-
- Ransomware Key Takeaways
- Why Ransomware Matters
- Stages of a Ransomware Attack
- How Ransomware Uses Psychological Pressure
- Types of Ransomware
- Example Ransomware Strains
- Role of Human Behavior in Cybersecurity
- Ransom Payment and Prevention
- Creating and Testing an Incident Response Plan
- Understanding if You Have a Ransomware Infection
- Difference Between Malware and Ransomware
- What is Multi-Extortion Ransomware?
- Why Ransomware Is Illegal
- Recovery from Ransomware Attacks
- Is Ransomware Still a Threat?
- Future-Proofing Against Ransomware
- Ransomware FAQs
Table of contents
- What Are the Most Common Types of Ransomware?
-
What is Ransomware Response and Recovery?
- How to Respond to a Ransomware Attack
- How Do Ransomware Attacks Begin?
- Reducing Dwell Time
- Common Threat Actor Techniques
- Data Theft and Multi-extortion Ransomware
- How to Uninstall Ransomware and Retrieve Data
- Steps to Recovery After a Ransomware Attack
- ® Incident Response Methodology
- Ransomware Removal and Recovery FAQs
- What are Ransomware Attacks?
- What is Ransomware Prevention?
What Is Ransomware?
2 min. read
Table of contents
Ransomware is malicious software (malware) designed to encrypt files or systems, making them inaccessible until a ransom, typically in cryptocurrency, is paid. It commonly spreads via phishing emails, malicious downloads, and software vulnerabilities, and increasingly, through sophisticated supply chain and remote access attacks.
There are two main types:
- Locker Ransomware: This type locks users out of systems.
- Crypto Ransomware: This type encrypts files and demands payment for the decryption key.
Recent trends in ransomware attacks include a tactic known as double extortion, where attackers steal sensitive data before encrypting it, and then threaten to leak it if the ransom is not paid.
Ransomware Key Takeaways
- Ransomware remains a significant cyber threat that disrupts operations and compromises data.
- Tactics are advancing, incorporating methods like double extortion and Ransomware-as-a-Service (Raas).
- Effective defense requires layers including Zero Trust architecture, endpoint detection and response (EDR), regular backups, and comprehensive user training.
- Early detection is crucial and can be enhanced through behavior analytics and threat intelligence.
- Implement a well-tested response plan to reduce damage and shorten recovery time.
- Avoid paying ransoms, as it may be illegal and doesn’t guarantee the recovery of data.
- Stay ahead of future threats, such as AI-driven and automated attacks, to maintain robust security.
Why Ransomware Matters
Ransomware continues to be a significant cyber threat with the potential to cause extensive harm across various sectors, including businesses, healthcare, and government. A successful ransomware attack can lead to temporary operational shutdowns, total data loss, and substantial financial and reputational damage.
Stages of a Ransomware Attack
Stage 1: Infection
Ransomware typically enters a system through malicious email attachments, drive-by downloads, or by exploiting software vulnerabilities. Phishing attacks are a common method, deceiving unsuspecting users into downloading and executing malicious software. Once inside, the ransomware quietly spreads across networks, targeting valuable data to encrypt.
Stage 2: Execution and Encryption
After infiltrating the network, ransomware encrypts files, effectively locking users of their data. This encryption process uses complex algorithms, making file decryption nearly impossible without the specific decryption key. The ransomware may target various files, including documents, images, and databases, causing widespread disruption.
Stage 3: Ransom Demand
Upon encrypting the data, ransomware issues a ransom note instructing the victim to pay a ransom in exchange for the decryption key. The note often includes detailed payment instructions, typically requesting payment through cryptocurrencies. It also warns victims against contacting law enforcement. The ransom demand may include a deadline, after which the ransom amount may increase or the decryption key may be destroyed.
How Ransomware Uses Psychological Pressure
Ransomware is no longer merely about locking up files; it’s about manipulation. Modern ransomware attacks use psychological warfare to pressure victims into paying quickly, often before they’ve explored recovery options. Here’s a breakdown of how these tactics work:
Urgency, Fear, and Manipulation: The Anatomy of a Ransom Demand
Ransomware groups don’t just rely on encryption—they thrive on panic. One of their key tactics is the countdown clock. Victims are informed that they have a limited time, such as 72 hours, to pay the ransom or lose their data forever. At times, the ransom demand doubles after a specific period. The aim is to push victims into making a hasty decision under pressure. But it doesn’t stop there.
Attackers frequently utilize double extortion, which involves stealing sensitive data before encrypting it. The ransom note subsequently threatens to leak that data publicly or sell it on the dark web if payment is not made. This can be particularly devastating for industries such as healthcare, finance, or law, where leaked data has legal and reputational repercussions.
Many ransomware variants delete backups, disable restore points, or tamper with system files to close off escape routes. That means even technically savvy teams may find themselves unable to recover unless they’ve prepared in advance with offline backups and incident response protocols.
