- 1. Why antivirus doesn't stop all modern attacks
- 2. What does antivirus actually cover in a modern small business?
- 3. Where does antivirus fall out of step with small business threats?
- 4. Where should security operate in modern small businesses?
- 5. What does browser-level enforcement actually protect against?
- 6. So—is antivirus enough for small businesses?
- 7. What should small businesses change about current security practices?
- 8. Effectiveness of antivirus for small businesses FAQs
- Why antivirus doesn't stop all modern attacks
- What does antivirus actually cover in a modern small business?
- Where does antivirus fall out of step with small business threats?
- Where should security operate in modern small businesses?
- What does browser-level enforcement actually protect against?
- So—is antivirus enough for small businesses?
- What should small businesses change about current security practices?
- Effectiveness of antivirus for small businesses FAQs
Is Antivirus Enough for Small Businesses? What It Misses
- Why antivirus doesn't stop all modern attacks
- What does antivirus actually cover in a modern small business?
- Where does antivirus fall out of step with small business threats?
- Where should security operate in modern small businesses?
- What does browser-level enforcement actually protect against?
- So—is antivirus enough for small businesses?
- What should small businesses change about current security practices?
- Effectiveness of antivirus for small businesses FAQs
Antivirus is useful but not enough for small businesses.
It detects known malware on managed devices but does not protect against credential misuse, browser-based access, or SaaS abuse. Most modern attacks happen before execution, in places antivirus was never designed to see.
Why antivirus doesn't stop all modern attacks
Most small businesses evaluate whether antivirus is enough after something breaks.
A phishing email lands. Someone signs in. Data is accessed. Sometimes exfiltrated. And the antivirus software stays quiet. That's the moment the question “Is antivirus enough for a small business?” surfaces.
You had antivirus installed. It was running. It didn't alert. Yet something clearly went wrong.
Which leads to a reasonable conclusion: either the product failed, or it was never in a position to intervene.
Here's the thing.
Antivirus is built to detect malicious software on a device.
But many modern attacks don't involve malware at all. They rely on stolen credentials, happen inside legitimate cloud applications, and unfold entirely within a browser session.
In these cases, nothing malicious is installed. Nothing executes locally, so there's nothing for the antivirus to see.
Which means the issue isn't that antivirus is broken. It's that the attack didn't occur in the layer antivirus was designed to protect.
That's the mismatch this article is about.
What does antivirus actually cover in a modern small business?
Antivirus serves as the 'boots on the ground' for your hardware.
Its primary role is to scan, identify, and stop malicious code from compromising the local operating system.
That includes scanning files, detecting known malware, and flagging suspicious execution behavior. Some tools also include basic behavioral monitoring to catch variants that don't exactly match known signatures.
To put it simply, antivirus focuses on what happens on the device.
It looks for harmful files. Watches how programs behave once they run. And assumes the device itself is managed, monitored, and consistently protected by an installed agent.
That assumption matters.
Because in most small businesses, antivirus doesn't come with full detection and response capabilities.
There's often no centralized telemetry. No automated containment. No ongoing investigation after an alert. Once something is detected, the outcome usually depends on a person noticing the alert and taking action.
The point is this: antivirus coverage typically stops at the endpoint.
It doesn't see what happens inside cloud applications, track user behavior across SaaS tools, or provide visibility into activity that never touches the local file system.
Important: This isn't a flaw. It's a design choice.
Ultimately, antivirus is built for post-execution malware defense.
It's meant to catch malicious software after it appears on a device or begins to run. It's not designed to control access. It's not designed to govern user actions. And it's not designed to enforce policy across unmanaged or shared systems.
That scope can still be useful. But it's narrow by design.
- What Is Endpoint Detection and Response (EDR)?
- What Are Endpoint Detection and Response Tools?
- What Is Endpoint Security Antivirus?
- What Is the Difference Between Advanced Endpoint Security and Antivirus (AV)?
Where does antivirus fall out of step with small business threats?
Antivirus is often evaluated as if every business operates in a tightly managed environment.
That assumption breaks down quickly in small organizations.
Many small businesses rely on personal laptops, shared office computers, or temporary access for contractors. Endpoint agents may not be installed everywhere. And even when they are, coverage is inconsistent.
There's also the operational reality.
Small businesses rarely have 24/7 monitoring or dedicated incident response. Alerts, if they occur, depend on someone noticing them. Often after the fact. That makes antivirus a reactive control, not a continuous one.
