Prisma Cloud adds developer-first Infrastructure as Code (IaC) Security to launch the most comprehensive platform built to unify security, development, and DevOps teams.
As enterprises undergo digital transformations and embrace cloud native applications, they want to unleash the creativity of their developers to rapidly develop and deploy new innovations. These enterprises need a simplified architecture to secure their cloud environments; one that enables them to leapfrog the cost and complexity of a patchwork of point products.
To complete that vision for our customers, Palo Alto Networks is excited to announce the integration of Bridgecrew’s Infrastructure as Code (IaC) security capabilities into the Prisma Cloud platform.
Bridgecrew is the pioneer in shift left and IaC security, where infrastructure protections are codified during development. The company’s developer-first IaC security platform offers developers and DevOps teams a unified way to enforce infrastructure security standards throughout the development lifecycle.
Infrastructure as Code presents an opportunity to shift security left
IaC allows developers to define how their infrastructure will be configured using a human-readable code format. This allows them to adopt software processes like version control, collaboration and testing on code (rather than live infrastructure). This improves speed and reliability when deploying and managing infrastructure.
However, this automated process means a single insecure IaC template could provision hundreds of insecure resources, snowballing to hundreds or thousands of security alerts. For example, a Unit 42 Cloud Threat Report recently found that 63% of third-party IaC templates contained insecure configurations and 96% of open source container images contain known vulnerabilities.
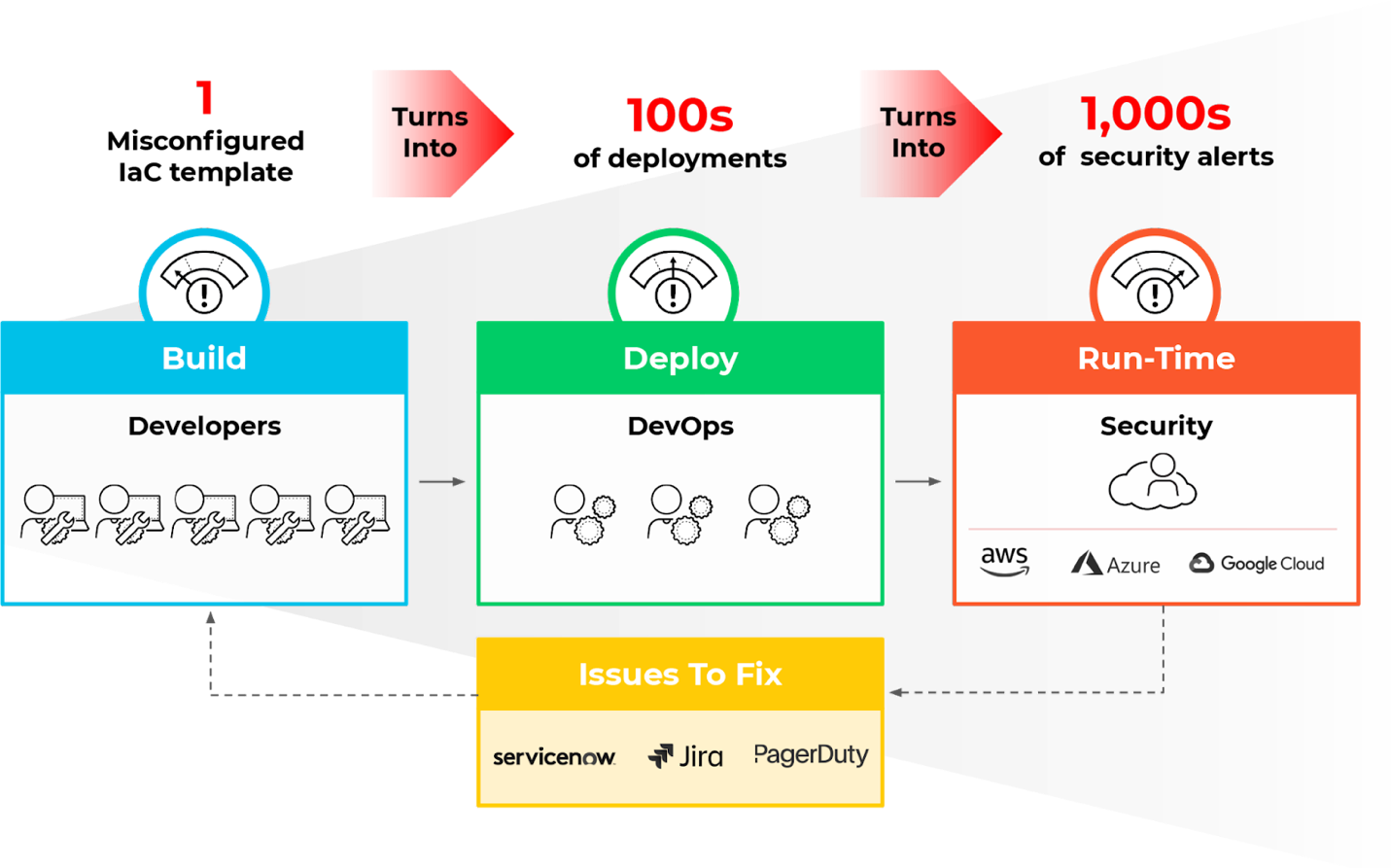
Shift left security aims to involve developers in security through automated feedback earlier in the development lifecycle. If security issues are addressed in code prior to deployment, then cloud resources are deployed securely from the beginning, and security teams are freed up to work on higher priority tasks.
How this integration reduces risk across the development lifecycle
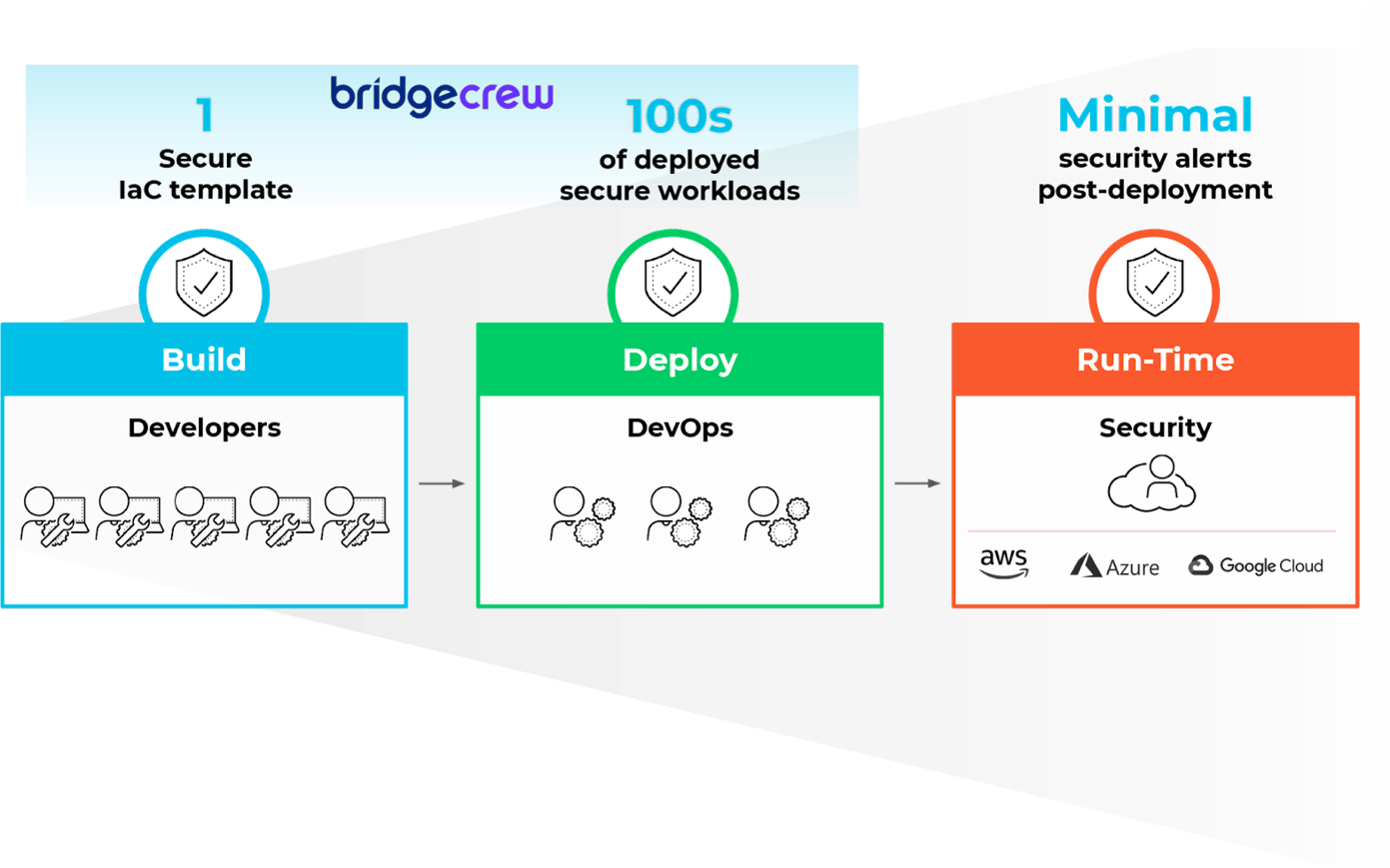
With Bridgecrew capabilities integrated directly in the platform, Prisma Cloud customers benefit from a single integrated platform that will deliver cloud security across code, build, deploy and runtime to seamlessly connect security with development and DevOps teams.
Developers gain visibility into misconfigurations in their code and security teams can be assured that misconfigured code is blocked or addressed before deployment. This is critical because developers know they need to secure their code, but they are often left out of policy decisions or aren’t fully aware of all the policies they need to enforce. Prisma Cloud is empowering developers to take ownership of their share of security. This creates a natural point of collaboration where teams can work together on misconfigurations and decide what constitutes acceptable risk.
Build Phase: Address Misconfigurations in IaC Templates
Popular IaC frameworks—such as Terraform, CloudFormation, Kubernetes manifests, Helm charts, Azure Resource Manager (ARM) and Serverless Framework—are used to provision and deploy resources across different cloud providers. If left undetected, misconfigurations in those templates, such as lack of encryption or insecure networking design, manifest as insecure cloud infrastructure.
Prisma Cloud IaC Security now allows customers to shift security left when provisioning cloud infrastructure, by alerting developers to misconfigurations during development. Prisma Cloud scans IaC files via command line interface (CLI) or integrated development environment (IDE) to check against hundreds of policies built into the open source tool Checkov that has been downloaded over two million times. These policies are built on industry benchmarks such as CIS, NIST, PCI, and HIPPA, as well as community use cases.
