-
- How to Respond to a Ransomware Attack
- How Do Ransomware Attacks Begin?
- Reducing Dwell Time
- Common Threat Actor Techniques
- Data Theft and Multi-extortion Ransomware
- How to Uninstall Ransomware and Retrieve Data
- Steps to Recovery After a Ransomware Attack
- ® Incident Response Methodology
- Ransomware Removal and Recovery FAQs
Table of Contents
-
What Is Ransomware?
- Ransomware Key Takeaways
- Why Ransomware Matters
- Stages of a Ransomware Attack
- How Ransomware Uses Psychological Pressure
- Types of Ransomware
- Example Ransomware Strains
- Role of Human Behavior in Cybersecurity
- Ransom Payment and Prevention
- Creating and Testing an Incident Response Plan
- Understanding if You Have a Ransomware Infection
- Difference Between Malware and Ransomware
- What is Multi-Extortion Ransomware?
- Why Ransomware Is Illegal
- Recovery from Ransomware Attacks
- Is Ransomware Still a Threat?
- Future-Proofing Against Ransomware
- Ransomware FAQs
- What Are the Most Common Types of Ransomware?
- What are Ransomware Attacks?
- What is Ransomware Prevention?
What is Ransomware Response and Recovery?
5 min. read
Table of Contents
Ransomware response and recovery involves identifying malware and minimizing the harm inflicted on affected systems as a result of ransomware attacks. Although data recovery from ransomware is often possible, the more difficult task is preventing the subsequent loss of productivity and revenue, damage to brand reputation, and potential exposure of sensitive information.
How to Respond to a Ransomware Attack
BlackCat Ransomware Case Study - Palo Alto Networks
So much of the ransomware discussion centers on prevention that the hard realities regarding actual attacks, and the actions taken to affect ransomware removal and recovery, can get obscured. Knowing what to do when your organization falls victim to a ransomware attack and your best efforts fail is critical.
Time is of the essence in ransomware attack situations. Knowing how to act quickly to halt the attack’s progression, prevent it from spreading, and communicate with attack groups in the event you need to negotiate are all important skill sets.
Organizations need to evolve defenses to address the various methods threat actors use to apply pressure. Today's incident response plans need to involve not only technical considerations but also safeguards for an organization’s reputation and how to protect employees or customers who may become targets for some of the extortionists’ more aggressive tactics.
Quick access to an incident response team and legal advisors is vital during extortion attempts. An effective response plan and crisis communication strategy will lessen uncertainty and clarify stakeholder roles and decision-making, such as payment approvals. Training employees on ransomware harassment and conducting a thorough post-incident review is essential to prevent future attacks.
How Do Ransomware Attacks Begin?
Ransomware attacks typically begin through the following vectors:
Phishing Emails
Attackers send emails that appear to be from legitimate sources but contain malicious attachments or links. When the attachment is opened or the link is clicked, the initial payload is downloaded and installed on the user’s device.
Exploit Kits
These are tools that cybercriminals use to exploit known vulnerabilities in software and operating systems. If a user's system is not updated with the latest security patches, exploit kits can provide an easy way for ransomware to infiltrate.
Remote Desktop Protocol (RDP) Exploits
RDP is a popular way to access computers remotely. Attackers can use brute-force attacks or stolen credentials to gain access to a network via RDP and then deploy ransomware.
Drive-by Downloading
Merely visiting a compromised website without interaction can lead to a ransomware infection if the site has a drive-by download setup to exploit browser vulnerabilities.
Malvertising
Malicious advertising can redirect users to ransomware distribution sites or trick users into downloading malicious software disguised as legitimate software.
Social Engineering
Attackers use psychological manipulation to trick users into breaking security procedures, such as giving away sensitive information or granting access to critical systems.
Software Vulnerabilities
Attackers can also exploit unpatched vulnerabilities in widely used software, deploying ransomware without any user interaction.
Supply Chain Attacks
By compromising a software provider or a vendor, attackers can use the trust relationship between businesses to deploy ransomware. For instance, a malicious update from a vendor could contain ransomware.
Network Propagation
Once inside a network, some ransomware variants can move laterally across connected systems, using various techniques to identify and compromise additional machines.
Understanding these vectors is crucial in developing effective defenses against ransomware. Regular security training, system patching, and vigilant monitoring of networks and emails are vital in preventing such attacks. Also, consider mitigating ransomware risk by performing targeted assessments and attack simulations designed to identify hidden vulnerabilities, weak security controls, or signs of compromise in your environment.
Reducing Dwell Time
Dwell time is the period of time a threat actor spends in your environment before being detected. If you can stop threat actors in the earlier stages of their attack, you can avoid downstream ransomware in your environment. To reduce dwell time and identify threat actor activity, ensure you monitor unusual indicators in your system.
