No Zero Trust initiative in the cloud is complete without verifying all network access across workloads and applications.
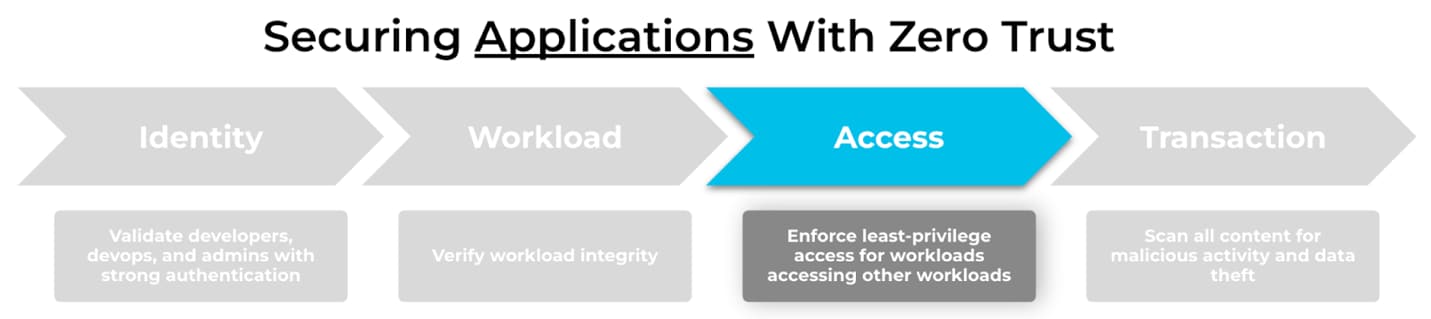
Zero Trust is a cybersecurity concept that companies are applying to users, applications, and infrastructure. Today, organizations adopt Zero Trust principles by removing implicit trust from every identity, workload, access request, and data transaction on the network - always verify their integrity across every digital interaction.
When moving to the cloud, developer and DevOps teams often take on modern compute architectures and development practices in order to build and deploy applications faster. Cloud native environments introduce new security risks and challenges which change the way security teams approach Zero Trust principles.
Enforcing least privilege network access between workloads and applications is critical to a Zero Trust architecture in the cloud.
Cloud Native Development Without Automated Security Facilitates Risk
In a cloud native world, change is constant. Developers and DevOps teams have operationalized the automation of deploying, scaling, and removing microservices rapidly - sometimes in a matter of seconds. However, if security workflows cannot keep up, this can lead to toxic outcomes.
Moreover, Palo Alto Networks Unit 42 Cloud Threat Researchers found that between April and June 2020, firewall configurations allowing all traffic to Kubernetes clusters increased by an astounding 122%. In other words, this implies trusted network access within the cloud.
What happens when there is a cloud breach?
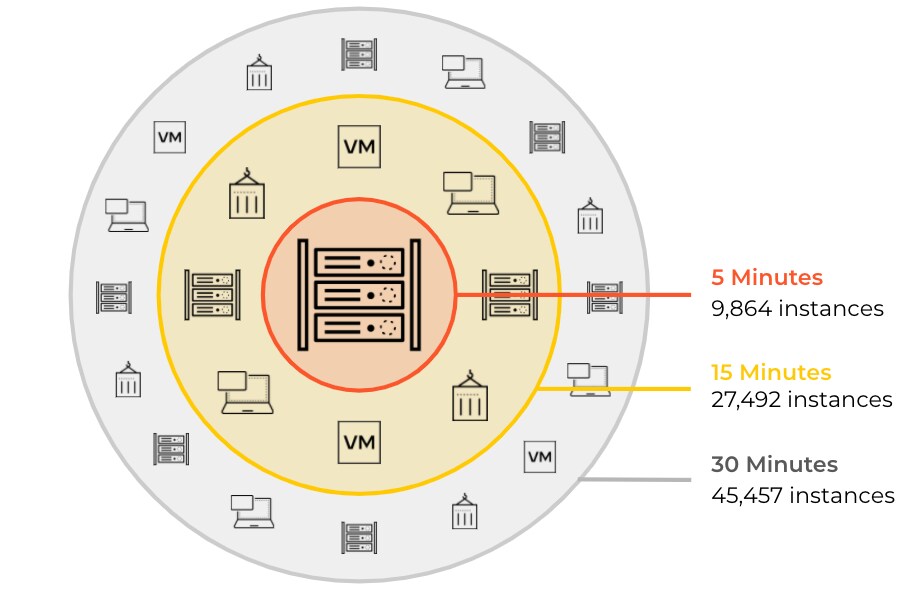
In the event of a breach, attackers leverage privileged network connectivity to move laterally within the cloud fast. For example, threat variants like malware can spread to as many as 45,000+ instances in a matter of 30 minutes.
Organizations who have figured out how to accelerate their cloud workload adoption must also understand how to integrate network security into their automation workflows.
