The main use cases for Cloud Security Posture Management (CSPM) are to continuously enforce resource configurations, assure compliance and detect threats. However, effectively managing user permissions and enforcing least privilege access is equally important for a robust cloud security posture.
Identity Issues Unique to The Cloud
Controls for who is authenticated (signed in) and who is authorized (has permission) to use cloud resources and make changes to configurations are inconsistently defined across cloud service providers (CSPs). There are many different – and sometimes overlapping – policies and levels of permissions that can be attached to each user, which makes the seemingly simple task actually rather complicated. Perhaps it’s no wonder why Gartner predicts that, by 2023, 75% of all cloud security breaches will be the result of inadequate permission management.
Cloud Infrastructure Entitlement Management (CIEM) aims to address this challenge by going beyond what traditional identity governance and administration (IGA) and privileged access management (PAM) tooling can offer. CIEM tools focus on some of the unique challenges posed by cloud environments like ever-changing architectures and disparate workloads.
With the recent launch of the Prisma Cloud IAM Security module, we start by solving one of the most common identity challenges our customers have: What are the effective permissions of X? In other words, who actually has access to what in our cloud?
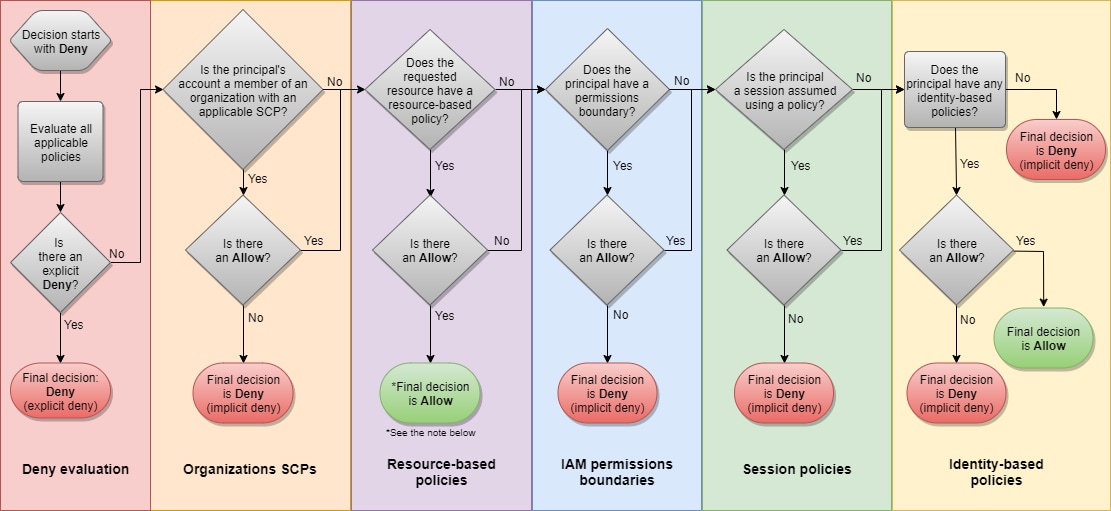
Net Effective Permissions
Prisma Cloud calculates these "net effective permissions" by first aggregating CSP-managed policies and user-managed policies, as well as policies attached to groups, roles, resources and access control lists (ACLs). Then it reconciles all of the different functions those permissions, roles and entitlements serve and how they are administered across cloud environments to holistically determine effective permissions. But that is only the beginning.
The IAM Security module correlates these net effective permissions with the actual usage at the API level, enabling users to identify risky permissions, overly permissive policies, widely granted permissions, public access and more. The API-level granularity provides high accuracy in recognizing the risks and offers confidence with specific remediation steps. With a fully automated flow, the module provides continuous, comprehensive protection for each cloud identity.
The module also introduces a new identity-specific policy type to Prisma Cloud, enabling users to create custom rules to address risks specifically related to identity. Furthermore, the module tracks actual user usage in cloud environments to analyze which permissions are redundant, and, most importantly, automatically recommends remediation steps to continuously enforce least privileged access.
CIEM + CSPM: The Power of Integration
By integrating the new IAM Security module with the existing CSPM capabilities in Prisma Cloud, users gain three unique benefits:
- The unparalleled flexibility to query any identity-related event, by using RQL to ask specific questions about their cloud environment, starting with simple questions such as:
- Which users have access to resource X?
- What accounts, services, and resources does the user name@domain.com have access to?
- Which resources can be accessed by the public?
- Granular visibility and posture management controls that go beyond mere configuration governance, like ensuring databases are not accidentally exposed to the public internet or firewall rules allow traffic to specific ports, and the ability to correlate those results with resource entitlements and user permissions.
- A deeper contextual understanding of risk, as CIEM capabilities can be augmented with our existing ML-powered User Entity Behavior Analytics (UEBA) to create higher-fidelity alerts that help prioritize identity-related issues.
The Prisma Cloud IAM Security module is available for all existing CSPM customers. Request a personalized demo and ask about a 30-day trial to begin analyzing your risky permissions, and simplifying your path to enforcing a least privilege access model.