- What is Data Security Posture Management? DSPM Guide
- What Is Cloud Data Protection?
- How DSPM Enables XDR and SOAR for Automated, Data-Centric Security
- DSPM Tools: How to Evaluate and Select the Best Option
- How DSPM Combats Toxic Combinations: Enabling Proactive Data-Centric Defense
- How DSPM Enables Continuous Compliance and Data Governance
- DSPM for AI: Navigating Data and AI Compliance Regulations
- What Is Data Exfiltration?
- What Is Data Discovery?
- What Is Data Classification?
- What Is Data-Centric Security?
- What Is Data Access Governance?
- DSPM Market Size: 2026 Guide
- How DSPM Is Evolving: Key Trends to Watch
- What Is a Data Flow Diagram?
- What Is Data Movement?
-
What Is Data Detection and Response (DDR)?
- Data Detection and Response Explained
- Why Is DDR Important?
- Improving DSPM Solutions with Dynamic Monitoring
- A Closer Look at Data Detection and Response (DDR)
- How DDR Solutions Work
- How Does DDR Fit into the Cloud Data Security Landscape?
- Does the CISO Agenda Need an Additional Cybersecurity Tool?
- Supporting Innovation Without Sacrificing Security
- DSPM and Data Detection and Response FAQs
- What Is Unstructured Data?
- What Is Structured Data?
- What Is Shadow Data?
- DSPM Vs. CSPM: Key Differences and How to Choose
What Is a Data Breach?
A data breach occurs when unauthorized individuals gain access to sensitive information, such as personal data, financial records, or intellectual property, within an organization's network or cloud infrastructure. Data breaches can result from various attack vectors, including malicious actors exploiting vulnerabilities, social engineering tactics, insider threats, and inadequate security measures. The consequences of a data breach can be severe, involving direct financial loss, as well as costs associated with reputational damage, legal repercussions, and operational disruptions.
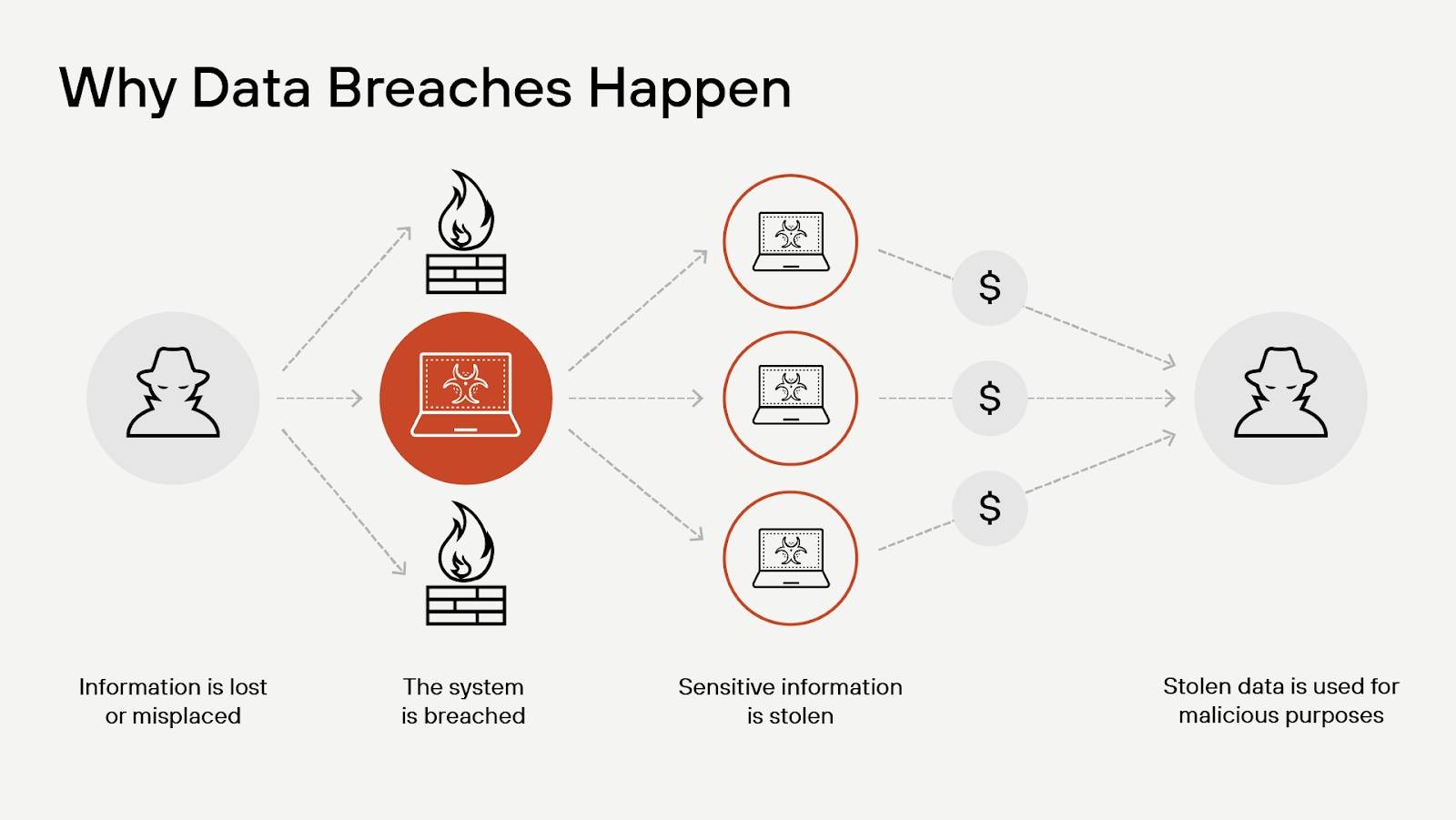
Figure 1: Lost or misplaced information creates a vulnerability, which is often the inciting incident that ends in data breach.
Data Breaches Explained
A data breach is a cybersecurity incident, but not all security incidents become data breaches. Events and activities that could compromise the confidentiality, integrity, or availability of an organization's information systems or data fall under the heading of security incident. Such incidents might include vulnerability detection, anomalous user activity, malware infection, denial of service (DoS) attack, policy violation, and unauthorized access. But a security incident isn't a data breach until data is accessed.
A data breach presents a more severe event, often targeted, where confidential information is accessed, stolen, or exposed. The unauthorized party gains access to an organization's sensitive data, which might include personally identifiable information (PII), financial details, user accounts, or trade secrets.
