We’ve all heard the excitement around platformization. Our CEO Nikesh Arora has been emphasizing its importance for over a year now. Platformization is our answer to the chaos of disconnected security tools. However, as many organizations race to simplify and strengthen their security posture, many overlook a critical element: IoT devices.
Having a unified platform from Palo Alto Networks is incredibly important because it allows us to not only consolidate all those functions into one place but also be much more efficient and capable of responding to the insights they provide. If the information is in a system that's not maintained or managed well, or it's not integrated with the rest of our systems, there could be a gap that can lead to a breach.
—Dave Munroe, CISO at NHL
This platform approach is powerful because it holistically strengthens your risk posture, reduces complexity of management, and allows significant efficiency gains.
Often overlooked, IoT devices, from smart lighting systems and badge readers to industrial equipment and medical devices, are truly everywhere. They’re also notoriously hard to secure. They aren’t always built with security in mind, often run outdated firmware, and can’t host endpoint security agents. Yet, they’re connected to the same networks that many organizations’ crown-jewel assets sit on.
If a bad actor gets onto the network via an IoT device, they can hide on compromised devices undetected for extended periods. They can easily move laterally, producing a rapidly growing attack surface, while hiding in broad daylight.
And as the threat landscape becomes increasingly fragmented, a platform approach is the single best way to protect your growing number of devices. When you platformize with Palo Alto Networks, you can simply activate the IoT Security license, which grants you the visibility to assess and prioritize risk. It also simplifies enforcement to ensure you get the most protection and efficiency across your entire estate. This is all done natively without having to deploy single-purpose sensors or having to integrate disparate technology stacks.
IoT security is critical for us at NHL because we need a solution that can detect and secure unusual devices. We have a lot of different devices in our environment, not only for broadcast, but sometimes industrial control – and you can't use a typical endpoint security solution on these devices like you would on a Mac or PC. Instead, you need a dedicated security solution to protect those devices. For us, IoT security has become increasingly important as we've moved to cloud broadcast and things that rely more on these unique appliances.
—Dave Munroe, CISO at NHL
Enhanced Visibility
With Palo Alto Networks, visibility isn’t just comprehensive – it's actionable. Our IoT Security solution automatically discovers and identifies every connected device on your network, even those that can't run agents, by simply monitoring the network traffic these devices generate for their day-to-day operation. Using ML-powered device profiling, we classify devices down to the model and OS without requiring manual intervention. That means real-time awareness of every asset – IT, OT and IoT, so you know exactly what’s connected, what it’s doing, and whether it poses a risk.
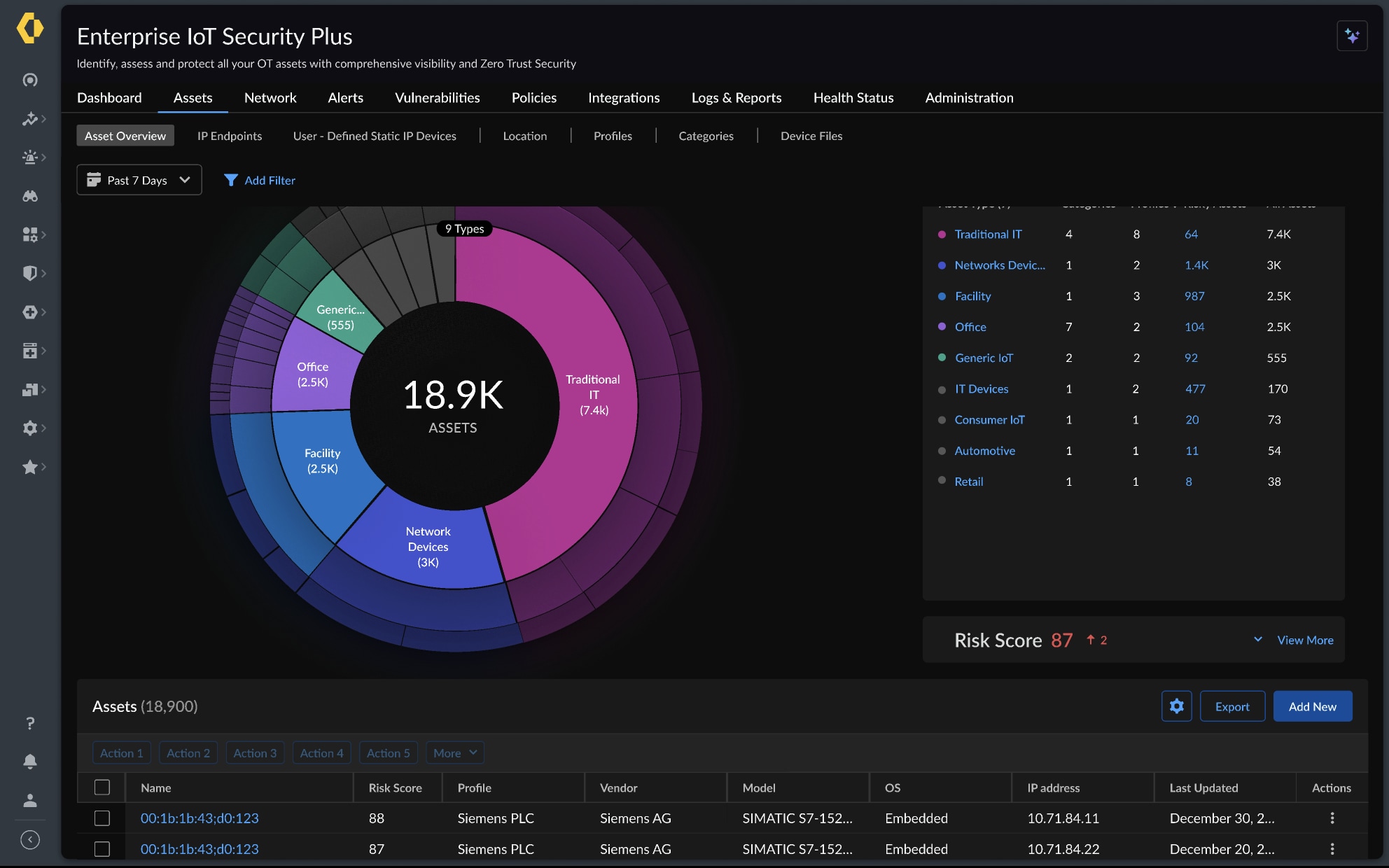
Enterprise IoT Security Asset Overview
Multi-Dimensional Risk Prioritization
