- What is Security Analytics?
-
What is SIEM?
- SIEM: The Foundation for XSIAM
- How SIEM Works
- Key Functions and Benefits of SIEM
- Role of AI and ML in SIEM
- SIEM Integration
- SIEM Use Cases
- How to Choose a SIEM Solution
- Best Practices for SIEM Implementation
- SIEM vs Other Security Solutions
- What is Cloud SIEM?
- The Evolution of SIEM
- The Future of SIEM
- SIEM FAQs
- What is Security Information and Event Management (SIEM) Integration?
- What is SIEM Logging?
- What Is Security Event Management (SEM)?
- How Do SIEM Tools Benefit SOC Teams?
-
What Is the Role of AI and ML in Modern SIEM Solutions?
- The Evolution of SIEM Systems
- Benefits of Leveraging AI and ML in SIEM Systems
- SIEM Features and Functionality that Leverage AI and ML
- AI Techniques and ML Algorithms that Support Next-Gen SIEM Solutions
- Predictions for Future Uses of AI and ML in SIEM Solutions
- Role of AI and Machine Learning in SIEM FAQs
-
What is Cloud SIEM?
- Why Use a Cloud SIEM?
- How SIEM Interacts with Cloud Environments and SaaS Applications
- Core Cloud SIEM Features and Capabilities
- Cloud SIEM Deployment Models
- On-Premise vs. Cloud SIEM Deployment
- Key Steps for Implementing Cloud SIEM
- Cloud SIEM Challenges
- Considerations of a Cloud Native SIEM Solution
- Cloud SIEM FAQs
- What Is Security Information Event Management (SIEM) Software?
- What are SIEM Use Cases?
- What Are Security Information and Event Management (SIEM) Tools?
What is a SIEM Solution in a SOC?
SIEM solutions and SOCs form the backbone of modern cybersecurity strategies, offering the tools and expertise needed to safeguard digital environments. A SIEM solution acts as the central nervous system of an organization's security framework. It collects, analyzes, and correlates data from various sources within the IT infrastructure, including network devices, servers, and security systems.
This data aggregation enables the SIEM to identify patterns and anomalies that could indicate a security incident, facilitating rapid detection and response to potential threats. By integrating a SIEM solution in a SOC, organizations can significantly enhance their ability to monitor, assess, and mitigate cybersecurity risks in real time.
What is a Security Information and Event Management (SIEM) Solution?
SIEM is a critical part of the cybersecurity framework, offering insights into an organization's security landscape. It uses advanced analytics like machine learning and pattern recognition to identify and respond to potential security incidents, reducing false positives.
Integration with SOC amplifies its capabilities by providing a consolidated view of the organization's security posture, facilitating swift decision-making and action. It empowers SOCs with the tools and intelligence necessary to maintain a vigilant and resilient defense against cyber threats, making it an indispensable component of any robust cybersecurity strategy.
What Is a Security Operations Center (SOC)?
A security operations center (SOC) functions in a cybersecurity program and manages threats against an organization. The SOC is responsible for identifying, investigating, and remediating threats. The SOC also advises security leaders and the business on the threats the organization may face as the threat landscape changes.
Historically, a SOC was an on-premises collection of people and technology, but there are also instances of it being shared responsibility, particularly for low-maturity, budget-constrained organizations. The modern SOC has mainly distributed personnel with a rapidly increasing use of cloud-native or hosted security tools.
Organizations will use three main SOC models: hybrid, internal, or tiered. Hybrid is a mix of internal and third-party service providers, internal is exclusively internal personnel only, and tiered has a top-tier SOC with multiple smaller SOCs that report up.
For a deep dive into a security operations center, read our article, What is a SOC?
Key Components of SIEM Solutions
In the dynamic field of cybersecurity, security information and event management (SIEM) systems stand as multifaceted solutions. They combine several key components to provide comprehensive security monitoring. Understanding these components is crucial for cybersecurity professionals to effectively implement and utilize SIEM systems.
Data Collection and Aggregation
Sources of Data and Integration Challenges
SIEM systems collect data from various sources within an organization's network, including firewalls, intrusion detection systems, antivirus software, servers, and network devices. The challenge is to unify the data into a compatible format for accurate analysis, keeping information the same.
Real-time Monitoring and Event Correlation
Techniques for Effective Event Correlation
SIEM systems perform real-time monitoring and analyze incoming data to detect anomalies or patterns that could indicate a security incident. Effective event correlation involves cross-referencing known threat patterns, statistical anomaly detection, and heuristic models to distinguish normal network behavior from potentially malicious activity, enabling quicker threat detection.
