Prisma Cloud’s new release provides support for web applications and APIs that use service mesh technologies from Istio and Linkerd and support for applications running on Windows hosts, as well as many additional new capabilities.
Service Mesh Support
Modern cloud native applications are developed as a set of distributed microservices. A service mesh is a dedicated infrastructure layer that allows developers to seamlessly add capabilities like observability, traffic management, and security, without changing application code.
According to the 2020 CNCF survey, almost 1/3 of all respondents already use a service mesh in production systems.
While service mesh technologies, such as Istio and Linkerd, help application developers with observability, traffic management and security, they don't not provide the full breadth of coverage against application layer attacks such as OWASP Top 10, bot-based activity and API abuse.
Given Palo Alto Networks’ commitment to provide a best-of-breed Web Application and API Security solution for cloud native applications, we are excited to announce the integration of Prisma Cloud’s WAAS module with service mesh technologies provided by the Istio and Linkerd projects.
This new integration with Istio and Linkerd does not require any code or configuration changes from WAAS customers, and enhances the protection for web applications and APIs with best of breed application layer defenses.
Support for Defender Agents Running on Windows Hosts
The new release of the Prisma Cloud WAAS module now provides application-layer protections for web applications and APIs which are deployed on Windows hosts and virtual machines.
Event Log Scrubbing
When a security event is triggered by the WAAS module (e.g. a web attack), Prisma Cloud will store certain attributes of the HTTP request and response such as the URL, Query parameters or parts of the message body which are associated with the event. In some scenarios, web applications and API transactions may include sensitive user information such as PII, credit card details or social security numbers as part of the HTTP request or response. Sensitive data sanitization is important for protecting user privacy as well as to ensure that logs comply with relevant regulations (e.g. PCI, GDPR, HIPAA, amongst others).
In order to support customers that are required to comply with such regulations, Prisma Cloud WAAS introduces a new capability dubbed “Log Scrubbing,” which provides the ability to define custom rules for redacting event logs based either on the location of the data, or by performing a text pattern match and replacing the sensitive information with a predefined placeholder text.
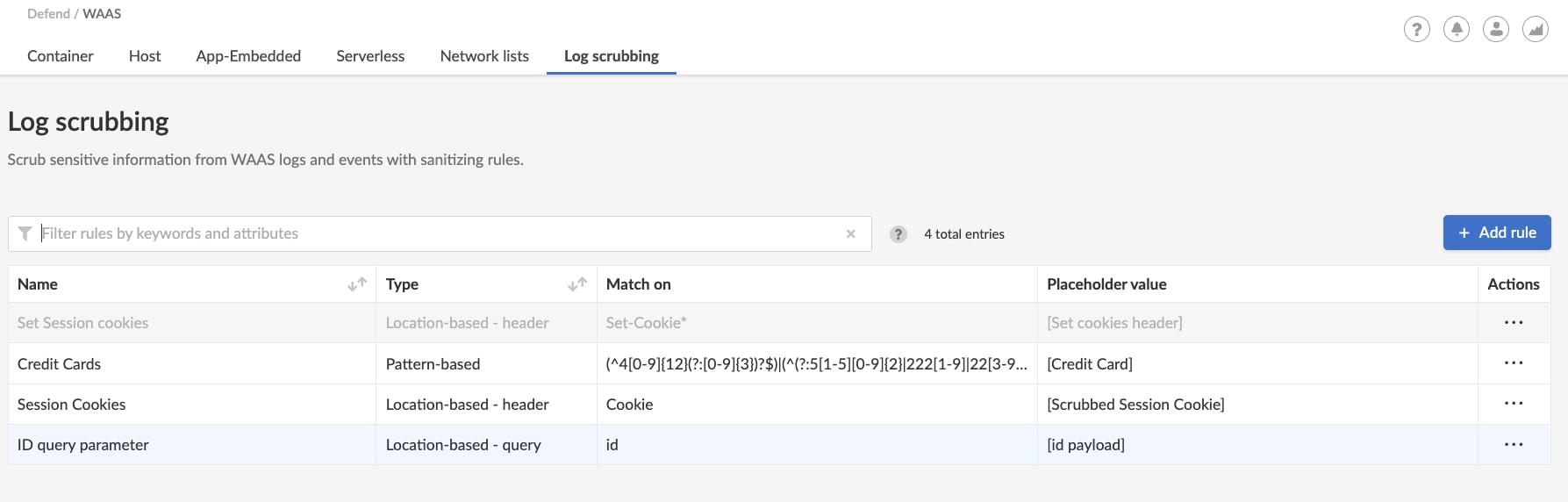
The new log scrubbing capability can be accessed through the Defend → WAAS → Log Scrubbing menu.
