On Feb. 2, 2022, three vulnerabilities rated as “critical” with a CVSS v3 score of 10 (CVE-2022-20699, CVE-2022-20700, CVE-2022-20708) impacting Cisco Small Business RV Series Routers were announced in a Cisco Security Advisory. These vulnerabilities would allow an unauthenticated attacker to inject and execute arbitrary code on the underlying operating system and elevate privileges (to root) on these routers.
One of the vulnerabilities (CVE-2022-20699) exists in the SSL VPN gateway of Cisco Small Business RV340, RV345, RV160, and RV260 Series Routers, which is often used when allowing remote employees access to internal resources. With a shift and increase in remote work, such exploits are frequently targeted by malicious actors. The CVE was ranked as “critical” by both the National Vulnerability Database (NVD) and CVE Numbering Authority (CNA).
While such vulnerabilities may seem to only impact small businesses, smaller companies are often connected to larger partners via VPN tunnels, thus should the communication link be insecure, so will the larger enterprise’s network.
How Do These Vulnerabilities Work?
The SSL VPN module vulnerability (CVE-2022-20699) is due to insufficient boundary checks when handling certain HTTP requests. By sending malicious HTTP requests to the affected SSL VPN Gateway device, a threat actor could execute code with root privileges.
Another web-based management interface vulnerability (CVE-2022-20700) can be exploited should an attacker utilize the insufficient authorization enforcement mechanisms. This could be done by submitting specific commands to an affected device allowing the malicious actor to elevate privileges to root and execute arbitrary commands on the contaminated system.
The web-based management interface vulnerability (CVE-2022-20708) is due to insufficient validation of user-supplied input, could allow an attacker to execute arbitrary commands on the underlying Linux operating system by sending certain input to an affected device.
These three vulnerabilities affect Cisco Small Business RV340 and RV345 (release 1.0.03.24 and earlier); as well as RV160 and RV260 (release 1.0.01.05 and earlier) Series Routers.
An additional critical vulnerability, CVE-2018-0125, exists in the web interface of Cisco Small Business RV132W and RV134W Series Routers. This vulnerability could allow an unauthenticated remote attacker to execute arbitrary code and gain full control of an affected system. Additional information can be found at Cisco’s Security Advisory.
Cortex Xpanse Discovers Vulnerable Versions
Recent scans with the Palo Alto Networks Cortex Xpanse platform reveal approximately 70,447 internet-exposed Cisco Small Business Routers. Based on the publicly available device version and model information, as of July 18, 2022, 251 of these routers are models affected by CVE-2022-20699, CVE-2022-20700 or CVE-2022-20708. 552 models were identified as being potentially impacted by CVE-2018-0125.
Software updates to address CVE-2022-20699, CVE-2022-20700 and CVE-2022-20708 have been available since February 2022. Of the 251 vulnerable models, 102 are using outdated software vulnerable to these issues. This estimate only contains routers certain to be vulnerable. There remain numerous Cisco Small Business routers with varying configurations that do not publicly broadcast model and version information, thus they cannot be confidently included in this data as a vulnerable system. Additionally, Cisco Small Business routers within internal networks are not included in our data.
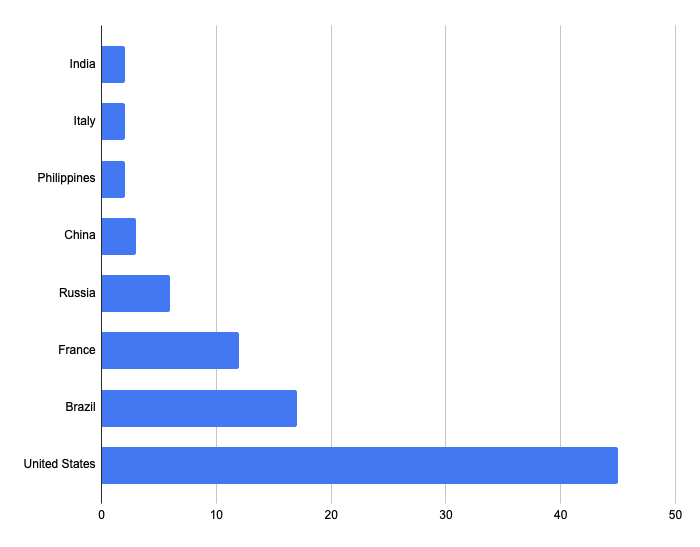
The majority of vulnerable Cisco Small Business Routers are found in the United States, followed by Brazil and France.
Is Your Organization Also Running End-of-life Software?
