There’s no hiding from it. Cloud data breaches are on the rise. Threat actors are more prevalent and sophisticated. And the stakes for organizations across all industries remain high.
In this post I’ll walk you through recent cloud threat data from Unit 42’s Cloud Threat Report, Volume 7: Navigating the Expanding Attack Surface. With a focus on identities and access management (IAM), I’ll build on that info to demonstrate how identity-based attacks happen. I’ll then show you how to establish a defense-in-depth approach to help your organization reduce your risks and stop breaches before they happen.
Cloud Breaches and Oversights in the Cloud
Let’s look at two breaches analyzed in the Unit 42 report as they break down the MITRE ATT&CK Cloud Matrix tactics, techniques and procedures (TTPs). The order of tactics corresponds to the paths of each attack.
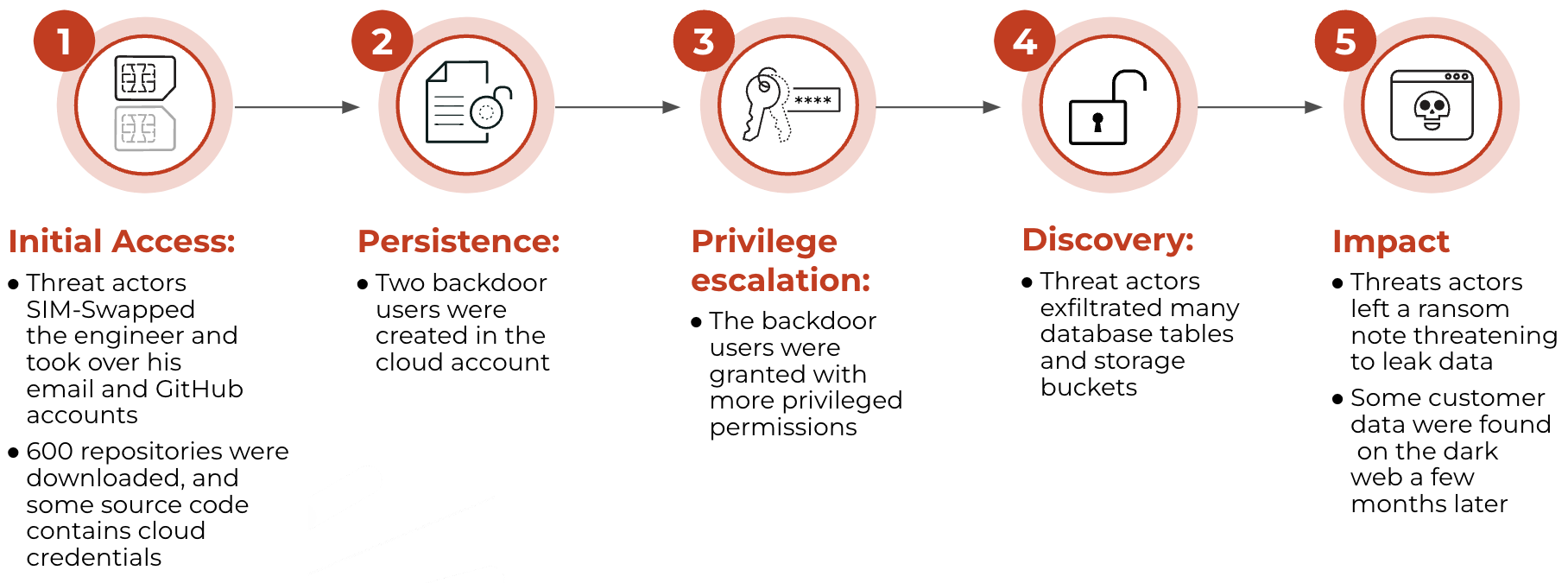
Incident #1: Sim-Swap Scam
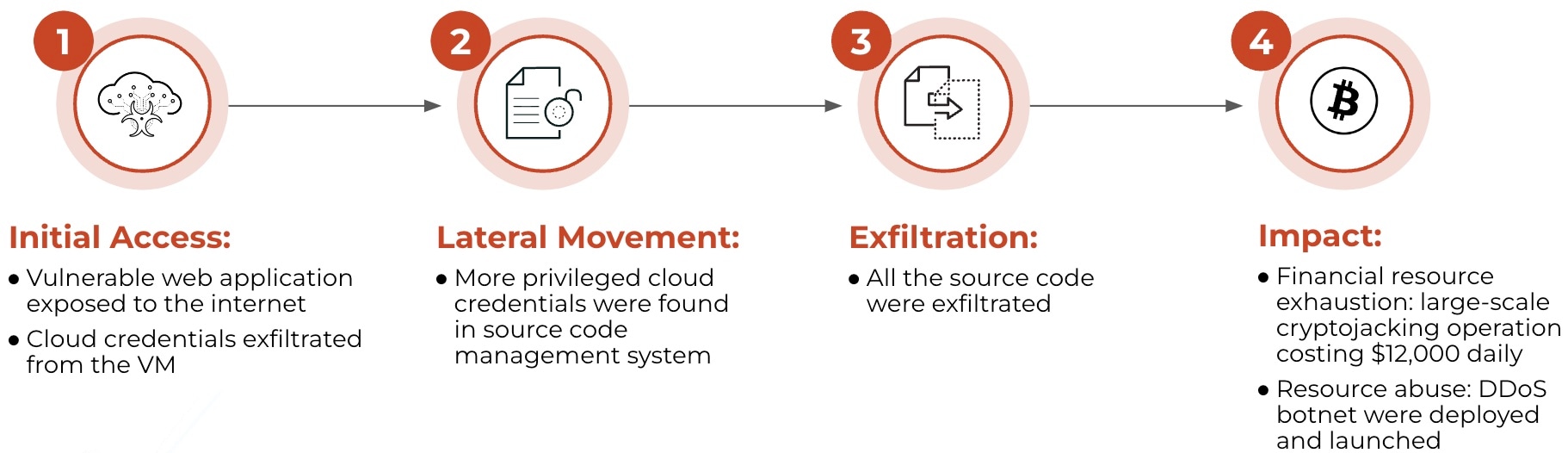
Incident #2: Cryptojacking Attack
When evaluating these incidents, we see common identity and access issues. Below, you’ll find more details on the incidents, as well as key findings from the 1,300 organizations mapped to these security issues in the Unit 42 report.
Issue 1: Hard-Coded Credentials
Incident #1: Credential leak in source control management (SCM) — Attacker uncovered 10 access keys belonging to four different cloud accounts.
