- 1. How does a harvest now, decrypt later attack work?
- 2. Why does the threat matter today if quantum computers don't exist yet?
- 3. What types of organizations and data are most exposed?
- 4. How are attackers exploiting the window before post-quantum cryptography?
- 5. When will Q-Day actually happen?
- 6. How to prepare for the post-quantum threat today
- 7. HNDL FAQs
- How does a harvest now, decrypt later attack work?
- Why does the threat matter today if quantum computers don't exist yet?
- What types of organizations and data are most exposed?
- How are attackers exploiting the window before post-quantum cryptography?
- When will Q-Day actually happen?
- How to prepare for the post-quantum threat today
- HNDL FAQs
Harvest Now, Decrypt Later (HNDL): The Quantum-Era Threat
- How does a harvest now, decrypt later attack work?
- Why does the threat matter today if quantum computers don't exist yet?
- What types of organizations and data are most exposed?
- How are attackers exploiting the window before post-quantum cryptography?
- When will Q-Day actually happen?
- How to prepare for the post-quantum threat today
- HNDL FAQs
Harvest now, decrypt later is a cybersecurity threat in which encrypted data is collected and stored today so it can be decrypted in the future when quantum computers can break current encryption.
It's a present-day risk because data protected by classical encryption can be captured now and later exposed once quantum decryption becomes feasible.
How does a harvest now, decrypt later attack work?
A harvest now, decrypt later (HNDL) attack happens in stages. It starts with data collection and ends years later with decryption.
The entire process is built on patience: steal what's valuable now, wait until technology can unlock it.
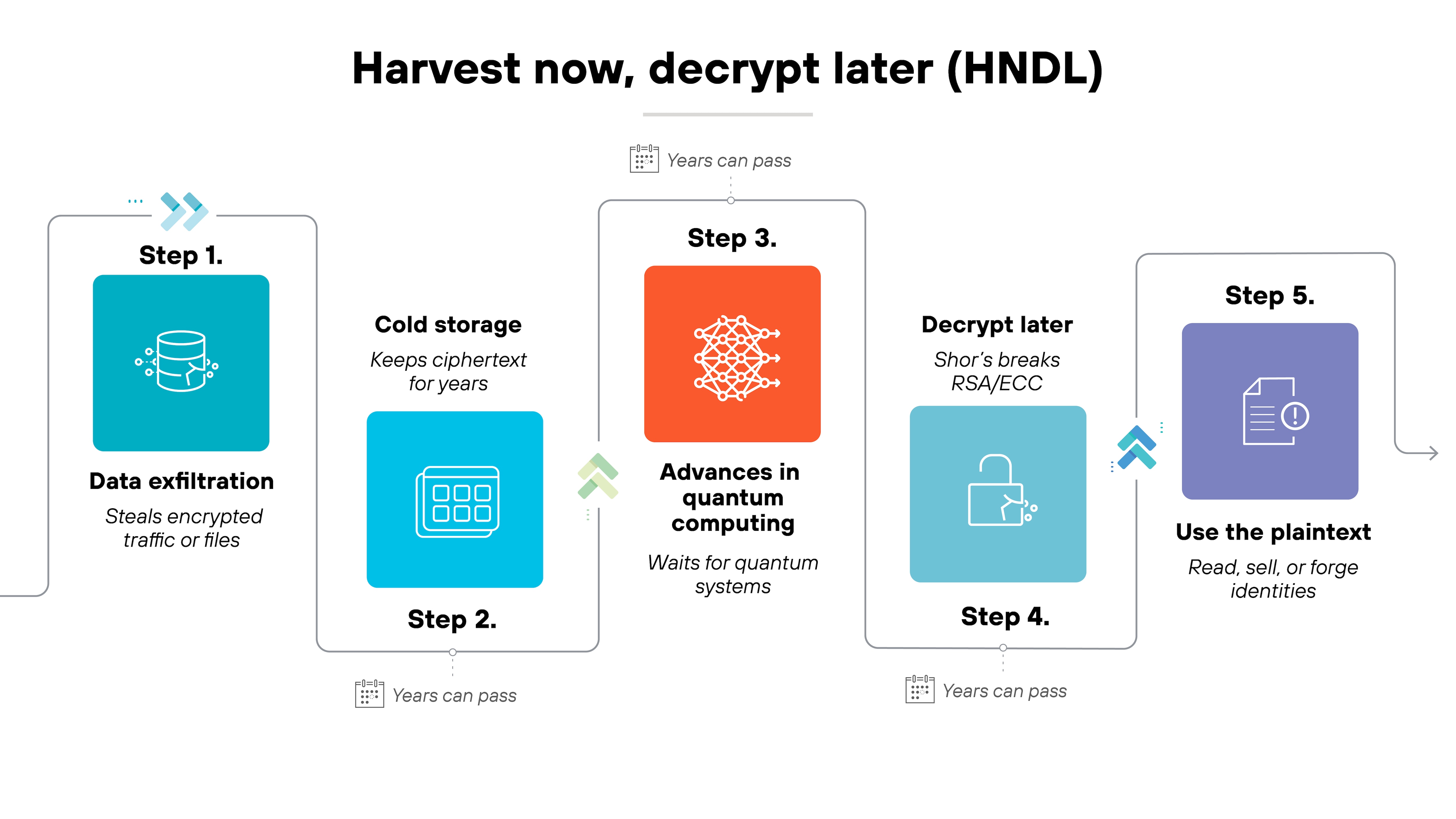
Understanding these phases helps show why this is not a future concern but a risk already in motion.
Phase 1 — Harvest
Attackers begin by collecting encrypted information through familiar means. That includes intercepting network traffic, exploiting endpoints, or stealing data from compromised servers.
Because the information is encrypted, the operation doesn't need to break it immediately. The goal is to quietly gather as much as possible while classical encryption still protects it.
Every intercepted file or transmission becomes a potential future target once quantum computing matures.
Phase 2 — Store
Next comes long-term storage.
The harvested data is archived—sometimes for years, sometimes for decades. It may sit in government repositories, data centers, or private cloud environments, waiting for quantum decryption to become practical.
Nothing active happens here, which makes this phase nearly impossible to detect. The simplicity is what makes it dangerous: once the data is collected, time does the rest.