As the threat landscape grows more complex, organizations face multiple risks across various devices, which makes visibility into these threats crucial. With so many risks to address, businesses can't remediate everything and must prioritize the most critical ones. This involves assessing threats based on their likelihood, potential business impact and the specific context of the organization, including any compensating controls in place. By customizing risk scores to align with an organization’s tolerance and priorities, businesses can focus on what truly matters to protect their operations effectively.
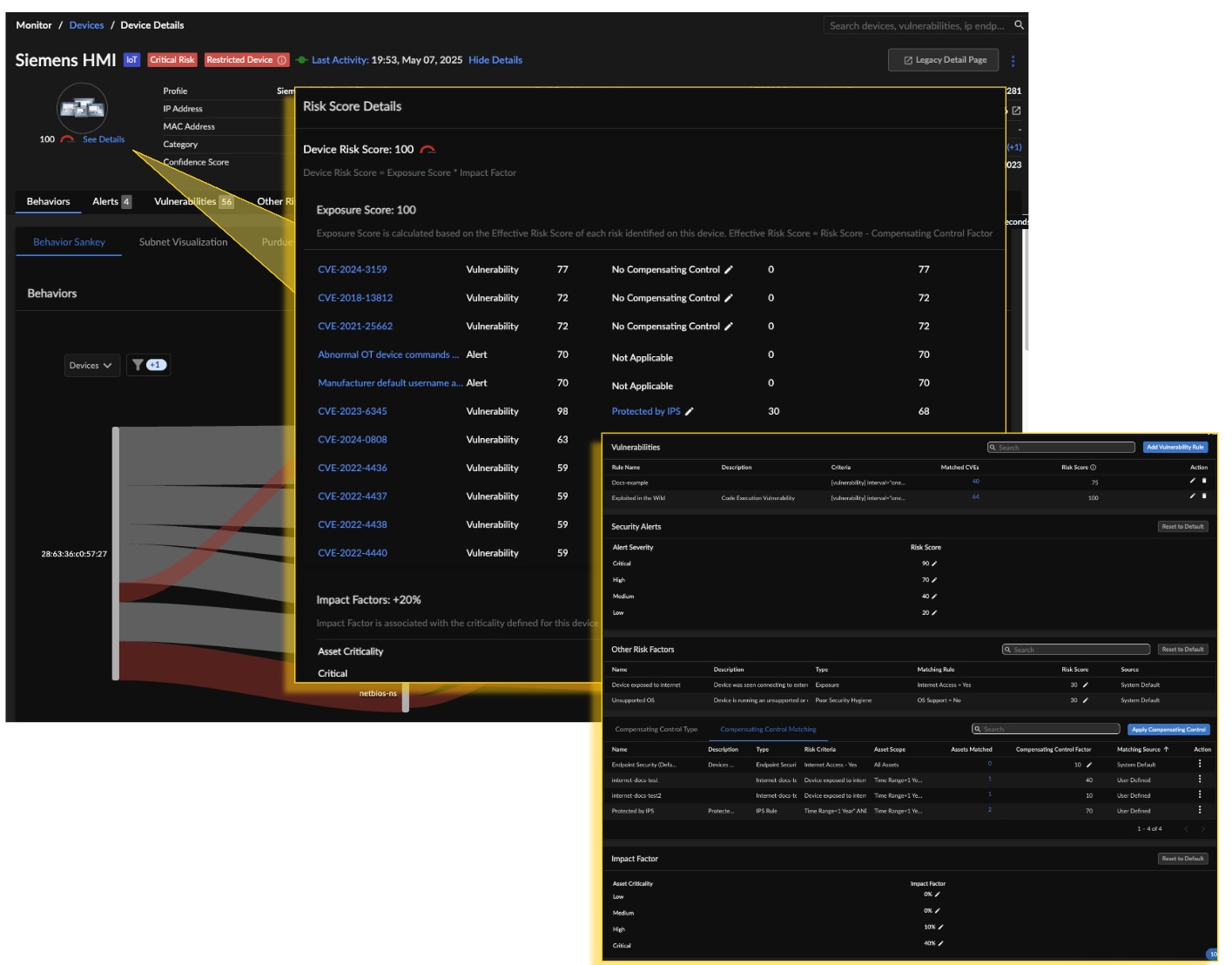
Risk Visualization and Customization
AI-Powered Policy Recommendations and Enforcement
Visibility is step 1; action is the ultimate goal. Visibility allows organizations to detect threats, understand vulnerabilities, and maintain situational awareness. However, true security requires proactive defense, robust controls and continuous risk management. Without action, visibility is just an observation, not protection.
Our platform takes enforcement to the next level with AI and behavior-based policy recommendations. Instead of relying on static rule sets or guesswork, Palo Alto Networks analyzes device behavior to generate precise, least-privilege security policies tailored to each IoT device. These policies can be pushed directly to our NGFWs, enabling real-time segmentation and the ability to virtually patch using threat prevention. If a device starts acting suspiciously, users can set policies to ensure it’s automatically isolated before an attacker can move laterally. That’s enforcement that is smart, scalable, and fast.
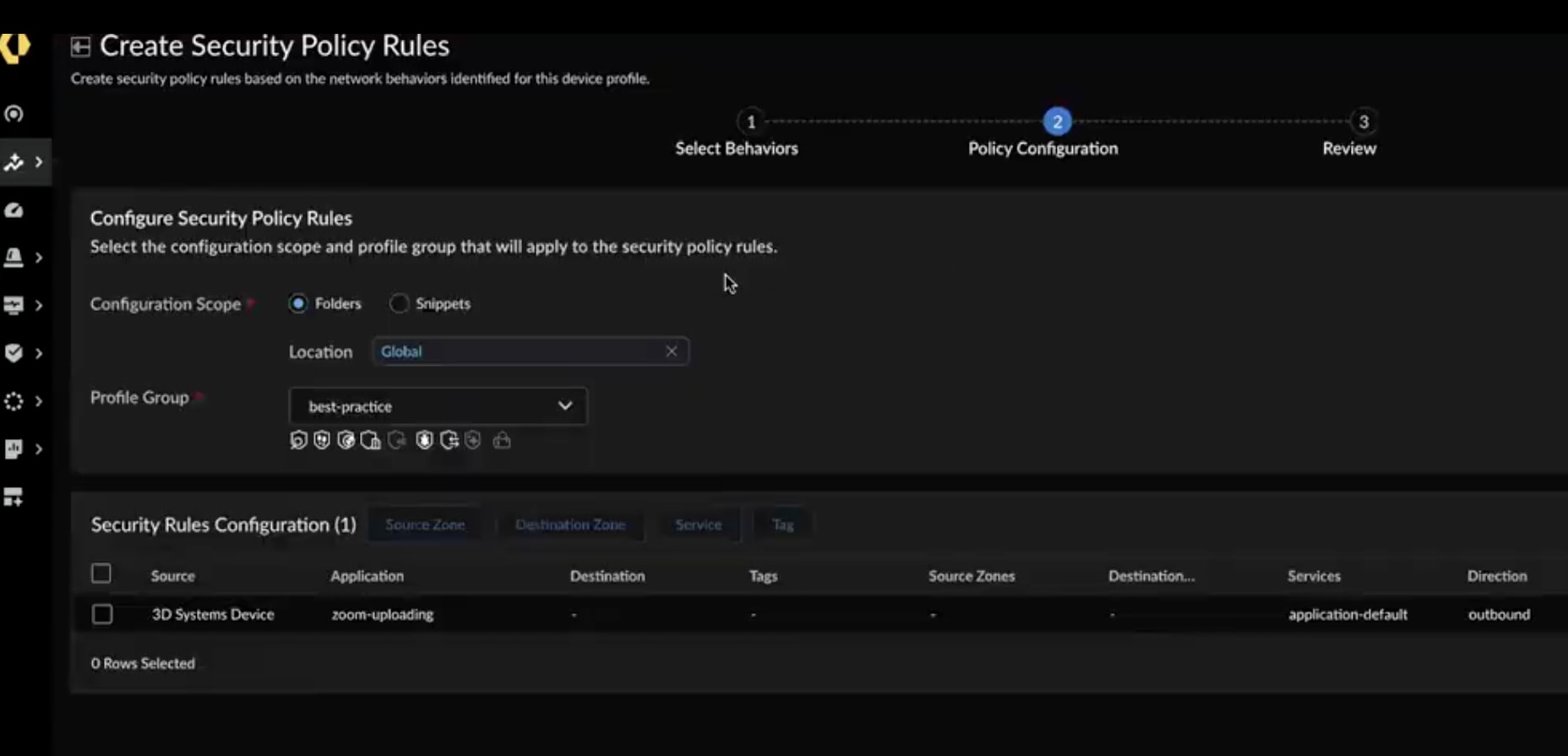
Create Security Policies
Optimized Integrations