Incident #2: Credential leak in virtual machine (VM) — Attacker exfiltrated temporary credentials associated with the VM instance. The threat actor also enumerated and viewed all the VM instances’ user data. A hard-coded GitHub credential in one VM instance’s user data allowed the threat actor to access the source code repositories for the entire company.
Key Findings:
- 83% of organizations have hard-coded credentials in their source control management systems
- 85% of organizations have hard-coded credentials in virtual machines’ user data
Issue 2: Weak Authentication and Unauthorized Access
Incident #1: Two new users were created to impersonate valid employees.
Incident #2: Threat actor created a backdoor IAM role that allowed access from an attacker-controlled account.
Key Findings:
- 76% of organizations don’t require multifactor authorization (MFA) for console users.
- 58% of organizations don’t enforce symbols in passwords.
Issue 3: Overly Permissive Access Leading to Lateral Movement and Privilege Escalation
Incident #1: One access key with the AWS IAMFullAccess role allowed the threat actor to create new users in the compromised account. This allowed attackers to perform reconnaissance and move laterally with ease.
Incident #2: The threat actor cloned all the repositories and scanned for more credentials. A cloud access key hard-coded in a continuous integration, continuous delivery (CI/CD) automation script granted the attacker administrator permissions.
Key Findings (Cloud Threat Report Volume 6)
- 66% of organizations use access keys for more than 90 days.
- 99% of permissions granted are inactive.
