We are excited to announce the availability of the Multi-VPC Cloud NGFW for AWS resource, the managed firewall that provides best-in class Palo Alto Networks security with AWS cloud native ease of use. By introducing this exciting feature, we’re introducing the ability to massively scale security by allowing you to share the same Cloud NGFW resource across multiple virtual private clouds (VPCs) in your AWS accounts.
Cloud NGFW for AWS Keeps Expanding to Meet Your Needs
First, some context: Over the years, Palo Alto Networks customers have used VM-Series Next-Generation Virtual Firewalls to protect their VPCs, which are virtual networks closely resembling traditional networks in data centers. These virtual firewalls provide best-in-class security with Layer 7 application controls, real-time signatures and URL categories updates, and ML-powered threat prevention. Our customers have always asked us whether we can make our best-in-class security as easy to consume as other AWS-native services. They were looking for a cloud-native experience for network security and wanted to avoid managing the deployment and security infrastructure and integrating it deeply with the AWS ecosystem.
We listened and launched Cloud NGFW for AWS back in March 2022. Cloud NGFW for AWS is a Next-Generation Firewall (NGFW) service on the AWS platform that is managed by Palo Alto Networks. It handles the delivery of next-generation security and its underlying infrastructure in a fully automated manner.
Since the inception of Cloud NGFW for AWS in March 2022, Palo Alto Networks has prioritized feedback from customers for driving product improvements. In response to customers like you who preferred AWS Marketplace procurement models to try and buy SaaS products, we enabled Cloud NGFW Free Trials and Cloud NGFW SaaS Contract Credits. We also expanded the service to 18 AWS regions.
Dedicated Cloud NGFW Resources
A Cloud NGFW resource provides NGFW capabilities for your VPC. This resource has built-in resiliency, scalability and lifecycle management. A NGFW resource spans multiple AWS availability zones, which are distinct locations within an AWS Region, engineered to be isolated from failures in other Availability Zones. They provide inexpensive, low-latency network connectivity to other Availability Zones in the same AWS Region.
Under the hood, a NGFW resource is a gateway load balancer-based VPC endpoint service. To use a NGFW resource, you create a dedicated subnet in your VPC for each desired AWS availability zone. You then create NGFW endpoints (also known as Gateway Load Balancer endpoints) on the subnets and update the VPC route tables to send traffic through these endpoints.
Until now, you created the Cloud NGFW resource and dedicated it to a single VPC in your AWS environment. You could use the Cloud NGFW resource by creating NGFW endpoints in that VPC. This dedicated resource would be sufficient if you use Cloud NGFW resources in a centralized deployment.
In the centralized architecture model, a dedicated security VPC provides a simplified and central approach to managing advanced access control, and threat inspection of traffic using an AWS Transit Gateway for all applications in the spoke VPCs. You would then configure route rules in the application VPCs and the transit gateway to redirect traffic to the security VPC for inspection. However, your deployment may require a hybrid architecture model, where the spoke VPCs can use the centralized VPC for east-west inspection. This model also allows distributing the inspection points (NGFW resources) on each application VPC that needs protection for its Internet Ingress/Egress traffic. However, you would incur hourly costs for each NGFW resource in your deployment, which you might want to avoid.
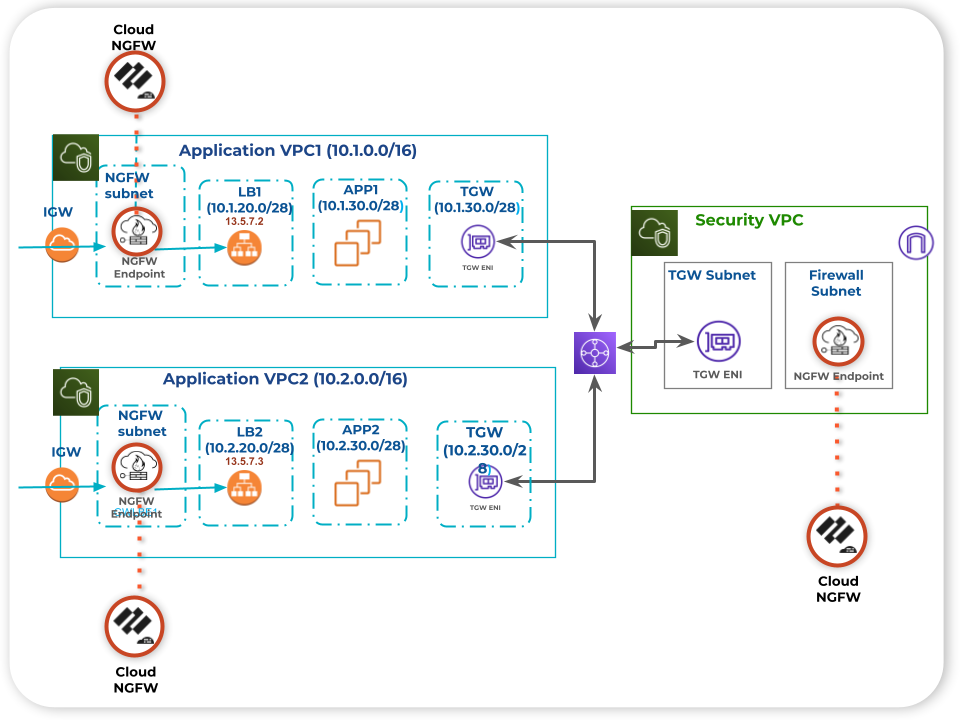
Multi-VPC NGFW Resources Change the Game
All that said, we heard your total cost of ownership (TCO) concerns about dedicating Cloud NGFW resources to VPCs and are excited to announce the general availability of the Multi-VPC NGFW resource. With this feature, you can create endpoints for an NGFW resource in different VPCs and route traffic to the NGFW resource for inspection.
