This post is also available in: 日本語 (Japanese)
Life Moves Fast in the Cloud
Did you know that 72% of organizations from around the world moved 30% or more of their workloads to the cloud in the last 12 months? More impressively, a quarter of these organizations moved upwards of 50% of their workloads. As our 2023 cloud-native security survey shows, life indeed moves fast in the cloud.
Change also cycles rapidly, particularly with cloud-native application development, where everything from IP addresses to containers is ephemeral. Each year delivers us to the brink of a new horizon, and each year Palo Alto Networks seeks out leaders on the cloud-native frontlines to ask about their challenges, as well as the strategies and solutions they employ to achieve their cloud-native security outcomes.
The State of Cloud-Native Security Report 2023
As in previous years, the State of Cloud-Native Security Report 2023 explores the findings of a survey spanning seven countries and five sectors of industry to inquire about practices affecting cloud-native development and security. Of 2,500+ survey respondents, greater than 50% represent enterprise-sized organizations. Approximately 50% of our population hold executive roles and 50% hold practitioner roles. From our 2023 findings, two themes emerge:
- The application lifecycle moves faster than we would have imagined 12 months ago.
- Complexity across an amalgam of challenges is the ultimate threat to securing cloud environments.
Our goal in this report remains the same, to provide you with empirical insights and inform your cloud-native security decisions in 2023 and beyond.
Cloud Migration Trends
As mentioned, workloads moved fast in 2023. Overall, survey respondents report a 13% increase over last year. Traditionally, cost and speed have been the catalyst drawing organizations to the cloud. After all, the cost and speed at which an enterprise can build an idea into a product are integral to success.
According to this year’s survey, though, cost did not make the list of top objectives behind migrating to the cloud. Cost, in fact, was an outlier, with only 8.5% of organizations citing “reducing/optimizing costs” for continuing to expand their cloud.
In 2023, organizations are foremost interested in building new and expanding existing products and services. Increasing efficiency and agility follows in a close second. The remaining reasons organizations are migrating to the cloud in order of rank are:
3. Creating new processes and workflows
4. Mitigating business and regulatory risk
5. Expanding into new markets
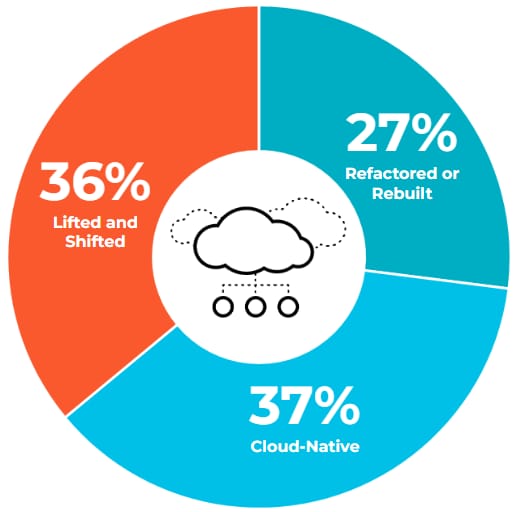
On average, organizations spend 24% of their total cost of ownership on application migration. The breakdown in methodology for application deployment is cloud native (37%), lift and shift (36%) and refactor or rebuild (27%). This is the first time cloud native is at the forefront of application development.
Platform as a service (PaaS) and serverless are the dominant application execution environments. Both PaaS and serverless are also expected to experience growth, as 70% of respondents report planned use increases in the next 24 months.
Because serverless and PaaS play a critical role in cloud application development, we may see further increases in cloud native, as well as replatforming, with lift and shift receding somewhat. This expectation is reasonable in view of Covid-era benchmarks that reflect an elevated push to move applications to the cloud.
Application Velocity
The cloud unquestionably improves time to market, innovation and operational efficiency. For developers eager to adopt DevOps, migrating to the cloud is an opportunity to accelerate the application development lifecycle. This year’s survey reveals just how agile and operationally efficient cloud-native applications can be.
