- What is Security Analytics?
-
What is SIEM?
- SIEM: The Foundation for XSIAM
- How SIEM Works
- Key Functions and Benefits of SIEM
- Role of AI and ML in SIEM
- SIEM Integration
- SIEM Use Cases
- How to Choose a SIEM Solution
- Best Practices for SIEM Implementation
- SIEM vs Other Security Solutions
- What is Cloud SIEM?
- The Evolution of SIEM
- The Future of SIEM
- SIEM FAQs
- What is Security Information and Event Management (SIEM) Integration?
- What is SIEM Logging?
- What Is Security Event Management (SEM)?
- What is a SIEM Solution in a SOC?
-
What Is the Role of AI and ML in Modern SIEM Solutions?
- The Evolution of SIEM Systems
- Benefits of Leveraging AI and ML in SIEM Systems
- SIEM Features and Functionality that Leverage AI and ML
- AI Techniques and ML Algorithms that Support Next-Gen SIEM Solutions
- Predictions for Future Uses of AI and ML in SIEM Solutions
- Role of AI and Machine Learning in SIEM FAQs
-
What is Cloud SIEM?
- Why Use a Cloud SIEM?
- How SIEM Interacts with Cloud Environments and SaaS Applications
- Core Cloud SIEM Features and Capabilities
- Cloud SIEM Deployment Models
- On-Premise vs. Cloud SIEM Deployment
- Key Steps for Implementing Cloud SIEM
- Cloud SIEM Challenges
- Considerations of a Cloud Native SIEM Solution
- Cloud SIEM FAQs
- What Is Security Information Event Management (SIEM) Software?
- What are SIEM Use Cases?
- What Are Security Information and Event Management (SIEM) Tools?
How Do SIEM Tools Benefit SOC Teams?
Security Information and Event Management (SIEM) tools streamline security processes and provide deep insights into an organization's security posture. They do this by integrating data from various sources and employing advanced analytics to pinpoint likely threats. SIEM tools are the technological support for SOC teams, enabling them to focus on incidents that pose a genuine risk to their systems, enhancing the efficiency and effectiveness of their response to cyber threats.
What is a SOC (Security Operations Center)?
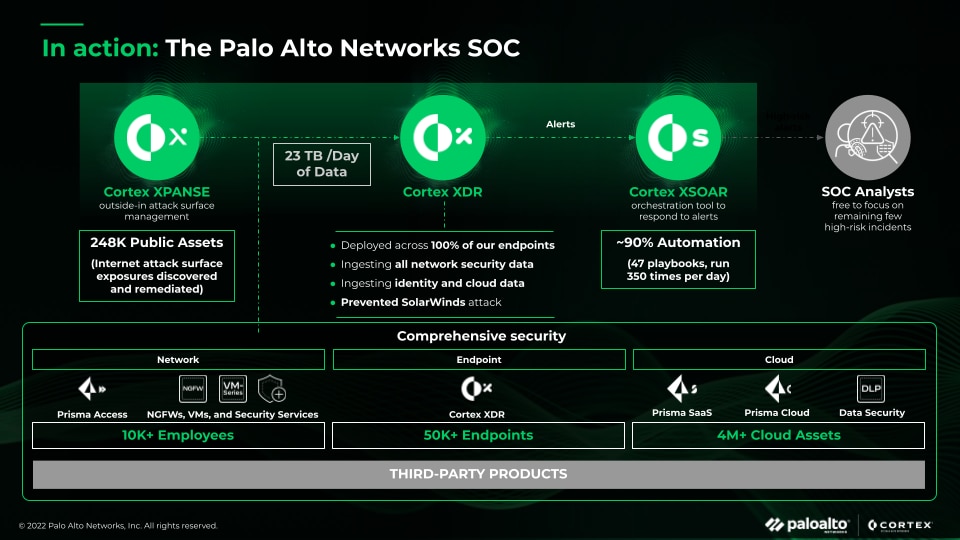
A SOC is the heart of an organization's cybersecurity defense, providing 24/7 surveillance and rapid response capabilities to protect against various digital threats. A SOC ensures that potential security incidents are correctly identified, analyzed, defended, investigated, and reported. The primary goal of a SOC is to protect the organization from security breaches and maintain the integrity, confidentiality, and availability of its information.
What is Security Information and Event Management (SIEM)?
SIEM is a critical tool in cybersecurity, acting as the brain and sensory system for an organization's digital environment. It helps security teams to quickly identify, assess, and respond to potential security events, ensuring the organization's digital health and safety.
When it comes to keeping an organization's digital systems secure, two essential tools come into play: Security information management (SIM) and security event management (SEM). SIM is like the system's memory, collecting and storing security-related data, while SEM is like our senses, detecting and interpreting what's happening in real-time.
