This post is also available in: 简体中文 (Chinese (Simplified)) 日本語 (Japanese)
Given the ubiquity of the Apache Log4J library in apps, you are in a dead heat to find and fix the vulnerability before it can be exploited.
Cortex XSOAR has created a first responder kit that helps you automate and speed your response. Here are some steps from the playbook:
- Data extraction & enrichment—collection of indicators suspected of trying to exploit the relevant CVEs such as CVE-2021-44228, CVE-2021-45046 and CVE-2021-45105
- Threat hunting—searching for IOCs across your SIEMs, Palo Alto Networks Panorama and XDR including advanced hunting for behavioral detection with Splunk and QRadar, hunting for Palo Alto Networks IPS signature with Panorama, hunting for known exploitation patterns on your servers using Cortex XDR
- Remediation—initiate blocking via firewall EDLs or manually, collect and present available detection rules and signatures
- Mitigation—provide Unit42 recommendations and links to the patch for further analyst investigations
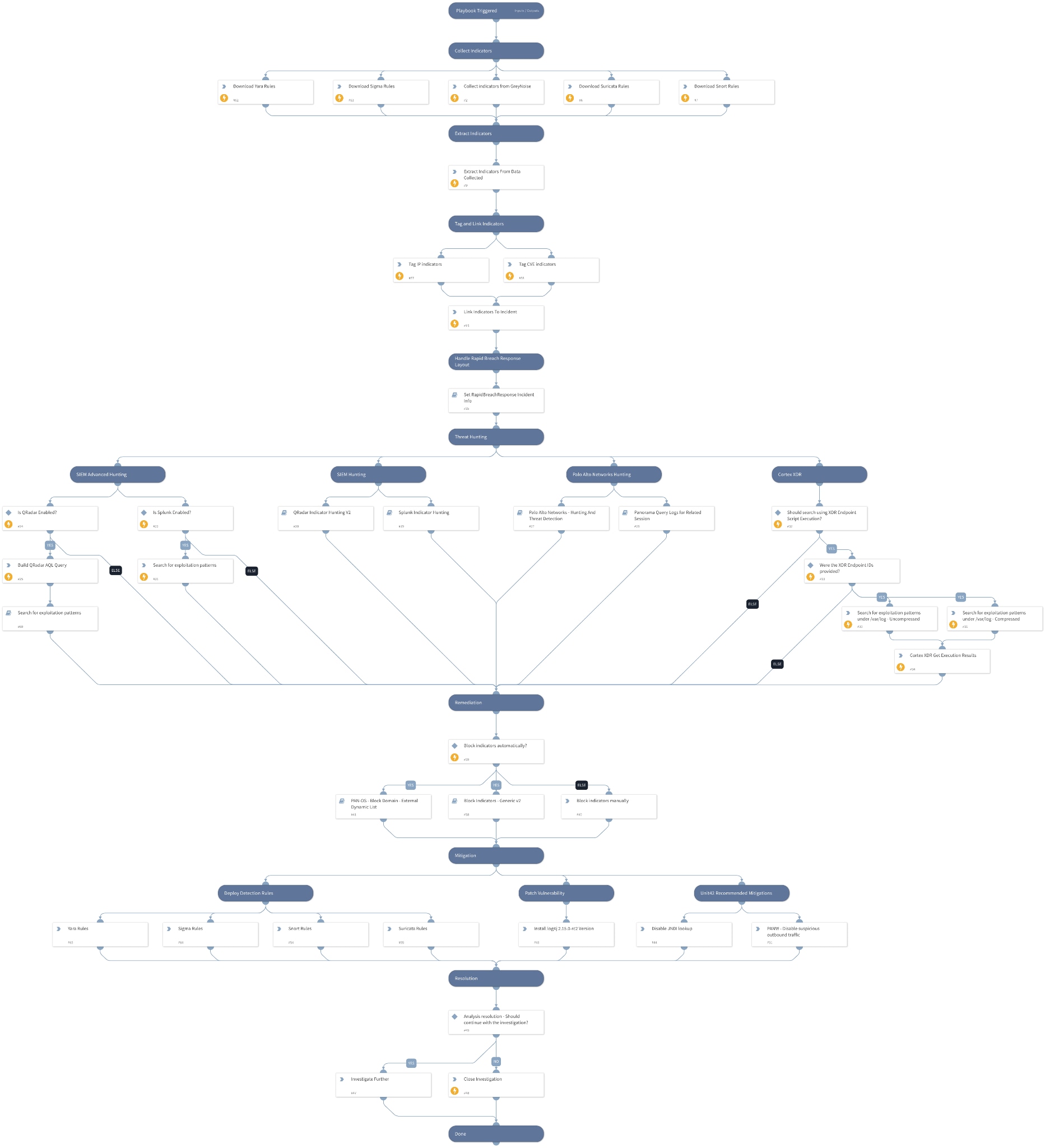
Apache Log4j RCE CVE-2021-44228 Content Pack
More details on this vulnerability can be found in our Unit 42 blog.
You can view and download the playbook content pack in our Cortex XSOAR Marketplace. If you do not have Cortex XSOAR, you can get our free Community Edition.