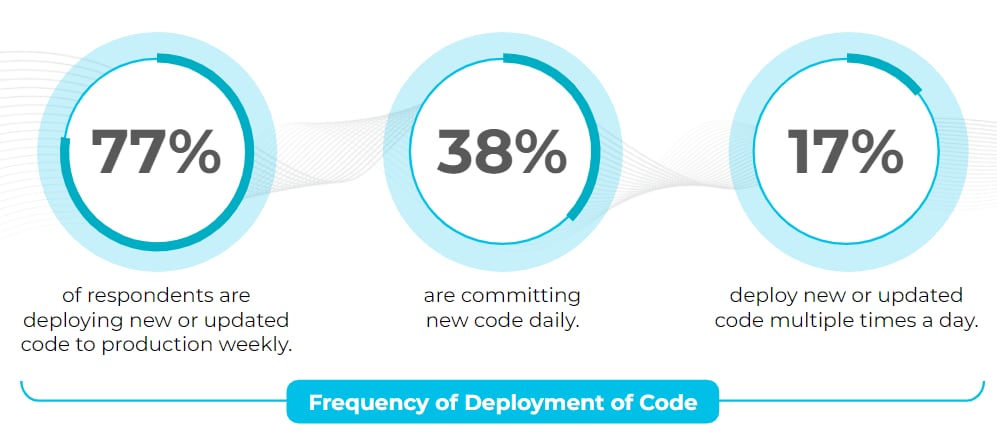
Seventy-seven percent of organizations we surveyed are deploying new or updated code to production weekly. As fast as that is, 38% of enterprises commit new code daily, and 17% deploy code multiple times a day.
But frequent deployment requires fast response times. A third of enterprises report operating with internal service level objectives of less than a day of lead time for changes. Thirty-eight percent of organizations expect service restorations within a day. Here’s the catch, though. Sixty-eight percent of respondents report increased deployment frequency, while 64% also report increased lead time for changes.
Because deployment frequency and lead time for changes measure velocity, we’re left with two questions to contemplate:
- If organizations aren’t achieving or sustaining velocity performance goals, does this point to inefficiencies in DevOps processes?
- Do increases in deployment frequency and lead time for changes suggest that security professionals are struggling to keep pace and pressure is taking its toll?
Speed and scale drive complexity. When we superimpose the ratio of 10 developers to one security professional, on top of code deployment rates, we can gauge the potential for oversights and complications.
Top Challenges with Cloud Expansion
While 60% of enterprises have been operating in a cloud environment for three or more years, complexity remains an issue. Most organizations attribute technical complexity to impeding their ability to leverage the full advantages of the cloud. It likely doesn’t help that cloud infrastructure continues to evolve for 80% of survey respondents.
When asked about their top cloud migration challenges, 42% of organizations cited technical complexity (defined in the survey as infrastructure limitations, system dependencies, etc.).
Interestingly, the next four challenges, as ranked by survey respondents, all stem from technical complexity.
2. Lack of Talent or Consulting Services: Complex environments require high levels of talent and adaptiveness to changing technology.
3. Maintaining Comprehensive Security: Complex environments are difficult to secure.
4. Lack of Visibility Across Services and Providers: Full visibility across the continuum of the application lifecycle is difficult in complex environments.
5. Meeting Compliance Requirements: Complex environments pose greater challenges in both maintaining compliance and reporting on it.
Implications for Security Teams
Accelerating application velocity has security teams caught between remaining responsive to app teams and securing an increasingly complex cloud environment across multiple layers in the cloud stack, including infrastructure, networks, VMs, containers, serverless functions, data, APIs, web apps, code and open source libraries. Without optimal programs in place, the feat is considerable.
As cloud-native technologies and application components evolve, security teams need to implement technologies and processes that enable them to mitigate risks while keeping pace with faster application development cycles. Often though, security is not adequately integrated in DevOps workflows, nor are developers and security professionals necessarily equipped with optimal tooling.