Look out for:
- The installation and usage of unauthorized remote access tools
- Unauthorized discovery activity (e.g., scanning, enumeration)
- Atypical file access or downloads
- Unusual network traffic
Common Threat Actor Techniques
As ransomware groups have evolved and maximized the effectiveness of ransomware as a service in recent years, multi-extortion techniques have allowed ransomware groups to increase leverage and maximize profit. Threat actors will look for any opportunity to gain the upper hand.
With multi-extortion techniques, attackers do more than encrypt files and disrupt business operations. For example, they often post information about breached organizations on dark web leak sites and threaten to release or sell stolen data if a ransom is not paid. The goal is to get you to pay more money faster.
To minimize ransomware attacks, follow a defense-in-depth approach, implementing safeguards throughout all layers of your infrastructure (e.g., email, web applications, and network). You can also employ services that monitor your brand and associated communications (e.g., communications on the dark web).

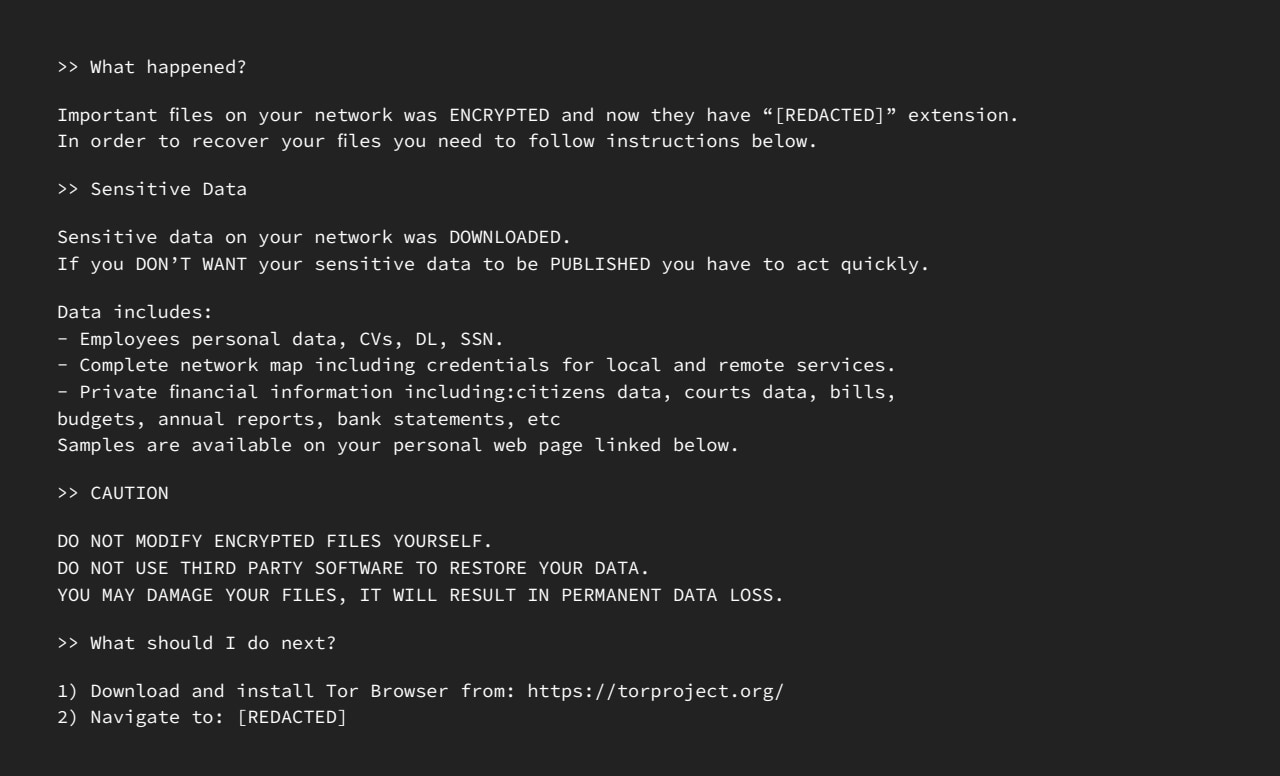
This is an example of a BlackCat ransom note that was dropped on a comprised system.
The ransomware landscape has continued to evolve, with specific extortion tactics becoming more prevalent. While the frequency of tactics can vary depending on the targets and attackers, the following were among the most commonly reported:
Encryption of Data
The fundamental tactic of encrypting a victim's data and demanding a ransom for the decryption key remains very common, as it directly impacts the victim's operations and creates a clear incentive to pay.
Data theft
Attackers often steal sensitive data before or during encryption and then threaten to release it publicly if the ransom is unpaid.
Multi-Extortion Ransomware
In addition to encrypting the victim's files, multi-extortion ransomware adds additional layers to the cyberattack involving the ransomware operator exfiltrating files and threatening to publicly release the victim's data unless the ransom is paid.