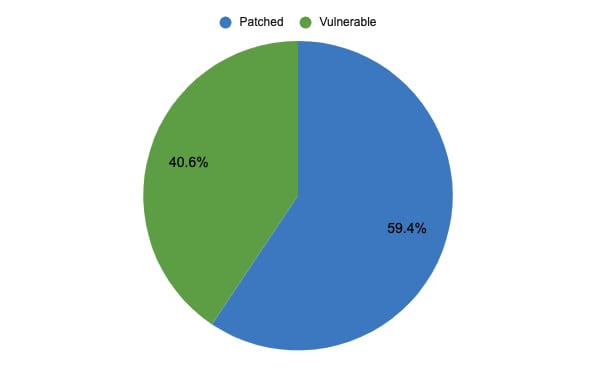
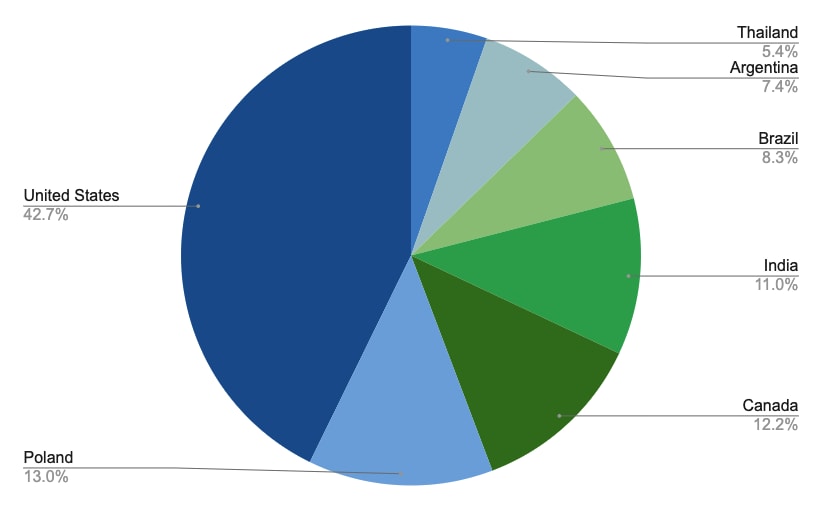
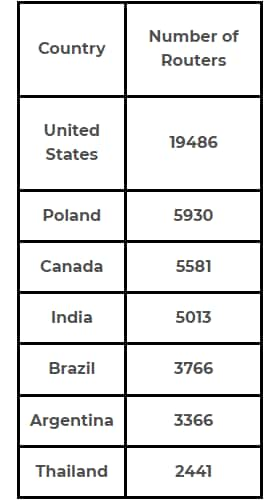
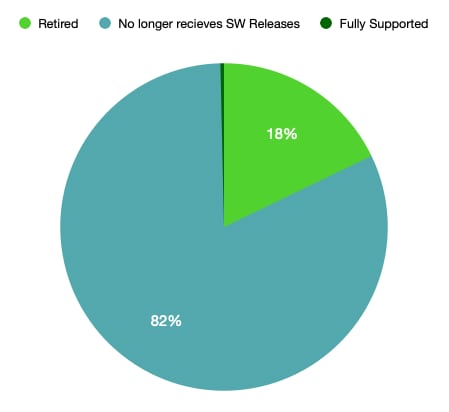
Per Cisco’s Small Business RV Series Routers End-of-Life and End-of-Sales Notices board, all RV Series Routers are end of life and will eventually no longer receive support. While some models will continue to be provided with security updates until Oct. 28, 2022 and will be provided with service until Oct. 31, 2026 at the latest, numerous other models are no longer being serviced and have been found in recent scans with the Palo Alto Networks Cortex Xpanse platform. Only Cisco Small Business RV340, RV345, RV160, and RV260 Series Routers continue to receive software releases and vulnerability/security support. Of the Cisco Small Business RV Series Routers identified, 12,573 routers were found to have reached end of life and are no longer supported by Cisco, while 57,621 routers were found to be no longer receiving software maintenance releases. Thus, 99.6% of the Cisco Small Business RV Series Routers discovered no longer receive software maintenance or updates. 42.7% of such end-of-life routers were found in the United States, followed by 13% in Poland and 12.2% in Canada.
Models that no longer receive new software releases are accumulating numerous vulnerabilities that will not be patched. Currently, there are 74 CVEs, the majority of which are rated as “High” with a CVSS v3 score of 7.2, affecting outdated Cisco Small Business RV130W, RV110W, RV130, RV215W Series Routers. Recently, a new critical vulnerability was identified, CVE-2022-20825, that affects similar models. Recent scans with the Palo Alto Networks Cortex Xpanse platform reveal 86 affected models on the public facing internet, all of which will remain vulnerable unless replaced with an updated model.
Similarly, Cisco released a Security Advisory on Feb. 3, 2021 detailing numerous vulnerabilities rated as “High” affecting Cisco Small Business RV042, RV042G, RV016, RV082 (releases 4.2.3.14 and earlier); as well as RV320 and RV325 (releases 1.5.1.11 and earlier) Series Routers. In recent scans with the Palo Alto Networks Cortex Xpanse platform, of the 70,447 Cisco Small Business RV Series Routers identified, 55,540 were found to be RV042, RV042G, RV016, or RV082 Series Routers. All of these no longer receive software maintenance releases or security updates as of the end of January 2021. Thus, 79% of all identified routers remain susceptible to this vulnerability, and will continue to be so.
What Can You Do?
Due to the critical nature of these vulnerabilities, we strongly suggest organizations review their internet-facing assets and ensure your systems are up-to-date, as it is vital to remaining secure against threat actors. As Cisco Small Business RV Series Routers are all on the path to end of life, it is suggested to migrate services to the latest Cisco ISR or Meraki MX67/MX67W/GX20/GX20+AP. As a best practice, follow vendor guidance and switch to newer models with support for security updates.
The Binding Operational Directive 22-01 (BOD 22-01), issued by the U.S. Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA), establishes a list of Known Exploited Vulnerabilities (KEVs). Multiple Cisco Small Business RV Series Router vulnerabilities are included in this list. Using the “Software Potentially Impacted by CISA Known Exploited Vulnerabilities (BOD 22-01)” issue category in Cortex Xpanse, users can easily find and view the above mentioned Cisco Small Business RV Series Router vulnerabilities, as well as numerous other potentially vulnerable services on their network. More information can be found in the associated blog post, How Cortex Xpanse Can Identify CISA-Identified Known Exploited Vulnerabilities.
Cortex Xpanse provides a continuously updated view of your attack surface, identifying vulnerable systems and thus allowing organizations to quickly detect and respond to newly evolving CVEs as well as newly outdated versions and models.
If you want to learn whether your organization is using vulnerable systems or versions of a software, please contact us.