This post is also available in: 日本語 (Japanese)
It’s like the snap of a familiar set of fingers wearing the gauntlet embedded with infinity stones. One moment, your cloud environment is untouched, containers, apps and data all right where they should be. The next, someone else is in control of what still exists and how it’s going to be used.
While it might sound dramatic to compare threat actors infiltrating your cloud environment to Thanos from the Marvel Cinematic Universe snapping his fingers to wipe out half of the universe, what both scenarios have in common is someone else deciding your fate. In a business setting, just like in the Marvel movies, this can have ripple-effect consequences that can be threatening to your organization and the rest of the world. No matter how small or large an organization’s cloud footprint may be, the more that attackers realize what’s possible in a cloud environment, the bolder they become – and the more dangerous to our interconnected world.
Now, all hope is not lost. It’s not as if we just let Thanos live in the Garden peacefully (in other words, walking away without consequences). While we can’t rewind time by taking the infinity stones for ourselves, we can change our approach to cloud security with a prevention-first security strategy.
First Things First: Learn Who Targets Cloud Native Infrastructure
Malicious actors who threaten your organization’s cybersecurity have historically done so by compromising systems and devices within an organization’s physical location. With the rise of hosting infrastructure within cloud service platforms (CSPs) and cloud native container platforms, attackers are modifying their tactics, techniques and procedures (TTPs) in order to compromise cloud infrastructure.
As a result, a new classification of threat actors has emerged, labeled by Unit 42 as “cloud threat actors.” Unit 42 defines a cloud threat actor as an individual or group posing a threat to organizations through directed and sustained access to their cloud platform resources, services or embedded metadata.
While cloud threat actors follow the same overall operational workflow as traditional threat actors, cloud threat actors have evolved their TTPs to a level of sophistication that enables them to potentially modify, create or delete cloud environment resources. Let’s dive into some of the details of who these cloud threat actors are and what they have in common with each other.
Unit 42’s Industry-First Cloud Threat Actor Index
To assist in defending against the growing threat of cloud threat actors, Unit 42 researchers created an industry-first Cloud Threat Actor Index, which charts the specific operations performed by threat groups who target cloud infrastructure.
The data found in the Cloud Threat Actor Index follows the MITRE ATT&CK® cloud and container matrices, giving security professionals a common framework around which to communicate and discuss the TTPs employed by these threat actors. The Cloud Threat Actor Index also employs the Unit 42 ATOM service to provide security professionals with all of the known indicators of compromise (IoCs) used by the cloud threat actors packaged within the industry standard STIX/TAXII format. This format allows for easy integration with cloud security tools and platforms.
The groups highlighted in the Cloud Threat Actor Index all directly target cloud service platforms. Going a step further, once they bypass traditional security defenses, they are able to gain an initial foothold within the compromised organization’s cloud infrastructure.
In the following section, we will explore one of the top five cloud threat actors targeting the cloud (this cloud threat actor can also be found in the index). We will then follow that example by explaining how these groups could be prevented from being able to execute at least two of their TTPs.
WatchDog: The Stealer
A description of WatchDog and their TTPs from the Cloud Threat Actor Index can be found below:
“WatchDog is a cloud-focused threat group that has a history of cryptojacking operations as well as cloud service platform credential scraping. They were first known to operate on Jan. 27, 2019. They use a variety of custom-built Go Scripts as well as repurposed cryptojacking scripts from other groups, including TeamTNT. They are currently considered to be an opportunistic threat group that targets exposed cloud instances and applications.”