What Does Zero Trust Mean for Network Access
At its core, Zero Trust seeks to eliminate implicit trust throughout the enterprise by continuously validating all digital transactions. When it comes to workloads accessing other workloads, all communications between entities must follow a least-privilege approach. The goal of this requirement is to minimize the blast radius of any security incident, by limiting the ability of an attacker to implement a lateral move across cloud applications.
If you want to reduce the risk of lateral movement, you must remove implicit trust from workloads, applications, and connection requests within the cloud ecosystem — always verify before authorizing.
Establishing trust between workloads in a cloud native environment may sound difficult, but Palo Alto Networks can help ease the journey to Zero Trust.
How We Can Help
Prisma Cloud Identity-Based Microsegmentation together with VM-Series and CN-Series software next-generation firewalls (NGFWs) deliver on the promise of Zero Trust for applications. The Palo Alto Networks portfolio combines workload identity with application context to enforce continuous least privilege access with Zero Trust principles.
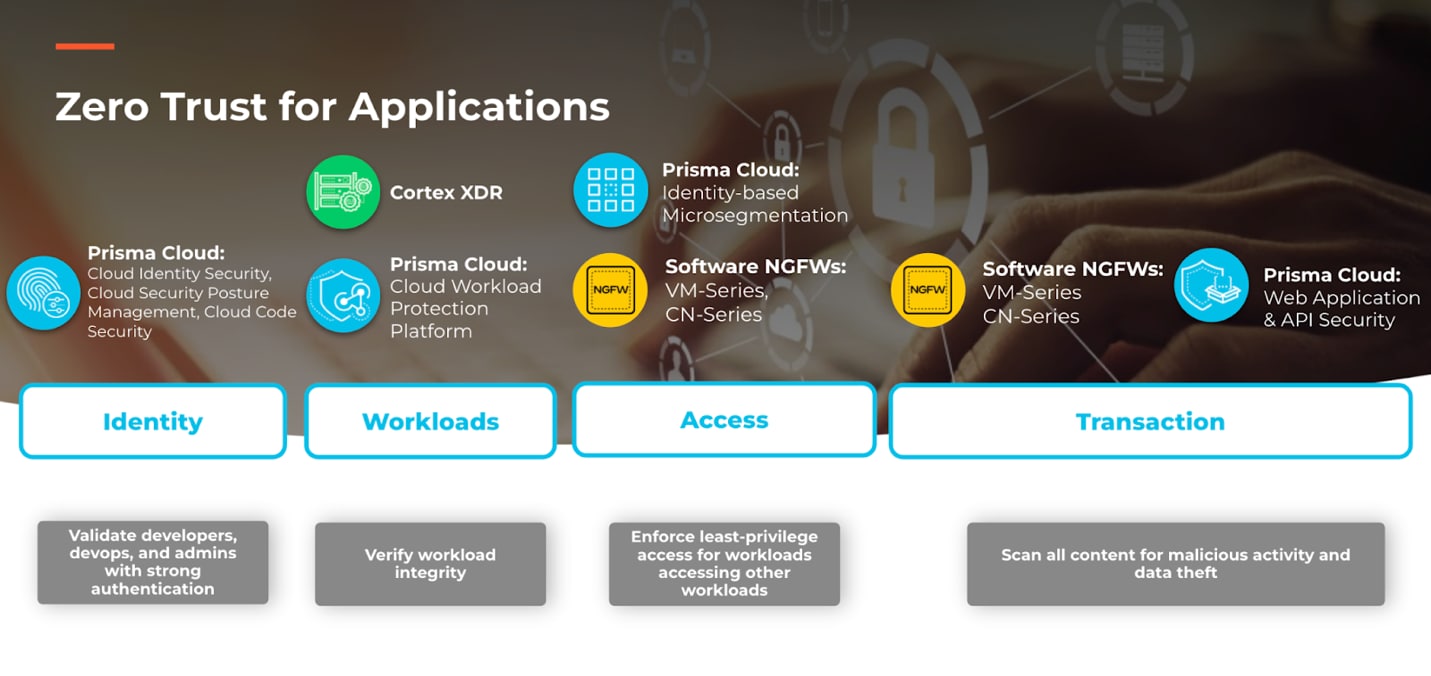
Prisma Cloud
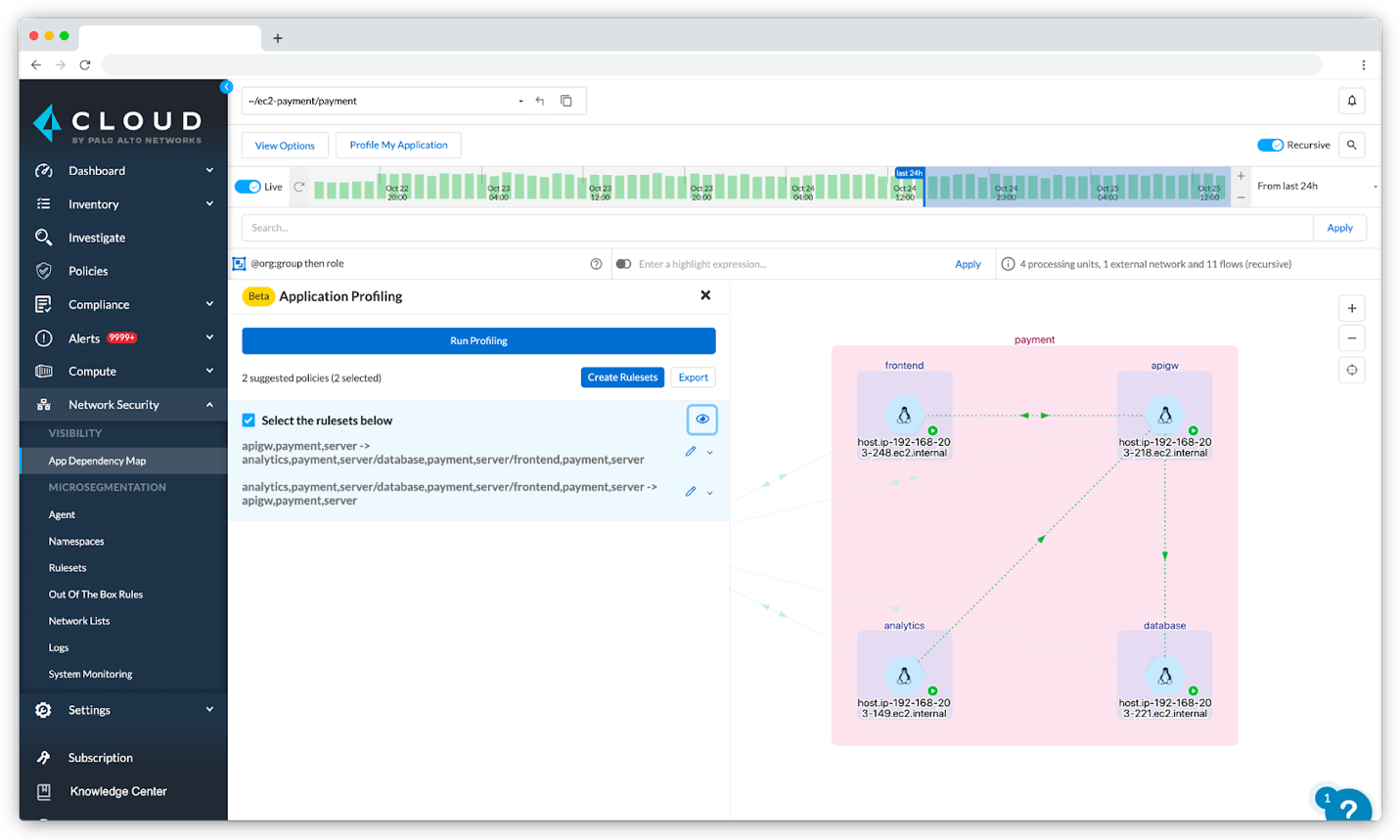
Prisma Cloud delivers microsegmentation for hosts, VMs, and containers across on-premise, cloud, and hybrid cloud environments. With Identity-Based Microsegmentation, security teams can visualize application dependencies, verify connectivity between workloads, and limit access between workloads.
Rather than IP-based policy, administrators manage segmentation policy using workload identities. For example, allow web microservices to database microservices or separate developer instances and production instances.
For fast moving cloud native environments, Prisma Cloud offers microsegmentation policy-as-code. This enables DevOps teams to codify identity-based segmentation policy and integrate policy-as-code files into continuous deployment pipelines. As applications are built and deployed, microsegmentation policy is deployed with the application ensuring new workloads enforce least-privilege network access.