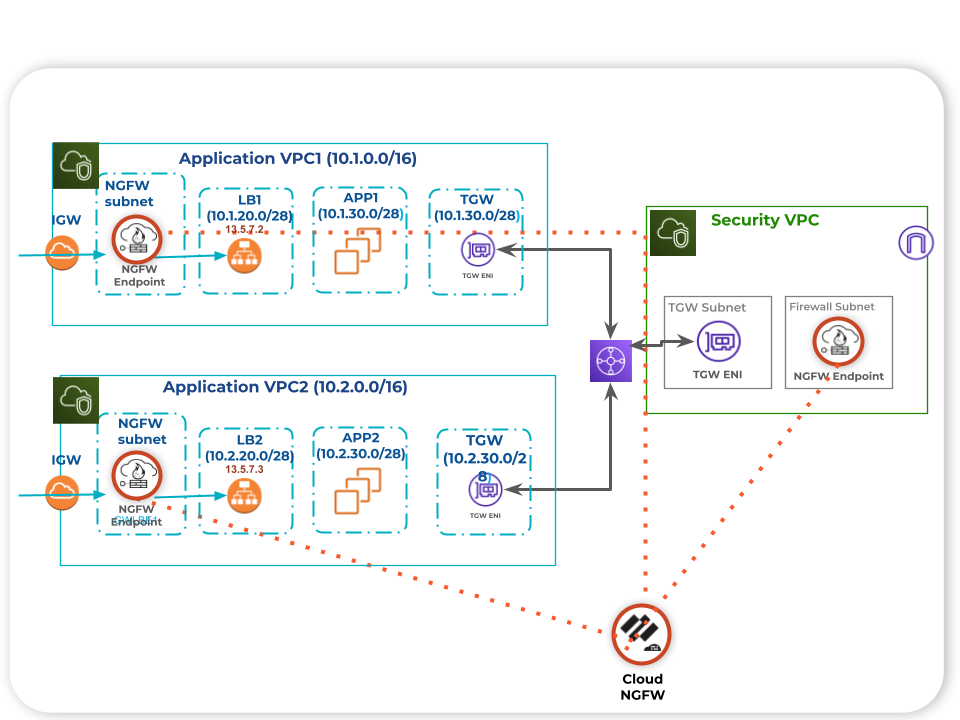
What’s more, you can have these VPCs in different AWS accounts with these significant operational benefits:
- Deployment flexibility: Now you can share Cloud NGFW resources across multiple VPCs in different AWS accounts.
- Scalable connectivity: Create up to 50 Cloud NGFW endpoints (also known as Gateway Load Balancer endpoints) across different VPCs and send traffic through these endpoints for NGFW inspection.
- Cost effectiveness: Reduce the number of NGFW resources needed to protect your AWS environment and consolidate your overall network security posture. There is no additional cost to share Cloud NGFW resources across multiple VPCs. You pay AWS directly for the Cloud NGFW endpoints (Gateway Load Balancer endpoints) that you would use to send traffic to the NGFW resource ($0.01/hr and $0.0035/GB).
This feature is now available in all Cloud NGFW for AWS supported AWS regions to help you realize these benefits in your AWS environment. You can also look at this brief demo video. To learn more, sign up for a 15-day free trial and visit the documentation and FAQ pages. As always, your feedback drives our feature roadmap and product development. Please contact us through your Palo Alto Networks support team if you have additional feedback or Cloud NGFW feature requests.