What Is a Double VPN?
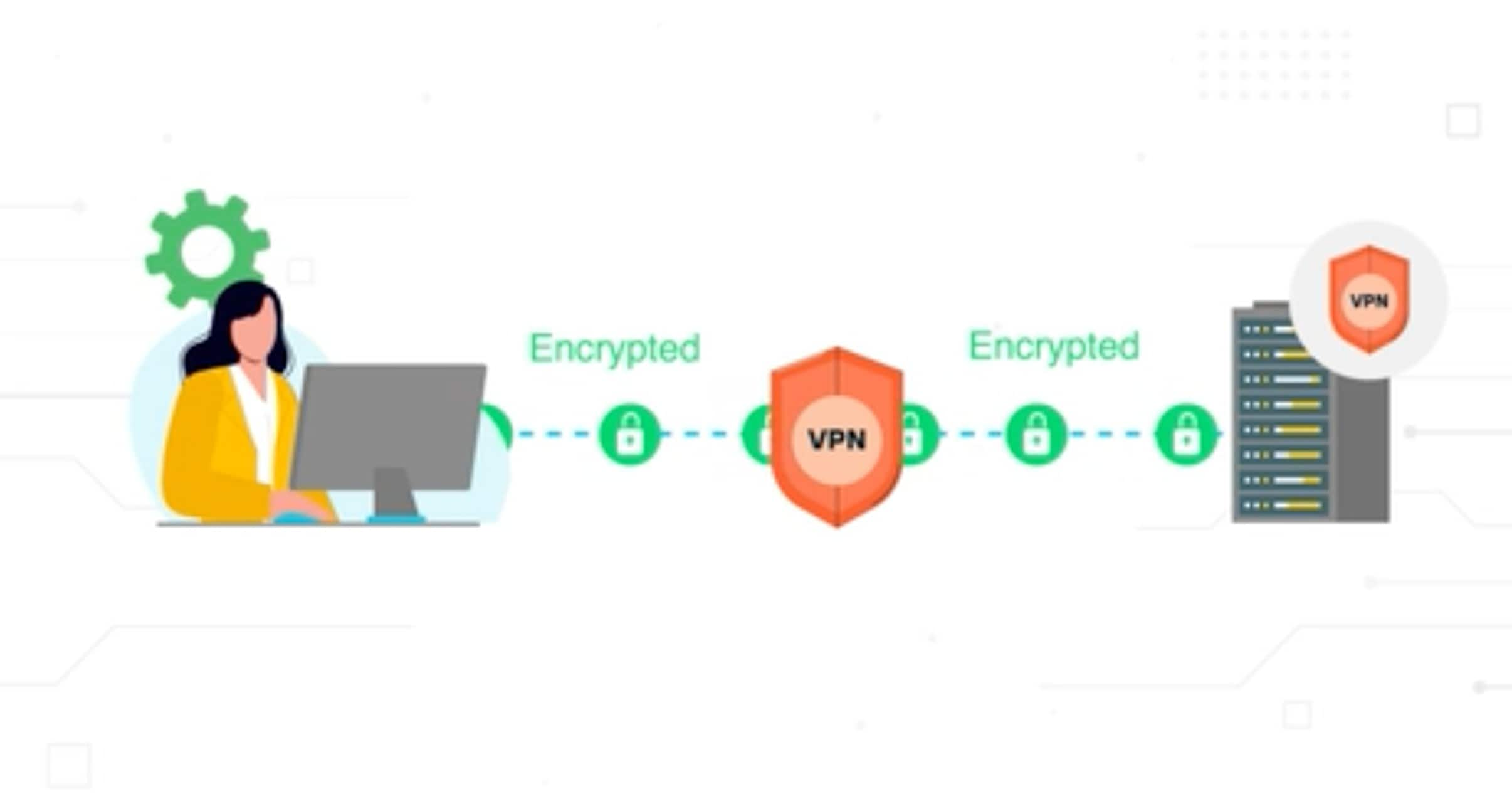
A double VPN is a configuration of a VPN setup that routes internet traffic through two distinct VPN servers, applying encryption at each stage.
The system doubles the encryption on the user's data, increasing the security of internet activities. As the data travels, each server re-encrypts the information before passing it on, which makes it significantly harder to intercept or decipher. Unlike a standard VPN, a double VPN provides an additional layer of privacy by hiding the user's IP address behind two separate servers.
What Does a Double VPN Do?
A double VPN is a feature that provides a fortified layer of security to online activity. It achieves this by encrypting connections twice and routing them through two distinct VPN servers. Each server acts as a discrete waypoint, ensuring that the data's origin remains obfuscated and the content inaccessible during transit.
The process is designed to safeguard against potential vulnerabilities in a single-server setup, making it considerably more challenging for unauthorized entities to track or intercept the data. This method is particularly useful when the integrity of the data transmission is critical and must be preserved against advanced threats. However, VPN providers don’t commonly offer a double VPN feature.
