As a security analyst, staying up-to-date on the latest threats is a crucial part of your job. This can be a time-consuming task, especially if you are manually researching vulnerabilities, exploits, viruses, and spyware. That's where Threat Vault comes in.
Threat Vault is a threat intelligence platform integrated into Cortex XSOAR, a security orchestration, automation, and response (SOAR) platform. With Threat Vault, you can easily research the latest threats and see how they can be detected and prevented by Palo Alto Networks’ Next-Generation Firewalls.
One benefit of Threat Vault is that it helps automate workflows. Instead of manually researching threats, you can use Threat Vault to quickly and easily access the information you need. This frees up your time to focus on critical threat analysis and response.
Threat Vault can help you get contextual information on these common threats when performing an investigation in your security operations center (SOC):
- Viruses - Piece of code injects itself into an application.
- Worms - Malware that exploits software vulnerabilities and backdoors to gain access to an operating system.
- Trojans - Malicious code or software that poses as an innocent program, hiding in apps, games, or email attachments.
- Spyware - Malicious actors gain access to an unsuspecting user’s data, including sensitive information such as passwords and payment details.
How Does Threat Vault Work?
Threat Vault gathers threat intelligence from a variety of sources, including data from third-party providers and Palo Alto Networks' own research. This information is then organized and stored in a centralized location, making it easy to access.
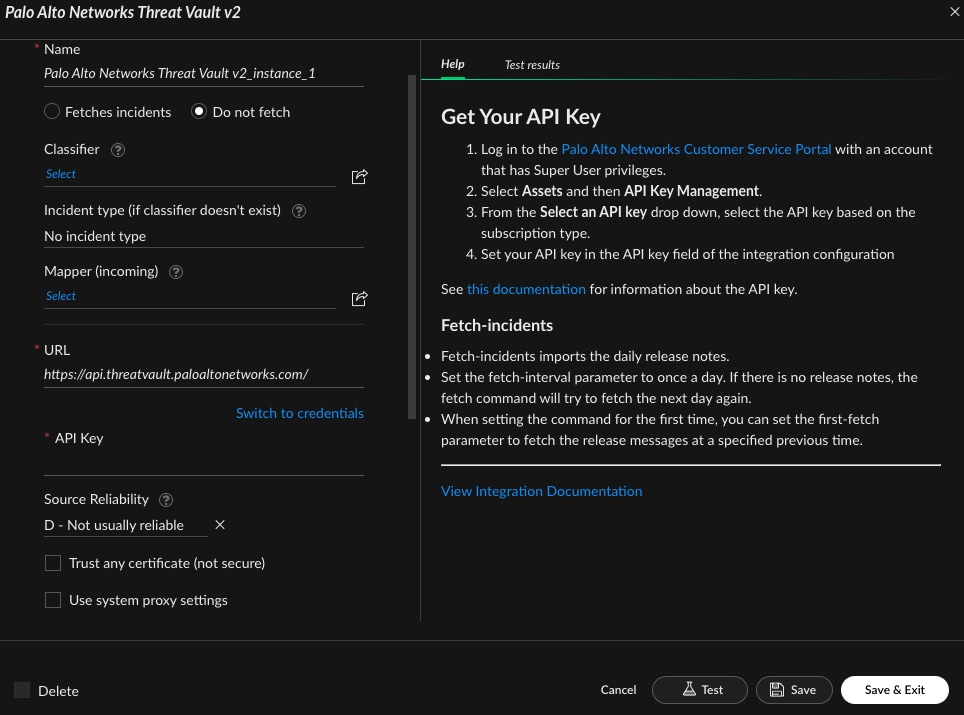
To use Threat Vault, simply log in to Cortex XSOAR and access the Threat Vault integration. From there, you can search for specific threats or browse the latest threats by category.