Alerting and Threat Detection
Balancing Sensitivity and Specificity in Alerts
SIEM systems aim to detect security threats and alert relevant personnel. Balancing alert sensitivity and specificity is challenging. High sensitivity leads to false positives and alert fatigue, while too much specificity leads to false negatives. Optimizing this balance is critical. SIEM systems use advanced algorithms and machine learning to improve alert accuracy and enhance overall security.
How Does SIEM Integrate with SOC?
SIEM (security information and event management) systems are integral to a security operations center (SOC). They provide the necessary tools and capabilities for comprehensive security monitoring, threat detection and analysis, incident response, and compliance management, all critical components of SOC operations. They integrate with SOC operations in several key ways to enhance the overall effectiveness of cybersecurity efforts:
- Data Aggregation and Management: SIEM systems collect and manage data from many sources across the organization's network, including firewalls, intrusion detection systems, network devices, and antivirus solutions. This data aggregation is crucial for SOC teams to view the security landscape comprehensively.
- Real-Time Monitoring and Alerting: SIEM solutions provide real-time monitoring of security data. They analyze this data to identify potential security threats or breaches and generate alerts. SOC analysts then prioritize and manage these alerts, forming the backbone of the SOC's monitoring capabilities.
- Event Correlation and Analysis: One of the most critical functions of SIEM in a SOC is correlating disparate data to identify patterns indicative of cyber threats. This correlation helps SOC teams recognize complex, multi-stage attacks that might not be apparent when viewing isolated events.
- Incident Response and Management: The SIEM system can trigger response protocols when identifying a security incident. It aids SOC teams in managing and tracking the incident response process, ensuring that all aspects of the incident are addressed.
- Compliance and Reporting: SIEM systems assist SOCs in maintaining compliance with various regulatory standards by automating the collection, storage, and reporting of security-related data. This is crucial for organizations adhering to GDPR, HIPAA, or PCI-DSS regulations.
- Threat Hunting and Forensics: SOC analysts use SIEM tools for proactive threat hunting. By analyzing historical data and current trends, they can identify previously undetected threats. SIEMs also provide valuable data for forensic analysis in case of a security breach.
- Integration with Other Security Tools: SIEM systems in a SOC often integrate with other security tools like endpoint protection platforms, threat intelligence feeds, and vulnerability management systems. This integration allows for a more coordinated and comprehensive approach to security.
- Workflow Automation and Orchestration: Advanced SIEM solutions can automate and orchestrate various security workflows, thereby improving the efficiency of SOC operations. This includes automating routine tasks and orchestrating complex processes across different security tools.
Benefits of SIEM Solutions in the SOC
SIEM products can provide the SOC team with a "big picture" view of security events across the organization. Because SIEMs are the only security controls with accurate enterprise-wide visibility, they could identify malicious activity undetectable by any other single host.
The analysis capabilities of SIEM systems allow them to detect attacks that would not be detectable through other methods and help adjust enterprise security controls to eliminate security gaps. Some of the top SIEM products can even prevent security breaches if they are detected while attacks are still in progress.
Why is SIEM Utilized?
Security information and event management (SIEM) aggregates security event data from applications, networks, endpoints, and cloud environments and then utilizes it for security monitoring, threat detection and response, and sometimes risk scoring.
SIEM software collects, stores, analyzes, and reports on log data generated by various systems and applications in a network. It monitors security-related activities such as user logins, file access, and changes to critical system files. SIEM vendors often include or sell additional functionality as add-ons, including user and entity behavior analytics (UEBA), and response actions via security orchestration, automation and response (SOAR).
Compliance reporting is a foundational component of SIEM, with risk posture and reporting becoming standard out-of-the-box features. Historically, SIEM was primarily an on-premises solution, but most of the SIEM market has migrated to cloud-native or hosted architectures. SIEM is and continues to be the cybersecurity system of record of many organizations' security operation centers (SOCs).
Traditional SIEMs
Initially, traditional SIEMs centralized logs, alerts, and events from different security tools within the environment and required compute, storage, and backup management to store this information from various systems.
This required an extensive investigation of information by a highly talented group that would have to sift through a massive amount of misleading data to find the genuine security dangers a business faced.
Traditional SIEMs faced several significant challenges, including:
- Inflexible datasets that could not be analyzed, limiting efficiency.
- Depleted staff resources due to challenges associated with maintaining and operating SIEMs.
- A large number of false positives.
- Inability to keep up with emerging threats as technology evolved, leaving enterprises at higher risk.