As shown, organizations face the same risks observed in the two cloud breaches, indicating a high likelihood of remaining vulnerable to these and similar security incidents.
Let’s look at recommendations for mitigation and how Prisma Cloud can help you take a defense-in-depth approach to effectively eliminate these attack paths.
Mitigation Steps for Hard-Coded Credentials
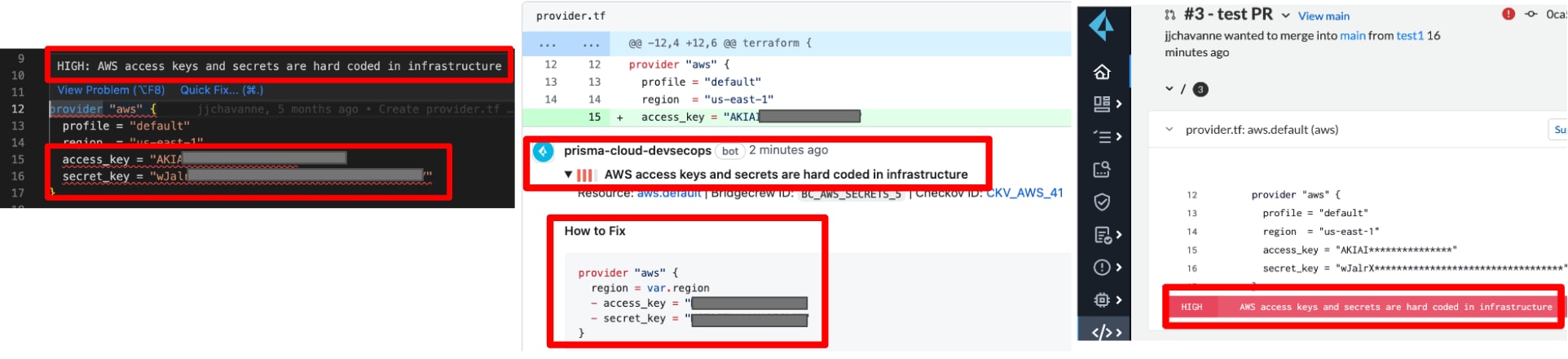
Step 1: Enable secrets scanning across the development lifecycle, especially as far left as possible.
Strong risk prevention demands secret scanning. Why? Because once code is committed into a repository, it’s immutable and part of git history. Even if you make a new commit that removes the hard-coded secret, it’s still searchable. Threat actors have tools that automatically search for this info.
Additionally, if you only scan at runtime, you only temporarily remove the risk. The same secret stored in an image or code can repeatedly get pushed into running workloads. To ensure you properly mitigate these risks, Prisma Cloud gives you end-to-end secrets scanning. By scanning for and even blocking (i.e., block merge at the pull request level), you can address exposed secrets and credentials across the development lifecycle, including:
- Developer’s IDE (integrated development environment)
- Source control management systems (both pre-merge and in repo)
- CI/CD pipelines
- Image repositories
- Running compute resources such as VMs, containers, and functions
Step 2: Scan cloud data stores for exposed secrets and credentials.
Developers and practitioners often save information in cloud storage buckets. This practice creates an additional target for threat actors to find and gain access to secrets and other sensitive data. You can scan and surface this info, however, with Prisma Cloud’s DLP cloud data security capabilities.
Step 3: Alert on anomalous credential usage.
If an attacker successfully exfiltrates cloud credentials from the VM — a common step once an attacker has gained access to a machine — Prisma Cloud can alert on the use of those credentials outside the VM.
Mitigation Steps for Weak Authentication and Unauthorized Access
Step 1: Enable MFA for all console logins and APIs.
It should go without saying — enabling MFA for all console logins and APIs is a critical best practice. If you haven’t already implemented, you should do so immediately for all your Identities.
Step 2: Scan runtime and IaC configurations to enforce MFA and password policies across organizations.