As we theorize on potential stress levels experienced by security professionals, our survey confirms talent churn, with 72% of organizations reporting a higher than usual turnover rate in cloud security roles. This statistic is supported by a Gartner study released days earlier. Unless organizations get proactive about alleviating "unsustainable levels of stress", Gartner projects attrition will continue for the next two years.
Challenges with Comprehensive Security
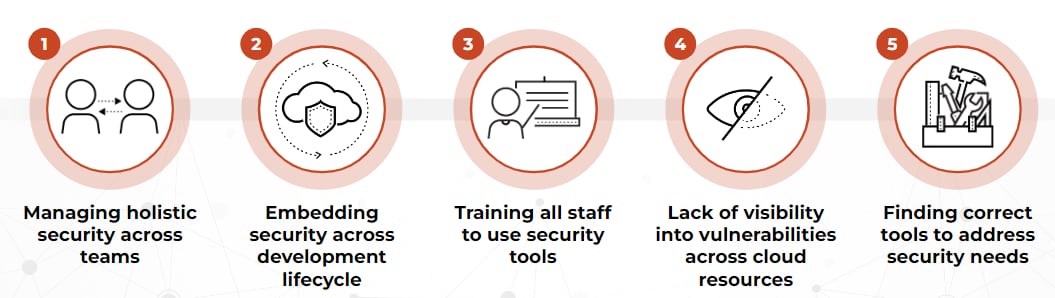
When looking at the top five challenges involved in providing comprehensive security, as identified by our respondents, we begin to see details come together to bring definition to both the challenges and the areas we’ve discussed.
Across Teams and Development Cycles
Given the plight of today’s security professionals, the top 2 challenges – managing holistic security across teams and embedding security across the cloud-native development lifecycle – come as no surprise. The operative word in both challenges is “across”. It’s time to shift left.
In the absence of proper tooling, rapid release cycles leave little room for security reviews and force organizations to take on avoidable risks. Theoretically, organizations understand that preventing vulnerabilities upstream – at the source, before deployment – requires aligned teams, in addition to security products that give value to everyone contributing to the application development lifecycle. But, the reality of integrating security in DevOps remains a challenging cultural shift.
Security Training
Seventy-eight percent of survey respondents say their individual teams are responsible for designing and implementing cloud security policies and procedures. To be fair, 81% say they understand their responsibility to deliver security across the development lifecycle.
But, while organizations have distributed responsibility for cloud security policies across teams, 47% of respondents say that the majority of their workforce doesn’t understand their security responsibilities.
We can’t underestimate an ever-turning learning curve. Cloud-native application development has created the need to secure exponentially more cloud assets across code, workloads, identities, data, etc., as well as across distinct execution environments. Utilizing multiple point tools to address each environment presents the challenge of ensuring staff are proficient with the tools.
Visibility Into Security Vulnerabilities
Over-tooling leads to an overly complex cloud environment, and it isn’t always an effective way to ensure strong security outcomes. Seventy-six percent of organizations report that the number of point tools they use creates blind spots.
Data also shows that security teams are looking for an integrated platform that provides near real-time visibility across their entire ecosystem. Specifically, 81% of respondents say they would benefit from a centralized security solution that sits across all their cloud accounts and services. What’s more, 78% of respondents believe cloud security needs greater out-of-the-box visibility and risk prioritization filtering with minimal learning.
Identifying the Right Security Tools
We know that complications arise when organizations adopt tools on a use-case basis, but for many organizations, that’s how it’s always been done. Status quo may explain the general dissatisfaction with current tools, as seen in several datapoints. More interestingly, it might explain why 77% of organizations say they struggle to identify what security tools are needed to achieve their objectives.
Ultimately, cloud security solutions must meet organizations where they are in their cloud journey. To be effective, security solutions need to cater to each organization's unique needs and priorities.
Top Incidents in Cloud Security
Of the most pervasive security incidents in the last 12 months, more respondents report experiencing risk introduced early in application development than any other event. Workload images with vulnerabilities followed closely, as did vulnerable web applications and APIs.
