Your security stack is working…to an extent. SOC teams today aren't struggling because they're missing threats, they're drowning because every tool is screaming for attention, burying critical alerts under mountains of low-priority noise. This massive volume of notifications, many of which are low-priority or false positives, leads to severe alert fatigue. Teams want to minimize the noise and focus their limited resources on what is necessary, especially when every SOC has unique risk tolerance, environment specifics, and organizational policies.
Customizing analytics rules addresses the alert overload by enabling users to easily adjust the severity of their detections. The SOC team can dim less relevant alerts, so the focus remains on high-value tasks. This on-demand control ensures the analytical output aligns with the enterprise’s prioritization and response.
Key Benefits of Customization
The core benefit of the flexible customization for Analytics Rules feature is the ability to align the security platform's output with your organization's unique risk profile and operational needs.
1. Achieving Optimal Triage and Risk Alignment
Every asset and user carries a different level of business risk. While a default medium severity may be suitable in some cases, a threat against a sensitive database or C-level executive requires immediate critical escalation. Cortex® XDR grants granular control over alert severity (critical, high, medium, low, informational) for individual rules, allowing SOC teams to directly control their alert queue and ensure prioritized triage. By reflecting the organization's unique risk tolerance, analysts can immediately focus on the most impactful incidents, minimizing response time and potential damage.
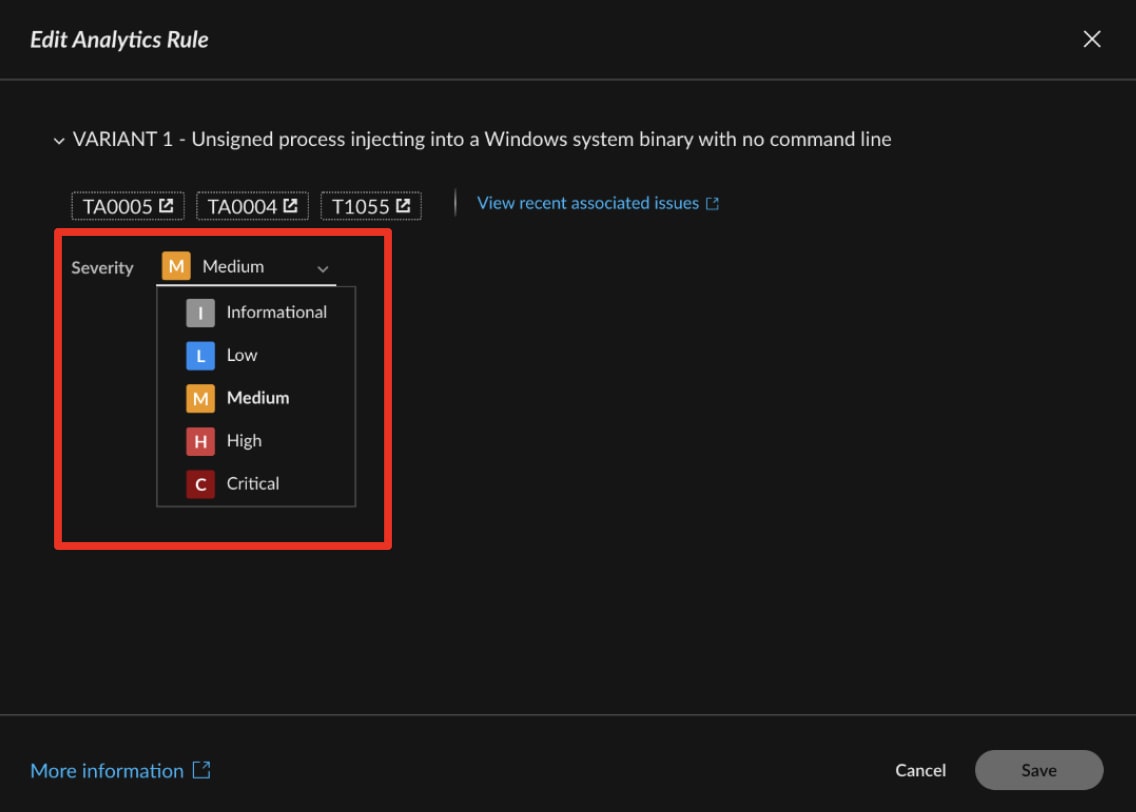
2. Guardrails and Warnings: Preventing Unintended Consequences
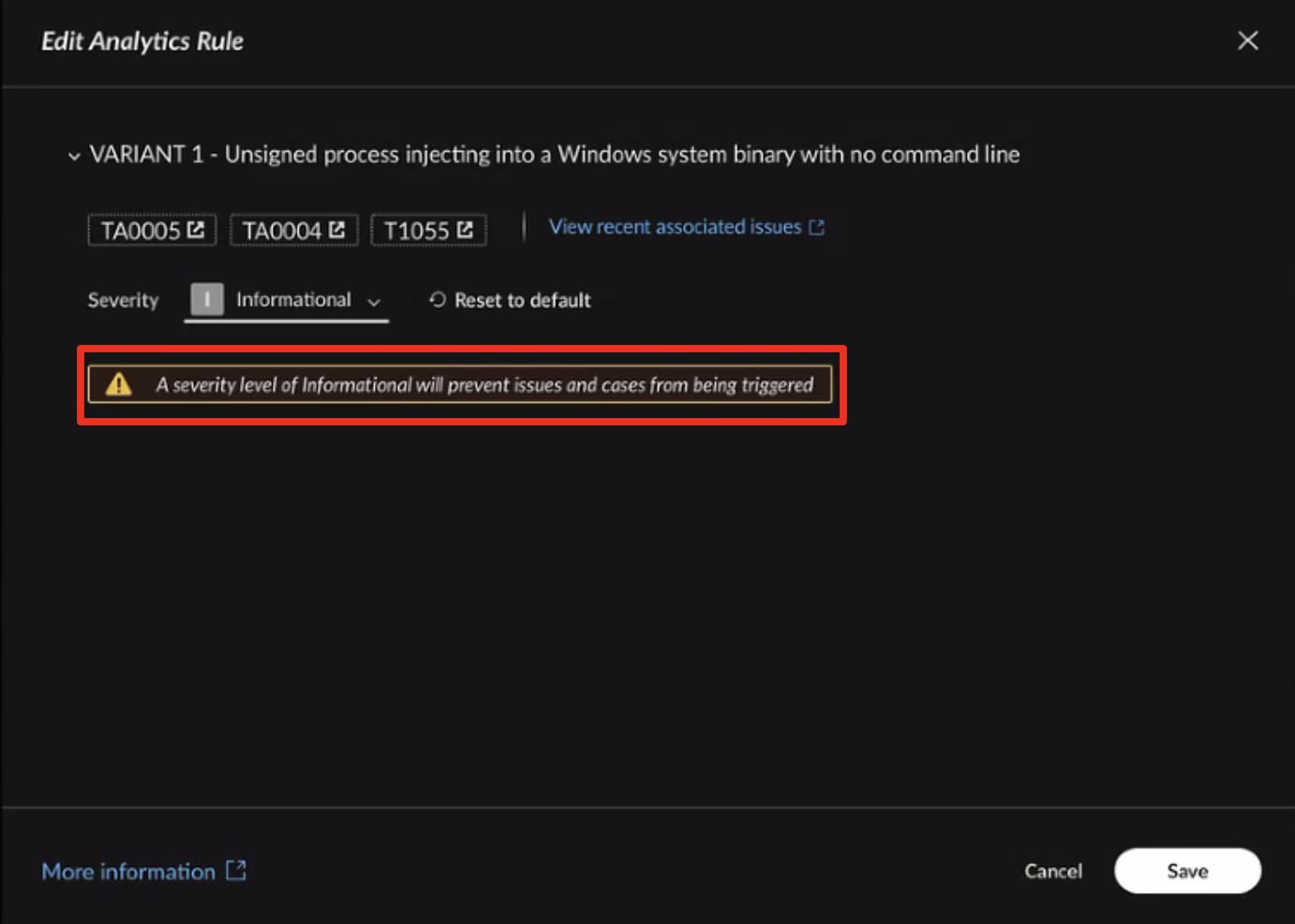
If an analyst accidentally tunes a behavioral rule to generate alerts at a high severity for common, low-risk activity, it can instantly create an unmanageable alert flood and cause operational blindness. While Cortex XDR is designed for immediate value by providing default alert severity based on Palo Alto Networks' expert threat intelligence and domain knowledge, customizing analytics severity is therefore an additional control to align the system with organization-specific risk tolerance. To prevent these kinds of operational errors when tuning these rules, Cortex XDR incorporates guardrails and warnings. These mechanisms are designed to build confidence and ensure the stability of the SOC workflow.