The Breach Lifecycle
A data breach follows a distinct lifecycle, progressing through multiple stages from reconnaissance to forms of cyber attack to post-incident recovery. Understanding this cycle helps organizations detect, contain, and mitigate security incidents before they cause extensive damage.
Reconnaissance and Targeting
Attackers begin by gathering intelligence on potential targets, searching for vulnerabilities in exposed infrastructure, weak credentials, or unpatched software. Reconnaissance techniques include open-source intelligence (OSINT), scanning for misconfigured cloud resources, and phishing campaigns to obtain login credentials. Advanced threat actors may conduct social engineering or leverage stolen credentials from previous breaches.
Initial Compromise
Once a target is identified, attackers establish an entry point using methods such as phishing, credential stuffing, exploiting software vulnerabilities, or misconfigured access controls. In cloud and hybrid environments, attackers may abuse overly permissive IAM roles, exposed APIs, or weak authentication mechanisms. The goal at this stage is to gain a foothold within the network while avoiding detection.
Privilege Escalation and Lateral Movement
After gaining access, attackers escalate privileges to obtain deeper control over systems. Techniques such as pass-the-hash attacks, abusing misconfigured privilege settings, or exploiting local administrative credentials allow adversaries to move laterally across an environment. Advanced attackers use fileless malware, living-off-the-land techniques (LotL), and stolen session tokens to bypass security controls and evade detection.
Data Exfiltration or Disruption
Once positioned within the network, attackers execute their primary objective. Sensitive data may be exfiltrated, encrypted for ransom, or modified to disrupt operations. Data exfiltration often involves stealth techniques such as encrypting stolen data in transit, using DNS tunneling, or leveraging compromised cloud storage. Ransomware attacks encrypt critical files, demanding payment for decryption keys, while destructive attacks aim to corrupt or erase key systems.
Detection and Containment
Organizations detect breaches through security monitoring, anomaly detection, threat intelligence feeds, or incident reports. Detection speed depends on the maturity of security operations, presence of automated alerting, and response preparedness. Once detected, security teams initiate containment efforts, such as isolating infected systems, revoking compromised credentials, and disabling malicious access points. Rapid containment prevents attackers from expanding their foothold or executing additional payloads.
