There is a lot of information on the web about preventing and recovering from CryptoWall or ransomware attacks in enterprise environments, but most don’t answer this basic question:
“How do I determine which CryptoWall-infected PC encrypted all the documents in one of my network-shared drives? I don’t have audit logging enabled on my file server.”
Although many organizations are working on migrating their document storage to the cloud, most still rely upon individual Microsoft network shares as a document repository for each business department. For example, the financial controller’s office may have a network share dedicated to that department, the HR department has a different one, etc. When a user’s PC in one of these departments becomes infected by CryptoWall, the ransomware iterates through all files on all folders on all local and mapped network drives and encrypts certain file types that the user has permissions to modify.
As a security lead for a hospital network, I created the following CryptoWall response plan specifically to deal with impacted department shared drives:
- Identify the user account that modified (encrypted) the shared drive files.
- Identify the infected PC and restrict network access.
- Create inventory of all network share directories impacted.
- Restore impacted directories from backup.
Identifying the user account in Step 1 can be challenging if you don’t know where to look. The best way to identify the user account used to encrypt the files is to examine the “owner” attribute of one of the instruction files created by the ransomware. Here are the steps to identify the owner:
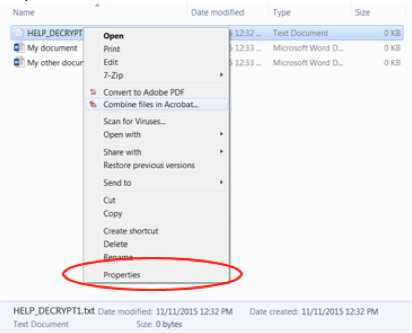
1. Right click on the instructions file (i.e., HELP_DECRYPT.txt) created by the ransomware on the network share, and select Properties.
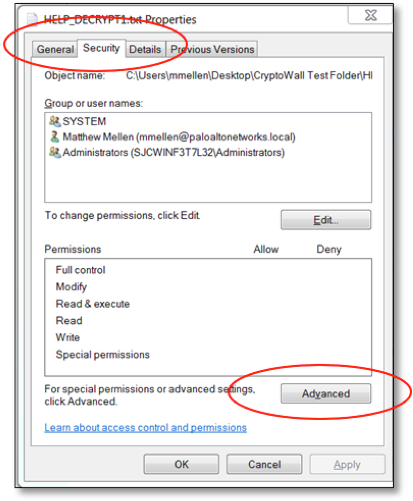
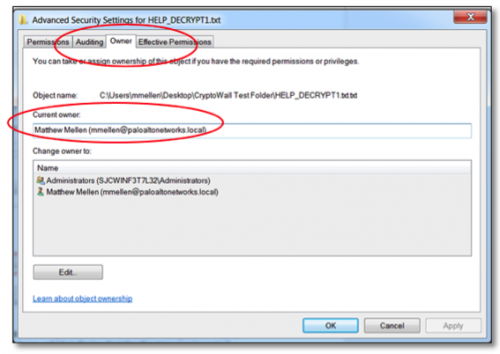
2. Select the Security tab --> Advanced --> Owner, and view the Current Owner attribute. The Current Owner attribute is likely the username used to encrypt the files in the directory.
Once you know the username used to encrypt the files, you can reset the user’s password, attempt to contact the person, and identify the user’s assigned PC in order to block it on the network. Once the PC is blocked, the server team can then identify the impacted directories on the network share (Tip: Use PowerScript to identify directories containing the instructions file). Finally, the Backup team can restore the files in all of the identified directories.
For more information on the latest CryptoWall threat, take a look at a detailed analysis of CryptoWall v3 authored by the Cyber Threat Alliance, cofounded by Palo Alto Networks.