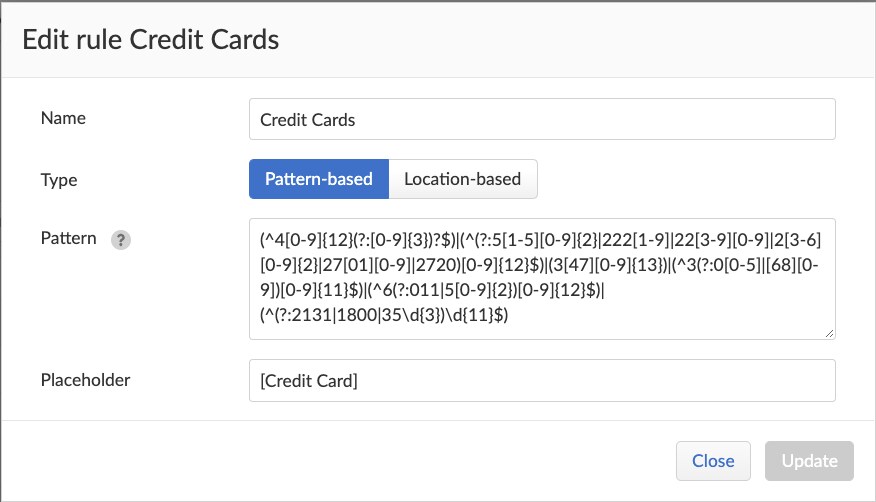
Head to Defend > WAAS to see the options now available.
Connectivity Monitor
Properly protecting applications and APIs against application-layer attacks is never an easy task, which may become even more complex when dealing with distributed cloud-native applications. Creating an accurate and efficient security configuration is critical and requires deep visibility into network and application health.
In order to ease the WAAS deployment process and provide users with assurance regarding application and configuration health, we are releasing a new capability dubbed “WAAS connectivity monitor,” which as the name implies, constantly monitors the connection between WAAS and the protected application. Relevant information is aggregated and contains data on pages served by WAAS as well as application responses. In addition, the new feature provides easy access to WAAS related errors registered in the Defender logs (Defenders send logs to the Console every hour). The connectivity monitor tab is available when clicking on an image or host protected by WAAS through the Radar view.
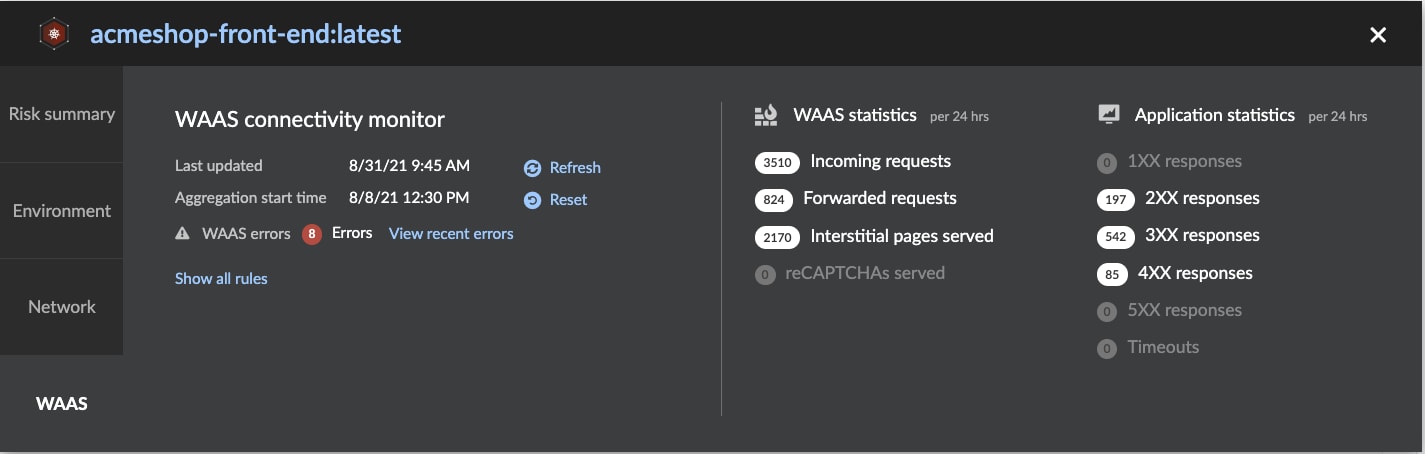
24-hour Aggregated data includes information such as:
- Total incoming requests handled by WAAS
- Requests forwarded to the application by WAAS
- Number of interstitial pages served (as part of the bot risk management capability)
- Number of CAPTCHA challenges served (as part of the bot risk management capability)
- HTTP response status code statistics
In addition, errors related to deployment health are also surfaced through this feature, such as:
- TLS certificate no longer valid
- Incoming requests with no application responses (multiple timeouts)
- Multiple 5XX responses received from the application in a short space of time
- Slow responses
Additional Enhancements
Palo Alto Networks is committed to providing the best possible solution for protecting cloud native web applications and APIs. As such, we are constantly listening to feedback and new requests from our customers. In this release, we included a slew of new features and enhancements based on feedback from our customers. These enhancements include:
- Extending WAAS custom rules to also scan HTTP response bodies
- Allowing adding policy exceptions directly from within the event viewer based on specific audits
- A console notification alerting users when a new WAAS virtual patch has been pushed from the Prisma Cloud Labs
- Ability to enforce minimum TLS version to prevent downgrade attacks
- Support for HTTP Strict Transport Security (HSTS) (RFC 6797) enforcement
- View TLS information on certificates that have been uploaded to an app config, so that users can confirm the certificate that was uploaded and monitor its expiration
- The Console will alert customers when a TLS certificate is about to expire or has already expired.
To learn more about Web Application and API Security, visit our detailed product webpage.