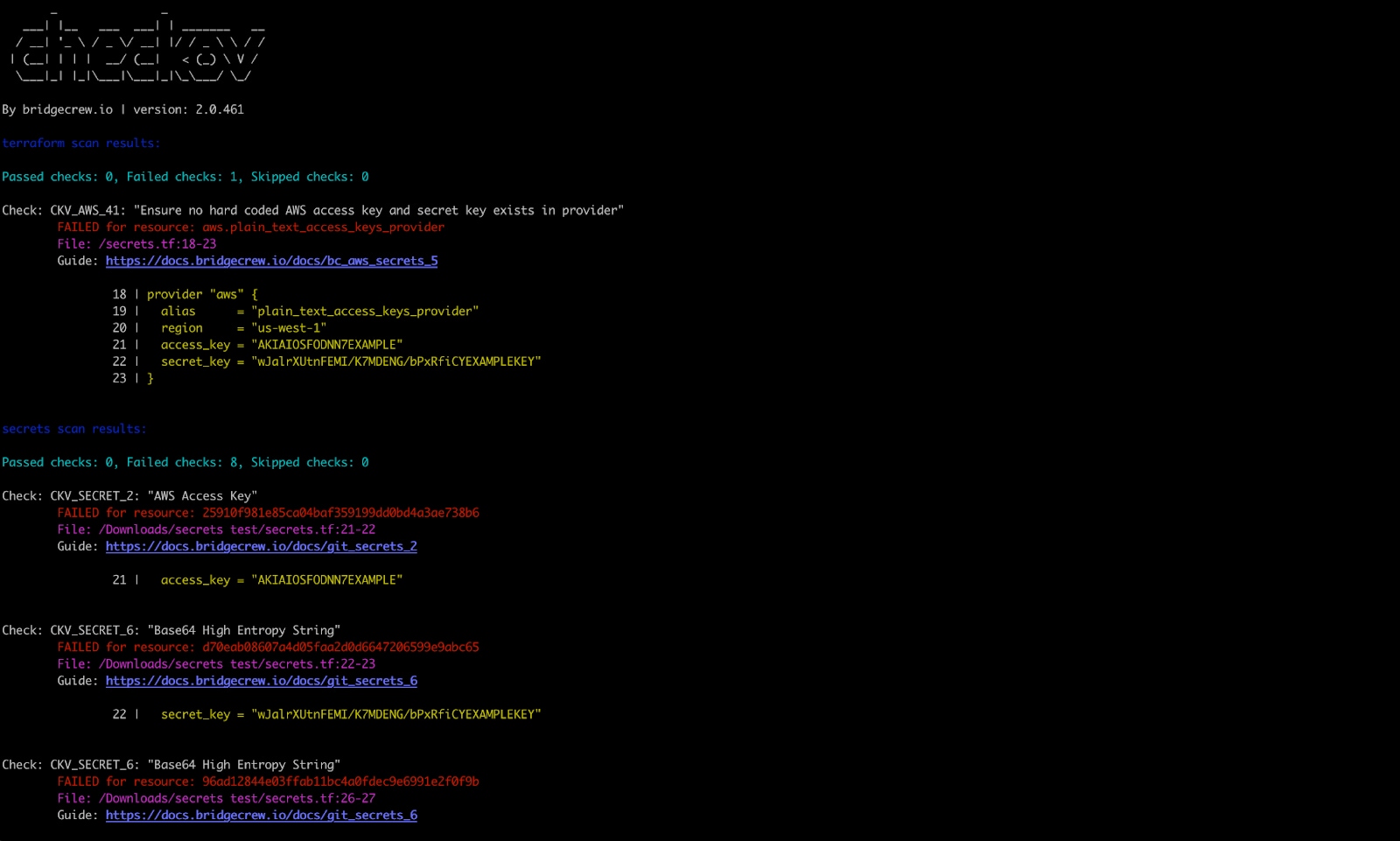
Prisma Cloud integrates these controls into developer tools to catch misconfigurations during code development. This means there are fewer misconfigurations when code is checked back into a version control system (VCS), and fewer misconfigurations for the cloud infrastructure when the code is applied.
