-
What Is SASE (Secure Access Service Edge)? | A Starter Guide
- Why do businesses today need SASE?
- What is SASE architecture?
- What are the components of SASE?
- What are the use cases for SASE?
- What are the benefits of SASE?
- What are the potential SASE implementation challenges?
- How to choose a SASE provider and what to look for
- How to execute a successful SASE implementation in 6 steps
- What are the most common SASE myths?
- How SASE works with complementary technologies
- Comparing SASE with other security and technology solutions
- What is the history of SASE?
- SASE FAQs
- What Is SSE? | Security Service Edge (SSE)
-
What is the cloud-delivered branch?
-
Secure Access Service Edge (SASE) Key Requirements
-
Protecting Data with a SASE Solution
-
End User Experience Monitoring
What Is SASE for the Cloud?
Secure access service edge (SASE) for the cloud provides users with secure and optimized access to cloud services, devices, applications, and resources, regardless of location. SASE for the cloud is a response to how IT is changing, where traditional perimeter-based security models aren't as effective because of cloud services, mobile devices, and remote work. It combines wide area network (WAN) and network security services into a single cloud-delivered service.
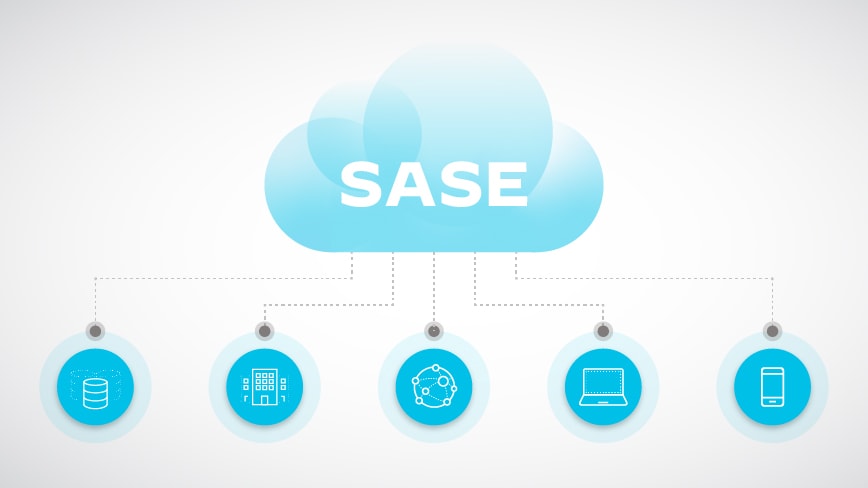
Fundamentals of SASE Architecture
SASE improves network security, reduces complexity, and boosts performance by moving network and security functions to the cloud. The SASE architecture looks like this:
- Cloud-centric architecture: SASE is built on a cloud-native model. Utilizing cloud infrastructure, it delivers network and security services that can be scaled up or down as needed. Cloud-based delivery of SASE services enables organizations to adjust their resources according to traffic patterns and business needs.
- Security service edge: With SASE, security services are delivered closer to users and devices at the network's edge. Especially for remote and mobile users, this helps reduce latency and improve performance.
- Software-defined WAN (SD-WAN): SASE architecture relies heavily on software-defined principles, like SD-WAN and software-defined security policies. Managing and automating network and security services is easier with SASE.
- Network and security convergence: Through SASE, networking and security services are unified. Traditionally, these functions were managed separately, which led to complexity and vulnerabilities. SASE integrates functions like SD-WAN, firewalls, secure web gateways, and Zero Trust network access.
- Zero Trust security: SASE is based on the Zero Trust security approach, which means devices and users aren't trusted by default. Identity verification, device health, and context determine access. As a result, the attack surface is minimized, and security is improved.
- Dynamic perimeter: In place of a fixed perimeter, SASE creates dynamic perimeters that adapt to user requirements. In today's remote and distributed work environment, this is especially important.
- Centralized management: With SASE, you can manage and enforce policies across the entire network, including remote locations and cloud resources. In this way, security enforcement and network administration are simplified.
By combining networking and security services into a cloud-native framework, SASE reimagines how networking and security services are delivered. This solution addresses the challenges of modern IT landscapes, like remote work, cloud adoption, and evolving security threats.
