The market has largely assimilated cloud security posture management (CSPM) tools for just three security functions:
- Visibility into runtime
- Configuration management
- Managing compliance
While these are important for maintaining adequate security hygiene and reducing risk in cloud environments (along with minimizing runtime configuration errors through shift left strategies), they only represent one part of an effective strategy.
I'll explain why threat detection is an essential addition to that strategy and show how Prisma Cloud is the only CSPM tool that can address it.
What Your Cloud Security Posture Management Tool is Missing
According to the IBM Data Breach Report 2020, it takes organizations, on average, 280 days to discover and contain a breach. Considering how essential the cloud has become for businesses, and how quickly it evolves, 280 days is more than enough time to cause significant damage.
Focusing on maintaining hygiene through compliance and configuration management, without monitoring for new threats, leaves organizations completely exposed. It's like spending time making sure the doors are locked without considering putting up security cameras. After all, there is no such thing as “perfect” protection, and a malicious actor just needs one loophole to exploit.
Given the added complexities of the cloud (accelerated development pace, distributed environments, diversity in microservices, constantly changing network activities) proactive threat detection must be a component of a comprehensive CSPM strategy. As more and more users and workloads are added to cloud environments, continuously monitoring behavior for suspicious activities is critical. This means a combination of static rule and machine-learning-based security policies; as well as user activity monitoring.
4 Components of Threat Detection in CSPM
Let’s take a look at four ways Prisma Cloud quickly detects risks and prevents incidents across cloud environments.
1. High Fidelity Threat Intelligence
There are numerous threat detection solutions on the market today. But a tool's ability to effectively identify and surface risks is only as good as its data source. For many solutions, this means a disparate assortment of cloud service provider (CSP) logs and open-source feeds.
Prisma Cloud delivers high-fidelity threat intelligence sourced from AutoFocus – a massive repository of network, endpoint and cloud intelligence data – that helps detect cryptomining, ransomware, Linux malware, backdoor malware, hacking tools and more. In addition, our own curation of 30-plus upstream data sources across commercial, open-source and proprietary feeds helps to provide accurate and granular risk context across multi-cloud environments.
2. Network Threat Detection
In fall 2020, the Unit 42 cloud threat research team found that cryptojacking affects at least 23% of organizations globally that maintain cloud infrastructure, a slight improvement over 28% of organizations in 2019. This shows the challenges organizations face in effectively detecting threats in their cloud environments.
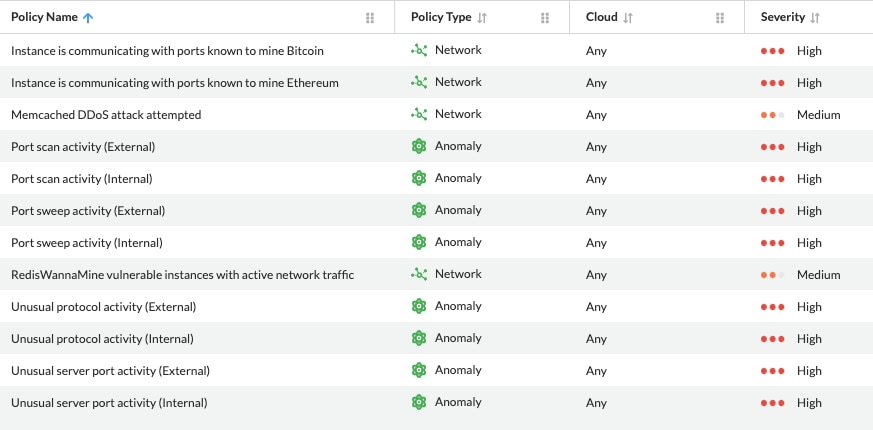
To address this, Prisma Cloud ships with hundreds of out-of-the-box security policies purpose-built to address threat vectors targeting public cloud environments, including detection of cloud-specific threats like crpytojacking activities. Organizations can then customize these policies as needed.
3. Network Anomaly Monitoring
While traditional rule or signature-based policies can prevent known bad behaviors from continuing, they can't protect against zero-day attacks and other types of advanced, persistent threats (APTs).
Prisma Cloud augments its vast library of security policies with machine learning-based and threat intelligence-sourced policies to provide comprehensive analysis into network behaviors such as traffic volume, bandwidth use and protocol use. This helps simplify in-depth investigations into suspicious network activities across Amazon Web Services (AWS), Microsoft Azure and Google Cloud.
For example, these policies provide the ability to:
- Detect unusual server port activity or unusual protocol activity from a client within or outside your cloud environment to a server host within or outside your network, using a server port or an IP protocol that is not typical to your network traffic flows.
- Detect port scan or port sweep activities that probe a server or host for open ports.
- Identify hosts within your cloud environment that may be compromised and sending out spam.
4. User Entity Behavior Analytics
The final piece of an effective threat detection strategy should focus on user behavior. Users who access cloud environments can pose a significant threat if not continuously monitored for unusual activities that could signal the possibility of credential or account compromise.
Prisma Cloud has long had a robust UEBA strategy that continuously monitors each user's activities, employing machine learning to identify what’s normal, and then alerting on any behaviors that deviate from that baseline.
Similar to the network anomaly policies, fine-grained controls enable users to train the machine learning model to minimize false positives and negatives, as well as customize alert disposition. Users can also specify policy-specific trusted lists to avoid getting anomaly alerts from resources that are known to be used for things like penetration testing.
Bringing It All Together for Comprehensive CSPM
The ability to accurately detect and quickly respond to threats requires a combination of continuous monitoring of network activities and user behavior across clouds, along with advanced threat detection techniques using machine learning and threat intelligence. Prisma Cloud enhances these capabilities by correlating additional resource visibility data to provide needed context with every alert.
Together, this dramatically enhances security teams’ ability to maintain cloud security posture and identify unusual network behaviors that could signal the presence of a threat before it’s exploited. Prisma Cloud users have seen as much as a 75% reduction in configuration errors and an 83% reduction in alert volume.
If your current strategy and toolset for CSPM is only focused on visibility, configurations and compliance, you're leaving your cloud environments exposed to potential vulnerabilities.