For cloud environments without mature DevOps models, Prisma Cloud makes microsegmentation policy creation simple. With a single click, Prisma Cloud uses learned traffic patterns to automatically generate optimal microsegmentation policy for any application.
Prisma Cloud is purposely built to help organizations simplify and accelerate their Zero Trust adoption for applications inside and across clouds.
Software NGFWs
The software NGFWs deliver precise application access controls to protect hosts, Kubernetes, and data across data centers, cloud, and hybrid cloud environments. This is made possible with App-ID™, a patented and industry-leading technology built into the software NGFWs. App-ID identifies applications within traffic regardless of their port, protocol, and evasive tactics.
As workloads access other workloads, software NGFWs inspect traffic at layer 7 and leverage App-ID to classify applications and enforce application access control. For example, instead of allowing all traffic on tcp/443, the software NGFWs can authorize Slack for instant messaging but block file transfer requests.
The software NGFWs come built-in with policy optimizer, a workflow that helps administrators identify overly permissive security policies and safely remove unused App-IDs without worry of application availability.
VM-Series and CN-Series NGFWs are engineered to continuously verify all application traffic and apply context-based policies as you move to the cloud.
Learn More
No Zero Trust initiative is complete without an evaluation of existing privileged access. Together, Identity-Based Microsegmentation and software NGFWs consistently enforce context-based access policies to workloads and applications.
If you want to see how Prisma Cloud Identity-Based Microsegmentation works in your environment, then request a 30-day trial for Cloud Network Security. If you want to get your hands on the software NGFWs, then sign up for an ultimate test drive.