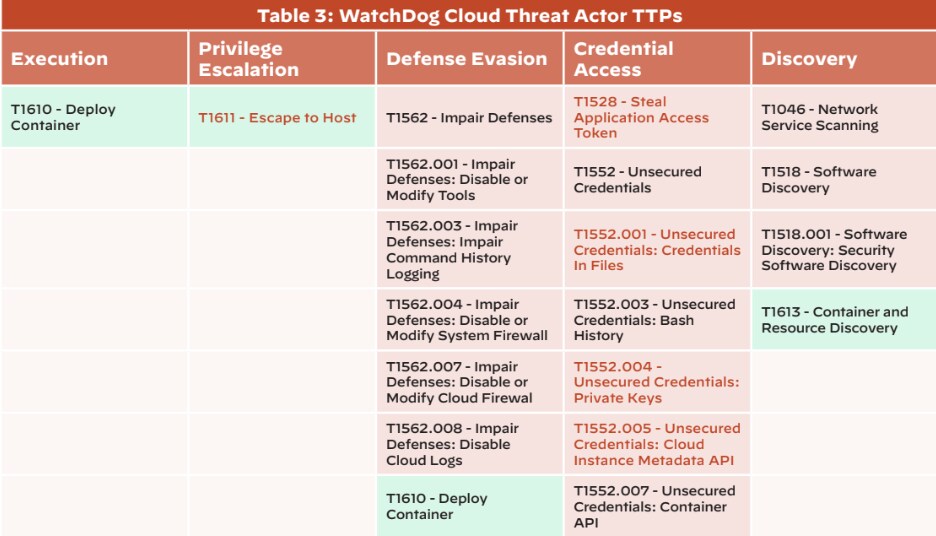
In the chart above, the red background denotes TTPs specific to cloud platforms, whereas the green background denotes TTPs that are container-platform specific. TTPs in red font denote operations that can lead to the wider compromise of cloud infrastructure.
As shown in the chart, there are several TTPs WatchDog employs that are container-specific and even allow for the possibility of container escape. Interestingly, these techniques can occur across any stage of the operational workflow – from execution all the way through to discovery.
Container Security: The Iron Man to a Modern Thanos
Dr. Strange only saw one possible outcome to defeating Thanos once and for all, which involved Iron Man sacrificing his own life; similarly we see one way (and only one) to ensure that cloud threat actors are unable to perform container-specific and container escape/resource-specific TTPs. And that one way would be through container security. Luckily, proper container security can be achieved through best practices – no heroes need sacrifice their lives.
By ensuring that your organization has purpose-built security that addresses vulnerability management, compliance, runtime protection and network security requirements for containerized applications, you are putting into place a prevention strategy that keeps you protected all the way from build to runtime and everything in between.
If you’re curious what to look for, this informational article provides insight into what a full lifecycle container security solution should have.
Why You Need a Cloud Native Application Protection Platform (Cue the Avengers Theme Song)
So Dr. Strange and Iron Man have helped make sure your containers can’t be targeted by Thanos, but what about all those other TTPs just waiting to be put to malicious use to infiltrate your cloud infrastructure some other way? That’s where the rest of the Avengers come in, and we all know that the team together is more powerful than any hero working alone.
When all the Marvel heroes work together: from Dr. Strange and Iron Man, to Captain America and Spider Man, to Black Widow and Hawkeye and the rest of the Avengers, Thanos doesn’t stand a chance. In the same way, when your organization deploys full lifecycle cloud security, neither does WatchDog or any other cloud threat actor.
For that reason, it is essential to assemble your own arsenal of defenses against these cloud threat actor groups, who are looking for any way to infiltrate your organization and take control of it. The best way to do that would be to employ a cloud native application protection platform (CNAPP).
With a CNAPP, you have the equivalent of every infinity stone and Avenger on your side: cloud code security, cloud security posture management (CSPM), cloud workload protection (CWPP), cloud network security (CNS) and cloud identity security. Sure, all of these capabilities are powerful on their own, but when your organization brings them together, cloud threat actors will be rendered powerless.
Get Your Copy of Unit 42’s Cloud Threat Actor Index
In Unit 42’s latest Cloud Threat Report, “IAM The First Line of Defense,” cloud threat researchers provide five cloud threat actor TTPs charts. They also dive into how proper identity and access management can be your first line of defense in protecting against being targeted by cloud threat actors. Finally, Unit 42 researchers provide in-depth recommendations for getting started on protecting your organization today, including how to deploy CNAPP suite integration, how to harden IAM permissions and how to increase security automation.
Download the Unit 42 Cloud Threat Report, Volume 6, now and learn how you can get started with implementing a Cloud Native Application Protection Platform that combines key defenses like a team of heroes and keeps your organization secure from code to cloud.
P.S. Want to learn about the research and recommendations directly from the experts? Watch our LinkedIn Live event on-demand now!