SIEM technology processes and analyzes the data from an organization's network in real-time, much like how our nervous system processes sensory information. It alerts the security team if it detects something unusual or potentially harmful, such as a cyberattack.
SIEM plays a central role in an organization's cybersecurity efforts, continuously monitoring and gathering information from various parts of the IT infrastructure. Analyzing this data can identify patterns or activities indicating a security threat, such as a hacker trying to break into the system. It's like having an intuitive sense to tell when something is wrong.
The Benefits of SIEM Tools for SOC Teams
SIEM systems are multi-faceted tools that significantly augment the capabilities of SOC teams. From aggregating and contextualizing security data to automating threat detection and simplifying compliance, SIEM is a cornerstone of robust cybersecurity defenses.
Log Aggregation: Centralizing Security Data
One of the primary functions of a SIEM is its ability to aggregate logs. It integrates with various endpoints and security solutions across the network, collecting and standardizing log files and alert data. This aggregation facilitates SOC analysts in incident detection, response, and proactive threat hunting by providing a unified view of security data.
Increased Context for Accurate Threat Detection
In the complex cybersecurity landscape, isolated data points often appear as harmless noise. SIEM systems excel in correlating these data points, providing the context needed to distinguish genuine threats from benign anomalies. This ability to discern subtle and sophisticated cyberattacks is crucial in protecting an organization's network.
Real-Time Monitoring and Alerting
SIEM systems function like vigilant, ever-watchful guards, offering continuous monitoring capabilities. They analyze and correlate data across the network in real time, promptly identifying potential threats. This constant vigilance ensures that SOCs remain a step ahead of cybercriminals, ready to act at the earliest indication of malicious activity.
Reduced Alert Volume and Enhanced Focus
Organizations often grapple with a flood of alerts from various security solutions, leading to alert fatigue. SIEM solutions help organize and correlate this data, pinpointing alerts most likely linked to real threats. This refined focus enables SOC analysts to concentrate on significant alerts, drastically reducing time spent on false positives.
Automated Threat Detection and Response
Many SIEM solutions have built-in rules for detecting suspicious activities, such as an unusual number of failed login attempts indicating a potential password-guessing attack. These automated detection capabilities expedite the identification of threats and enable automated responses to certain attack types, enhancing the speed and accuracy of the SOC's reaction.
Enhanced Incident Response
Speed is critical in responding to detected threats. SIEM tools automate crucial initial stages of the incident response process, enabling SOCs to contain and mitigate risks quickly. This rapid response is vital in minimizing the damage and impact of security breaches.
Compliance and Reporting Ease
In the tightly regulated realm of cybersecurity, compliance is not just a best practice but a mandate. SIEM tools simplify this aspect by automating the creation of comprehensive reports, streamlining compliance audits, and ensuring adherence to various regulatory standards.
Implementing SIEM in SOCs
SIEM (security information and event management) can be seamlessly integrated with existing security systems to improve the overall security infrastructure without needing a complete overhaul. Integrating SIEM can enhance an organization's overall security infrastructure, providing a more comprehensive approach to security.
Along with giving organizations a unified view of their security posture in real-time, SIEM tools are scalable and can be customized according to each organization's specific requirements. This flexibility ensures that SIEM tools remain effective, regardless of the size and complexity of a network. They can be tailored to meet the organization's unique needs and provide a more comprehensive approach to security.
It is important to note that implementing a SIEM system requires skilled professionals who understand the nuances of cybersecurity. The staff responsible for implementing and managing the SIEM system should have the necessary training and expertise to make the most of the technology. Investing in staff training is crucial for maximizing the benefits of a SIEM system.
Challenges and Considerations
While SIEM systems are powerful tools for enhancing cybersecurity, they challenge SOC teams. Addressing these challenges requires a thoughtful approach, ensuring the SIEM system enhances security and aligns with the organization's broader objectives and capabilities.
Balancing Configuration with Threat Response
To make a SIEM solution work, it has to be connected to various security systems and endpoints within an organization's network. This is important for the SIEM to be effective in providing value. However, the initial setup of the SIEM can be time-consuming. It requires considerable effort from SOC analysts, which can take their attention away from detecting and responding to threats on the network.
Rule-Based Threat Detection
SIEM solutions can automatically detect certain types of cyberattacks by analyzing data. However, these detections are based on predefined rules. While this helps identify familiar threat patterns, it also has limitations. These rule-based systems may not be effective in recognizing new or unusual attacks that don't match known patterns or behaviors.
Alert Generation without Inherent Validation
SIEM systems gather and analyze data from various platforms within an organization's network to detect potential threats. Based on this information, they generate alerts. However, these alerts are only sometimes accurate. Even though SIEM alerts are more detailed and informative than raw data, they can still produce false positives. SOC teams must verify the accuracy and relevance of these alerts since SIEMs don't validate them.