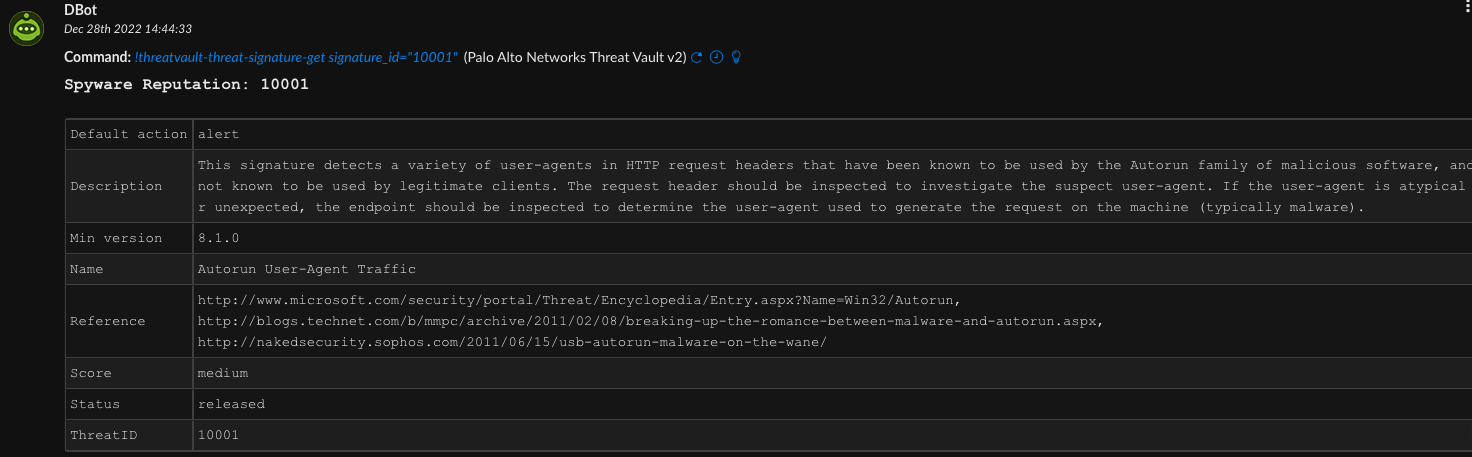
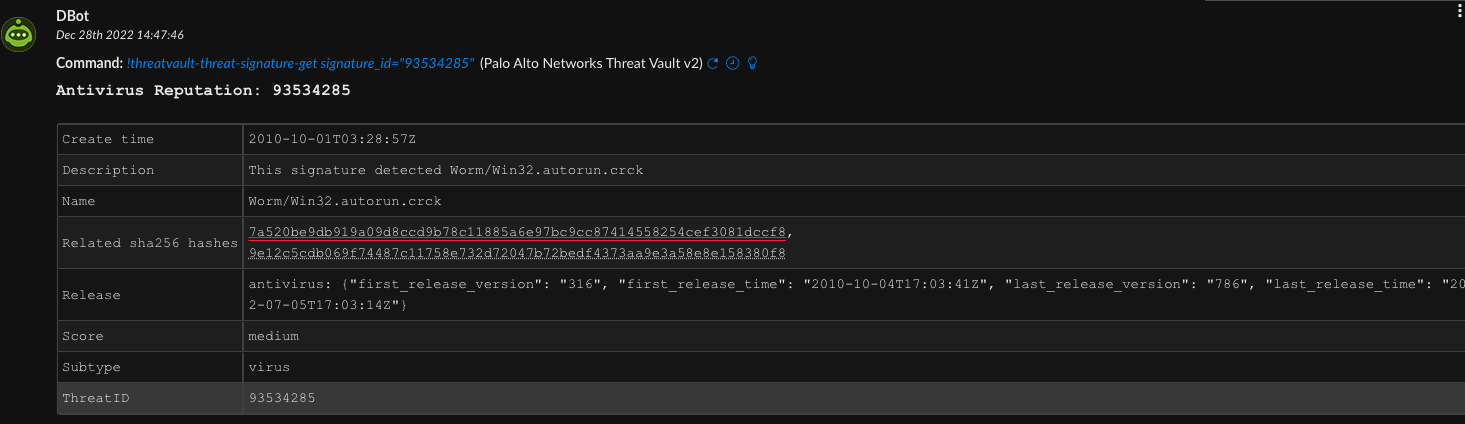
You can also search for threats that are associated with a specific type, or vendor, or CVE in case you want to perform a more speaker-headed investigation.
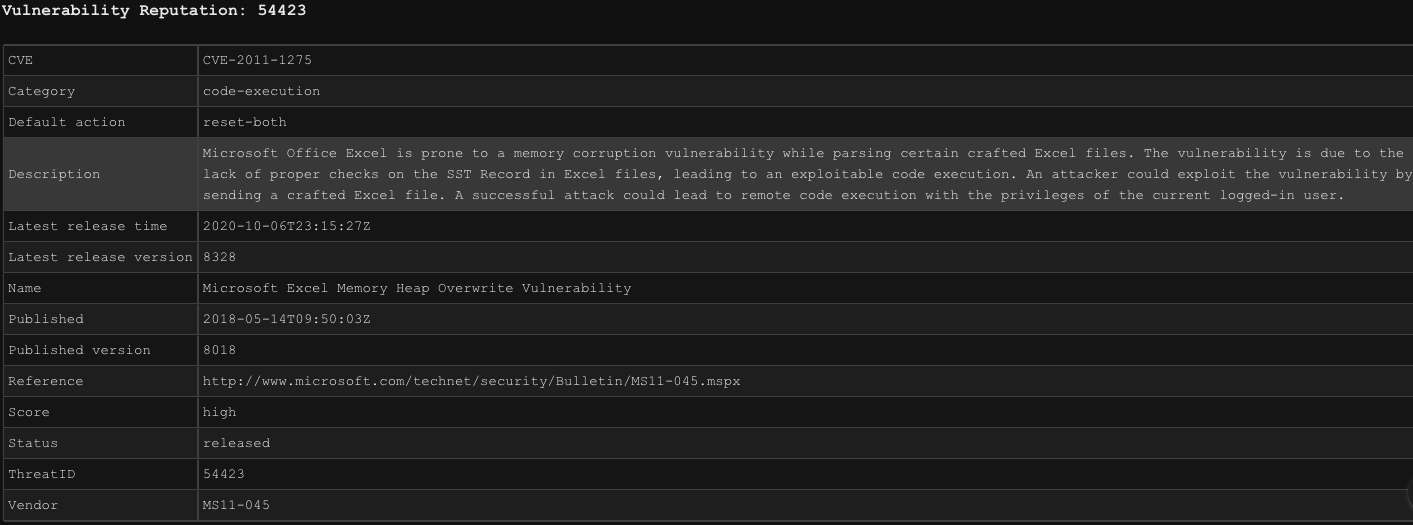
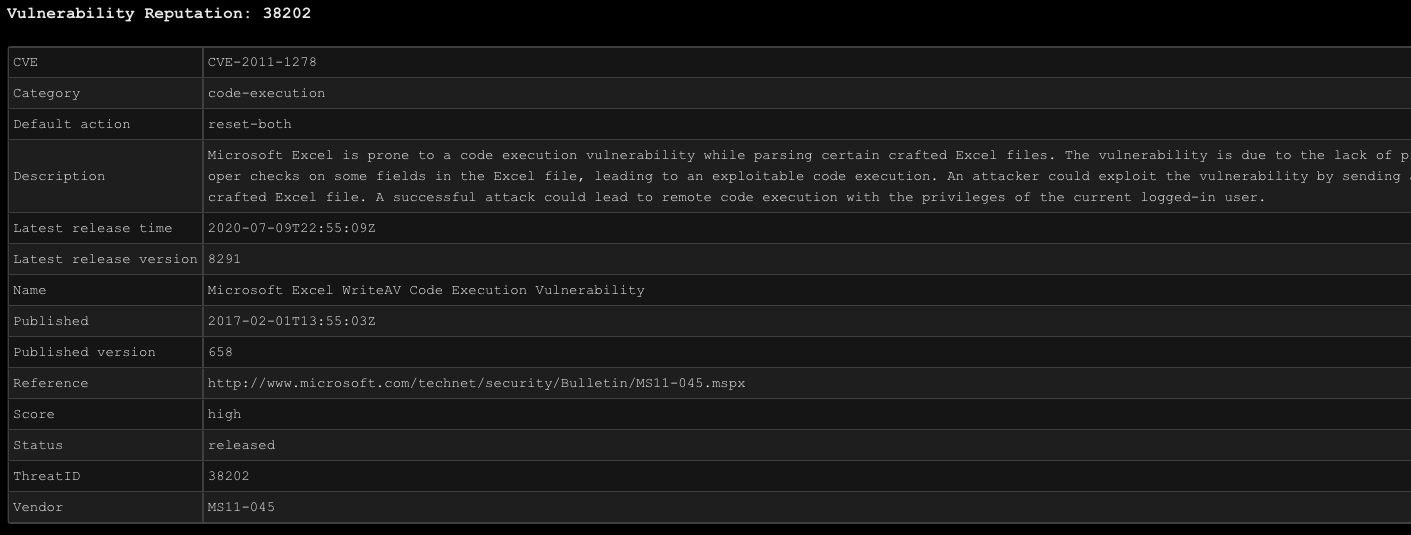
The Full Benefits of Threat Vault
Threat Vault can also be used to see how specific threats are detected and prevented by Palo Alto Networks’ Next-Generation Firewalls. But Threat Vault doesn't just provide information on the latest threats, it can automate your workflow by creating incidents in Cortex XSOAR. For example, you can set up a daily incident that fetches the Threat Vault release notes and automatically creates an incident in Cortex XSOAR. This can help you stay up-to-date on the latest threats without manually checking for new information.
Another feature of Threat Vault is its ability to provide actionable intelligence. It not only provides information about the latest threats but also provides recommendations for how to mitigate those threats. This can be incredibly valuable to security analysts, as it helps prioritize efforts and make more informed decisions about how to protect their organization.
Conclusion
Threat Vault is a valuable tool for security analysts looking to automate their workflows and stay up-to-date on the latest threats. By providing access to actionable intelligence and integrating with other security tools and platforms, Threat Vault helps you quickly and easily research and respond to threats, freeing up your time to focus on more important tasks. And with the ability to create incidents in Cortex XSOAR based on Threat Vault release notes, you can stay informed about the latest threats without having to check for updates manually.
For more information on the Threat Vault content pack, refer to the pack documentation here. If you like these ideas or would like to suggest other ideas, please collaborate with us through the Cortex XSOAR Aha page. Please suggest ideas or vote for others.
To learn more about how you can automate security operations with Cortex XSOAR, check out our virtual self-guided XSOAR Product Tour
We also host virtual and in-person events, so check here for upcoming ones.