Value Proposition
Working together, the integrated solution provide by Palo Alto Networks and Aruba Networks maps user and device information to network security policies, enabling IT to govern what a user can access with a particular device and authorized application.

Why Aruba?
Palo Alto Networks and Aruba Networks have been working together to deliver upon a concept that we call Adaptive Trust. Instead of recreating the past mistakes and outdated assumptions in security, we sought to build a solution built upon 3 concepts.
- You need to identify users – from the very point they’re on the network, you need to know who they are. That’s why identity is important, and it’s core to what Aruba does to secure the access layer.
- You have to have context such as knowing who the users is and what the device is in order to understand what they should be allowed to access. In other words, context is important and should be coordinated and preserved to enforce granular policy
- You need protection, to make sure that out of the applications that you do permit, you make the traffic safe.
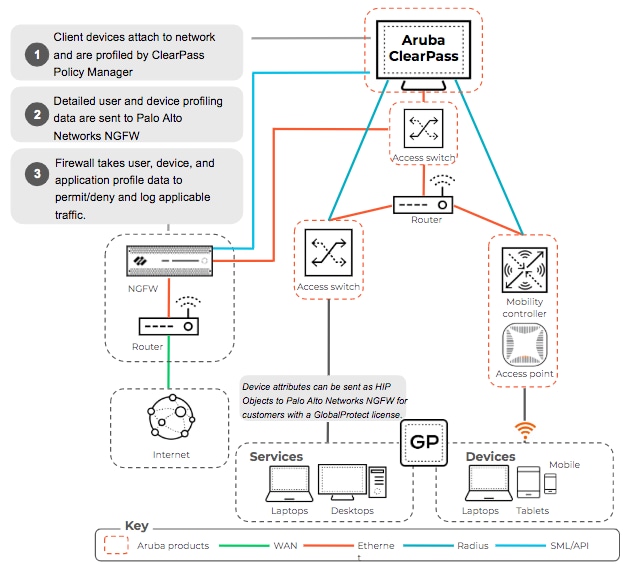
Bringing together the technology from Aruba Networks and Palo Alto Networks together, we deliver upon this very concept for adaptive trust.
PARTNER TOPICS
Solution Brief
Customer Case Study
- Maine Township HSD 207 – Wireless Network Security
- CSU: Common Network Initiative – Security Infrastructure Refresh
Solution Overview
For more information or question about this partnership, please contact strategicpartners@paloaltonetworks.com.