Prisma Cloud helps identify MFA misconfigurations across cloud service providers (CSPs). It supports runtime and build time policies when using IaC, such as Terraform or CloudFormation, to configure MFA settings. Prisma Cloud can also equip you to block non-compliant MFA configurations at build time and/or auto-remediate issues at runtime.
Step 3: Adopt federated authentication with tools such as Okta and Azure Active Directory.
Prisma Cloud provides direct integration with common identity provider (IdP) services to give you full visibility and control across your cloud providers. What’s more, Prisma Cloud can find users created outside your IdP service so you can remove or migrate them when needed.
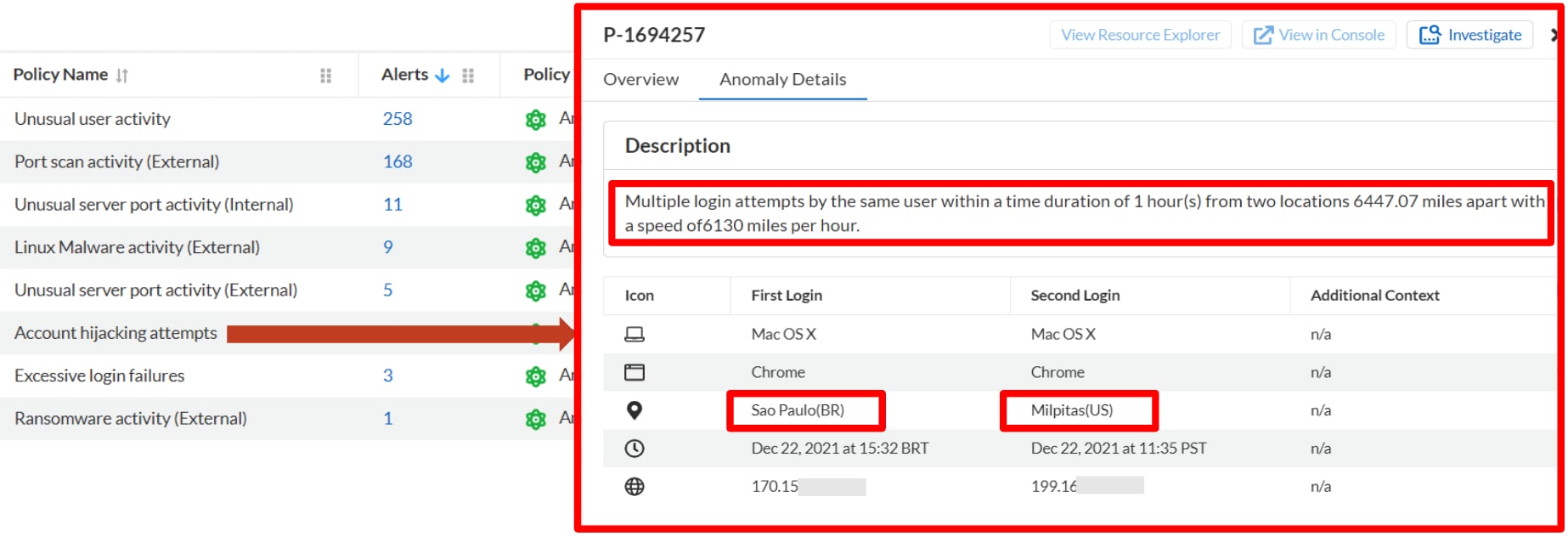
Step 4: Alert on anomalous login and other unusual user behaviors.
Prisma Cloud provides out-of-the-box user and entity behavior analytics (UEBA) anomalous policies for the range of atypical activities — from account hijacking to excessive login failures — and will immediately alert you to suspicious behavior occurring in your cloud environments.
Step 5: Block unauthorized access on public-facing workloads.
In the case of AWS, configuring IMDSv2 alone won’t prevent someone from accessing credentials from AWS’s metadata service if the VM is compromised. When utilizing public-facing workloads, the use of an agent becomes critical. Prisma Cloud’s agents can automatically block unauthorized access and secure the credentials from threats both at runtime and at the application layer. Prisma Cloud provides this level of security for any type of workload — including VMs, containers, and serverless functions.
