In the cybersecurity maze, finding and addressing vulnerabilities is like chasing shadows. Every point of weakness opens a door to potential threats. While many organizations rely on the CVE system to identify and track these threats, the CVE system can leave you exposed. Why? Because vulnerabilities slip through the cracks. Let's explore how.
Not All Vulnerabilities Have a CVE ID
Full Disclosure
Vulnerabilities need to go through a responsible disclosure process, which begins with security researchers reporting found vulnerabilities to the vulnerable project safely. Disclosure policies usually hold a 90-day (60-120 days) disclosure deadline. Vulnerability details can be publicly shared after this deadline, or earlier if a fix becomes available.
But vulnerabilities for which a responsible disclosure process has not been carried out still exist, and many have been openly discussed on public platforms like GitHub prior to receiving a CVE. Researchers or developers often voice their concerns, perhaps due to nonresponsiveness from project maintainers or perhaps without realizing they’re describing a vulnerability within the responsible disclosure process.
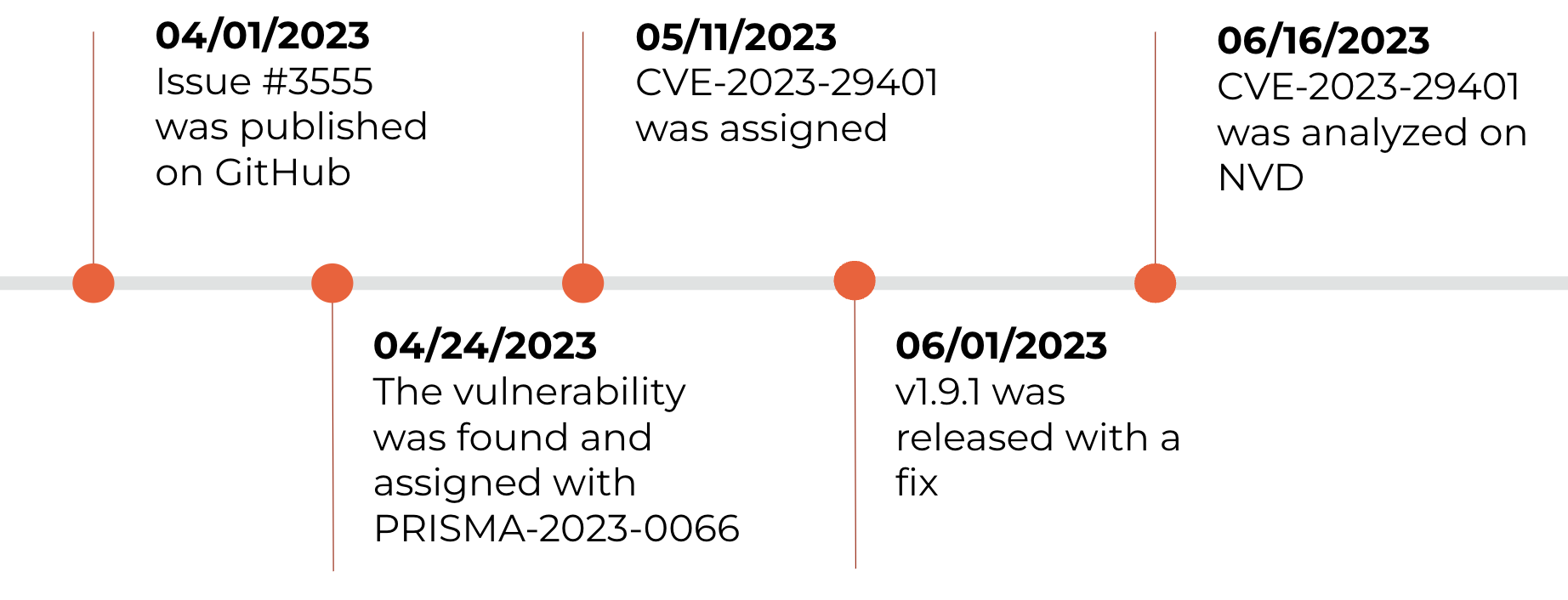
For example, let’s look at issue #3555 in the github.com/gin-gonic/gin repository, which discloses a security issue. While this issue was introduced on April 1, 2023, a CVE was assigned to this issue only on May 11 and fully analyzed in NVD on June 16. Meanwhile, on April 24, we posted PRISMA-2023-0066 to cover the gap, 17 days before the CVE and 53 days before the National Vulnerability Database (NVD) analysis.
Quick Fixes
Developers may patch a vulnerability without recording a CVE. Their reasons vary — from avoiding negative attention to arguing that the responsibility to fix it belongs to the user and not the project. Or maybe they reason that an issue requiring only a minor fix isn’t worth the CVE process.
At Prisma Cloud, rather than initiating a dispute process for all cases, we lean toward providing an advisory notice to Prisma Cloud customers — using PRISMA IDs.
The Role of PRISMA IDs
PRISMA IDs are not zero days. They represent security issues publicly discussed or fixed but not assigned a CVE (yet).