How Does a Double VPN Work?
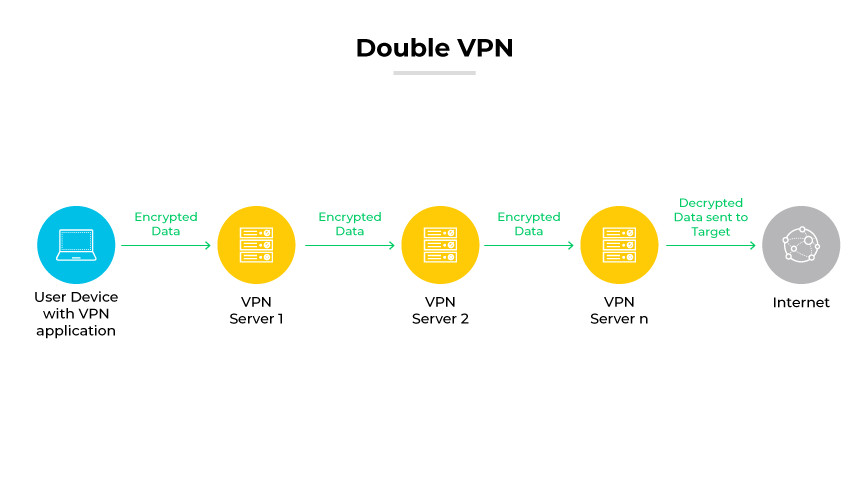
A double VPN channels internet traffic through two separate servers, encrypting data twice. Dual encryption ensures that the user's original IP address and data content are concealed even if one server is compromised.
Initially, the VPN application encrypts the user’s traffic and directs it to the first server. This server applies a second encryption layer and masks the user's IP address. The double-encrypted data is sent to a second server, which decrypts it before reaching the final destination.
Double VPN structures are especially beneficial in environments where information security and anonymity are paramount. However, it should be noted that this increased security measure may result in slower connection speeds due to the complex encryption and decryption process.
Double VPN Benefits
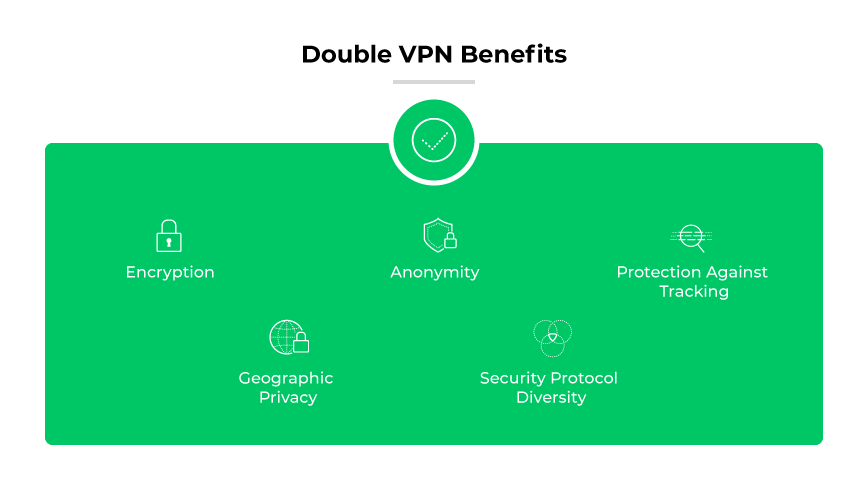
Enhanced Encryption
Traffic passes through two encryption phases when using a double VPN. Even if one encryption layer is compromised, the second layer maintains the security of the data.
Improved Anonymity
With traffic rerouted through two servers, the second server only recognizes the IP address of the first server, not the user's original IP address. This process significantly obscures the digital footprint of the user.
Protection Against Tracking
Internet service providers (ISPs) can determine when a VPN is in use but cannot discern the final destination of the user's traffic, adding a layer of obscurity against external monitoring.
Geographic Privacy
Double VPN servers are often strategically located in different countries. This separation further disguises the user's true location by adding multiple geographic hops in the datapath.
Security Protocol Diversity
Enterprises can use a mix of different security protocols across the two VPN servers, such as TCP and UDP. This diversification can enhance security against certain types of network attacks.