The complexity of traditional SIEMs created a lot of work for security teams, as they were required to sort through hundreds or thousands of lines of information to figure out what was happening. A traditional SIEM lacked the automated capabilities necessary to detect threats and respond to incidents in real-time, which next-gen SIEM platforms aimed to provide.
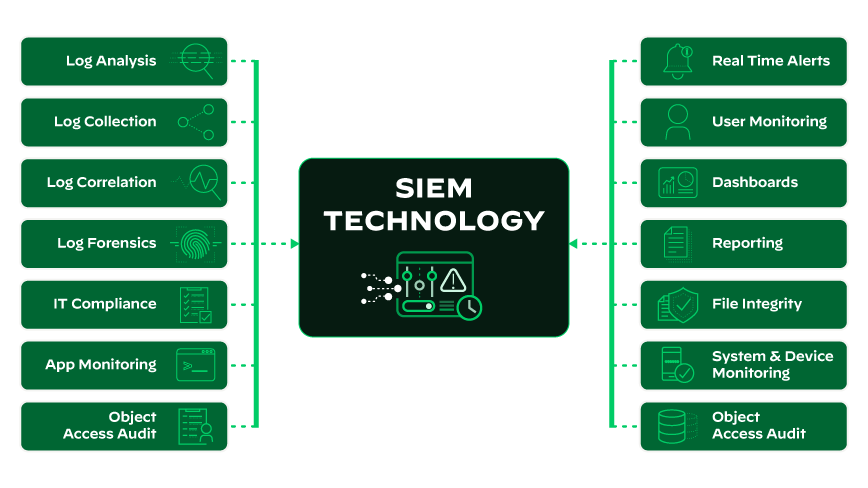
Limitations of a SIEM
Despite their many benefits, SIEM solutions have some significant limitations, such as:
- Configuration and Integration: For a SIEM solution to provide value to an organization, it must be appropriately configured to connect with the various endpoints and security solutions within the network. This can be a time-consuming process for SOC analysts, which detracts from their ability to detect and respond to active threats.
- Inaccurate or Incomplete Data: A SIEM solution uses data collected from various sources to work correctly. If any of these data sources are inaccurate, incomplete or not connected to the SIEM properly, it can lead to problems with the solution. This can make it difficult for SOC analysts to trust the data provided by the SIEM solution, which can impact its overall effectiveness.
- Rules-Based Detection Capabilities: SIEM solutions can detect attacks automatically based on the data they collect. However, these detection capabilities are largely rules-based. So, while a SIEM may be very good at identifying certain types of threats, it is likely to overlook novel attacks that do not match an established pattern.
- False-Positive Detections: SIEMs generate alerts based on collected data and analysis, but no alerts are validated. As a result, the SIEM’s alerts — while potentially higher quality and more context-based than the data and alerts it ingests — can still contain false-positive detections.
What Is Next-Generation SIEM?
In the modern era of advanced threats, many advanced threats have become polymorphic rather than static, meant to evade detection by continually changing their behavior. SIEM systems must be able to process more data while also recognizing distinct patterns within that data more effectively.
Many commentators predicted the demise of legacy SIEM systems due to their limitations and difficulties. However, the technology has continued to evolve as more features have been bolted onto existing products.
While SIEM systems were once designed to process only a limited number of data sources, the "next generation" of SIEM systems can process a vast amount of data (both security and non-security events) and correlate it expeditiously.
SIEM Solutions in SOC FAQs
A SIEM should:
- Be capable of analyzing, gathering, and presenting information it collects from the network and connected security devices.
- Have identity and access management applications.
- Have tools for vulnerability management and policy compliance.
- Consists of the operating system, application logs and database, and external threat data.
SIEMs were built for vast log collection, with security analytics bolted on after the fact. They were built to collect logs, aggregate data, and analyze it, with compliance as the primary driver and big data storage and analysis as the solution.
With the evolution into security analytics platforms, SIEMs continue to face their original big data challenge and further analytics, correlation, query and visualization challenges. SIEMs take a nebulous approach to identifying threats, thereby running security analytics on top of huge datasets. — Forrester, Adapt or Die: XDR Is On A Collision Course With SIEM And SOAR.
For organizations needing more expertise or resources to implement, manage, maintain, and monitor a SIEM solution, other options, such as managed security services (MSS) and managed detection and response (MDR) services, may be worth researching.
Central log management is a solution that can be a first step toward a SIEM and helps to provide a centralized view of log data. Log data records everyday activity across an organization and can help troubleshoot issues and support broader business needs. While log management helps to aggregate log data, a SIEM provides much more capability. Therefore, a business should determine what it needs to ensure the functionality meets its expectations to avoid overpaying.