Eradication and Recovery
Once containment is achieved, the focus shifts to removing the attacker's presence from the environment. Security teams remediate vulnerabilities by patching exploited flaws, resetting compromised accounts, purging malware, and reinforcing security controls. Recovery efforts include restoring affected systems from secure backups, verifying data integrity, and conducting forensic analysis to ensure full threat removal. Organizations also reassess security posture to prevent recurrence.
Post-Breach Analysis and Hardening
After recovery, security teams perform a comprehensive incident review, analyzing attack vectors, security gaps, and response effectiveness. Lessons learned inform security improvements, data policy, and threat models. Regulatory reporting may be required based on the nature of the breach and affected data. Strengthening security controls — such as enhancing logging, enforcing least privilege access, and improving user awareness training — helps reduce the likelihood of future breaches.
To counter the risk of data breaches, organizations need to implement a comprehensive security strategy that encompasses data loss prevention (DLP), encryption, access control measures, and periodic security assessments. Employing monitoring tools and establishing incident response protocols are also vital for promptly detecting and addressing potential breaches. By taking a proactive stance on data security, organizations can safeguard their valuable assets and uphold the confidence of customers, partners, and stakeholders.
Video: Global marketing company enlists Unit 42® to investigate a smishing campaign turned data breach.
Why Preventing Data Breaches Matter
While the top motive is financial gain, attackers may have other agendas — reputational damage, cyber warfare, corporate espionage, hacktivism. Bad actors often employ sophisticated techniques, such as social engineering, phishing, malware, or exploiting unpatched software vulnerabilities to bypass security controls and exfiltrate data. Once the data is acquired, they may sell it on the dark web, use it for identity theft, or leverage it for further cyber attacks on the organization or its customers.
The scope of damages resulting from a data breach are far-reaching and multifaceted, often impacting an organization — as well as its customers, employees, and stakeholders — in numerous areas, each diminishing the organization’s financial profile.
Financial Loss
Breaches aren’t cheap. Financial losses, in fact, are often the most apparent aftermath of a data breach, as organizations face direct costs to underwrite investigation, remediation, recovering lost data, and compensating affected customers. Cybersecurity insurance premiums will of course increase — and require organizations to fortify their security infrastructure. The long-term financial impact can also extend to legal settlements, penalties for non-compliance with industry regulations, and loss of intellectual property or trade secrets, hindering the organization's competitive edge and growth prospects.
Identity Theft
Identity theft resulting from a data breach can expose an organization to significant legal, financial, and reputational risks. Affected customers or employees may suffer financial or emotional harm, leading to lawsuits against the organization for inadequate security measures. What’s more, the organization may incur costs to provide identity theft protection services or compensate victims for their losses.
Breaches involving identity theft can also damage customer trust and brand reputation, resulting in lost sales and customer attrition. Additionally, organizations may face regulatory fines or penalties for failing to safeguard personal information adequately, further exacerbating financial and legal consequences.
Reputation Damage
Reputational damage from a data breach can have lasting effects on an organization's credibility, trustworthiness, and brand value. Loss of customer trust can lead to decreased sales, customer churn, and difficulty in attracting new clients. Along the same lines, public perception in the wake of breach headlines can damage business partnerships and investor confidence. In competitive industries, reputational harm can sink market share and profitability. Even attracting and retaining skilled employees may become challenging.
Legal Penalties
Organizations failing to protect sensitive data may face legal penalties and fines. The damages multiply if they are found to have violated data protection regulations such as GDPR, SOX, or HIPAA.
Organizations may face lawsuits from affected customers, employees, or business partners, resulting in costly settlements or judgments. Regulatory authorities can impose fines and penalties for inadequate security practices or failure to promptly disclose the breach. Additionally, organizations may be subject to mandatory audits, monitoring, or reporting requirements as part of enforcement actions, increasing legal costs and operational burdens.
Business Disruptions
Data breaches can disrupt business operations, resulting in downtime, lost productivity, and revenue. This unproductive time is due to teams working to mitigate damage and prevent whatever led to the loss from reoccurring.
Operational disruptions caused by data breaches can hinder productivity and require significant resources to manage incident response, system recovery, and the implementation of new security measures.
