With ransomware attacks more prevalent than ever across various industries, the need for fast and efficient response is crucial to incident responders. To help combat this growing threat, Cortex XSOAR has just the content pack to help security teams be more effective in dealing with these nefarious bad actors.
According to the Palo Alto Networks Unit 42 Ransomware Threat Report, the average ransom demand in cases handled by Unit 42 increased 144% year-over-year from 2020 to 2021, making ransomware attacks one of the fastest-growing cyber threats in recent history. Ransomware was also the third most used cyberattack method in 2021, accounting for 10% of all data breaches. This explosive uptick in attacks is expected to continue in 2022 and beyond.
In order to better deal with these attacks, the Cortex XSOAR’s ransomware content pack can help accelerate incident response and orchestrate threat intelligence by enabling SecOps teams to standardize and speed up the post-intrusion response processes. This content pack automates the majority of the ransomware response steps, allowing the incident response and SecOps teams to review and add guidance and input wherever necessary.
With this pack, incident responders can better understand their position and exposure against threat actors by collecting the required information from their environment, executing the investigation steps, containing the incident, and visualizing the data with its custom post-intrusion ransomware layout.
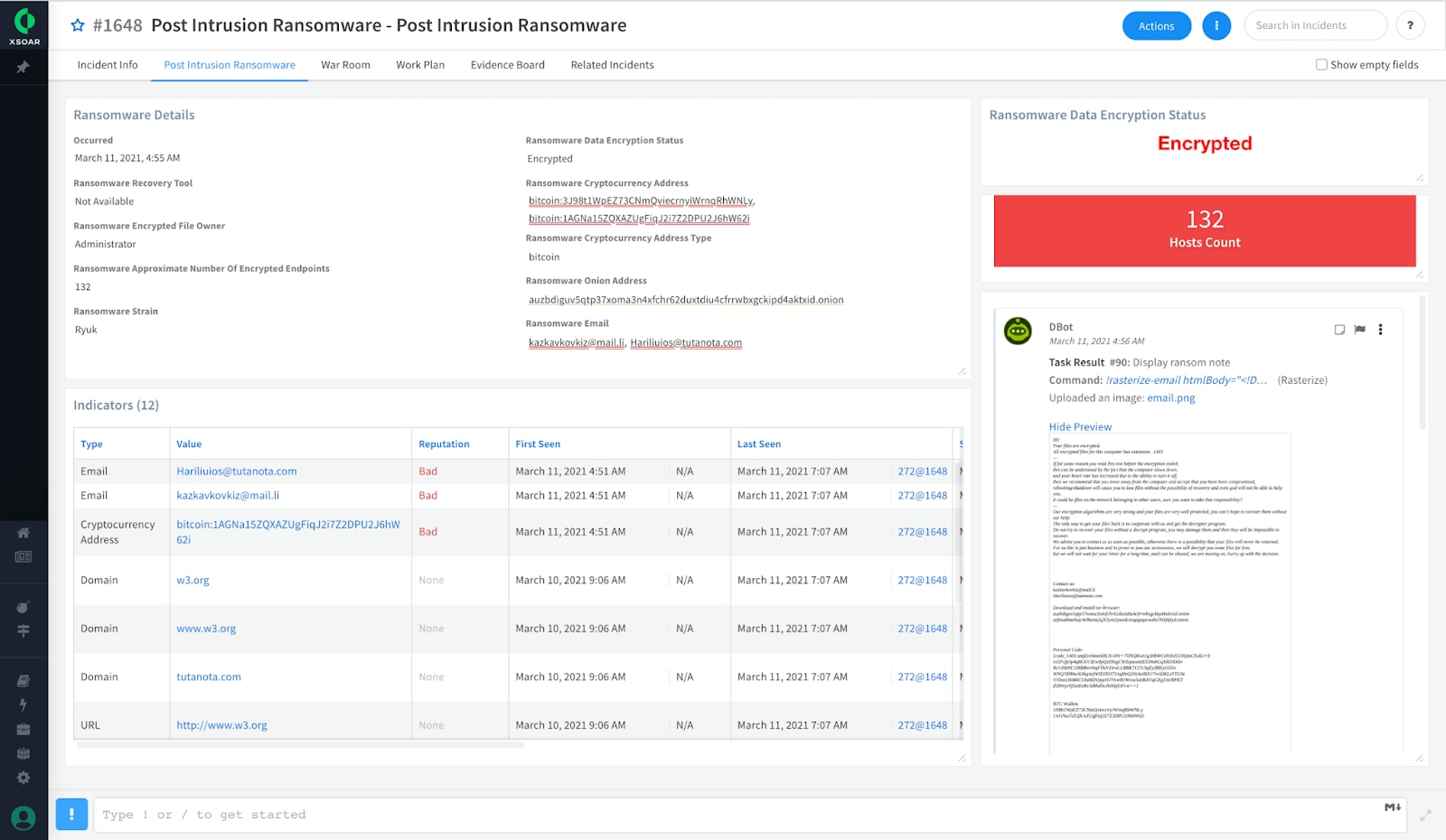
How the Ransomware Content Pack Works