The added threat increases the pressure on the victim to pay the ransom quickly and makes it more difficult for them to refuse to pay. These attacks can be particularly damaging because they disrupt the victim's ability to access their own data while also potentially exposing sensitive or confidential information to the public.
Harassment of Employees and Customers
Attackers increasingly contact employees and customers of the affected organization, pressuring the company from multiple angles to pay the ransom to avoid damage to its reputation and relationships.
Time-Sensitive Ultimatums
Many ransomware groups use countdown timers that threaten irreversible consequences if the ransom isn’t paid within the given timeframe, exploiting the urgency to force quick decision-making.
The commonality of these tactics underscores the importance of comprehensive preventative measures, strong backup strategies, and incident response plans to mitigate the risks before an attack occurs and respond effectively if one does happen. It's also worth noting that the landscape can shift rapidly, and new tactics can emerge at any time, so continuous monitoring of cybersecurity trends is crucial.
Data Theft and Multi-extortion Ransomware

Manufacturing, Professional and Legal Services and Wholesale and Retail are the most heavily impacted industries targeted by ransomware extortion.
Ransomware groups often threaten to leak data stolen from victims. Due to the efficacy of this tactic, many threat actors target regulated data sets or highly commercially sensitive information for maximum leverage.
What is Data Theft?
Data theft is the unauthorized taking or intercepting of files and personal information from a computer system. This can be accomplished through various means, such as hacking, malware, phishing, or insider threats. The stolen data may include sensitive personal information, intellectual property, business documents, customer databases, and other valuable digital assets. Cybercriminals can use this data for various malicious purposes, including identity theft, financial fraud, corporate espionage, or selling information on the dark web.
What is Multi-Extortion Ransomware?
Multi-extortion ransomware is an advanced attack that combines encrypting a victim’s data with threats of leaking it, harassing stakeholders, launching additional attacks, and demanding further ransoms. This strategy amplifies the pressure on victims to pay to avoid greater damage, such as operational disruption, public exposure, and legal consequences.
This multi-pronged approach significantly increases the pressure on victims to pay the ransom, as they face multiple potential consequences beyond losing access to their data. It also complicates the recovery process and increases possible damages, including reputational harm and regulatory issues, mainly if sensitive customer data is involved and privacy laws such as GDPR are violated.
How to Uninstall Ransomware and Retrieve Data
Uninstalling ransomware from a compromised system can be a challenging and complex task, but it is not impossible. To remove ransomware from your systems, follow these steps:
- Isolate the infected system: Disconnect the compromised computer from the network to prevent the ransomware from spreading to other devices.
- Identify the ransomware: Identify the ransomware type affecting your system. This is crucial for two reasons: to explore decryption tools and to understand the malware for effective removal. If available, trustworthy decryption tools can help recover encrypted files resources.
- Remove the ransomware: Use reputable antivirus or anti-malware software to scan and remove the ransomware from your system. Make sure your antivirus definitions are up to date. Some ransomware variants may be resistant to removal. In such cases, you may need to consult with a professional computer security team, such as Unit 42, or use specialized removal tools.
- Restore your files: Restore files from a clean backup source if you have backups. Do not use backups made while the system is infected, as they may contain encrypted files, or the malware will restart the infection. If you don't have backups, you can recover your files using decryption tools if they are available for your specific ransomware variant. Law enforcement agencies, cybersecurity companies, and community-driven initiatives sometimes release such tools.
- Strengthen your security: After removing the ransomware, improving your system's security is essential to prevent future infections. Update your operating system and software, and install a reliable security suite. Be cautious about email attachments, downloads, and links from untrusted sources.
Steps to Recovery After a Ransomware Attack
Even after a ransomware incident is resolved, it takes time for an organization to fully restore operations, remediate security issues, improve security controls, and recover the financial and reputational ground lost. After ransomware has been removed, the following steps should be taken to recover.
Investigation
Conduct a thorough investigation to understand how the ransomware entered your systems, the scope of the impact, and any data that might have been compromised or exfiltrated.
Restoration and Recovery
Restore data from backups, ensuring you do not reintroduce ransomware into the network. Validate that backups are clean before restoration. This should be done systematically and with caution to avoid reinfection.
Communication
Communicate with internal and external stakeholders about the incident, what is being done in response, and what steps will be taken to prevent future incidents.
Enhancement of Security Posture
Based on the findings from the investigation, enhance your security protections to prevent similar attacks. This may include patching vulnerabilities, improving email filtering, and enhancing endpoint protection.
Training and Awareness
Provide training for employees to recognize and respond to phishing attempts and other malicious activities that could lead to a ransomware infection.
Continuous Monitoring
Implement continuous monitoring strategies to detect and respond to future incidents quickly.