Loss of Intellectual Property
Loss of intellectual property (IP) in a data breach can dismantle an organization's competitive edge and future revenue streams. Competitors can exploit stolen IP, such as trade secrets, proprietary technology, and research findings, to overtake the organization's market position. Data breaches involving IP can also deter potential business partners or investors who may question the organization's ability to protect valuable assets.
Preventative Costs
Organizations that suffer a breach may be required to invest in additional security measures to prevent future breaches. These measures can be costly, especially if done on mandated timelines to maintain compliance or meet legal mandates.
Data Breach Reporting
Organizations must report data breaches to regulatory authorities, affected individuals, and sometimes the public, depending on the nature and scale of the incident. Legal requirements vary by jurisdiction, industry, and the type of data involved, but most regulations mandate timely disclosure.
Regulatory frameworks such as the General Data Protection Regulation (GDPR) in the European Union require organizations to report breaches involving personal data to supervisory authorities within 72 hours of discovery. Failure to comply can result in significant fines.
The California Consumer Privacy Act (CCPA) mandates breach notifications to consumers if certain thresholds of affected data are met, with penalties for non-compliance.
The Health Insurance Portability and Accountability Act (HIPAA) in the United States imposes strict reporting requirements for breaches involving protected health information, including notifications to affected individuals and the Department of Health and Human Services.
Breaches affecting 500 or more individuals must be reported to the Department of Health and Human Services (HHS), affected individuals, and, in some cases, the media within 60 days.
Breaches affecting fewer than 500 individuals must be reported to affected individuals without unreasonable delay, but notification to HHS can be included in an annual report, submitted no later than 60 days after the end of the calendar year in which the breach occurred.
Notification obligations often include details, such as the nature of the breach, the types of data exposed, potential risks, and recommended actions for affected individuals. Some regulations require direct communication through email or mail, while others allow public disclosure when a breach affects a large population of individuals. Organizations operating in multiple jurisdictions must navigate overlapping compliance requirements, which is challenging and makes incident response planning and legal consultation valuable.
Failing to report a data breach within the required timeframe can lead to financial penalties, reputational damage, and loss of customer trust. Proactive cybersecurity measures, such as encryption, access controls, and continuous monitoring, reduce the likelihood of breaches and support compliance with reporting obligations.
How Do Data Breaches Happen?
Data breaches are caused by several factors, 74% of which include the human element, either through error, privilege misuse, stolen credentials, or social engineering, according to the 2023 Data Breach Investigations Report (DBIR). DBIR also shows that 83% of breaches involved external actors, and the primary motivation for attacks remains financial gain.
When data breaches are caused by malicious actors, several attack patterns often contribute to the unauthorized access and exposure of sensitive information.
Direct Attack
Malicious actors take advantage of vulnerabilities in the IT organization and use them to gain escalated privileges or avoid security controls. In some cases, the attackers capitalize on mistakes in implementation or management. In others, they directly leverage novel attacks and vulnerabilities that organizations cannot prepare for.
Malware
Attackers leverage malicious software to infiltrate computers or networks to steal sensitive information or create tunnels granting them access to internal networks. These attacks can include ransomware that exfiltrates sensitive data while locking it from legitimate access.
Insider Threats
Internal users such as employees or contractors misuse their legitimate access to systems to steal sensitive information, which is as much an act of cybercrime as a data breach committed by a nation state. Insider threats are challenging to detect, as their access to data may appear normal and not stand out to detection-based controls looking for signs of external attack.
Physical Theft
Criminals stealing physical devices such as laptops, mobile phones, or hard drives from employees working remotely or traveling can quickly gain access to the sensitive information they contain.
When it comes to data breaches stemming from employee mistakes, the breach could likely have been avoided had the organization been aware of its data's risky position.
One way in which data breaches stem from mistakes is when inadequate access controls are in place. Data may be over-exposed when permissions are too lax, and individuals have access to sensitive information that is unnecessary for their job functions. Similarly, data may also be left in locations accessible to unauthorized individuals who can access it without authentication or effort.
Misconfigurations that lead to data breaches may occur when IT assets are initially configured. Failure to follow best practices or account for all aspects of how other cloud or network assets are configured can expose data or make it easier for attackers to gain access.