Phase 3 — Decrypt
Finally, when quantum computers are capable of running algorithms like Shor's, that stored data can be decrypted. Information that was once secure becomes readable.
Financial records, state communications, intellectual property, and medical data are all at risk if still protected by classical public-key encryption.
The end result isn't a sudden breach. It's the delayed payoff of data stolen long ago. This is why long-lived records encrypted by classical algorithms remain a present-day exposure.
Why does the threat matter today if quantum computers don't exist yet?
The previous section explained how attackers carry out harvest now, decrypt later collection. But understanding why it matters today requires looking at how long data needs to stay protected.
The risk doesn't start when quantum computers arrive. It starts the moment encrypted data is collected.
That's because some information has to stay confidential for decades. Government records. Intellectual property. Personal identifiers. If that data is intercepted today, it can still be decrypted later once quantum computing matures.
The quantum threat is deferred. Not distant.
Organizations can't wait for quantum computers to exist before acting. For those that do, the damage will likely already be in motion. Which is why preparing early isn't optional. It's foundational to maintaining confidentiality over time.
Here's the core issue.
Encryption and secrecy don't last equally long.
Data has a required secrecy lifetime. Encryption has an effective lifetime. If the encryption expires first, the data becomes vulnerable. That mismatch is called data lifespan risk.
In other words, if you're still using classical cryptography to protect long-lived data, it's already exposed to harvest-now-decrypt-later collection.
The key takeaway: defending against this risk starts now. The focus isn't on stopping quantum computers. It's on reducing what adversaries can harvest before they arrive.
What types of organizations and data are most exposed?
Some types of organizations face higher exposure than others because their data must remain confidential far longer.
And some organizations can't afford for their data to ever be public.
| Sectors and data types with highest quantum exposure |
|---|
| Organizations | Data most at risk |
|---|---|
| Financial institutions | Transaction records, customer PII, long-term contracts |
| Government agencies | Diplomatic communications, census data, classified archives |
| Defense contractors | R&D, supply chain data, technical schematics |
| Healthcare providers | Medical records, genetic data, research datasets |
| Cloud providers | Encrypted traffic, client data stores, cross-border transfers |
Financial institutions. Government agencies. Defense contractors. Healthcare providers.