Compliance and Reporting
Follow any necessary compliance regulations regarding data breaches, including reporting the incident to government bodies or notifying affected individuals.
Specific recovery steps can vary depending on the nature of the attack, the type of data involved, and the affected organization's pre-existing incident response protocols. Consulting with cybersecurity professionals and legal experts during the recovery process is often crucial to ensure proper incident handling.
Unit 42® Incident Response Methodology
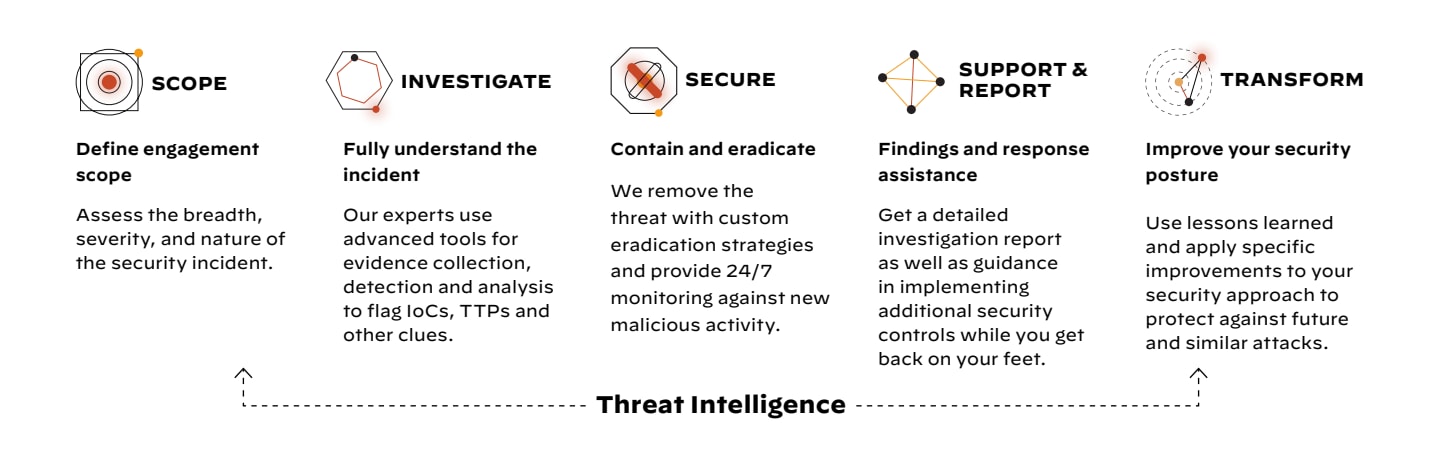
Palo Alto Networks follows a proven methodology as outlined in this image.
Unit 42, the threat intelligence and incident response team at Palo Alto Networks, helps customers respond to and recover from ransomware attacks through a combination of expert-led services, threat intelligence, and proactive defense strategies.
Scope
For an accurate understanding of the incident, getting the scoping phase right is critical. This allows us to align the right resources and skill sets to get your organization back up and running as quickly as possible and accurately estimate the effort needed to assist you.
Investigate
We work to fully understand the incident as we investigate what happened, leveraging the available data and working alongside your team.
Secure
As the incident is contained and the threat actor and their tools are eradicated from your environment, we concurrently assist your organization with rapidly restoring operations.
Support and Report
Unit 42 will also assist you in understanding the incident's root cause and potential impact, including any unauthorized access or acquisition of sensitive information that may trigger legal obligations.
Transform
A key step in incident response is helping ensure an improved security posture going forward. We work with you to apply specific improvements and build out incident response plans that will help protect against future and similar attacks.
Read Mitigating Cyber Risks with MITRE ATT&CK for an in-depth set of recommendations by Unit 42 incident responders.
Ransomware Removal and Recovery FAQs
Isolate the infected system from the network to prevent the spread of ransomware. Turn off Wi-Fi and Bluetooth, and unplug any storage devices. Use antivirus software to scan and remove the ransomware from the system if possible. Contact a cybersecurity professional for assistance.
It depends on the type of ransomware. Some decryption tools are available for certain ransomware strains, which can be found on websites like No More Ransom. However, there's only a guarantee for decryption with the specific key, and efforts should focus on restoring files from backups.
Law enforcement agencies and cybersecurity experts generally advise against paying the ransom. Paying does not guarantee file recovery and may encourage future attacks. Instead, focus on removing the malware and restoring systems from backups.
After removing the ransomware using antivirus or anti-malware tools, it's crucial to conduct a thorough scan of the entire network and validate the system's integrity. Engaging a cybersecurity firm for a post-mortem analysis is recommended to ensure all backdoors and malware traces are eradicated. Regularly update security patches and change all system passwords as a precaution.