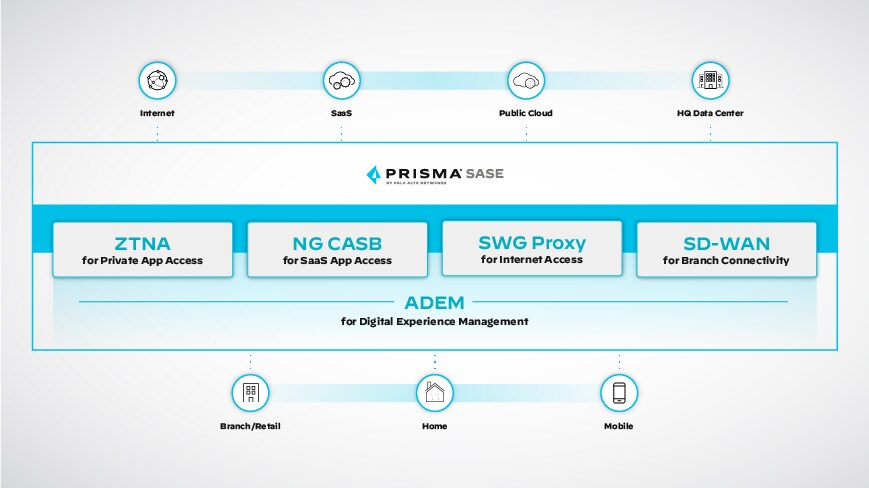
SASE Components for Cloud Security
SASE is a comprehensive framework integrating various components to provide cloud-centric security and networking capabilities. While specific implementations may vary among different SASE providers, here are some common SASE components for cloud security:
Firewall as a service (FWaaS): FWaaS offers advanced firewall features in the cloud. Inspecting and filtering incoming and outgoing data ensures that only authorized traffic passes through.
Secure web gateway (SWG): A SWG protects against web-based threats such as malware, phishing, and other malicious activity by filtering web traffic, categorizing URLs, and inspecting content.
Zero Trust network access (ZTNA): ZTNA enforces Zero Trust security by granting access to resources based on user identities, device postures, and other factors. As a result, only authenticated and authorized users can access applications and resources.
Cloud access security broker (CASB): A CASB acts as an intermediary between users and cloud service providers, helping to enforce security policies and protect data as it moves between on-premises and cloud environments.
Data loss prevention (DLP): DLP solutions monitor and prevent unauthorized transfers or leaks of sensitive information. A SASE architecture employs DLP capabilities to safeguard data as it moves from one user to another.
Identity and access management (IAM): IAM solutions manage authentication, access permissions, and user identities. In SASE, IAM is crucial for enforcing proper access controls and ensuring secure access.
Threat detection and response: In SASE solutions, advanced threat detection and response mechanisms, like behavioral analytics and machine learning, are used to identify and mitigate security threats.
Encryption and VPN services: To make data transmission between users and cloud resources more secure, SASE often includes encryption and VPN services.
Application visibility and control: With SASE, organizations can monitor and manage applications on the network, ensuring only approved apps are used, and security policies are followed.
Cloud security posture management (CSPM): Integrating CSPM within SASE ensures that cloud services and resources are correctly configured and secured.
Digital experience management (DEM): DEM's insights into user experience can inform SASE's network and security policies, enabling organizations to deliver both a high-quality and secure digital experience for their users across distributed environments.
SASE isn't limited to these components, and the specific features and offerings will vary based on the provider and cybersecurity landscape. Cloud security challenges may require new components and capabilities as SASE evolves.
SASE and Cloud Connectivity
SASE is closely aligned with cloud connectivity because it provides secure and optimized access to cloud resources for users and devices, no matter where they are. The key to SASE and cloud connectivity is ensuring users can securely and efficiently connect to cloud services and applications.
SASE providers usually have global points of presence (PoPs) worldwide. The PoPs provide entry and exit points for network traffic so that users can connect to cloud services with low latency and optimal performance.
SASE also uses software-defined networking to intelligently route traffic across various paths, including direct cloud connections, VPNs, and SD-WANs. Thanks to this optimization, users can access cloud resources via the most efficient and reliable routes, and cloud applications can access the necessary bandwidth and low-latency connections.
Remote users and branch offices can access cloud services securely with SASE. In organizations with distributed workforces or multiple locations, this is particularly important. With SASE, organizations can connect directly to cloud providers. Through this direct connection, traffic isn't backhauling through the corporate data center, which enhances performance and reduces latency.
Application-aware SASE solutions prioritize and route traffic based on application requirements. In this way, critical applications get the resources and connectivity they need.
By combining security and networking capabilities, SASE enhances cloud connectivity. Regardless of where users and devices are located, it optimizes access to cloud resources.
Implementation Strategies for SASE
Implementation strategies for SASE should include planning and deploying a combination of security and networking components to achieve a unified and cloud-centric security approach.
- Assessment and Planning
- Analyze your organization's current network architecture, security posture, and cloud usage habits.
- Identify the specific business goals and challenges you want to solve with SASE.
- Define your security requirements, including user authentication, access controls, data protection, and compliance.
- SASE Provider Selection
- Find out which SASE provider aligns best with your organization's needs by researching and evaluating them.
- Review industry analyst reports for SASE to help identify the top vendors.
- Consider global PoP, security services, integration capabilities, and pricing.
- Consider selecting a vendor who can offer a complete SASE solution (also known as Single Vendor SASE) to avoid having to integrate solutions from multiple vendors.
- Critical Applications and Resources
- Analyze which applications and cloud resources are critical to your business.
- Prioritize these applications and resources for optimal performance and security.
- User Identity and Access Management:
- Manage user identities, roles, and permissions with IAM.