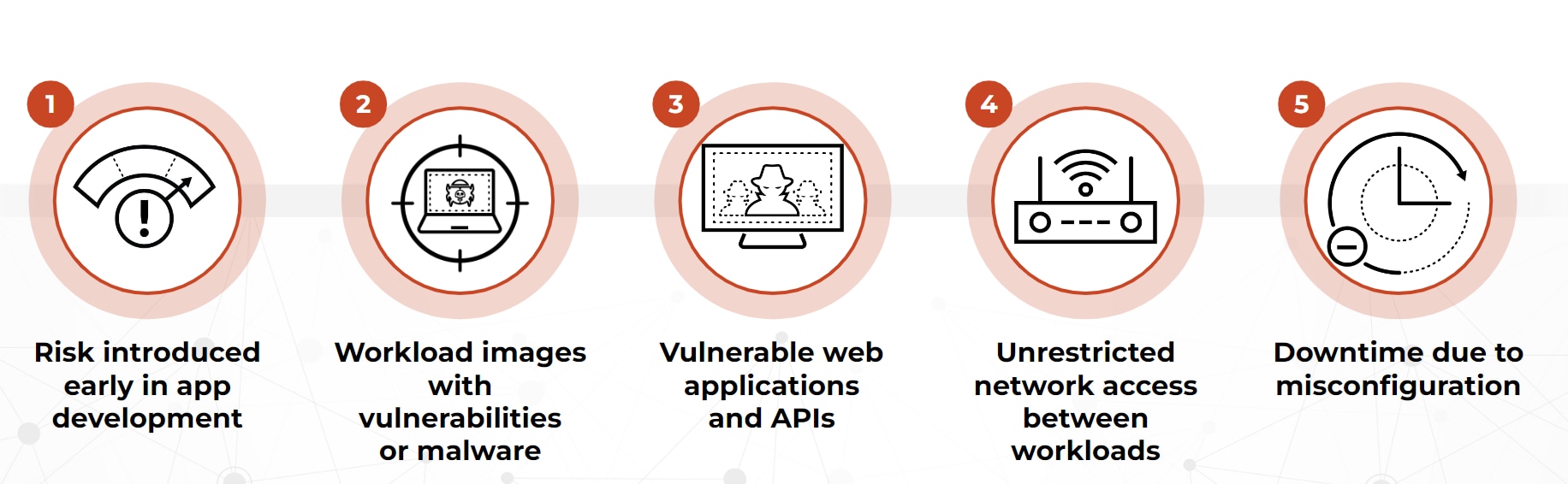
Thirty-two percent of respondents report that a lack of visibility into vulnerabilities across cloud resources led to a security incident. Because unaddressed vulnerabilities can be exploited in production, it’s imperative to catch and remedy them early in the application development lifecycle. Unfortunately, 90% of organizations tell us that they’re unable to detect, contain and resolve a cyber threat within an hour.
Any delay in the detection of malicious activity is costly, as most organizations know. One hour might be all a bad actor needs to infiltrate a network, scout out the environment, and gain access to valuable resources. Perhaps the attacker will escalate their privileges and progress to different systems to alter, extract or destroy data. Under the cloak of darkness, any amount of time is too much time.
Still, while 39% of organizations report an increase in the number of breaches, 68% say they’re unable to detect a security incident in under an hour. Visibility is key to security.
Going Forward
Building, deploying and running applications in the cloud is a complex endeavor, especially with the increased agility and efficiency afforded by DevOps. As organizations look to the future, the data encourages us to break down our silos and create processes that teams can adhere to. Development, operations, security teams and every stakeholder along the application development lifecycle must share responsibility for providing effective, comprehensive security.
Get the Full Report
The conversation today is the tip of the iceberg. Download the State of Cloud Native Security Report 2023 for findings on budget, balancing security tools and solution providers, as well as factors that drive success or advise us on how best to prepare for cloud security trends on the horizon.
I also invite you to join me for additional insights as I walk through the data in our State of Cloud-Native Security Webinar, which is available on-demand for your convenience.