Now layer in how attacks typically start today.
Most compromises don't begin with malware. They begin with access.
A phishing email convinces someone to sign in. Credentials are reused. A session token is captured. From there, the attacker operates inside legitimate applications: Email. Cloud storage. Accounting platforms. CRM tools.
The activity looks like a normal user session because, technically, it is one.
This is where timing matters.
Antivirus is designed to intervene after something suspicious executes on a device.
But when an attack happens entirely through identity misuse or browser-based access, there's no execution event to detect.
Access is granted before malware ever appears. Sometimes malware never appears at all. Data can be viewed, copied, or exfiltrated directly through the browser. Especially in cloud and SaaS environments.
Basically, the threat model has shifted. But antivirus is still anchored to a point in the attack chain that small business attacks increasingly bypass.
If an attacker logs in with valid credentials, antivirus has no reason to respond. So the core issue isn't detection quality. It's enforcement timing.
Where should security operate in modern small businesses?
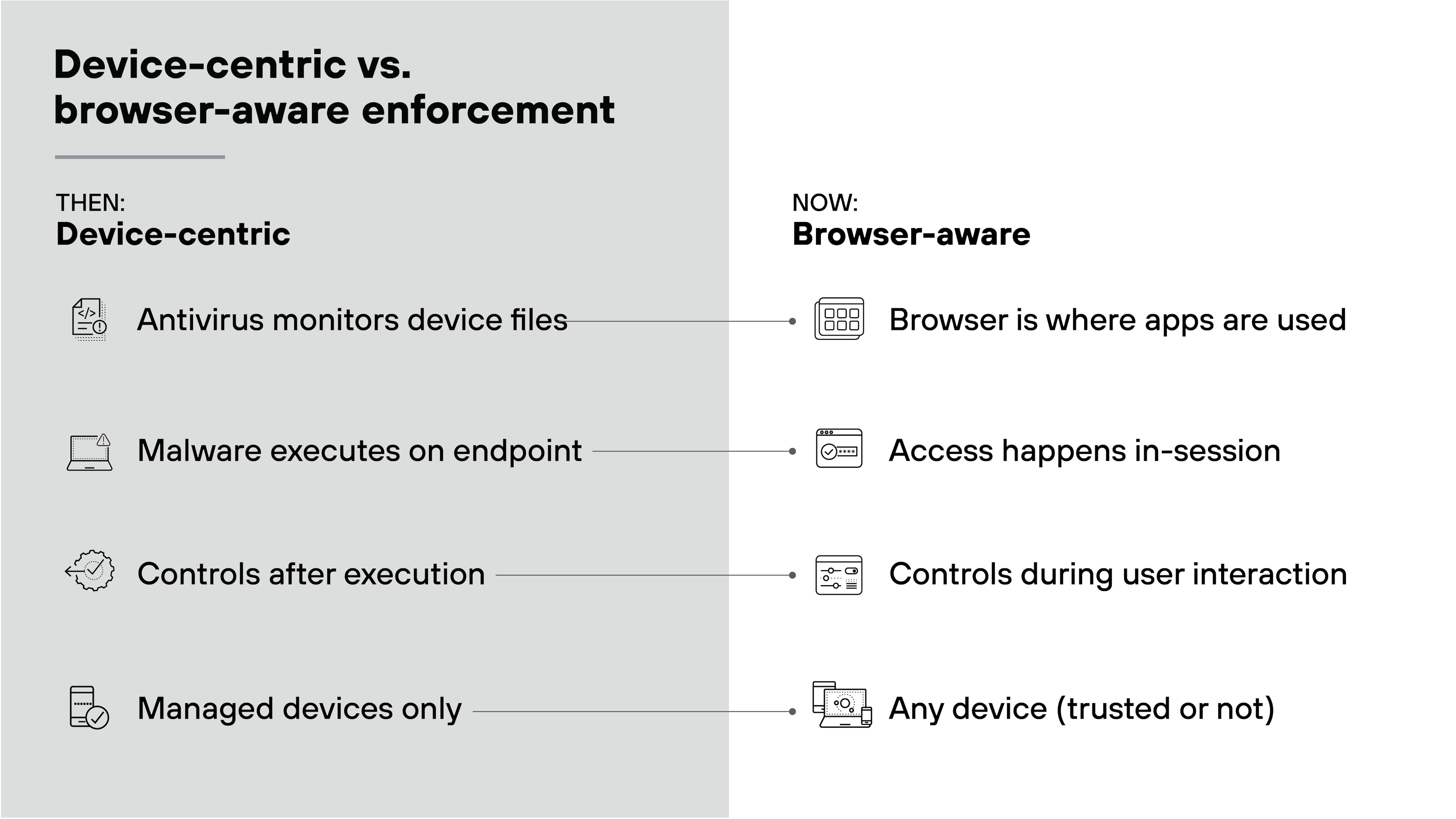
Security decisions no longer happen only on the device. Increasingly, they also happen in the browser.
