Address the gaps of last generation CSPM tools with more context and proactive security measures that prevent repeated mistakes.
When companies switch to the cloud, it’s natural for their security teams to adopt a cloud security posture management (CSPM) tool to gain visibility, detect misconfigurations and solve compliance challenges. After all, CSPM solutions provide valuable security insights, including those that normally require an agent or proxy. With cloud environments becoming more complex, organizations and cloud security vendors must adapt to stay ahead of modern threats.
This blog covers how CSPM technologies changed over time and what makes a modern approach stand out from traditional solutions.
The Evolution of CSPM Tools
Since the cybersecurity industry introduced CSPM, offerings have developed to better equip businesses with more comprehensive security. Here are some of the key milestones we’ve observed in the market and their challenges.
First Generation CSPM
The first generation of CSPM tools helped organizations address three security functions:
- What assets do I have across my public clouds?
- Where are my misconfigurations?
- What is my compliance posture?
During this era, CSPM provided essential visibility without requiring any agents, proxies or network scanners, making it easy to adopt. But security teams quickly realized a new challenge—they had an overwhelming number of misconfigurations and didn’t know which risks to prioritize.
Second Generation CSPM
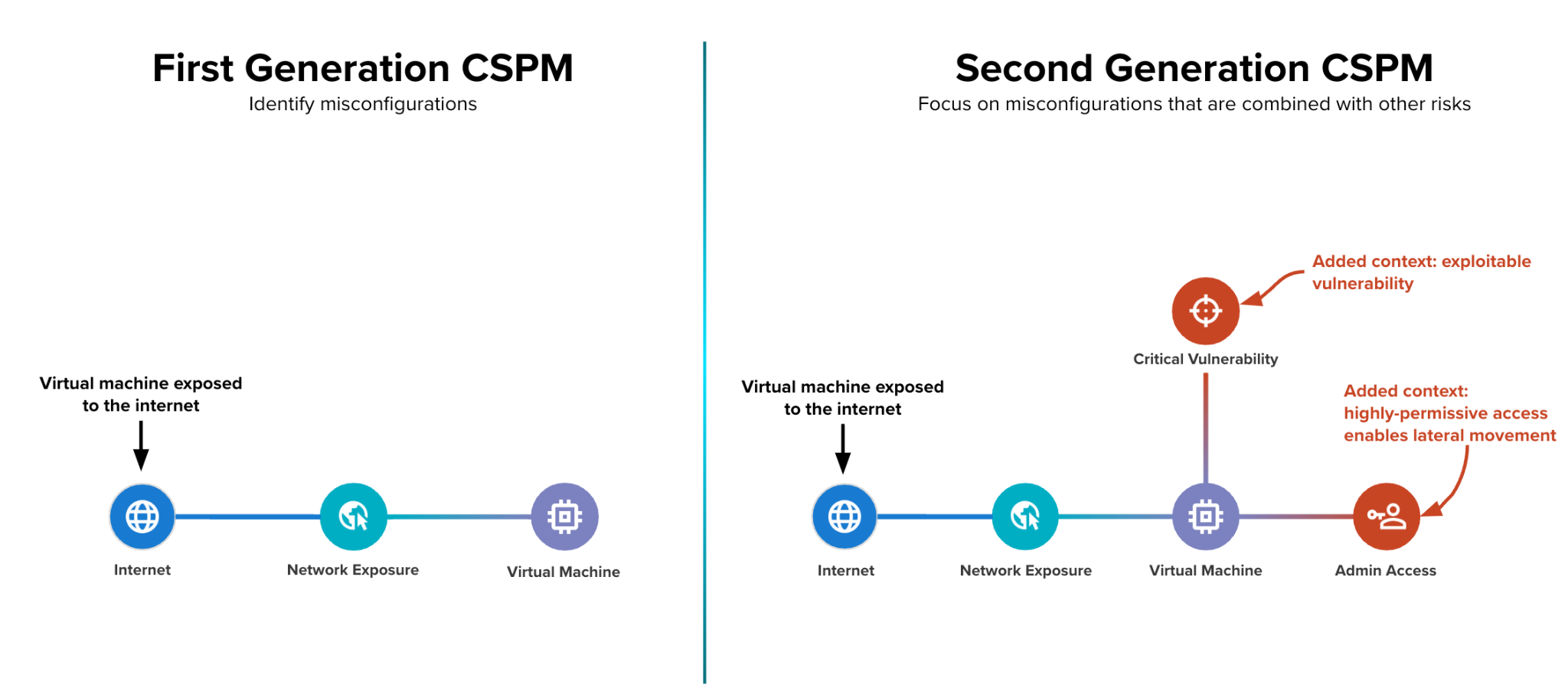
To overcome the alert prioritization challenges, the industry responded by consolidating CSPM with other cloud security functions, often into a cloud-native application protection platform (CNAPP). This shift increased the scope of CSPM to include identifying and correlating risk factors that form attack paths within cloud environments, such as misconfigurations, network exposures, vulnerabilities and excessive permissions.
