Start Your Automation Journey with the XSOAR Common Playbook Pack
As you embark on automating your security operations, determining which use cases to prioritize for automation can be a challenge. It requires careful consideration of your organization's unique threat landscape, the criticality of specific types of incidents, and the feasibility of automating processes without compromising the need for human judgment.
The Cortex XSOAR Common Playbooks pack provides the foundation for automation by encapsulating best practices and industry knowledge. Leveraging the Common Playbooks pack will not only accelerate your automation process but will allow you to reap the collective wisdom of the cybersecurity community. These playbook templates will streamline your decision-making process regarding which use cases to automate first and can be easily customized playbooks to align with your specific security requirements, ultimately strengthening your overall incident response capabilities.
The Common Playbooks pack, which contains 87 playbooks, is a collection of pre-built playbooks that serve as a foundation for orchestrating common security use cases. Crafted and maintained by Palo Alto Networks' security experts, these playbooks are designed to accelerate incident response and reduce manual efforts for repetitive incident response tasks. Key playbook automations include data enrichment, threat intelligence, forensics, malware analysis, case management, network, and endpoint protection.
In this blog, we will delve into the most frequently used playbooks in the pack, exploring their significance in fortifying cyber defenses and optimizing incident response.
Deploying the Common Playbook Pack
Initiating your journey with the Common Playbooks content pack in Cortex XSOAR is a straightforward process. The Common Playbooks pack is bundled with the XSOAR server, so you only need to review the content and choose which playbooks you wish to use. Once you have selected the playbooks you wish to utilize, some inputs will need customization to suit your environment. The playbook inputs are versatile, covering a wide range of variables including decision points, automation thresholds, and user preferences.
Here are two examples from the Block Indicators - Generic v3 playbook, which we will discuss in detail later. An additional layer of security is provided by the 'UserVerification' input, which permits organizations to determine whether user verification is required before blocking IPs. This input prevents unauthorized or unintended actions from occurring. Furthermore, the 'RuleDirection' input is significant, determining whether a newly created rule should be in the network direction of outbound or inbound blocked traffic.
Organizations can modify these inputs to align with evolving security policies, threat landscapes, or unique network configurations. This level of customization ensures that security teams can optimize their workflows, strike a balance between automation and manual intervention, and maintain a responsive and effective cybersecurity posture. Don't be intimidated by the review and customization processes, as they only need to be performed once.
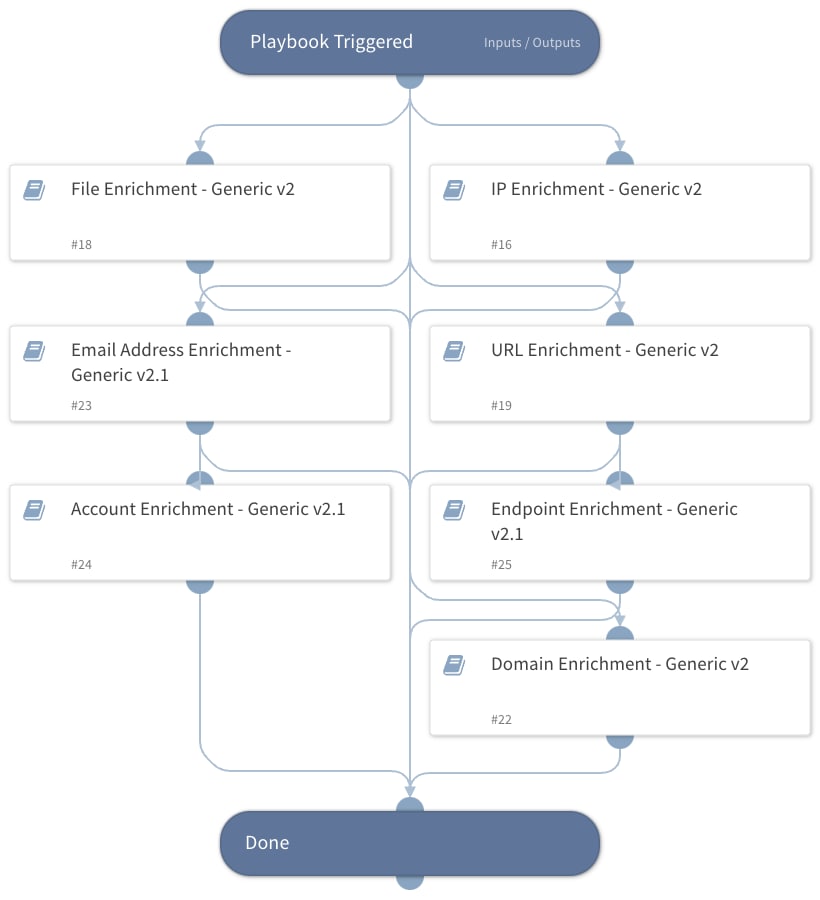
Entity Enrichment - Generic v2.1
This playbook is designed to enhance cybersecurity analysis by systematically enriching entities such as IP addresses, domain names, URLs, email addresses, user accounts, file hashes, and endpoints. As part of the playbook flow, not only are entities ingested but also organizational data, such as internal IP addresses and internal domains, which are vital to the enrichment of domain names, IP addresses, URLs, and emails.
