This post is also available in: 日本語 (Japanese)
Cloud native supply chains have been highly tuned to meet the demands of DevOps speed and innovation. They are typically made up of containers and infrastructure as code (IaC) with open source dependencies to speed up innovation and CI/CD pipelines to automate the delivery of new features. With our latest release, Prisma Cloud now provides an automatic inventory and visualization of your cloud native supply chain. This provides quick visibility into the software bill of materials, connections between components and code pipelines that make up your cloud native applications.
Software supply chains have direct access to proprietary code and are just a few pivots away from production environments and sensitive data, and thus are increasingly becoming the target of attacks. Gartner predicted that “by 2025, 45% of organizations worldwide will have experienced attacks on their software supply chains, a three-fold increase from 2021.” Organizations need to prepare for these attacks from every angle.
Risks to Software Supply Chains
Supply chains are made up of two primary elements – the various application and infrastructure components that make up cloud native applications and the pipeline that builds and delivers these components into a working application environment. Both of these pieces are subject to threats from bad actors attempting to tamper code to install cryptominers or exfiltrate sensitive data.
In Unit 42’s recent Cloud Threat Report, the team conducted a red team exercise against a software supply chain and a study of the posture of open source code. They found that access to overly permissive credentials opened the door for lateral movement and continuous integration (CI) pipeline poisoning. This highlights how easy it can be for attackers to gain access to a pipeline to inject malicious code.
As part of the same research, a scan of open source components across repositories and registries found that a shocking 64% of Terraform modules contained at least one high or critical misconfiguration, and 91% of container images contain one high or critical severity vulnerability. If any of these open source components were included in an application, they would increase the attack surface for bad actors.
Principles of Supply Chain Security
Protecting against these attacks requires a full stack, full lifecycle approach to securing pipelines. Prisma Cloud already provides comprehensive security for cloud native supply chains. Now, Prisma Cloud inventories and visualizes the pieces of your application supply chain.
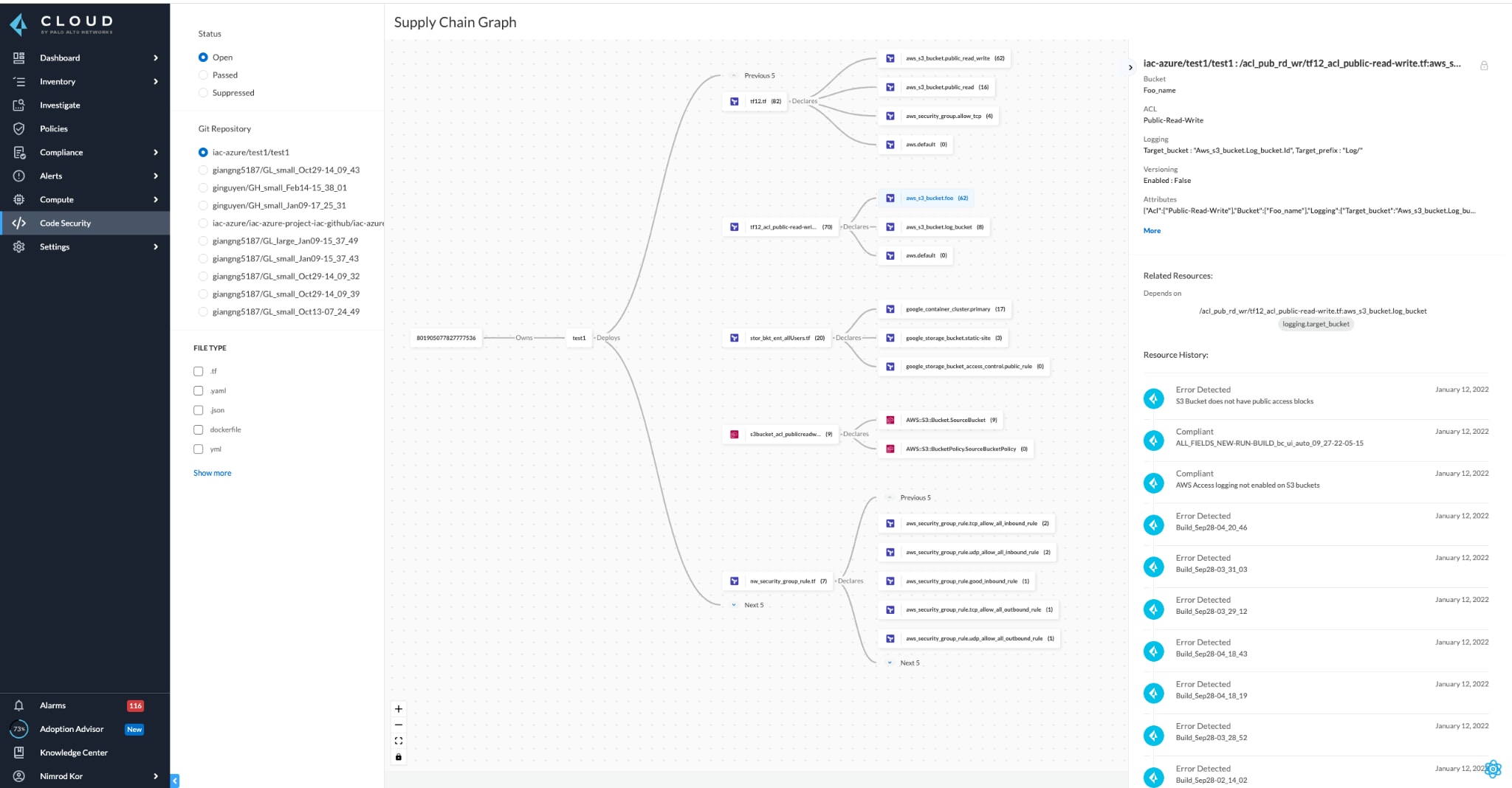
With this visibility, DevOps and security teams alike will have a better understanding of all of the components of their applications and how to improve their posture.
For each component of this software supply chain in the new visualization, Prisma Cloud provides protection from code to cloud.
Code