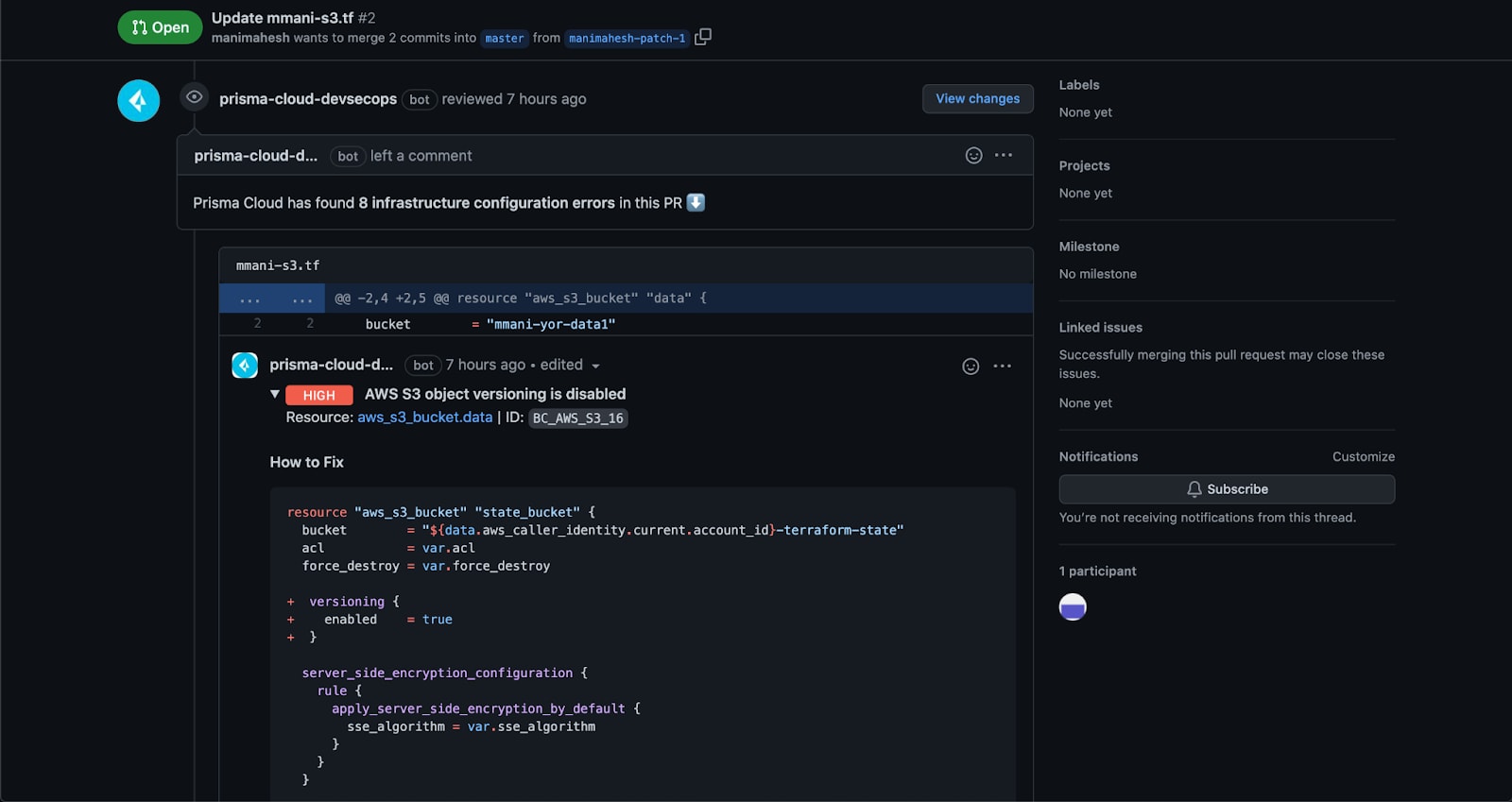
Deploy Phase: Embed Security in the CI/CD Pipeline
Prisma Cloud embeds IaC scanning into the continuous integration/continuous deployment (CI/CD) workflow. When an issue is discovered, developers and DevOps teams receive actionable feedback directly in their CI/CD tools. Powered by policy-as-code, Prisma Cloud provides guidance, guardrails, and remediation in the form of pull request comments, CI tests and automated commits/pull requests.