Double VPN Disadvantages
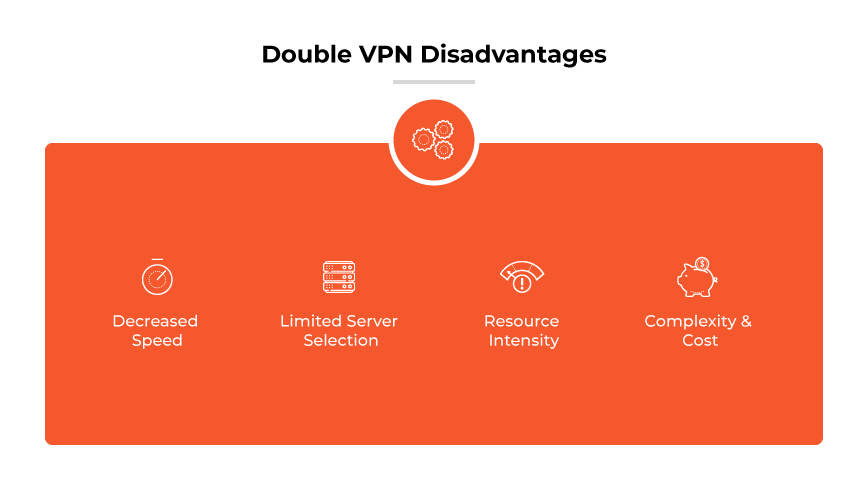
Decreased Speed
The implementation of a double VPN adds a layer of complexity to data transmission, which commonly results in a slower internet connection. Each data packet is encrypted twice and must traverse two separate server points, increasing the time taken for data to reach its destination.
This can particularly impact activities requiring high-speed internet, like downloading large files or streaming video content in high definition.
Limited Server Selection
With a double VPN, the data passes through two VPN servers instead of one. This can significantly limit the selection of servers available to the user.
Not all servers are configured to support double VPN connections, which can restrict users to a smaller subset of servers. This can potentially lead to congestion and further reduce speed. This limitation can also restrict access to content that may only be available through servers in specific geographic locations.
Resource Intensity
A double VPN configuration demands additional processing power because the data is encrypted and decrypted an extra time. This additional load can strain system resources, leading to reduced performance, particularly on devices with limited processing capabilities.
Complexity and Cost
The complexity of a double VPN setup inherently brings about additional costs. Services that offer such configurations usually do so at a premium, given the increased infrastructure and maintenance required. The additional expense may be unnecessary in a business context given that so many other advanced enterprise VPN solutions are available on the market today.
Is a Double VPN the Same as VPN Chains or Multihop VPNs?
Double VPNs and VPN chains, also known as multihop VPNs, share a common goal: to enhance online privacy and security by routing internet traffic through multiple servers. However, they are not identical in structure or implementation.
A double VPN sends internet traffic through two VPN servers. This means that the user's data is encrypted twice before reaching the intended destination. This process is typically managed within a single VPN provider's framework, which often allows for simpler setup through the provider's application.
VPN chains, in contrast, can extend beyond two hops and may use multiple VPN providers. However, it may not be possible to launch different VPN clients simultaneously. VPN chaining often requires manual configuration and may demand a deeper understanding of network settings.
Using servers from different providers means that the user must manage multiple subscriptions and ensure the services are compatible. This can complicate the setup process. Furthermore, as the chain lengthens, the cumulative effect on internet speed becomes more pronounced, often resulting in a slower connection.
From an enterprise perspective, the use of a double VPN or multihop VPN should be considered in the context of the organization's specific security requirements and the capabilities of their network infrastructure. Decisions should be based.
Is a Double VPN Necessary?
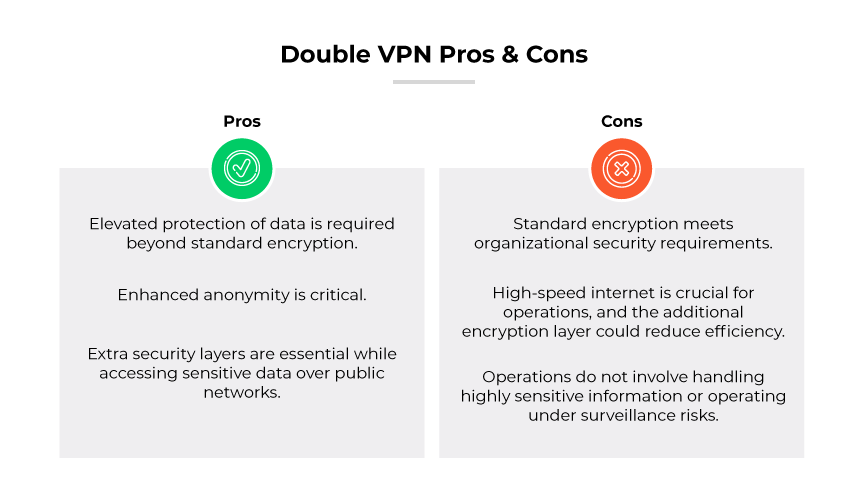
In enterprise environments, the use of double VPNs is relatively rare compared to their usage in individual consumer contexts. The necessity of a double VPN depends on specific security needs. It is not mandatory for most enterprise environments but offers heightened security where sensitive data is handled.