A secure supply chain begins with secure open source components. Open source components make up a majority of modern applications, however, most contain some vulnerability. Prisma Cloud already identifies vulnerabilities and misconfigurations in repository packages and IaC files locally through our integrated development environment (IDE) integrations and Command Line Interface (CLI) tools powered by Bridgecrew. For many security issues identified, Prisma Cloud provides fix suggestions to empower developers to secure their own code.
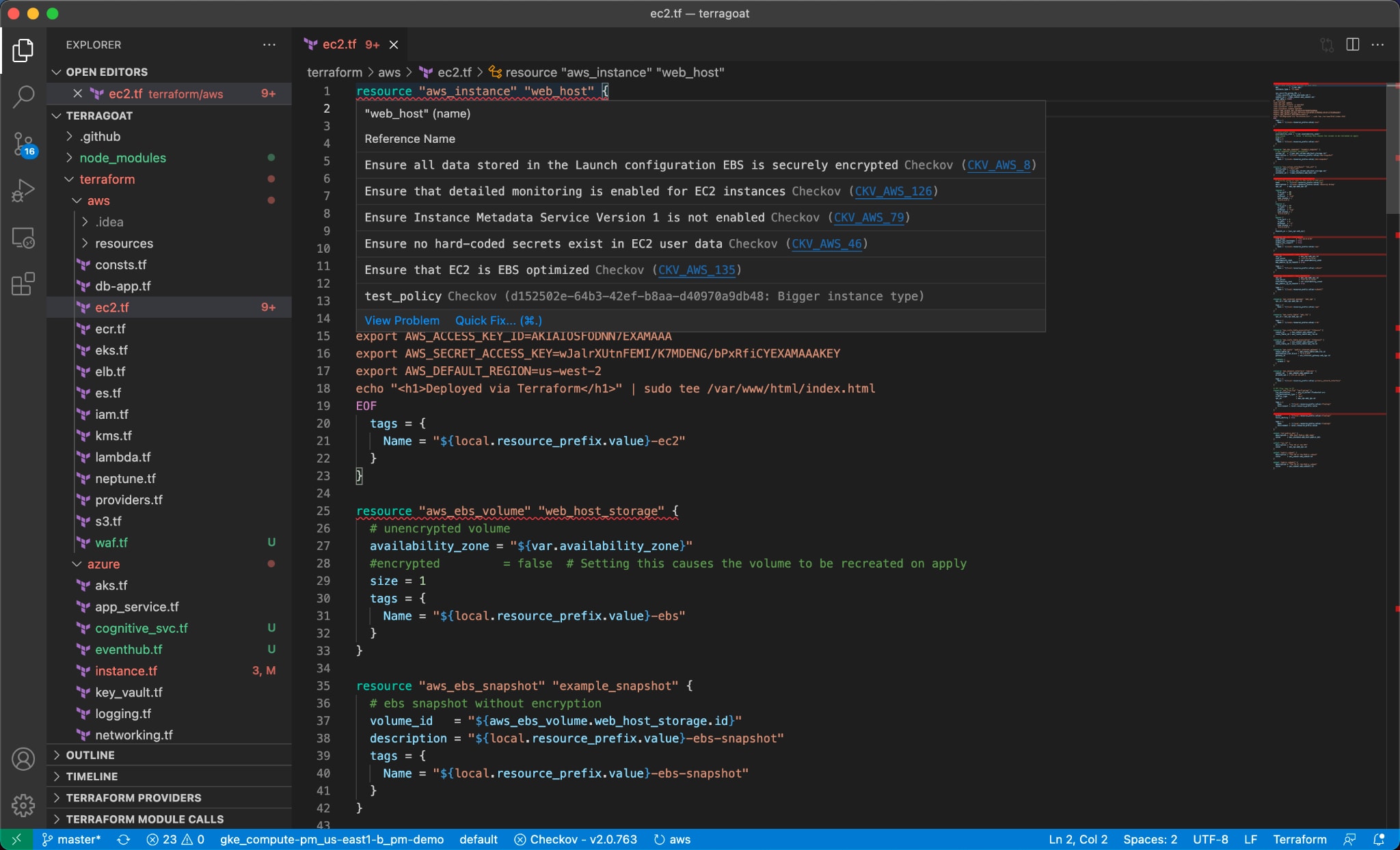
Before pulling any image out of a public registry that may contain malware, Prisma Cloud includes container sandbox technology to vet images before use. These tools in combination help ensure that the components that make up an application are as secure as possible before leaving the developer’s desktop.
Additionally, it’s all too easy to include a secret like an API key in your development environment and mistakenly commit that to a repository, exposing your organization to attack. Prisma Cloud includes checks to identify secrets to prevent exposure.
Build
At this stage, software supply chain security expands from beyond components to include the pipeline. Prisma Cloud’s integrations with version control systems (VCS) and CI/CD pipelines include checks and guardrails to ensure that only secure code is integrated into repositories, and secure container images make it into trusted registries.
Additionally, Prisma Cloud checks the integrity of the VCS and CI/CD pipelines themselves and ensures that correct branch protections are in place to prevent code tampering attacks. Pipelines given permission to deploy infrastructure for testing and automation can be limited to the minimum permissions required to accomplish their tasks.
