It seems like every time you turn on the news, there’s a major new attack method or zero-day vulnerability ready to be exploited: Solarwinds Sunburst, Microsoft Exchange zero-day exploit, Nobelium threat group, Kaseya, Log4J, and the list goes on.
To ensure that your organization is resilient to these attacks, speed is of the essence.
This week’s playbook, or rather set of playbooks, can help you quickly process, collect and hunt for indicators of compromise (IOCs) associated with a zero-day vulnerability or exploit, and perform quick response actions upon discovery of said IOCs.
Each playbook would be unique to the type of exploit, but the abstracted workflow below illustrates the various types of tasks that can be automated to speed up the investigative and hunting process for you.
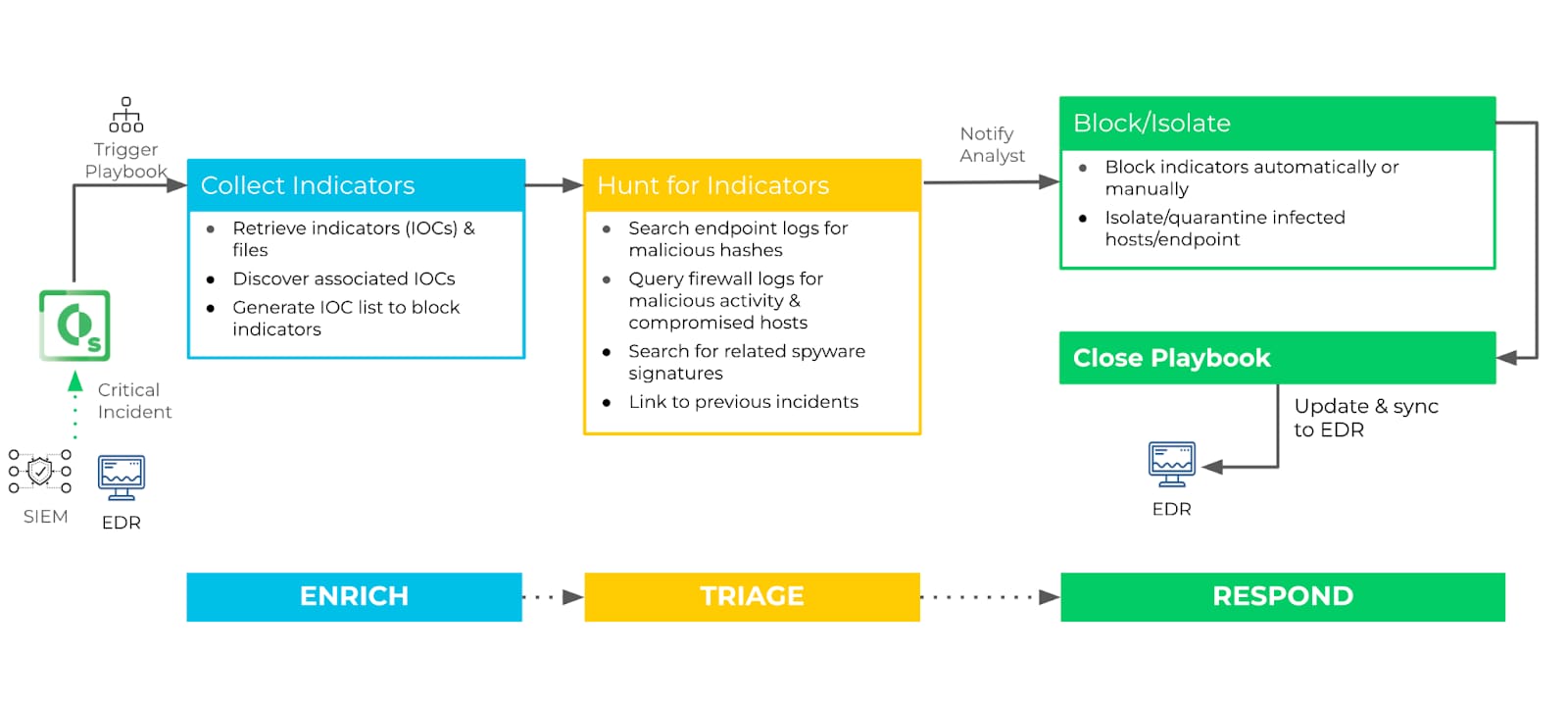
Enrich and Triage:
In the case of a breach or zero-day alert, the process of retrieving and discovering associated IOCs is as repetitive as it is important. Your analysts risk getting mired in this grunt work while the attack continues to manifest. Secondly, isolated security tools can struggle to reconcile threat data across platforms and get an overall understanding of malicious activity and spread.
By running an automated playbook at the outset of incident response, your team can query endpoints, firewalls, and other incidents in seconds, shaving off wasted time that can be used towards locking down defenses.
Respond:
The playbooks can execute initial response actions based on IOCs. For instance, a playbook can block indicators, isolate, or quarantine infected hosts, or feed malicious indicators back into threat intelligence databases and tool watchlists to build resiliency and avoid future attacks using the same indicators.
So the next time you hear about a breach or zero-day in the news, don’t panic. We might just have a playbook to help you out. Some examples of playbooks available in the XSOAR Marketplace include:
- Sunburst and SolarStorm Hunting and Response
- FireEye Red Team Tools Investigation and Response
- HAFNIUM - Exchange 0-day Exploits
- Codecov Breach - Bash Uploader
- CVE-2021-22893 - Pulse Connect Secure RCE
- NOBELIUM - wide scale APT29 spear-phishing
- CVE-2021-34527 | CVE-2021-1675 - PrintNightmare
- Kaseya VSA 0-day - REvil Ransomware Supply Chain Attack
To learn more about how you can automate security operations with Cortex XSOAR, check out our virtual self-guided XSOAR Product Tour
We also host virtual and in-person events, so check here for upcoming ones.