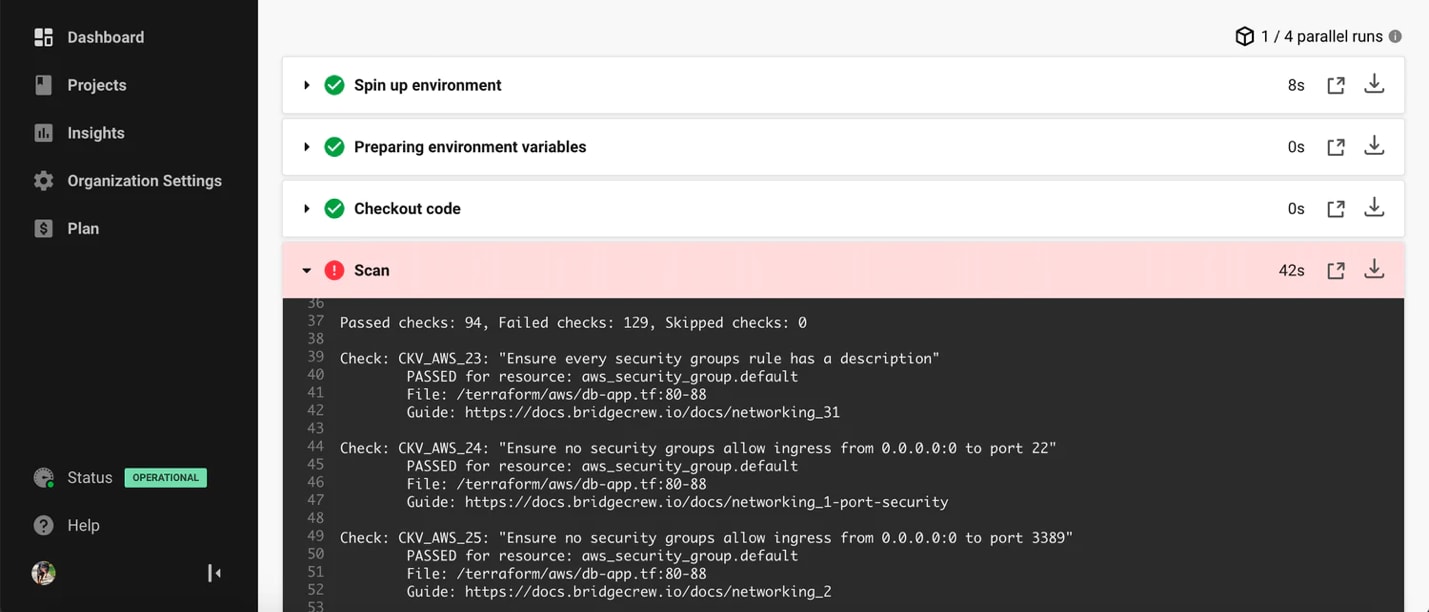
Every code scan across the development lifecycle is then viewable within Prisma Cloud, all in a centralized platform next to the other cloud native security platform capabilities.
Run Phase: Combine Best-of-Breed IaC Scanning and Cloud Native Security Platform
The integration means development teams can address a majority of misconfigurations in code to minimize the burden on security teams, freeing up security teams to focus on misconfiguration alerts for resources not deployed with IaC and more advanced security concerns like anomalous account behavior and network threat detection.
