Zero Trust is an opportunity to modernize how we secure cloud transformations, and it begins with cloud identities and infrastructure.
Public cloud adoption comes with an increasing sprawl of workloads and infrastructure, as well as ways to access these critical resources. This sprawl is accelerated in part by infrastructure as code (IaC), which offers DevOps teams a predictable way to repeatedly deploy cloud resources and infrastructure, and cloud identities that offer the first line of defense for cloud APIs. However, permissions are hard to manage and tend to become overly permissive rather than deal with granular requirements and misconfigurations in IaC tend to proliferate, increasing the chance of a cloud breach or over privileged users and broadening the attack surface.
These security gaps are a result of implicit trust. Applying Zero Trust principles can catch issues earlier and limit the impact of permissions to minimize risks.
What is Implicit Trust for Cloud Identities and Infrastructure Configurations
Cloud Identities and Entitlements
As organizations move to the cloud, they are responsible for managing the identities of users – both human and non-human –and their access permissions to other cloud infrastructure. As a company’s cloud footprint grows, so do the number of users and the number of permissions to track, worsening the challenge of managing privileges.
Gartner recently reported that "the vast majority of granted entitlements in IaaS are unnecessary. More than 95% of accounts in IaaS use, on average, less than 3% of the entitlements they are granted, which greatly increases the attack surface for account compromises."
Granting identities and assigning over-privileged access are examples of implicit trust. Where can implicit trust go wrong?
A trusted user could have their credentials compromised. If the compromised identity has oversized permissions, the bad actor has the ability to create a large blast radius. They can access existing machines or storage buckets to exfiltrate sensitive data or deploy new virtual machines for crypto mining.
Threat researchers from Unit 42 showed the impact of one overly permissive identity in their 2H2020 Cloud Threat Report, demonstrating how a single misconfiguration could result in millions of dollars in potential damages.
Cloud Infrastructure and IaC
Companies moving to the cloud often take on DevOps principles to automate cloud management workflows. DevOps teams use various open source repositories, software libraries, and IaC templates to repeatedly configure and deploy cloud infrastructure.
Similar to cloud identities, many teams implicitly trust the software repositories and code are safe from vulnerabilities and risky configurations. However, Unit 42 threat researchers scanned various open source repositories and registries and found that 63% of third-party IaC templates contained insecure configurations.
Enforcing Zero Trust principles can help minimize identity and configuration driven risk.
Zero Trust for Cloud Identities and Infrastructure
Zero Trust is a strategic cybersecurity approach which eliminates implicit trust and enforces cybersecurity checks across any cloud interaction. It is an opportunity for security and DevOps teams to ask the right questions about their cloud identities and infrastructure:
- Do you trust the identities accessing the cloud infrastructure?
- Are identities being assigned with the right privileges?
- Do you trust the code integrity along the development and deployment process?
- Do you trust your third-party infrastructure as code (IaC) template?
A requirement for minimizing the blast radius for compromised attacks and vulnerabilities is to create a least-privilege model for all identity and access management (IAM) accounts and to add automated guardrails for IaC pipelines.
For cloud identities, the best approach is to enforce least privilege access - validate every identity and only grant the permissions required by each identity. Users and services should only have the specific ability to create, see, modify, and delete the specific resource types that are relevant to their role. Wildcard access should never be permitted. Even with this in place, monitor account behavior to identify and block anomalous usage.
For cloud infrastructure, enforce security checks across the entire development lifecycle. Instead of waiting for runtime to identify misconfiguration, begin by scanning code and IaC templates for misconfigurations before anything is deployed. As you identify flaws and vulnerabilities during the development lifecycle, provide actionable feedback to remediate issues. It is important to integrate security checks into CI/CD workflows. This allows security teams to block insecure code from being integrated into the main branch and from being deployed into production.