And finally, there’s the messaging. Ransom notes are meant to intimidate featuring elements like red text, blinking countdowns, frightening icons, and phrases like “We are the only ones who can help you.” It all contributes to a well-crafted psychological attack.
What Happens If You Pay?
Let’s be honest—some victims do pay. In some cases, ransomware operators actually provide a decryption key. Groups like LockBit or REvil have been known to deliver on their promises to maintain a “business reputation” within the cybercrime world. Fewer will pay if people don’t believe the attackers will hold up their end of the bargain.
But here’s the catch: there are no guarantees.
Victims may receive a buggy or incomplete tool, and others may never hear from the attackers again. Even if the decryption works, payment doesn’t erase the risk of data leaks, repeat attacks, or regulatory penalties—especially if sensitive customer data is involved.
What If You Don’t Pay?
If your organization is lucky (and prepared), you might have clean backups stored offline. This is the safest and most effective way to recover without paying. Sometimes, free decryption tools are available from trusted sources like NoMoreRansom.org, which collaborates with global law enforcement and cybersecurity experts.
Still, for organizations without backups or access to a decryption tool, data loss may be permanent. Even after recovery, the fallout, such as downtime, brand damage, legal action, and customer trust issues, can be long-lasting.
Types of Ransomware
Ransomware has evolved into various forms, each designed to achieve its malicious goals uniquely. Understanding the different types of ransomware is crucial for developing effective defense strategies. Below are the primary types, each with distinct characteristics and methods of operation that can affect the severity and nature of an attack.
Crypto Ransomware
Crypto ransomware encrypts personal files and demands a ransom for the decryption key. This type is the most common and can cause severe data loss if the ransom is not paid, especially if backups are unavailable.
Locker Ransomware
Locker ransomware locks the user out of their device while leaving the files intact, restricting access to the infected system. Although the data remains on the system, the user cannot access it without paying the ransom.
Double Extortion Ransomware
Double extortion is a tactic where attackers encrypt data and steal it before locking systems. This means victims face two threats:
- Pay to get their files back.
- Pay to prevent public exposure of sensitive information.
An organization may have backups that allow for data recovery without ransom payment, but the risk of data leaks can be even more destructive. Attackers frequently threaten to disclose sensitive information on public sites or sell it on dark web platforms if the ransom is not met.
This tactic elevates the risks, particularly for organizations managing regulated or sensitive data such as customer information, intellectual property, financial papers, or medical records. The potential reputational and legal ramifications of a leak can be significant, which is why many pressured companies contemplate making a payment.
Ransomware as a Service
Ransomware as a Service (RaaS) is a business model ransomware developers use. It allows affiliates to use the ransomware in exchange for a percentage of the ransom payments. This model has made ransomware attacks more accessible and has significantly increased their spread.
Wiper Ransomware
Wiper ransomware mimics traditional ransomware by demanding payment and displaying a ransom note, but its true purpose is to delete data irreversibly.
In contrast to conventional ransomware, which theoretically allows for recovery with a decryption key, wiper ransomware erases files, overwrites essential data, or damages system components beyond repair. Paying the ransom does not assist the victim because nothing remains to decrypt.
Wipers are frequently employed in politically motivated cyberattacks or to inflict maximum disruption. A notable example is NotPetya, which, while appearing as ransomware, functioned as a wiper that severely impacted global companies and incurred billions in damages. Other instances include HermeticWiper and WhisperGate, both used in assaults on Ukraine.
These attacks pose a significant risk, as they completely eliminate the chance of recovery—unless the victim has fully isolated backups or an effective disaster recovery plan.
Scareware
Scareware tricks victims into thinking their system is infected with a virus or malicious content. It then demands payment to fix the alleged issue, like WinFixer.
Doxware (or Leakware)
Doxware threatens to release sensitive or personal information unless the ransom is paid. It’s becoming more common as attackers target individuals and businesses.