While monitoring open-source vulnerabilities, our research team identifies those you need to be aware of and, when applicable, assigns PRISMA IDs to them. From 570 vulnerabilities assigned PRISMA IDs, 60 have been replaced with a CVE ID approximately 108 days on average after publishing the PRISMA ID. This list also includes critical vulnerabilities, such as SpringShell (CVE-2022-22965), CVE-2023-25813 (sequlize) and CVE-2022-25845 (com.alibaba:fastjson).
Let's consider another example, noting the timeline of CVE-2021-4279 for the npm package fast-json-patch:
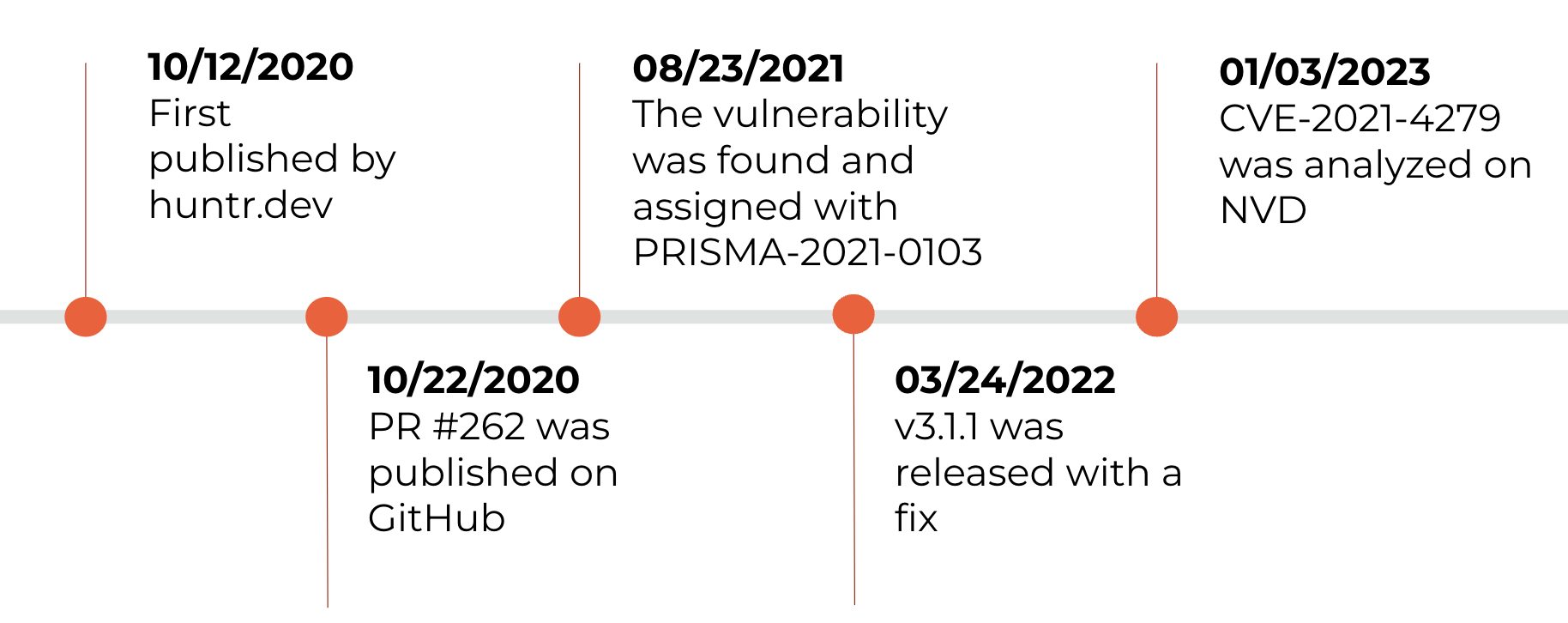
Our team assigned PRISMA-2021-0103 213 days before the fix rolled out, and 498 days before a CVE was published and analyzed in NVD. All this time, longer than a year, we tracked the vulnerability under its PRISMA ID, keeping our users informed and proactive. Interestingly, the vulnerability had been used in a CTF challenge, and an unmerged PR in the JSON-Patch Project’s repository — referenced by PRISMA-2021-0103 — was even mentioned in a few CTF write-ups.
Why Create PRISMA IDs?
Through PRISMA IDs, we’re able to equip you with high-impact information to fortify your defenses. Think about the rise in supply chain attacks. If our researchers can pinpoint these security issues, attackers can too. A vulnerability lacking a CVE ID isn’t likely to trigger security scanners. PRISMA IDs serve as your early warning system.
Selective Assignment: We assign PRISMA IDs only when necessary. If a project disputes the 'vulnerability’ classification of an issue, we might still consider it important for you to know about. You may, for instance, need to validate certain parameters or use other tools.
Timeline Efficiency: Our PRISMA IDs get to you well before CVEs, allowing you to act on vulnerabilities faster.
Stay One Step Ahead with Prisma Cloud
Cloud security can seem like a cat-and-mouse game. Prisma Cloud lights up the vulnerabilities in your open-source code and helps you outpace potential threats. Thanks to our Unit 42 researchers’ work, you can map your attack surface and protect your organization from new vulnerabilities.
If you’d like to learn about Prisma Cloud, take it for a free 30-day test drive.