- Impact Warning: When setting a rule's severity to a low level (informational or low) or a high level (high or critical), users will receive a prompt warning. This ensures a clear understanding of the potential consequences, such as losing sight of genuine threats (if too low) or increasing the rate of false positives (if too high).
- Reversion Option: Teams can easily revert any custom change back to the default severity value at any time.
3. Maintaining Governance and Safe Deployment
When unauthorized users or those without the necessary expertise attempt to modify global security rules, they risk creating a significant security gap or causing a widespread operational outage. To prevent such unintended errors and ensure customization is performed securely and transparently, the feature integrates strong governance and safety controls. Changes are subject to role-based access control (RBAC) to limit modifications to authorized users, and the feature is fully supported in multi-tenant managed environments (MSSP use cases). For audit and oversight, dedicated fields track who made the change, when, and which rules were modified, ensuring full accountability.
Example Scenario for Customization
The flexibility to adjust severity is crucial for matching the detection platform to the customer's unique risk environment.
Example: Reducing Severity for Noise Suppression
Consider a "Rare Remote Service Command Execution" rule. In most environments, this is correctly flagged as high severity, indicating a potential lateral movement or post-exploitation activity.
Customization Need: In a specific environment that runs frequent, automated, and benign remote scripts for IT configuration management (such as nightly patch installations managed by a unique automation service account), this rule may generate consistent, expected alerts.
Action: The SOC team may change the severity for this specific rule to medium (or even low) when triggered by the known automation service account.
Result: This customization reduces alert noise in the high-priority queue, saving analyst time without sacrificing the underlying detection logic.
Conclusion
Ultimately, Cortex XDR provides a prevention-first approach to secure every endpoint, reduce risk, and unify the SOC. With flexible customization for Analytics Rules, security teams can tailor the system's output to their specific environment, ensuring that high-risk threats are immediately escalated and routine noise is suppressed. This fine-tuned approach transforms alert fatigue into prioritized, effective security operations, allowing analysts to focus on what matters most: stopping the attacker.
Ready to transform your endpoint security? Explore how Cortex XDR and Cortex Extended Data Lake™ (XDL) can help you leverage unified data to secure every endpoint and reduce risk.