These sectors handle information that must stay confidential for decades. And cloud providers sit at the center of it all, storing and transmitting vast volumes of encrypted data on behalf of other industries.
In other words, the exposure for these sectors lasts as long as the data itself. If the encryption protecting it expires first, that information becomes vulnerable to harvest-now-decrypt-later collection.
While awareness of this risk is growing—especially in sectors with strict data retention laws—urgency isn't consistent. Many organizations recognize the problem but delay taking action because the quantum timeline feels uncertain.
Be aware: architecture matters as much as policy.
Multi-cloud adoption and global data sharing make the attack surface larger. Encrypted traffic now travels across multiple providers, networks, and jurisdictions. So every new transfer creates another point where it can be intercepted and stored.
Put simply, the more distributed data becomes, the harder it is to ensure that none of it's being quietly collected for later decryption.
How are attackers exploiting the window before post-quantum cryptography?
Attackers aren't waiting for quantum computers to arrive. They're preparing now.
State actors and advanced persistent threat (APT) groups are stealthily collecting encrypted data while it's still protected by classical algorithms. Once quantum decryption becomes practical, that data could be unlocked years after it was taken.
Why would they do that?
Because the payoff is long-term.
Intelligence services view encrypted information as a strategic asset.
Diplomatic archives. Research data. Proprietary designs. These can all hold lasting value.
Even if they can't be read today, they can reveal political intentions, defense strategies, or scientific breakthroughs later.
The cost is low, too.
Large-scale interception of encrypted network traffic is cheap and simple with today's infrastructure.