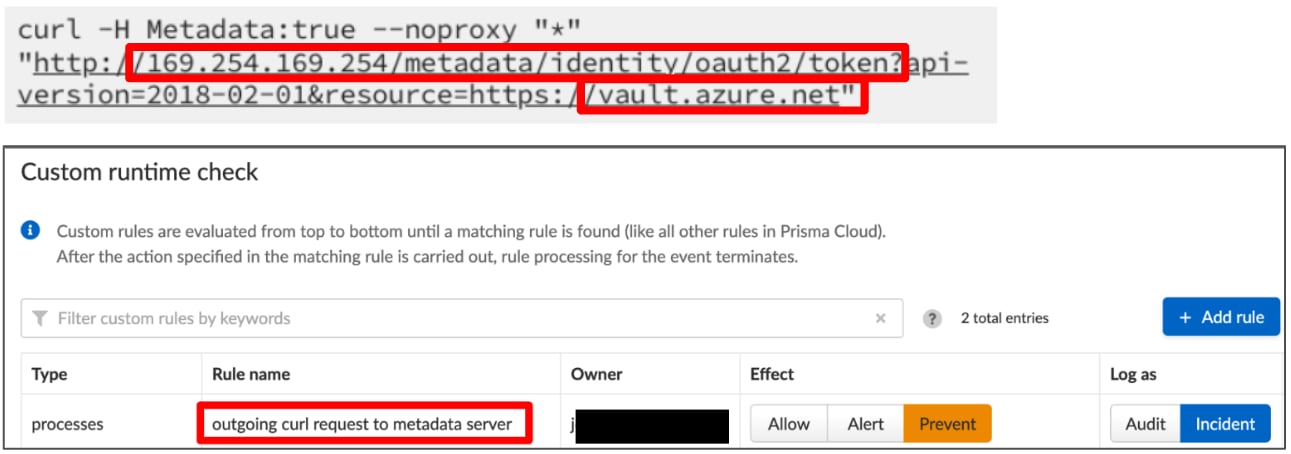
Mitigation Steps for Overly-Permissive Access Leads to Lateral Movement and Privilege Escalation
Step 1: Enforce key rotation policies and enable monitoring.
CSPs have improved their authentication capabilities in the last few years, now offering better temporary credential options, for example. Organizations should use these features when possible. Data tells us, though, that organizations struggle to migrate to and enforce use of these best practices, neglecting to rotate credentials and remove inactive identities — both of which leave doors open to attackers.
Prisma Cloud’s out-of-the-box policies alert on inactive identities and access keys that haven’t been used in 90 days, among other red flags. It also offers the ability to create custom policies to suit your organization’s needs.
Step 2: Adopt cloud infrastructure entitlement management (CIEM) capabilities to calculate risky and unused permissions across your environment.
Implementing the Zero Trust model goes hand in hand with defense in depth, both ensuring you effectively secure the frontline and backdoors of your application lifecycle. Prisma Cloud’s CIEM capabilities deliver simple, consistent IAM across Amazon Web Services (AWS), Microsoft Azure and Google Cloud Platform (GCP).
By accurately calculating net-effective permissions, Prisma Cloud helps you understand your multicloud identity risk — including identities managed with IdPs and SSO tools, such as Azure AD and Okta. To help enforce least-privileged access, Prisma Cloud provides you with recommendations to remove unused permissions. Users can also leverage automated remediation to rightsize permissions on an ongoing basis.