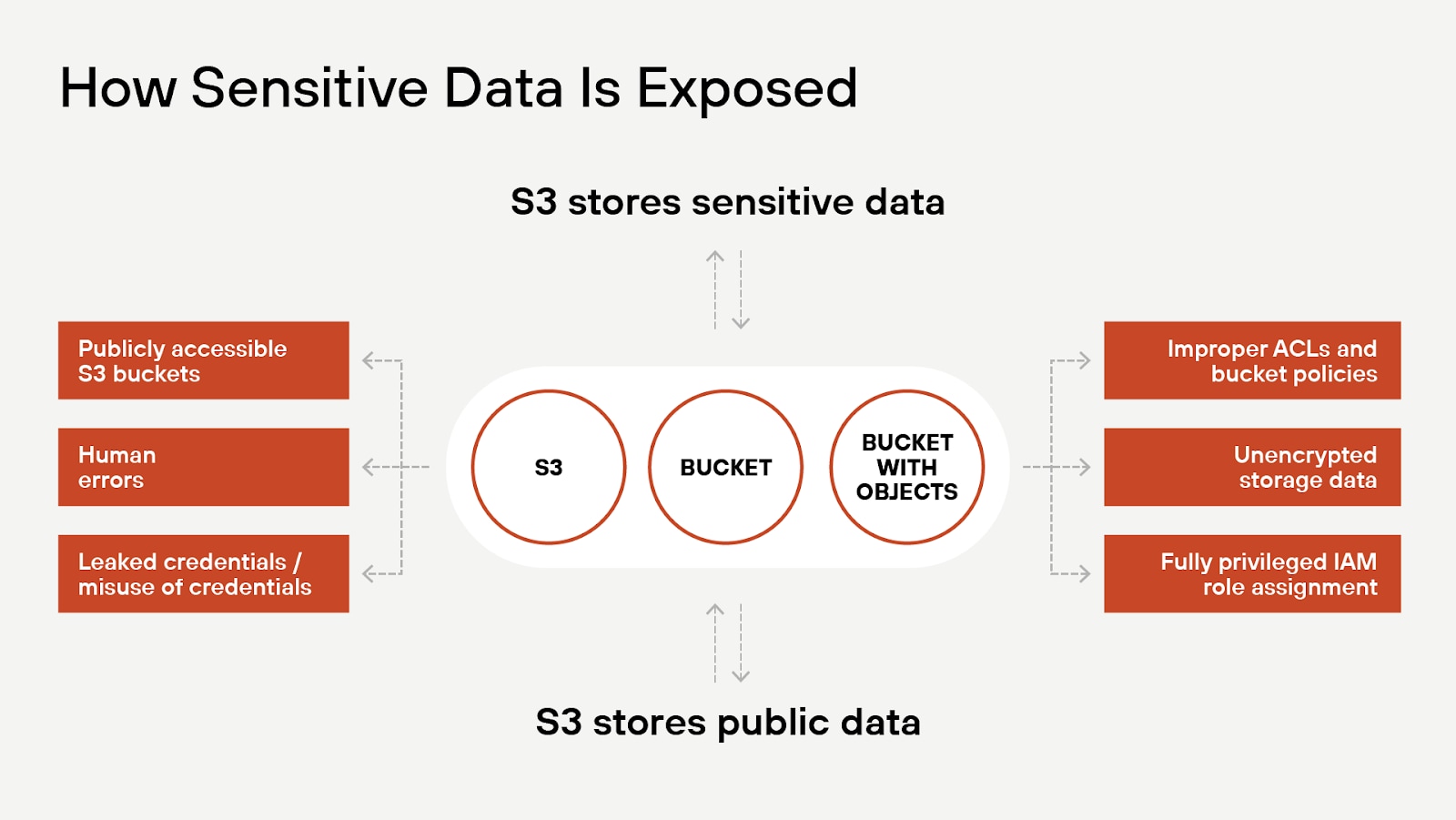
Figure 2: Potential ways that sensitive data stored in S3 buckets can be exposed.
Failure to maintain systems adequately can also make it easier for cybercriminals to lead successful attacks. Systems not patched promptly may have easily identified vulnerabilities that cyber attackers can exploit, allowing them access to systems that may otherwise have been too well secured to attack.