True platformization means more than consolidating internal tools; it’s about creating an open, extensible security ecosystem. Palo Alto Networks Enterprise IoT Security brings this philosophy to life by seamlessly integrating with the third-party tools your teams already rely on.
Whether its syncing asset context into your asset management solution for streamlined inventory and ticketing, feeding risk-based insights from your vulnerability management provider for smarter vulnerability management, or sending enriched telemetry to your SOC for faster detection and response, our platform ensures IoT intelligence doesn’t stay siloed. These integrations empower organizations to unify workflows, enhance decision-making, and extend the power of a platformize approach across the broader security stack.
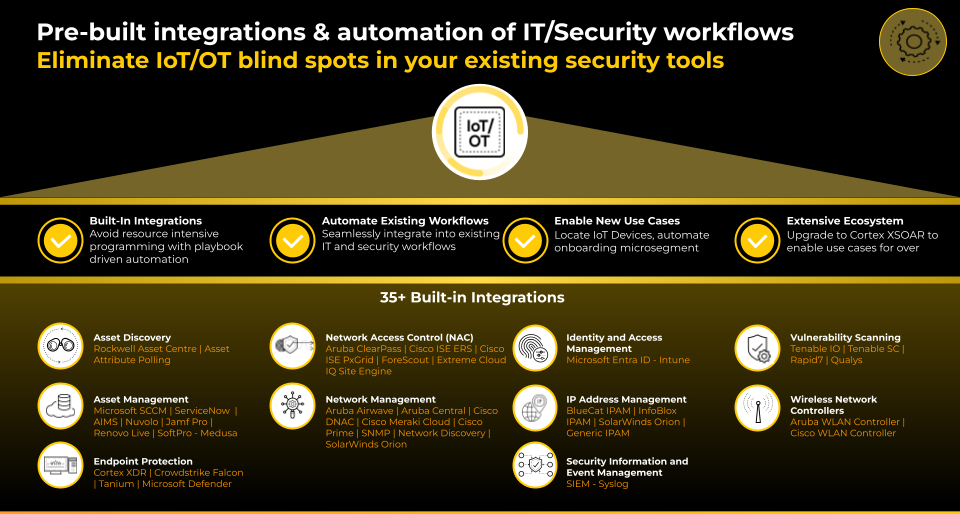
Third-Party Integrations
Seamlessly Incorporate IoT Security Into Your Cybersecurity Platform
Ultimately, every unmanaged, unmonitored and unprotected device is an open door for attackers. And with IoT adoption accelerating across every industry, that risk is only growing.
At Palo Alto Networks, we’ve built an IoT security solution that doesn’t live in a silo. It’s fully integrated into the industry’s most complete cybersecurity platform, giving you unmatched visibility, intelligent policy enforcement and seamless orchestration across your entire digital footprint.
Want to see firsthand how you can seamlessly incorporate IoT security into your own platformization journey? Register for our upcoming hands-on workshops or sign up for a free trial to experience how Enterprise IoT Security can help. Because at the end of the day, we all know that if you can’t see it, you can’t secure it.