- What is Security Analytics?
-
What is SIEM?
- SIEM: The Foundation for XSIAM
- How SIEM Works
- Key Functions and Benefits of SIEM
- Role of AI and ML in SIEM
- SIEM Integration
- SIEM Use Cases
- How to Choose a SIEM Solution
- Best Practices for SIEM Implementation
- SIEM vs Other Security Solutions
- What is Cloud SIEM?
- The Evolution of SIEM
- The Future of SIEM
- SIEM FAQs
- What is Security Information and Event Management (SIEM) Integration?
- What Is Security Event Management (SEM)?
- What is a SIEM Solution in a SOC?
- How Do SIEM Tools Benefit SOC Teams?
-
What Is the Role of AI and ML in Modern SIEM Solutions?
- The Evolution of SIEM Systems
- Benefits of Leveraging AI and ML in SIEM Systems
- SIEM Features and Functionality that Leverage AI and ML
- AI Techniques and ML Algorithms that Support Next-Gen SIEM Solutions
- Predictions for Future Uses of AI and ML in SIEM Solutions
- Role of AI and Machine Learning in SIEM FAQs
-
What is Cloud SIEM?
- Why Use a Cloud SIEM?
- How SIEM Interacts with Cloud Environments and SaaS Applications
- Core Cloud SIEM Features and Capabilities
- Cloud SIEM Deployment Models
- On-Premise vs. Cloud SIEM Deployment
- Key Steps for Implementing Cloud SIEM
- Cloud SIEM Challenges
- Considerations of a Cloud Native SIEM Solution
- Cloud SIEM FAQs
- What Is Security Information Event Management (SIEM) Software?
- What are SIEM Use Cases?
- What Are Security Information and Event Management (SIEM) Tools?
What is SIEM Logging?
Security information and event management (SIEM) is a comprehensive solution in cybersecurity. It combines security information management (SIM) and security event management (SEM) to provide real-time analysis of security alerts generated by applications and network hardware.
SIEM systems collect and aggregate log data generated throughout an organization's technology infrastructure, from host systems and applications to network and security devices such as firewalls and antivirus filters.
SIEM logging is at the heart of SIEM's capability - a crucial element that transforms raw data into meaningful insights, enhancing security measures and strategies. SIEM logging is collecting, aggregating, and analyzing log data from diverse sources within an organization's IT infrastructure. This process turns SIEM into a centralized platform, enabling security analysts to sift through vast data to spot potential security threats and respond effectively.
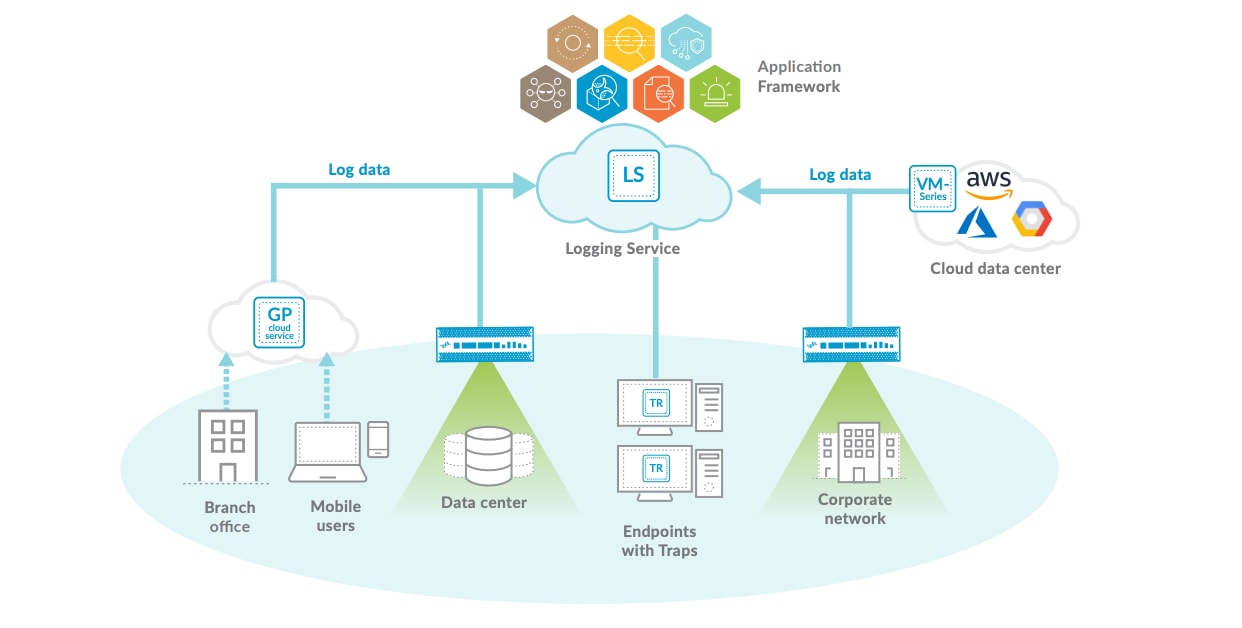
Palo Alto Networks Logging Service enables actionable insights by applying machine learning and advanced analytics to large volumes of data within the Application Framework.