- Improve secure access by implementing multifactor authentication (MFA).
- Zero Trust Architecture
- Embrace the Zero Trust model and assume that no user or device is inherently trustworthy.
- Apply strict access controls based on user identity, device health, and context.
- Network Security Services
- Implement FWaaS, SWG, and other security services your chosen SASE provider offers.
- Create policies that govern traffic flow, content filtering, and threat detection.
- SD-WAN and Network Optimization
- Ensure low-latency connections to cloud resources by integrating SD-WAN.
- Dynamically adjust traffic paths based on application requirements.
- Remote Access
- Set up secure remote access so remote and mobile users can access cloud services.
- Create policies that control remote access based on user profiles.
- Monitoring and Analysis
- Monitor and analyze network and application performance, as well as security events.
- Adapt your SASE deployment to emerging threats by using these insights.
- Migration and Integration
- Migrate existing security and networking solutions to SASE.
- Make sure your infrastructure and cloud are integrated seamlessly.
SASE implementation requires collaboration between IT teams, security experts, and stakeholders. Adapt your implementation strategies to your organization's needs and stay on top of industry trends.
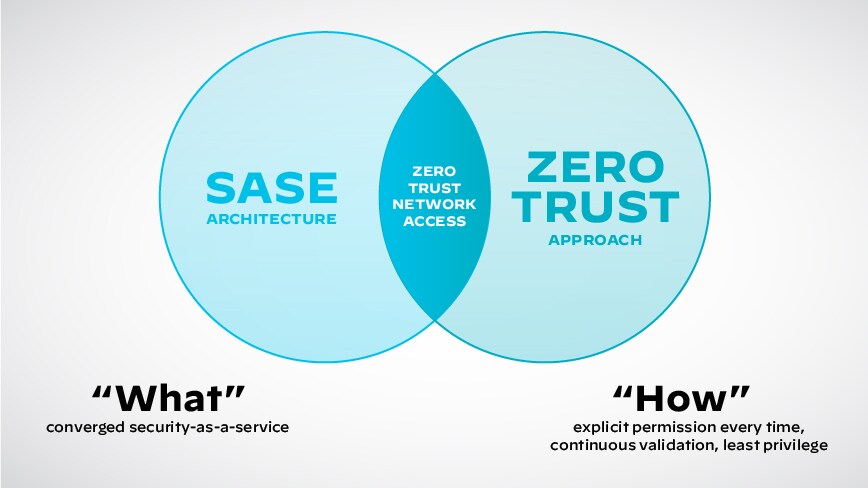
SASE and Zero Trust Security
SASE and Zero Trust security go hand in hand to create a holistic approach to modern cybersecurity. SASE and Zero Trust security aim to tackle the challenges posed by evolving IT landscapes, like cloud adoption and remote work.
A Zero Trust approach is identity-driven and treats all users, devices, and applications as potentially untrusted. Secure access is granted based on strict authentication, authorization, and continuous monitoring.
SASE and Zero Trust security use identity as the primary factor to grant application access. Using user and device identities to enforce policies, SASE integrates the Zero Trust requirement for strong identity verification.
A Zero Trust architecture emphasizes granular access controls based on least privilege, giving users only necessary access. With SASE, access is dynamically adapted based on the user's context and behavior.
They are both great for securing cloud resources and remote access. Regardless of location, SASE grants access based on zero-trust principles.
Continuous monitoring and assessing user and device behavior is vital to zero trust. SASE uses similar monitoring practices to detect threats and anomalies.
SASE has a unified architecture that seamlessly integrates networking and security. With a SASE framework, Zero Trust principles can be implemented across cloud services, remote users, and branch offices.
With SASE, you can implement Zero Trust principles effectively, ensuring that cloud resources and apps are secure, no matter where you are.
SASE and Cloud Security Future Trends
Organizations are recognizing the benefits of integrating security and networking into a unified framework, driving SASE adoption. SASE will become more popular as businesses adopt cloud services and remote work.
Machine learning and artificial intelligence will continue to enhance SASE providers' threat detection and response capabilities. Real-time traffic analysis will allow sophisticated threats to be identified.
Security models based on Zero Trust will continue to gain traction, become more mature, and become more widely used. Organizations will invest more in technology that enforces access controls, continuous monitoring, and behavioral analytics.
As cloud environments and applications rely more on APIs, securing APIs will become more important, and SASE providers will offer enhanced API security features.
With edge computing and IoT gaining popularity, SASE will be used to secure edge devices and data processing, necessitating the integration of security services closer to the edge.
In a multicloud world, SASE solutions will provide uniform security policies and controls across various cloud platforms, simplifying management and ensuring robust cloud security.
With DevOps practices and cloud-native architectures evolving, SASE solutions will integrate more seamlessly into these environments to ensure security is considered.
As SASE platforms get better analytics capabilities, organizations can gain more insight into network and security events, which will help them hunt for threats more effectively and improve security performance.