Internal research from Palo Alto Networks found that in the typical cloud environment, only 1% of cloud misconfigurations are linked to open attack paths. Identifying these helps security teams focus on the issues that matter.
With organizations seeking tool consolidation, pure-play CSPM tools vanished during this era. This doesn’t mean CSPM is dead. On the contrary, a Gartner forecast predicts that by 2026, 60% of organizations will view preventing cloud misconfigurations as a cloud security priority, compared with 25% in 2021.
Why Second Generation CSPM Falls Short
The second wave of CSPM emerged to address the challenges caused by previous iterations; however, these solutions leave visibility and security gaps because of several critical limitations:
- Attack surface blind spots – Scanning only the inside of the clouds is incomplete visibility. Our research indicates that approximately 30% - 40% of an organization's publicly accessible attack surface is unknown. This creates the need for an “outside-in” view of your company’s clouds.
- No application context – Traditional CSPM approaches provide an asset-centric view of your cloud, while internal teams think in terms of applications. This leaves security teams blind to application risk impact and makes collaboration with development teams difficult.
- Find and fix treadmill – Resolving issues at runtime completely ignores that a single configuration mistake in code can multiply into dozens, sometimes hundreds, of cloud misconfigurations. Traditional approaches leave security teams stuck in a loop of identifying and resolving issues in their cloud environments, many of which are repeated mistakes that could have been prevented.
The New Generation of CSPM
At Palo Alto Networks, we believe CSPM should provide more visibility, context and prevention-first security. The new wave of CSPM builds on the groundwork laid out by previous iterations and addresses gaps by delivering the following:
External Attack Surface Management
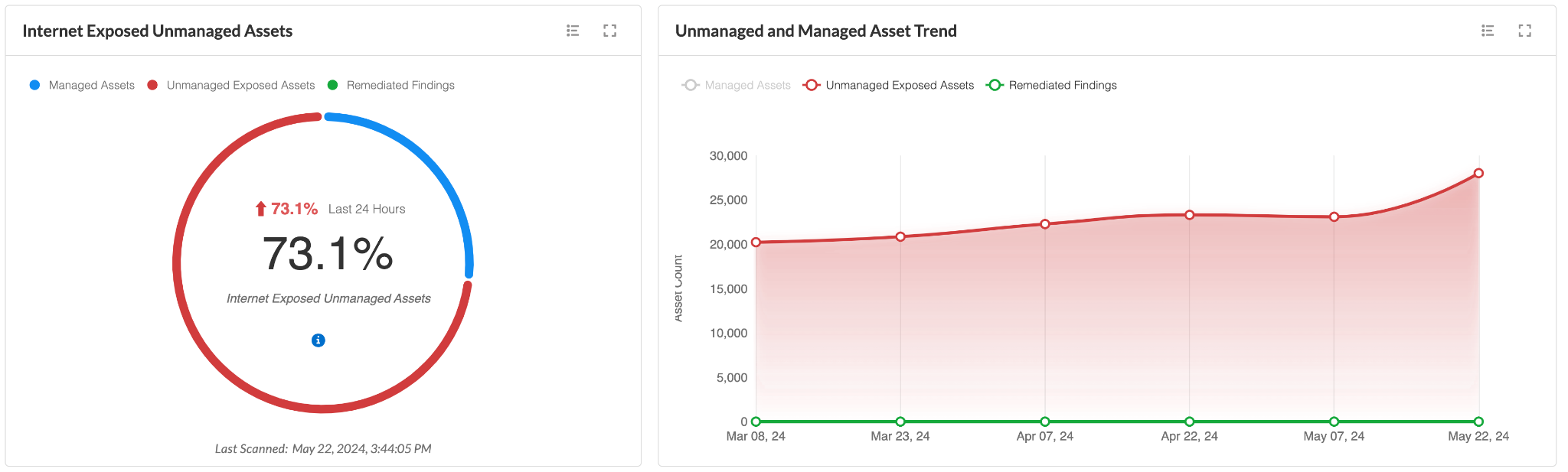
A modern CSPM approach scans the entire internet to discover internet exposures and evaluate the risk of the shadow clouds, unknown assets or unmanaged services. Prisma Cloud, a Code to CloudTM platform, makes this possible through cloud discovery and exposure management (CDEM), enabling security teams to gain an outside-looking-in view of their cloud environments, including clouds they might not know even existed.
Application Context
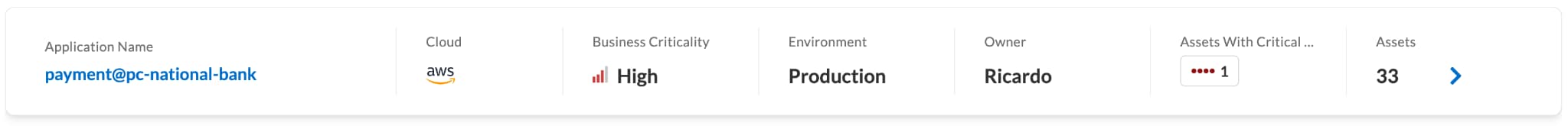
Traditional CSPM tools focus on assets and workloads, but security and developer teams really care about the applications. Prisma Cloud delivers AppDNA, helping security teams understand what applications are deployed across clouds, which assets form the application and who owns the application.