The playbook consists of seven sub-playbooks, each enriching a particular type of entity. To automatically gather contextual information and subsequently present a comprehensive analysis, each sub-playbook leverages integrations such as Active Directory, identity and access management, antivirus, XDRs, and threat intelligence platforms. This comprehensive enrichment not only enhances cyber defenses by providing a more detailed understanding of potential threats but also optimizes incident response by significantly reducing the time and manual effort required for investigative tasks. As the playbook integrates with other security tools, a cohesive and efficient incident response workflow is created for dealing with various types of security incidents.
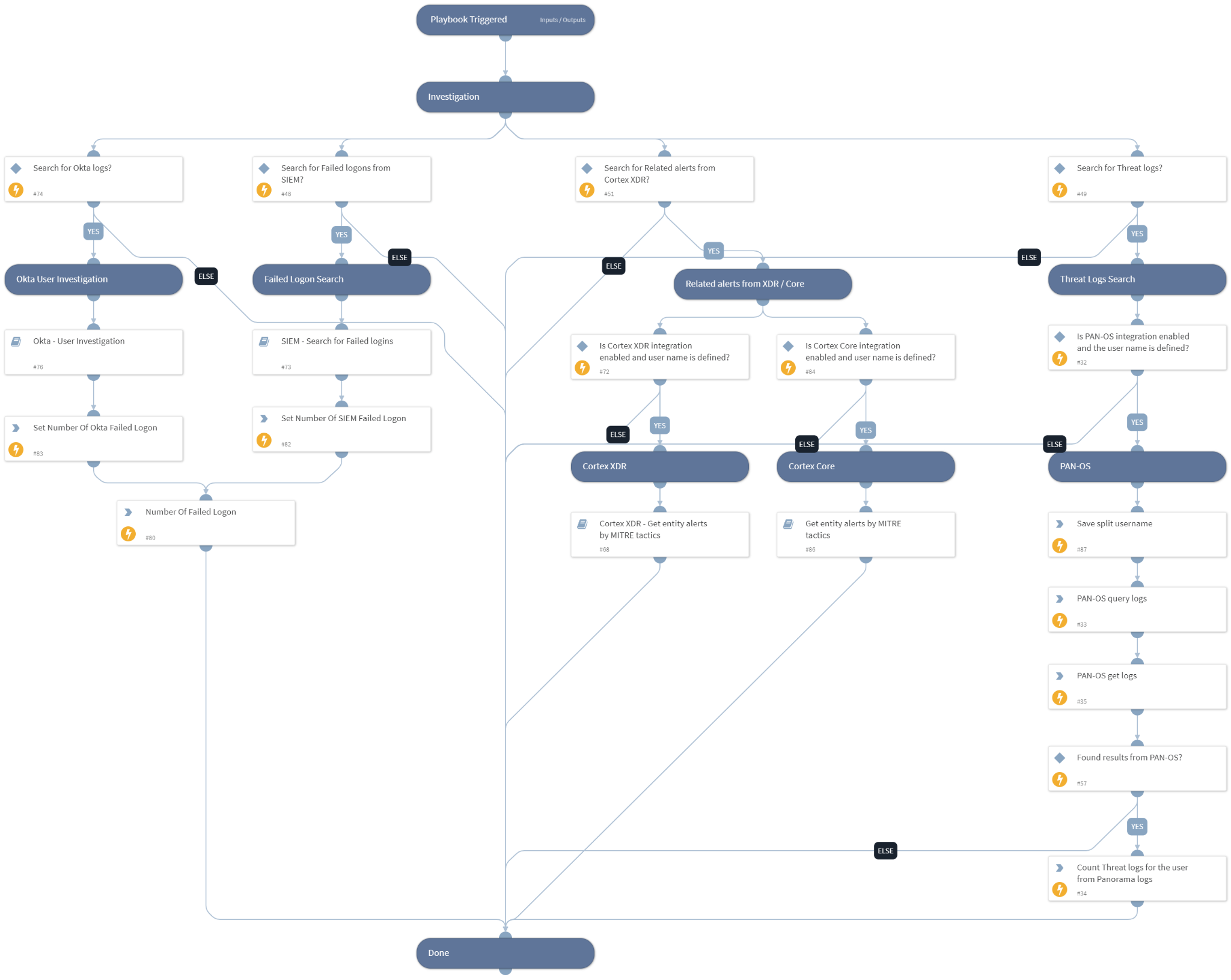
User Investigation - Generic
The playbook serves as a valuable asset in automating user-related investigations, strengthening cyber defenses, and optimizing incident response. In this playbook, an investigation is conducted on a specific user utilizing queries and logs gathered from SIEMs, identity management systems, endpoint protection platforms (EPPs), and firewalls with the objective of rapidly collecting and analyzing information regarding user activities and potential security risks.
By automating these investigative tasks, security teams can efficiently assess user behavior, identify anomalies, and detect potential threats. This proactive approach not only enhances cybersecurity by providing real-time insights