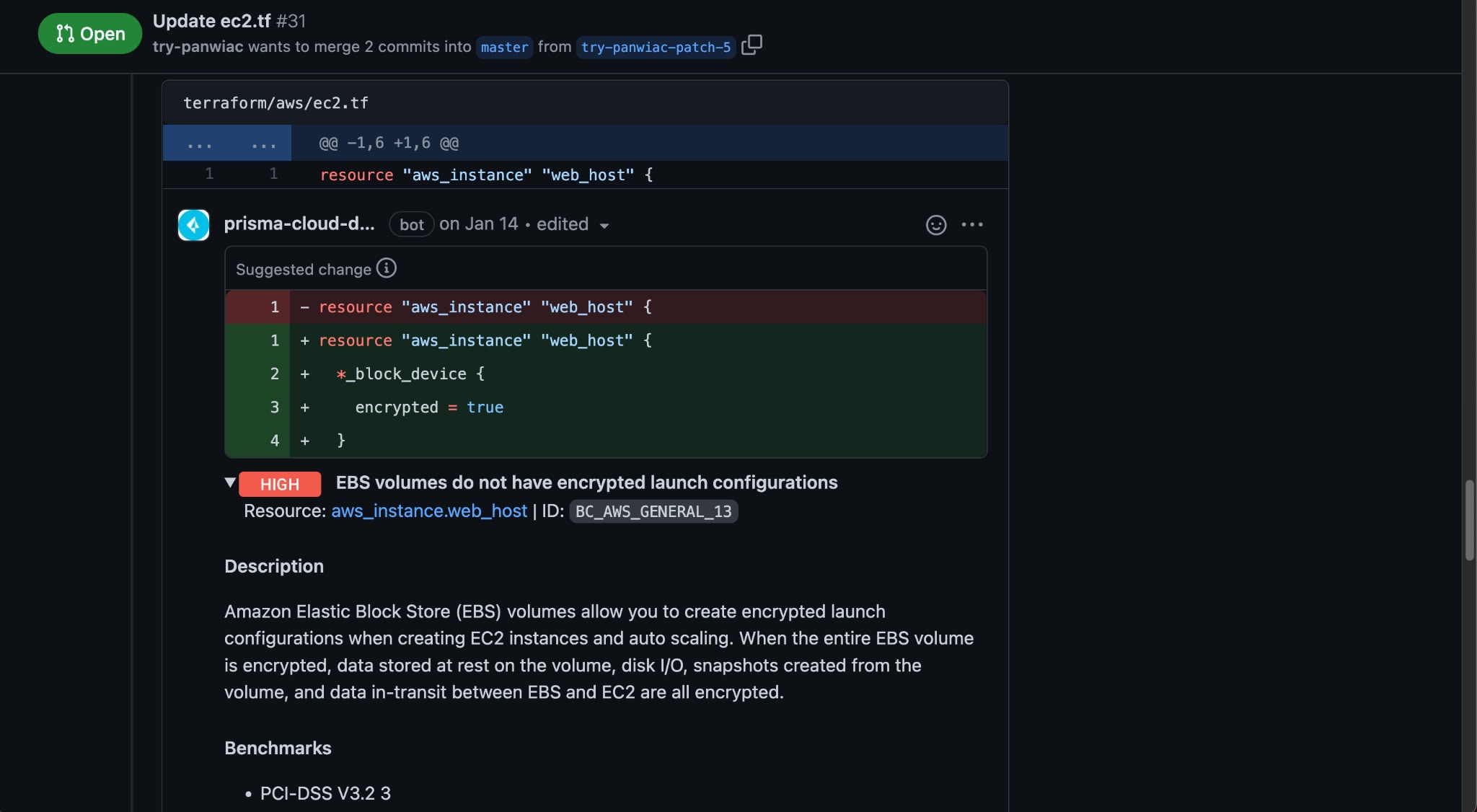
Deploy
At the deployment stage, a secure supply chain will have a final gate for admission into a running environment. Here Prisma Cloud’s admission controller and integration with cloud native technologies like Open Policy Agent (OPA) can be the final line of defense to prevent insecure configurations. Also, Prisma Cloud can enforce that only trusted images are pulled from registries into production. This prevents image poisoning attacks.