Internet backbones, satellite links, and cloud exchanges all move massive volumes of encrypted data every second. Capturing it is easier than ever. And that means adversaries can build vast archives now and wait for the tools to catch up.
Crucially: that window is what makes harvest-now-decrypt-later attractive.
It's a low-risk, high-reward investment. Once quantum computers reach the threshold for breaking modern cryptography, everything stored during this period could suddenly become readable.
When will Q-Day actually happen?
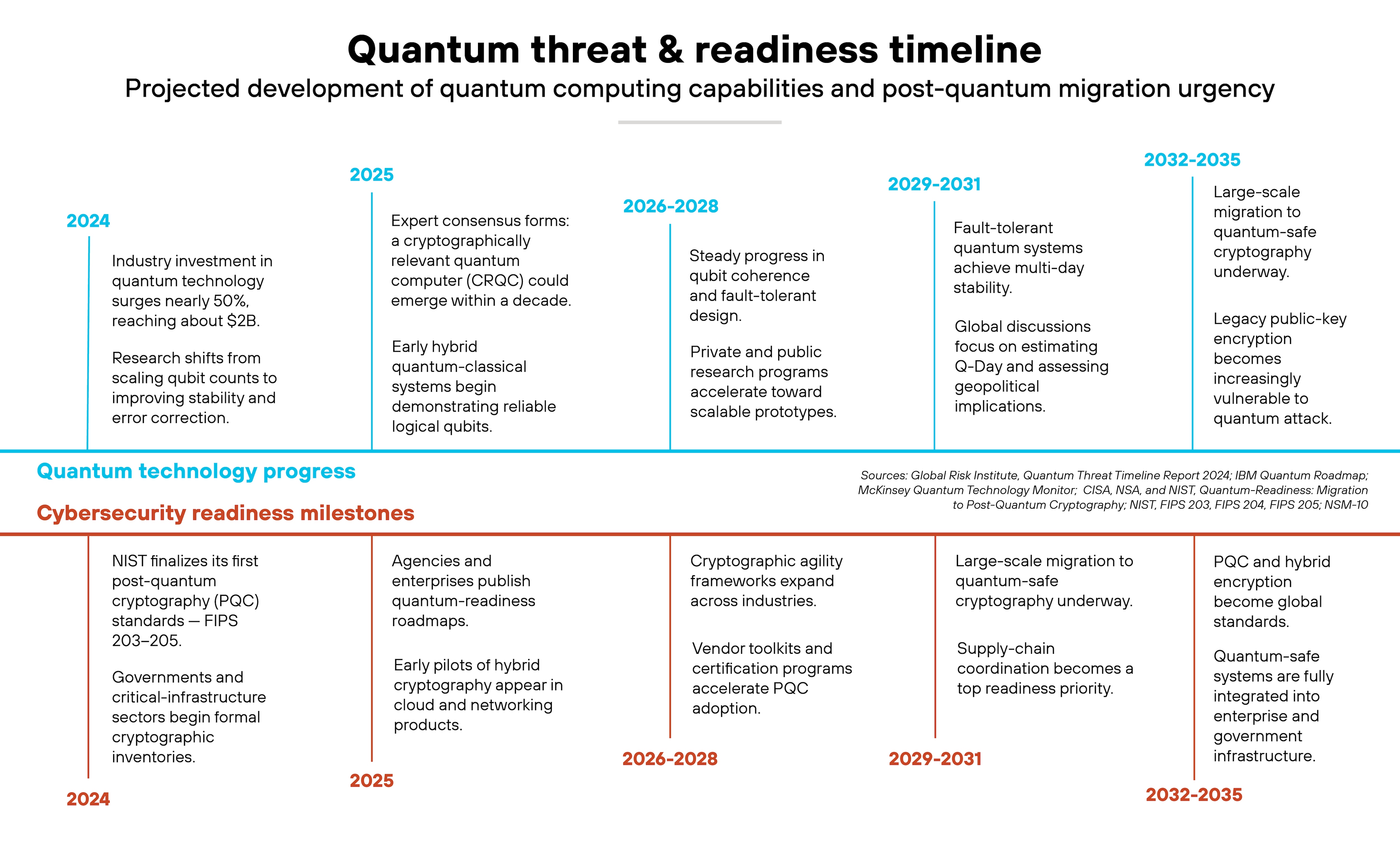
No one knows the exact date of Q-Day—the moment when quantum computers can break today's encryption. But experts agree it's not centuries away.
Most projections estimate a window of roughly 10 to 15 years. Some predict sooner, others later. The disagreement reflects how many variables remain unresolved.
Here's why forecasts differ.
Building a cryptographically relevant quantum computer isn't just about adding more qubits. Those qubits have to stay stable long enough to perform complex operations. And that requires breakthroughs in error correction, scalability, and hardware design.
Funding and national investment also play a role. Countries pouring billions into quantum research could shorten the timeline dramatically.
Remember: uncertainty itself is the risk.
Migration to post-quantum cryptography can't be reactive. Once a quantum computer reaches the threshold to break RSA or elliptic-curve encryption, it will already be too late to protect the data that was stolen years earlier.
To put it another way, waiting for a confirmed date for Q-Day misses the point.
The goal isn't to predict the day quantum decryption becomes possible. It's to make sure encrypted information will still be secure when that day comes.
And it is coming.
How to prepare for the post-quantum threat today
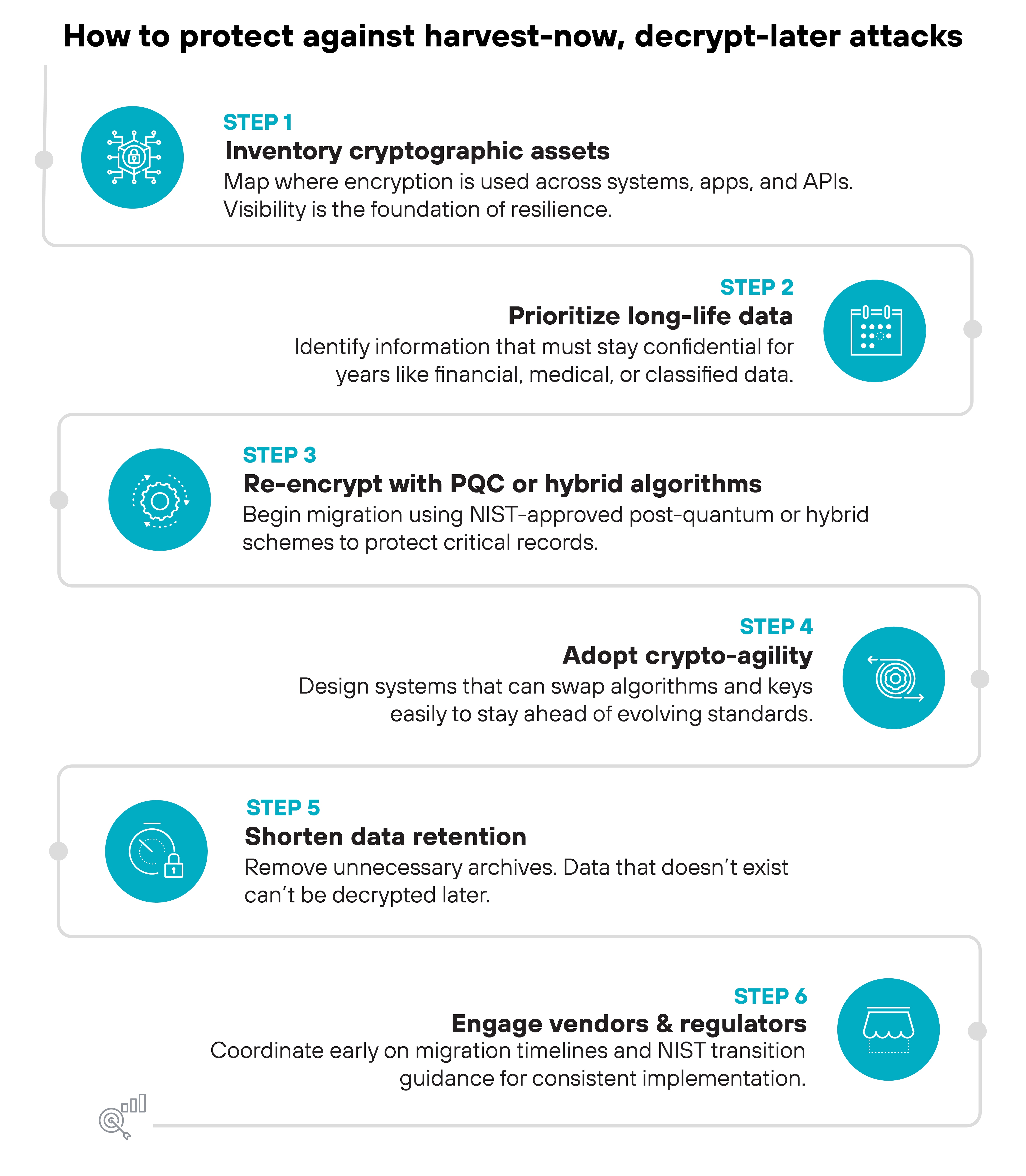