Alternatively, some human mistakes are unpredictable. Cybercriminals may target employees using phishing attacks to trick well-intentioned employees into revealing confidential information or inadvertently granting access to them. Additionally, employees make mistakes and may send emails with sensitive information to the wrong recipients or share data with individuals who should not have access, leading to a data breach.
The Prevalence of Data Breaches
Can it happen to you? We know data breaches have become a persistent challenge for organizations of all sizes and across all industries. Still, a part of us thinks we’re immune. But having avoided making headlines to this point doesn’t mean we won’t become the next.
As people increasingly live their lives online, sending volumes of personal data to the cloud each day, attackers seek their next payday. The Identity Theft Resource Center (ITRC) defines the surge in breaches, reporting a 78% increase in data breaches in the US, affecting over 353 million individuals.
Among notable incidents was the breach at the Indian Council of Medical Research (ICMR), which exposed an unprecedented 815 million records, primarily Covid-related health data. Across industries, software faced serious breaches with Progress Software and Okta, where over 60 million and 32 million records, respectively, were compromised. The financial sector witnessed a major breach at Latitude Financial, impacting 14 million records. In healthcare, the Meow ransomware gang attacked Vanderbilt University Medical Center, while HCA Healthcare had to notify 11.27 million patients that their information was stolen from an external storage location.
The nature of these attacks varied, with supply chain attacks targeting companies like 3CX and Cisco IOS XE, highlighting the extensive impact of such breaches.
The trend underscores the urgent need for enhanced cybersecurity measures and strategies to protect sensitive information in an increasingly interconnected and digitalized world.
Lessons from Headlining Breaches
The frequency and severity of data breaches exposes millions of individuals to identity theft, fraud, and financial loss. By looking closely at breach events, organizations can garner insights into attack methodologies, security gaps, and regulatory consequences.
The following cases examine how attackers gained access, whether regulatory failures played a role, and what organizations could have done differently to prevent or mitigate the damage.
AT&T Data Breach
In April 2024, AT&T experienced a significant data breach affecting approximately 73 million current and former customers. The compromised data included Social Security numbers, phone numbers, and addresses. The breach raised concerns about data security in telecommunications and the risks associated with large-scale customer databases.
Unauthorized access originated from AT&T’s workspace on a third-party cloud platform. Attackers exploited vulnerabilities in this external environment to infiltrate AT&T’s systems and exfiltrate sensitive customer data. While specifics on the initial entry point remain undisclosed, third-party environments often present additional risks due to shared security responsibilities and potential misconfigurations.
The incident highlighted the importance of third-party risk management, strong identity controls, and continuous monitoring. Organizations leveraging external cloud platforms must ensure vendor security practices align with internal policies and implement zero-trust principles to prevent unauthorized access. Monitoring third-party integrations and regular security assessments help mitigate risks associated with external dependencies in cloud-based infrastructures.
MOVEit Transfer Vulnerability Exploitation
In June 2024, a critical authentication bypass vulnerability (CVE-2024-5806) was discovered in the MOVEit Transfer software, a widely used file transfer tool developed by Progress Software. The vulnerability, rated 9.1 on the CVSS scale, posed a significant risk to organizations relying on MOVEit for secure data exchange.
Threat actors exploited this flaw by manipulating the SSH public key authentication process, allowing them to bypass authentication mechanisms and gain unauthorized access. Successful exploitation required attackers to have knowledge of a valid username and target an internet-facing SFTP server running the affected version of MOVEit Transfer.
Widespread exploitation of the vulnerability underscored the importance of timely patch management and proactive vulnerability scanning. Organizations using third-party software must rapidly assess and apply security updates to mitigate risks associated with zero-day threats. Continuous threat intelligence monitoring, attack surface reduction, and segmentation help minimize exposure to software supply chain risks.
Ticketmaster Entertainment Breach
In 2024, Ticketmaster Entertainment suffered a data breach resulting in unauthorized access to customer data. While specific figures on affected individuals were not disclosed, the breach raised concerns about the security of personal information in the entertainment and ticketing industry.
Threat actors exploited vulnerabilities in Ticketmaster’s systems, potentially leveraging weaknesses in third-party integrations or internal application flaws to access sensitive customer data. The exact entry point remains under investigation, but attacks on customer databases and transaction systems are common in industries handling high volumes of personal and payment information.