Why is SIEM Logging Important for IT Security?
The SIEM platform is a central component of many traditional security programs that analyzes any number and type of log files to identify security incidents or emerging threats. This feature differentiates it from security tools like EDR (endpoint detection and response).
SIEM vendors often offer additional functionality, such as UEBA (user and entity behavior analytics) and response actions via SOAR (security orchestration, automation, and response) as add-ons. With advanced SIEM logging, security teams can detect and alert suspicious activities, analyze user behavior to identify anomalies, and have centralized visibility into security events across the organization.
SIEM monitors security-related activities such as user logins, file access, and changes to critical system files, which are captured as log data. The software then applies analytics and correlation algorithms to this data to identify potential security incidents or threats.
SIEM vs. Log Management: Understanding the Differences
While SIEM and traditional log management involve collecting and storing log data, SIEM goes further. It combines log data with additional contextual information, enabling more analysis and real-time threat detection, a feature typically absent in basic log management systems.
Log Management
A log management system collects, stores, and sometimes analyzes log data generated by various systems, applications, and devices within an IT infrastructure.
Log management aggregates logs from different sources, organizing them in a centralized location, and typically involves tasks like retention, archival, and basic search functionalities. Log management systems are a repository where security analysts can access and analyze logs as needed. Still, they may not generally provide automated security analysis or real-time threat detection.
SIEM Management
SIEM tools enhance log management by allowing real-time analysis and correlation of security events. These tools collect log data from various sources and use security-focused analytics and correlation techniques to identify patterns, anomalies, and potential security incidents.
SIEM systems include threat intelligence integration from internal and external sources, alerting, incident response workflows, and compliance reporting. They provide a more comprehensive view of an organization's security posture by correlating data from multiple sources to identify and respond to security threats effectively.
Log management focuses more on log collection and storage, while SIEM integrates this data to provide real-time security monitoring, threat detection, and incident response capabilities. SIEM solutions often encompass log management as a core component but go beyond it to offer advanced security functionalities.
Differences Between SIEM and Syslog
Syslog is a protocol used to send log messages within a network. It's a standard protocol that many devices and systems (like routers, switches, servers, firewalls, etc.) use to generate and transmit log data. Syslog messages contain information about these devices and applications' events, errors, or activities.
Syslog messages can be collected and sent to a centralized location (like a Syslog server or a SIEM system) for storage, analysis, and monitoring. However, syslog does not analyze or correlate these logs; it's primarily a method for log transport.
Key Components in SIEM Logs
The critical components of SIEM logs are the fundamental data elements that these systems collect and analyze to identify and respond to security incidents. These components include:
- Timestamps: Each log entry is marked with a timestamp, indicating when the event occurred. This is crucial for chronological analysis and correlating events across different systems.
- Source and Destination Information: Logs contain details about the source (where the event originated) and destination (the event's target). This information is vital in network security for tracking data flow and identifying potential external threats.
- User Information: Logs often include user information, such as usernames or account IDs, especially for access control and authentication events. This helps in identifying which users were involved in specific events.
- Event Type: This specifies the nature of the event recorded in the log, such as a login attempt, file access, system warning, error messages, or network connections.
- Action Taken: If the event triggered a response, this is recorded in the log. For instance, whether an access attempt was allowed or denied or if an error triggered a specific system response.
