboxes or ingests them using mail listeners.
- Creates a phishing incident within Cortex XSOAR associated with the email.
- Extracts and enriches all indicators from email attachments.
- Analyzes files and provides reputation using your sandbox and threat intelligence integrations.
- Generates a screenshot of the email and embedded links, and calculates reputation for all indicators involved.
- Runs checks for SSL certificates of URLs, email address breach involvement, domain-squatting and email authenticity using SPF, DKIM and DMARC checks.
- Identifies similar phishing incidents belonging to the same campaign, providing visibility and manual or automatic actions to respond to such incidents.
- Calculates severity for the incident based on the provided initial severity, indicator reputations, email authenticity check, and critical assets if any are involved.
- Remediates the incident by blocking malicious indicators, searching for and deleting malicious emails upon analyst approval.
- Engages with the end user regarding the incident such as notifying them of receipt of email and providing further instructions if an email is found to be malicious.
As part of this pack, you will also get out-of-the-box phishing incident views, a full layout and automation scripts. All of these are easily customizable to suit the needs of your organization.
Learn More
These two packs are just a couple of the more than 900 automation packs and integrations we offer our users out of the box. Do check out the Cortex Marketplace to discover more automation use cases!