The incident highlighted the necessity of strong access controls, continuous security assessments, and robust third-party security measures. Organizations handling customer data at scale must ensure regular penetration testing, secure API configurations, and least-privileged access policies to limit potential attack surfaces. Data encryption, transaction monitoring, and behavioral analytics further help detect and mitigate unauthorized access attempts before significant compromise occurs.
How to Prevent Data Breaches
As the security landscape continues to change, professionals should focus on key areas to fortify their organization's cybersecurity posture and protect valuable data assets.
People and Data Asset Protection
The human factor remains a significant vulnerability in any cybersecurity strategy. Security engineers and CISOs must work together to create comprehensive security awareness programs that educate employees on the latest threats, such as phishing and social engineering tactics. Organizations should tailor these programs to different roles within the organization and provide practical guidance on how employees can protect sensitive data and avoid falling victim to attacks.
Granular Access Control
The adoption of Zero Trust security architectures has become imperative in today's multicloud environments. Shifting the focus from perimeter-based security to a granular, data-centric approach, Zero Trust emphasizes continuous validation of user identities. Security engineers should work closely with CISOs to design and implement Zero Trust frameworks, incorporating elements such as strong authentication, microsegmentation, and least-privilege access controls to reduce the attack surface and risk of data breach.
Vendor Management
Another critical area for security professionals is the growing prominence of supply chain attacks, which target third-party vendors and software dependencies to infiltrate a larger organization's network. CISOs must collaborate with procurement and vendor management teams to develop effective vendor risk assessment processes. Security engineers, on the other hand, should focus on implementing strong security controls around software development and deployment pipelines, such as secure code reviews, vulnerability scanning, and automated testing.
Automated Protection with AI and ML Technologies
The integration of artificial intelligence (AI) and machine learning (ML) in cybersecurity tools enable organizations to analyze vast amounts of data quickly to identify patterns and uncover potential threats. By leveraging AI and ML, security engineers and CISOs can create more proactive defense strategies that adapt to the ever-changing tactics of cybercriminals. Additionally, AI-powered tools can automate repetitive tasks, allowing security teams to focus on higher-level strategic planning and incident response.
Data Security Posture Management
A comprehensive data security strategy enables organizations to discover, classify, protect, and govern their cloud data to prevent data breaches. Using a unique combination of assessment and monitoring, a complete solution can be created to safeguard an organization's data. A powerful and extensive platform should provide data risk visibility in real time, helping to locate, classify, and prioritize data risk in multiple public cloud environments.
Data security posture management (DSPM) and data detection and response (DDR) capabilities redefine data security, providing significant advantages over traditional security solutions. The cloud-native and agentless approach combining DSPM, data loss prevention (DLP), and DDR equips organizations with a comprehensive data security strategy tailored to the modern threat landscape.
Data Breach FAQs
An ACL consists of a set of rules, each specifying a user or a group, the associated resource, and the type of access granted or denied. The access permissions can include read, write, execute, delete, or a combination of these actions. When a user or a group attempts to access a resource, the system checks the ACL to determine whether the requested action is allowed or not.
ACLs and bucket policies, for instance, determine who can access data in an S3 bucket. If these aren’t set up correctly, a data breach could result.
Cloud data protection is the process of securing sensitive information stored within cloud environments. It involves implementing a combination of security measures, such as encryption, access control, data backup, and data loss prevention to safeguard data from unauthorized access, tampering, or loss.
Cloud data protection also includes adherence to regulatory compliance, such as GDPR, HIPAA, or PCI DSS, to ensure the privacy and security of personally identifiable information (PII) and other sensitive data.
Often resulting from weak authentication mechanisms, misconfigurations, or compromised credentials, data access refers to unauthorized individuals gaining access to sensitive information within an organization's network or cloud environments. While it's the initial stage of a breach, it may not lead to data exposure or theft.
Data exposure, on the other hand, happens when sensitive information is made accessible to unauthorized individuals, usually due to misconfigurations, software vulnerabilities, or human errors. For example, a misconfigured cloud storage bucket with public access could expose sensitive data to anyone with the link. When unauthorized individuals see or access the exposed data, it constitutes unauthorized access.
Data theft involves the actual unauthorized acquisition, copying, or transfer of sensitive information from an organization's systems with the intent to use the data for personal gain or malicious activities. Data theft is a serious offense and inflicts the most severe outcome of a data breach, as it typically results in direct harm to the affected organization and individuals.