When a ransomware attack is detected by one of several alert sources such as Cortex XDR, this pack automatically triggers the post-intrusion ransomware investigation and response playbook to identify, investigate, and contain the ransomware attack. This semi-automated playbook helps you better understand the status of the attack by collecting the information needed from your environment, performing the required investigation steps, containing the incident, and displaying the data with the Post Intrusion Ransomware incident layout.
The ransomware content pack requires the ransom note and an example of an encrypted file to identify the ransomware variant and find the most appropriate recovery tool via the online database. Plus, all the relevant stakeholders are automatically notified of the attack.
The playbook includes a manual task for determining the incident timeline that is an essential part of the recovery process. Since the data encryption is the final step in the attack, prior attacker actions are investigated.
The playbook includes options to further investigate the activity of the user whose files were encrypted and identify additional endpoints that experienced the attack. If auto-remediation is approved, the malicious indicators from the ransom note are automatically blocked. Alternatively, the containment of affected files can be done manually as well.
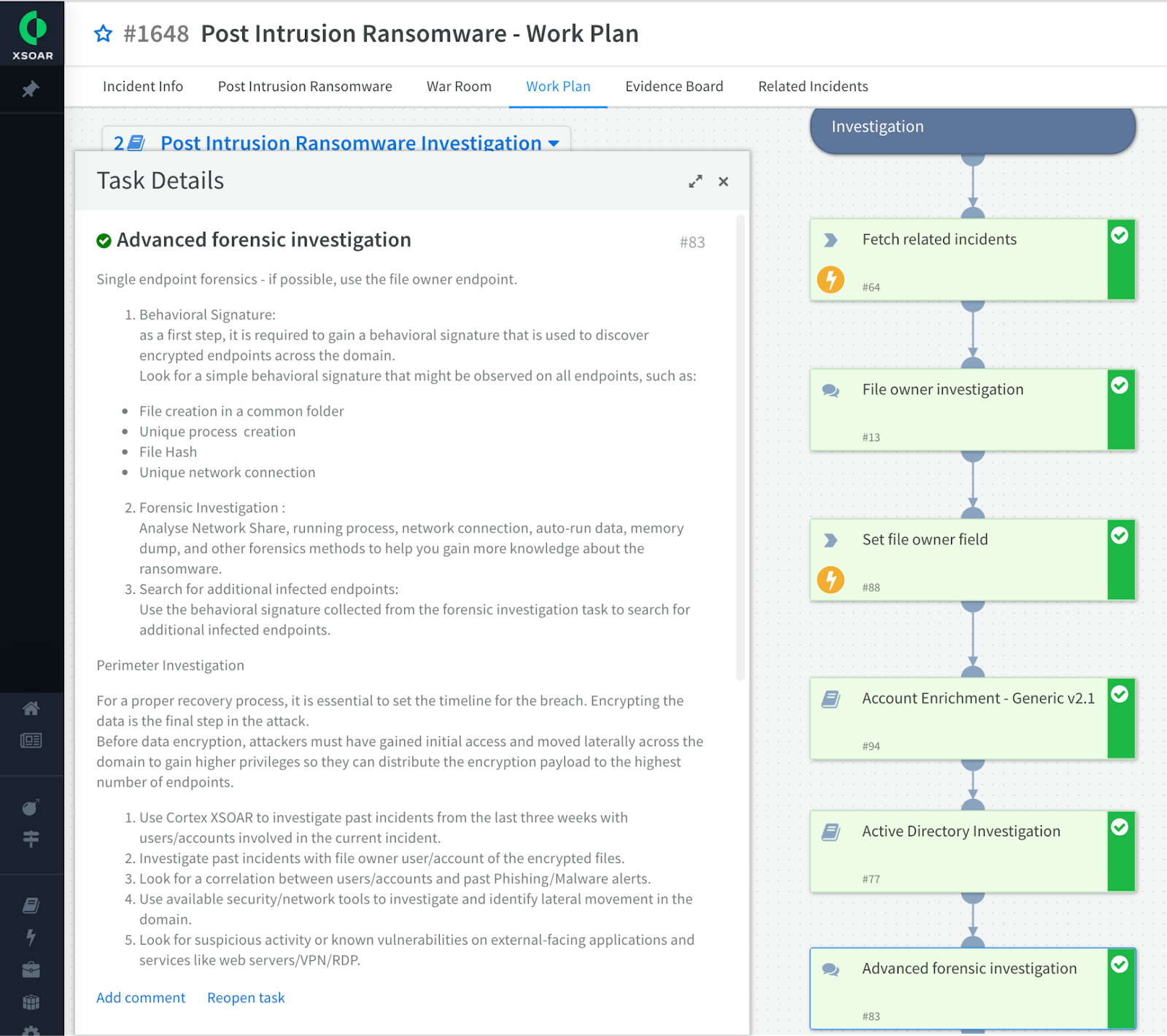
Expanded view of the advanced forensics investigation task of the Ransomware playbook
Ransomware Content Pack Main Features:
- Performs automated user and host data enrichment
- Performs automated endpoint isolation and user revocation
- Provides guidance to retrieve the necessary files to identify the ransomware strain
- Extracts indicators from the ransomware note, including cryptocurrency and onion addresses