into user-related risks but also optimizes incident response by streamlining security incident identification and containment. The User Investigation - Generic playbook empowers security professionals with a comprehensive toolset to navigate and respond to user-centric security challenges, contributing to a more resilient and proactive cybersecurity posture.
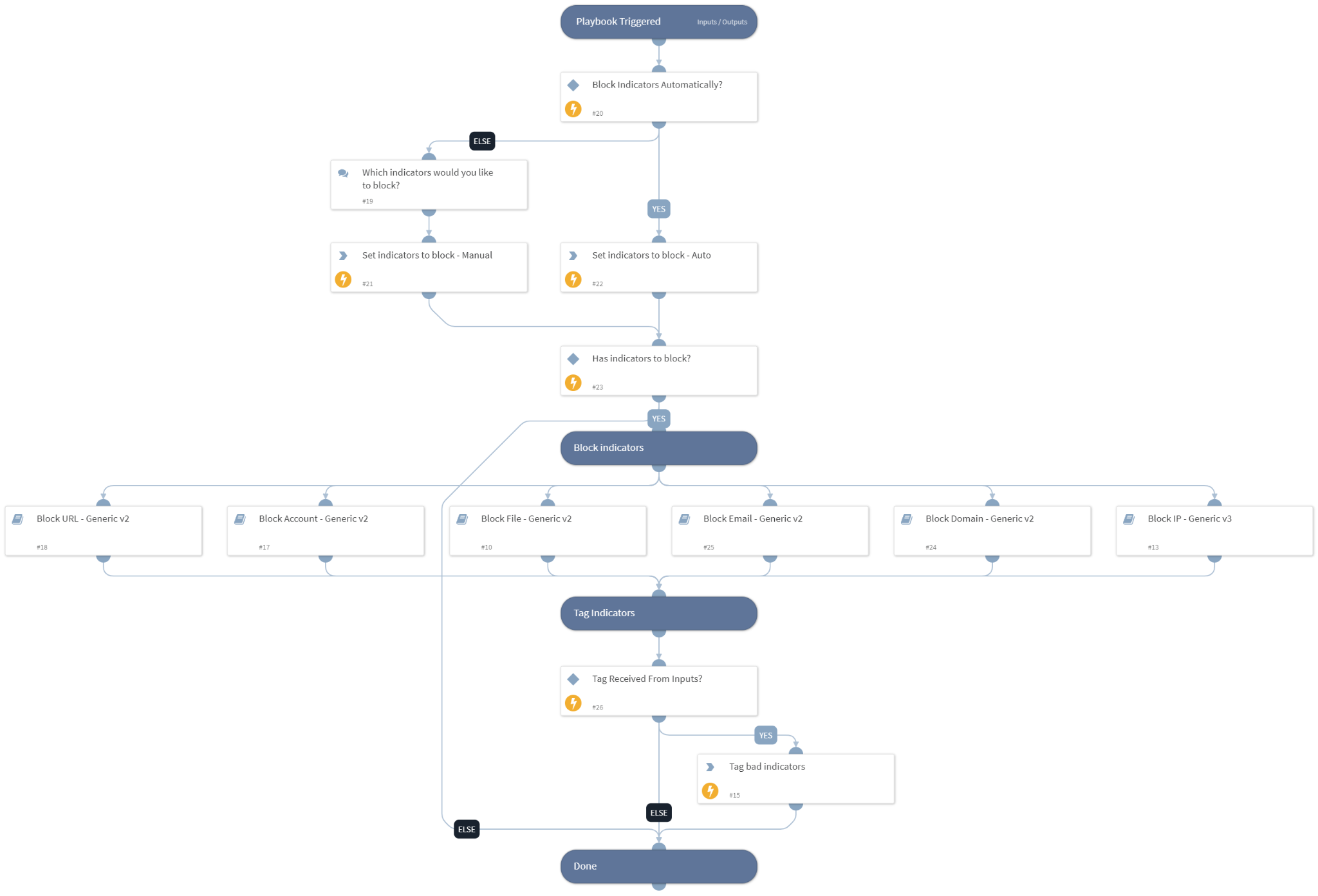
Block Indicators - Generic v3
The playbook is designed to automatically respond to identified threats by orchestrating the blocking of malicious indicators, including IP addresses, domains, file hashes, URLs, email addresses, and user accounts - across a variety of integrations such as firewalls, WAFs, identity management systems, email relays, and SASEs.
The playbook initiates its structured flow with a pivotal first step: Checking the configurations of the 'AutoBlockIndicators' playbook input which determines whether the indicators will be automatically blocked. This crucial decision point determines whether the playbook will autonomously block indicators or whether the user will be given the option to choose which indicators to block.
This playbook is primarily used as a sub-playbook after previous playbooks have completed the processes of identifying, enriching, and analyzing suspicious indicators. By automating this process, the playbook not only fortifies cyber defenses by preventing the spread of threats but also optimizes incident response by minimizing the time it takes to neutralize potential risks. The streamlined automation significantly accelerates the process of blocking malicious indicators, enabling organizations to respond promptly to emerging threats and enhance overall cybersecurity resilience. Additionally, the ‘AutoBlockIndicators’ playbook input configuration outlined above illustrates the flexibility and efficiency embedded in the playbook, offering organizations a tailored and responsive approach to mitigating cyberthreats.
The playbooks described in this blog represent just a fraction of what is included in the Common Playbooks content pack. Each playbook contributes to the optimization of your team’s efficiency, empowering your team to scale and respond faster to critical incidents. The strength of your automation orchestration and response lies not just in the tools you use but in the strategy and expertise behind their deployment. The Common Playbooks pack is designed to integrate seamlessly into your operations, providing a streamlined, adaptable approach to security challenges.
So, take the first step today by checking out the pack and all its playbooks in the Cortex Marketplace. Explore the different pack capabilities, experiment with the automations embedded in the playbooks, and experience it transforming your SOC into a more dynamic, responsive, and effective unit.
To learn more about how you can automate security operations with Cortex XSOAR, check out our virtual self-guided XSOAR Product Tour
We also host virtual and in-person events, so check here for upcoming ones.