How Prisma Cloud helps with Zero Trust for Identities and Infrastructure
Prisma Cloud by Palo Alto Networks is the industry’s most comprehensive Cloud Native Application Protection Platform (CNAPP). Cloud Identity Security analyzes cloud identity and access management (IAM) policies for overly permissive access. Further, over time Prisma Cloud analyzes usage patterns to eliminate unused entitlements and create a least privilege access model.
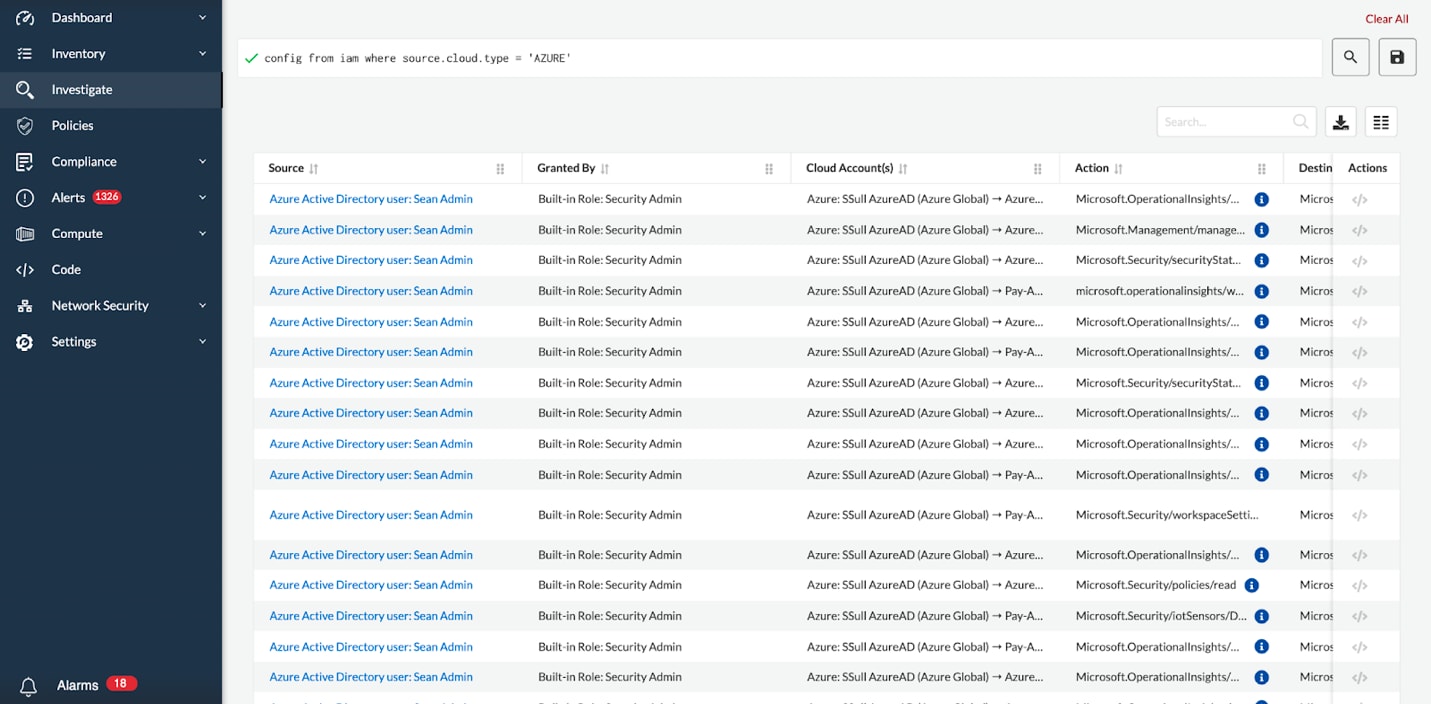
With Cloud Code Security, developers receive feedback at every step of the software development lifecycle. Policy violations are prioritized by severity and feedback includes fixes in code and ready to commit to resolve misconfigurations. Our easy to add and manage integrations add in guardrails to block insecure code from becoming insecure cloud infrastructure.