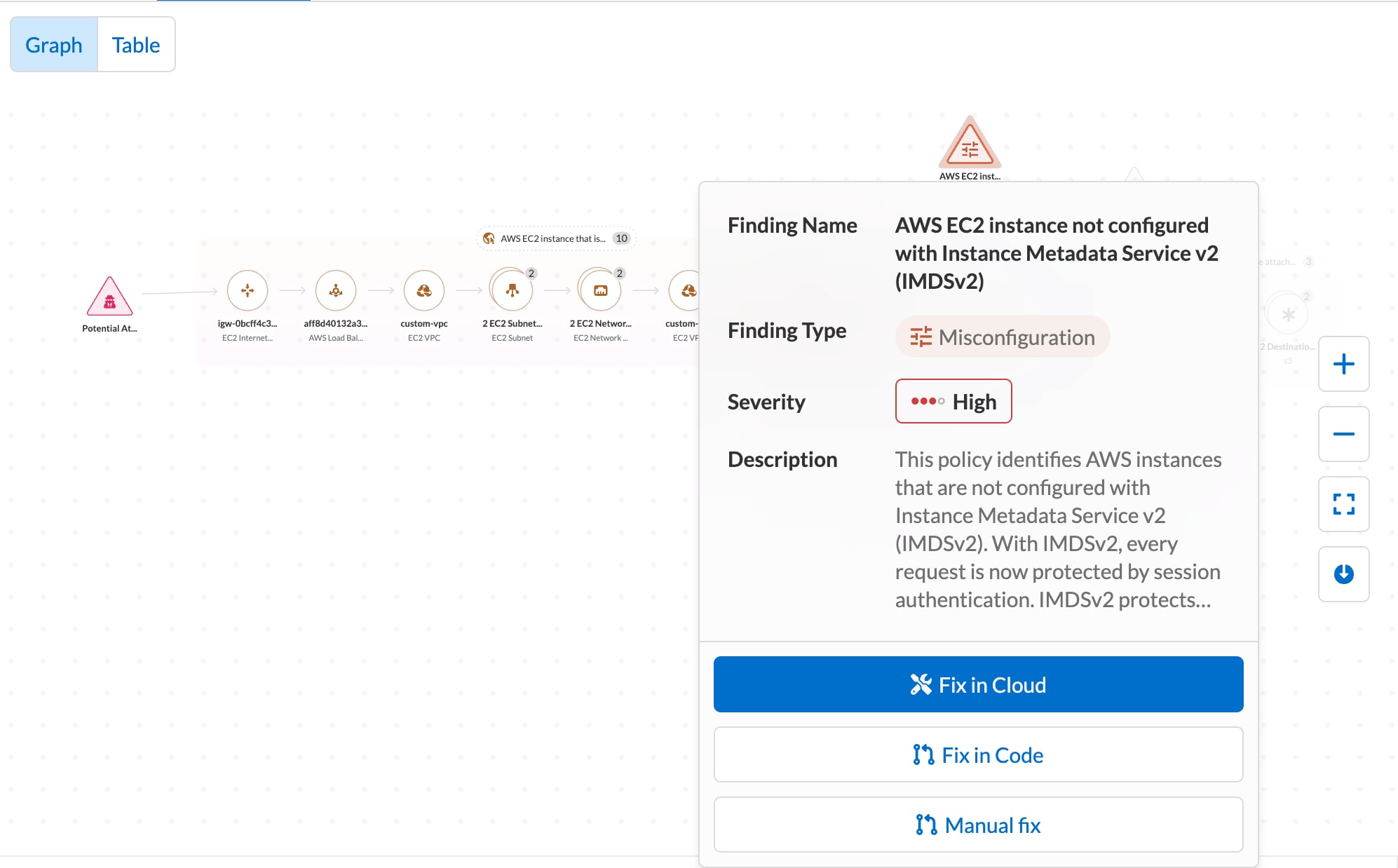
Tracing Cloud Risks to Code
Forwarding cloud misconfigurations to developers via ticketing systems is an extremely common, but inefficient CSPM approach. Tackling issues in the cloud as opposed to fixing mistakes at the source is like treating an illness instead of curing it. That’s why Prisma Cloud traces cloud risks back to the infrastructure-as-code (IaC) misconfiguration that caused the issue, enabling security teams to resolve security risks at the source.
These are just a few of the many reasons why organizations choose Prisma Cloud to secure their applications from code to cloud. Want to see what critical risks lurk in your cloud? Schedule a quick cloud security assessment.