- Provides guidance on additional recommended investigation steps such as endpoint forensics, searching for more infected endpoints, and investigating activities of the infected user
- Performs Active Directory forensics
- Automatically blocks malicious indicators
To learn more about the associated integrations, playbooks, scripts, commands, and automations, please refer to the Palo Alto Networks Developer Doc.
Conclusion
With the help of the ransomware content pack and the core capabilities and integrations available within Cortex XSOAR, SecOps, incident response, and threat intel teams can work more efficiently and effectively to respond to the growing ransomware threat. Teams can save countless hours of manual labor trying to piece disparate sources of information together from multiple tools.
Cortex XSOAR automates the process of user investigation, endpoint isolation, notifications, enrichment, and threat hunting by orchestrating across SIEM, firewalls, endpoint security, and threat intelligence sources so that response teams can quickly shut down the ransomware. By doing so, we minimize the risk and potential of losing important data, and limit the financial impact of ransom demands and its impact on the entire enterprise.
To learn more about how you can automate security operations with Cortex XSOAR, check out our virtual self-guided XSOAR Product Tour
We also host virtual and in-person events, so check here for upcoming ones.
Please Suggest Other Ideas or Vote!
If you like these ideas or would like to suggest other ideas, please collaborate with us through the Cortex XSOAR Aha page: https://xsoar.ideas.aha.io/ideas