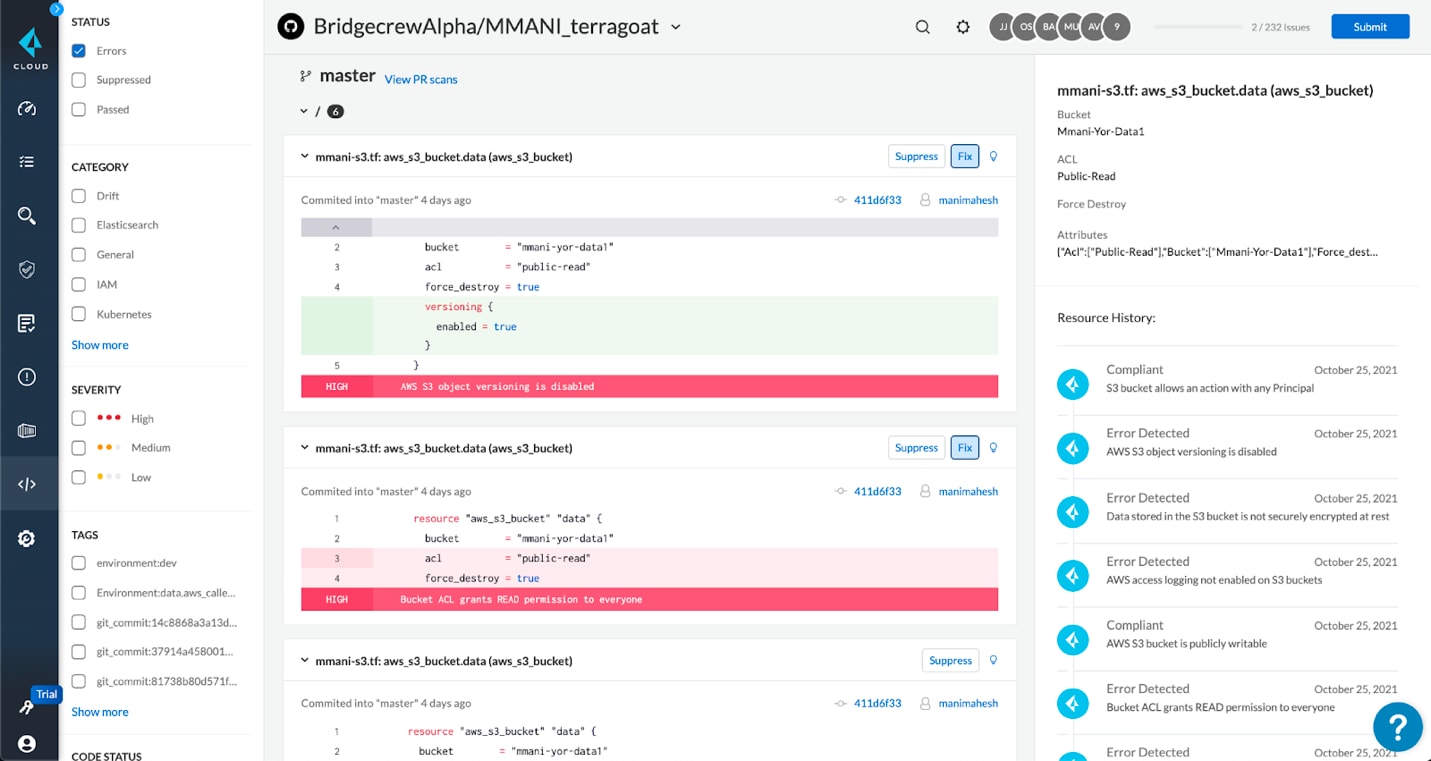
Learn More
Prisma Cloud makes it simple for security teams to enforce Zero Trust principles across the entire development lifecycle.
To learn more about Zero Trust principles and how they fit into our vision for Prisma Cloud, check out our fireside chat on LinkedIn Live on Feb. 8. Palo Alto Networks product leaders will offer insights on how to adopt a Zero Trust strategy for your cloud native applications.