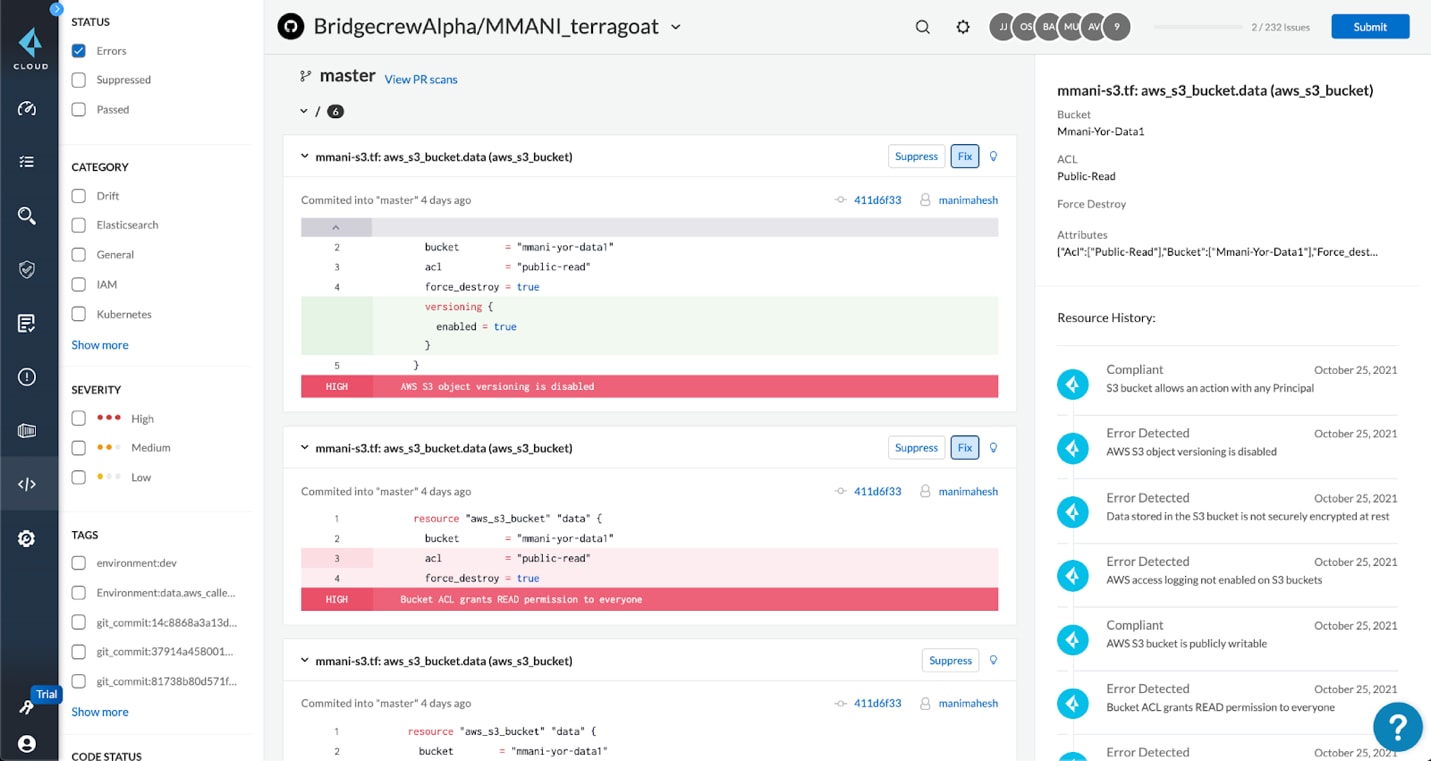
Additionally, the IaC security capabilities can address many of the requirements for industry compliance, while existing functionality in Prisma Cloud makes it simple to generate audit reports for a comprehensive library of benchmarks.
Finally, we’re creating a unified alerting mechanism. Notifications can be routed to the relevant team through integration with Jira, Slack, Splunk, Email, ServiceNow, MS Teams.
Full lifecycle cloud infrastructure security
Integrating Bridgecrew into the Prisma Cloud platform bolsters our full lifecycle, full stack security capabilities. Developers benefit from early, actionable feedback, embedded into their tools, preventing misconfigurations in cloud infrastructure from reaching production while reducing alert fatigue for security teams. By enabling closer collaboration across development, DevOps and security teams, Prisma Cloud helps create more secure infrastructure across the development lifecycle.
The integrated Bridgecrew and Prisma Cloud offering will be generally available in January 2022. To experience this combined, full-lifecycle offering, please visit our website and schedule a demo.