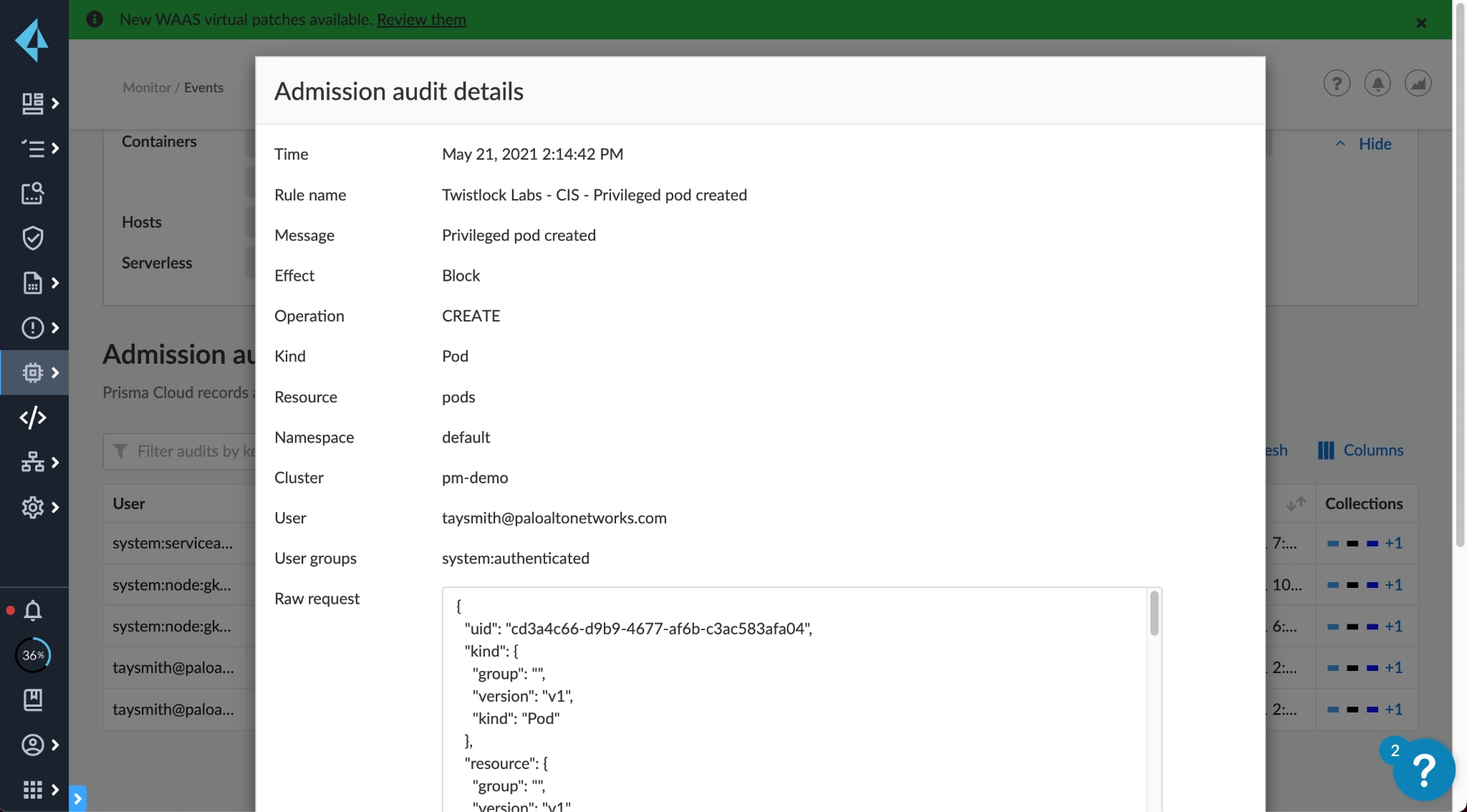
Run
At the run stage, all of those components should continuously be monitored for newfound misconfigurations and vulnerabilities. Prisma Cloud provides a fast feedback loop to quickly provide vulnerability discoveries and remediation guidance to go back to the code and patch dependencies fast. Additionally, even with the most proactive approach to security, you still need runtime security to identify zero-days and threats.
One Platform for Supply Chain Security
Prisma Cloud’s latest enhancements bring overall visibility into the posture of your software supply chain. This, in combination with Prisma Cloud’s existing compliance and vulnerability checks, ensure that the components that make up your applications and the pipeline that assembles them are secure.
If you want to begin securing your software supply chain from end-to-end, request a trial of Prisma Cloud. We also welcome you to join us at the upcoming Code to Cloud Summit to hear about our approach to supply chain security from Guy Eisenkot, senior director, product management, Palo Alto Networks.