Governments and industry groups are accelerating post-quantum migration because of harvest-now-decrypt-later exposure. But defense ultimately starts at the organizational level.
The key is to act before quantum decryption becomes possible. Again, once the data is collected, it can't be unharvested.
Here's how to start:
Inventory cryptographic assets and dependencies.
Map every place encryption is used: applications, APIs, devices, and third-party integrations. Visibility is the foundation of any quantum-resilient strategy.
Prioritize long-life and sensitive data.
Identify which records must remain confidential for years or decades, such as financial transactions, intellectual property, and classified archives. Those should migrate first.
Re-encrypt or segment data using post-quantum or hybrid algorithms.
Adopt NIST-approved PQC standards—ML-KEM (FIPS 203), ML-DSA (FIPS 204), and SLH-DSA (FIPS 205)—where possible. Hybrid models let you combine classical and quantum-safe encryption during transition.
Start with pilot environments or non-critical workloads to validate performance, compatibility, and interoperability before scaling broadly.
Adopt crypto-agility.
Design systems to change algorithms and keys easily.
Static cryptography locks you into today's vulnerabilities. Crypto-agility should also extend to certificate management, key rotation, and lifecycle governance.
Shorten data retention.
Data that no longer exists can't be decrypted later. Review archival policies and delete what you don't need.
Engage vendors and regulators.
Align migration plans, compliance requirements, and interoperability standards early.
Follow NIST's post-quantum cryptography transition guidance and monitor emerging timelines in your industry to stay synchronized.
These steps align with broader PQC migration and zero-trust design. Every encrypted record you protect now is one that won't become tomorrow's breach.