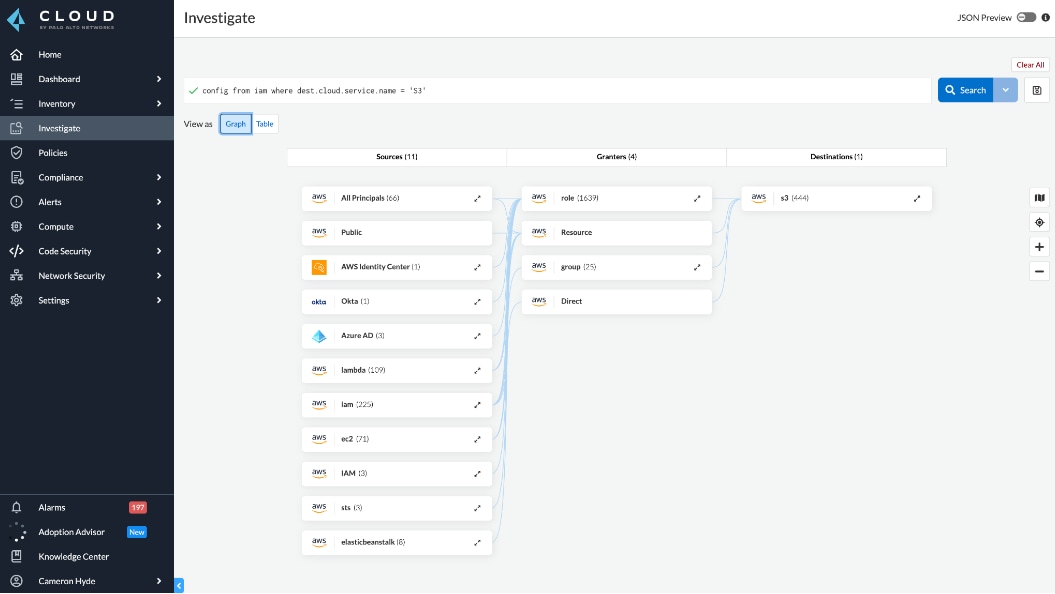
Findings and Recommendations
To avoid areas of weakness that allow threat actors to steal your credentials and gain unauthorized access, consider creating a strategy that works toward end-to-end visibility, risk prevention and runtime protection to secure identity and access issues across all stages and areas of your cloud environments. Prisma Cloud is designed to make that possible.
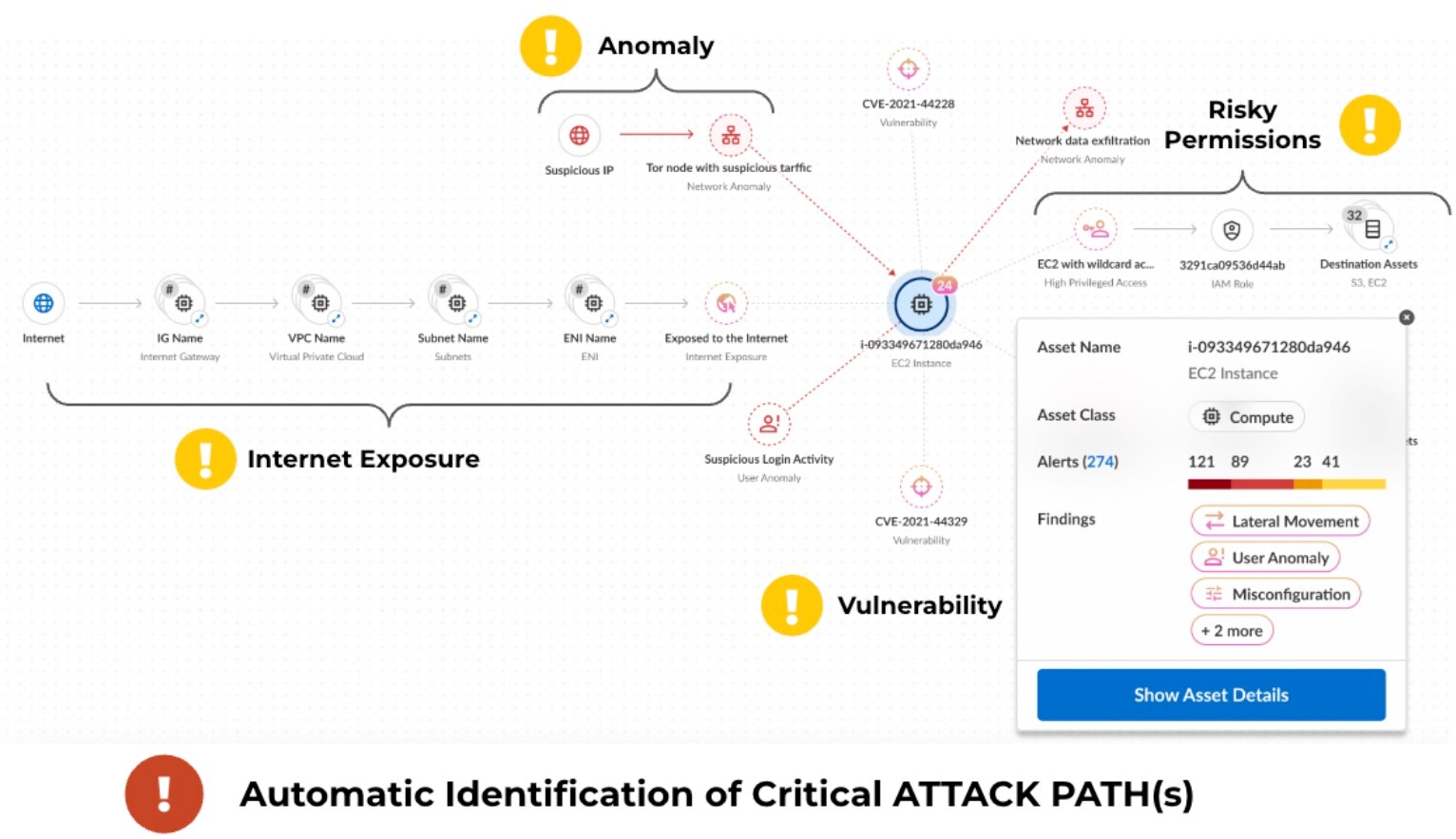
Going Beyond Identity and Access: Context Is King
To accurately prioritize risks, you need to evaluate your identity and access issues in context of big-picture details, such as internet exposure, data exposure, critical and high vulnerabilities and anomalous activity. Only with full data context can you analyze your attack paths well enough to understand your risks and immediately mitigate your most crucial issues.
Prisma Cloud has robust cloud data context through complete visibility across the development lifecycle. This, coupled with powerful threat intelligence, gives organizations extremely accurate anomaly detection, along with network threat and vulnerability data to maximize contextualization of your risks.
What Does AI Say About the Defense-in-Depth Approach?
Curious to see what AI had to say on the topic of defense in depth, I prompted my tool of choice with several questions. AI responded with good advice and offered some well known best practices.
Here are three key points I received from the prompt, “Explain why a holistic defense-in-depth approach is so critical to protect your identities and access in the cloud.”
AI Response:
- The cloud is a complex environment with a wide range of potential attack vectors. This makes it difficult to protect against all possible threats with a single security control.
- Attackers are constantly evolving their techniques and tactics. This means that security controls that are effective today may not be effective tomorrow.
- Human error is a factor in many data breaches. This is why it is important to have multiple layers of security in place to reduce the risk of a breach caused by human error.
In short, AI agreed that a defense-in-depth approach helps organizations mitigate risks by layering multiple security controls across the cloud environment to protect against a range of attacks.
Most notable to me about the feedback I received was AI’s emphasis on the human element. It went as far as to say that employees (humans) are often the weakest link in the security chain.
Palo Alto Networks research, among other leading research efforts, continue to highlight the risks and difficulties of managing cloud identities and access. There is no getting around the difficulty. It’s really difficult. But, by taking time to understand the risks and how threat actors infiltrate cloud environments, you can build and implement an effective risk-based strategy.
Learn More
Prisma Cloud’s holistic approach and ongoing innovations in cloud security give you the defense in depth you need to stay ahead of threat actors and keep your cloud assets and data safe.
If you haven’t checked us out in a while, I encourage you to experience Prisma Cloud firsthand with a free 30-day test drive.