That's where employees log in to email. Where client documents are shared. Where payroll and billing systems are accessed. And it's also where attackers can exploit access if nothing stands in their way.
Essentially, the browser has become the new control point. Most critical actions—whether legitimate or malicious—happen inside that session.
However:
Most antivirus tools are still focused on what happens after something bad lands on the device.
That leaves a gap.
Security can't just operate after a problem starts.
It needs to act during the session. While the user is clicking, typing, sharing, or uploading. That's the moment risk is introduced. That's the moment it must be contained.
So security should operate at the point of access. In real time. Regardless of what device someone's using.
That shift changes everything.
It repositions the browser as the logical enforcement layer. Not because it's trendy, but because it's where business happens now. And where exposure begins if controls aren't there.
This doesn't require a full-stack replatform. It just means recognizing that modern work—and modern risk—both start in the same place. Inside the session. Inside the browser.
COMPARISON
Prisma for Business vs. Consumer Browsers: See the difference.
View DatasheetWhat does browser-level enforcement actually protect against?
Browser-level enforcement applies controls where antivirus can't.
It can limit what users can do with sensitive data during a session.
For example, it can prevent copy, paste, print, download, or screen capture. It can watermark what's visible. It can log actions taken during access. It can require reauthentication before specific actions. And it can enforce these policies without needing to trust the underlying device.
These capabilities fall under a product category known as secure browsers, also sometimes referred to as enterprise browsers or secure enterprise browsers.
These tools apply policy directly in the session without needing to manage the underlying device. They treat the browser as a controllable environment, allowing organizations to restrict activity, monitor behavior, and enforce security during access itself.
This is important because most small businesses can't guarantee device trust.
Contractors, remote staff, and shared computers are common. Browser-based controls work even when no endpoint agent is installed. Even when there's no malware present. Even when no file ever gets downloaded.
That's the difference.
Browser enforcement protects the data itself during use.
Not just the device. It gives small businesses a way to apply consistent policy at the only place risk can be controlled in real time: inside the session.
Not before. Not after. While it's happening.
That's what makes it structurally different from antivirus and necessary alongside it.
Explainer Video
See for yourself how Prisma Browser for Business ensures productivity never comes at the cost of security.
So—is antivirus enough for small businesses?
Antivirus is still useful for what it's designed to do, which is to help detect and stop malicious software on individual devices as a baseline layer of defense. That protection is still important.
But antivirus alone isn't enough for most small businesses today.
That's because, as mentioned, work no longer happens primarily on managed endpoints. It happens in cloud applications, browsers, and across personal devices, shared systems, and remote access.
So whether antivirus is “enough” depends on where your controls operate. Not how many tools you deploy.
If security only engages after something runs on a device, gaps remain. Especially in SaaS-first, browser-based environments.
In short:
Antivirus is necessary. But on its own, it's not sufficient for how small businesses work—and how they're attacked—today. That's why many small businesses are shifting enforcement to where the risk actually happens.
What should small businesses change about current security practices?
Antivirus alone isn't enough, but the next step isn't just adding more tools. It's stepping back and rethinking where risk actually shows up:
Where are your users working?
What devices are they using?
When are actions most likely to introduce exposure?
And most important—what controls do you have at those moments?
You don't need to rip out what you have. But you may need to shift your focus.
This isn't about replacing antivirus entirely. It's about recognizing where enforcement needs to happen—at the point of access, inside the browser, during the session itself. That means evaluating security tools built to operate there.
Secure browsers give small businesses a way to apply policy in real time, across devices they don't own or fully control. They make it possible to enforce access rules, monitor behavior, and protect data at the moment risk is introduced.
That's how you align protection with the way small businesses actually work today.
Get the secure browser free for 30 days.
No long-term contracts. Cancel anytime during your free trial.
Start your 30-day free trial