- Resource Accessed: Particularly in the context of access control and file integrity monitoring, logs detail which resources (like files, databases, or applications) were accessed.
- Severity Level: Many SIEM systems classify events by severity level, helping prioritize responses. For example, a failed login attempt might be a lower severity, while malware detection would be a high severity.
- Status Codes: These codes provide quick reference points to understand the outcome of an event, such as successful or failed processes.
- Data Transferred: In the case of network security events, the amount of data transferred during an incident can be a key indicator of the nature and severity of the event.
- Additional Contextual Information: Advanced SIEM systems might add more context to logs, like geolocation data, system configuration changes, or correlation with known threat databases.
These components provide a comprehensive view of the security events within an organization's IT infrastructure, enabling effective monitoring, analysis, and response to potential security incidents.
The Mechanics of SIEM Logging
Understanding the underlying mechanics of SIEM Logging is key to appreciating its value in cybersecurity. This section delves into the core processes involved in SIEM Logging, from data collection to generating alerts and reports.
Data Collection
SIEM Logging is a crucial process that helps organizations effectively monitor and secure their IT infrastructure. The process of SIEM Logging starts with data collection. Every element of an organization's IT infrastructure, from firewalls to applications, contributes logs, which provide a composite view of the network's health and security.
Data Normalization
Once the data is collected, the next step is data normalization. This vital process involves standardizing disparate log formats into a unified structure. Data normalization makes analyzing and comparing logs easier, which is crucial in identifying patterns and anomalies.
Detection and Correlation
The next stage is detection and correlation. This is where SIEM tools showcase their ability to identify patterns and anomalies in the normalized data. Early detection of potential security incidents is crucial; this stage helps achieve that goal. This step is crucial for the early detection of potential security incidents.
Alerts and Reporting
Finally, SIEM systems generate alerts and reports. Generating alerts and reports is the final piece of the puzzle. SIEM systems notify teams of immediate threats and aid in compliance and deeper security analysis through comprehensive reporting. The reports generated by SIEM systems are particularly useful in identifying trends and patterns, which can help organizations improve their overall security posture. SIEM systems notify teams of immediate threats and aid in compliance and deeper security analysis through comprehensive reporting.
SIEM Logging Best Practices
The best practices for SIEM logging are essential for maximizing the effectiveness of SIEM systems. These practices help ensure that SIEM tools collect and analyze data efficiently and contribute to improved security postures for organizations. Here are some of the key best practices:
- Selective Data Collection: Carefully select which data sources to monitor and collect logs from, focusing on those most relevant to your organization's security needs. This targeted approach helps in efficiently utilizing SIEM resources and reducing noise from irrelevant data.
- Data Normalization: Normalize log data to a consistent format. This standardization is crucial for practical analysis, allowing for more straightforward correlation and data comparison from different sources.
- Real-time Monitoring and Analysis: Set up SIEM systems for real-time monitoring and analysis to enable immediate detection and response to potential security incidents.
- Event Correlation: Employ sophisticated algorithms for event correlation. This involves analyzing patterns and relationships in the log data to identify potential security threats.
- Regular Updates and Maintenance: Regularly update and maintain your SIEM system. This includes updating rules and signatures, patching software, and ensuring the system is tuned to adapt to the evolving security landscape.
- Compliance and Regulation Alignment: Ensure that your SIEM logging practices align with relevant compliance requirements and regulations, which may dictate specific data types to be collected and retained.
- User and Entity Behavior Analytics (UEBA): Implement UEBA to detect anomalies and potential threats based on deviations from established behavior patterns.
- Effective Storage Management: Manage log data storage efficiently, considering the storage solutions' security and scalability.
- Regular Review and Auditing: Periodically review and audit the SIEM system and its logs to ensure its functioning as intended and identify improvement areas.
- Training and Awareness: Ensure your team is trained and aware of using the SIEM system effectively. This includes understanding the system's capabilities and interpreting and responding to the alerts it generates.
- Integration with Other Security Tools: Integrate SIEM with other security tools and systems for a more comprehensive security approach. This can enhance overall visibility and threat detection capabilities.
SIEM Logging Challenges and Solutions
SIEM log management comes with challenges, and addressing them effectively is critical to maintaining a robust cybersecurity posture. Here's an expanded view of the common hurdles in SIEM logging and how to overcome them:
| Problem | Solution |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|