Fileless Ransomware
Fileless ransomware operates in memory and doesn't leave a trace on the hard drive, making it harder to detect
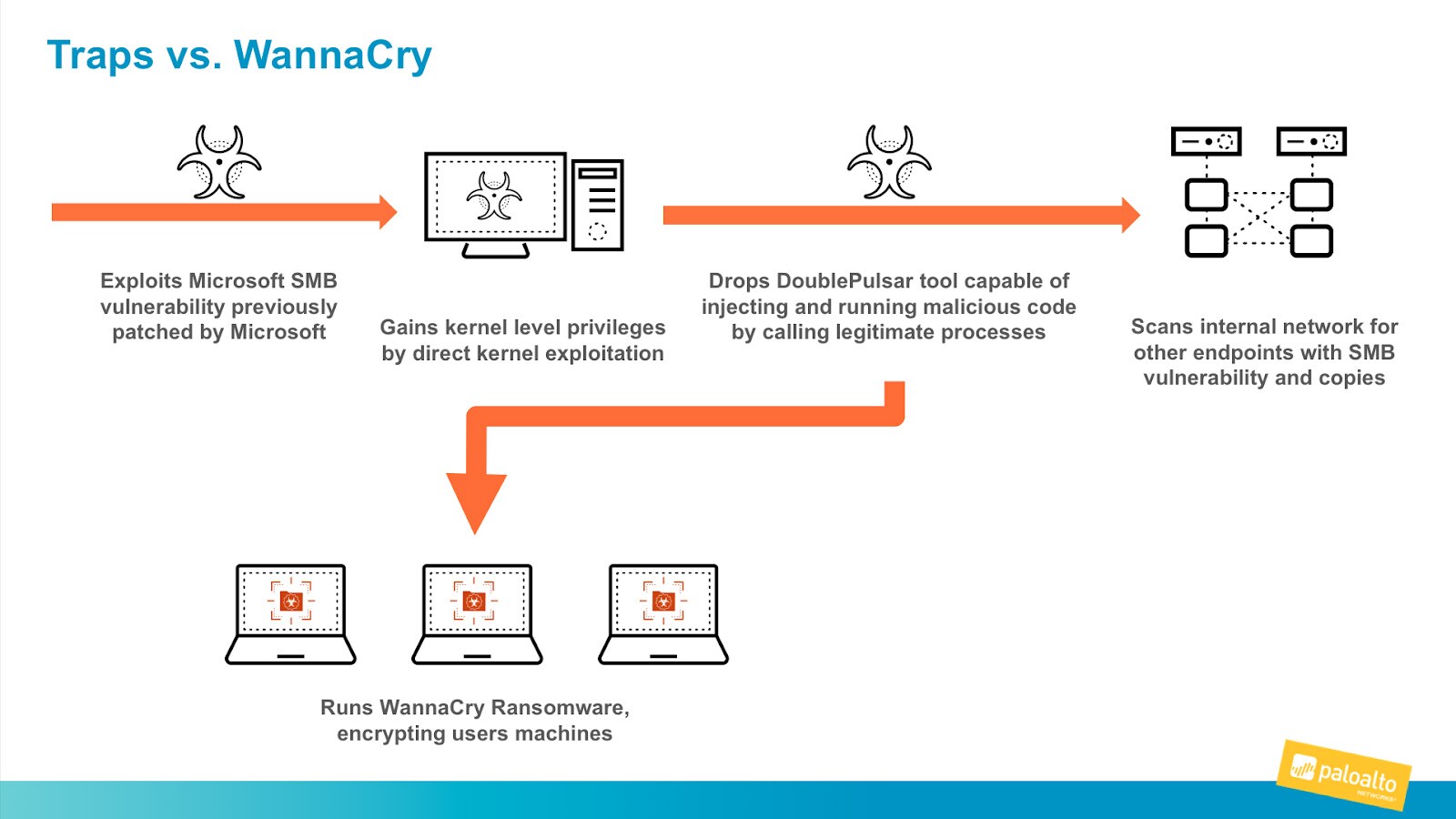
Example Ransomware Strains
Some well-known ransomware strains include:
- WannaCry: In 2017, this ransomware attack targeted systems running Windows OS and impacted over 200,000 computers in 150 countries.
- Ryuk: Known for targeting large enterprises, Ryuk is notorious for its use of double extortion tactics.
- Cryptolocker: One of the earliest and most notorious examples of ransomware, Cryptolocker encrypted files and demanded payment in Bitcoin.
Role of Human Behavior in Cybersecurity
Human error remains a significant vulnerability in cybersecurity. Social engineering tactics, such as phishing emails, exploit human behavior to gain access to systems. Educating employees on identifying suspicious emails and adopting safe browsing practices can greatly reduce the risk of a ransomware attack.
Ransom Payment and Prevention
Should You Pay the Ransom?
Paying the ransom does not guarantee that the decryption key will be provided, nor does it prevent future attacks. It is generally advised against paying the ransom, as it supports cybercriminals' illegal operations and funds their activities.
Prevention Measures
To prevent ransomware attacks, organizations can take several proactive measures, including:
- Regular Backups: Regularly back up important data to offline or cloud-based systems to minimize data loss.
- Security Training: Implement comprehensive training to educate employees about phishing attacks and safe computer practices.
- Patch Management: Ensure operating systems, software, and applications are up-to-date with the latest security patches.
- Anti-Ransomware Solutions: Deploy anti-ransomware and network monitoring tools to detect and block suspicious activities.
- Zero Trust Security Model: Assume all attempts to access network resources are threats, requiring verification at all times.
- Microsegmentation: Divides the network into isolated segments to contain breaches and limit potential damage.
- Endpoint Detection and Response (EDR): Use tools to protect endpoints, such as computers, mobile devices, and servers, from ransomware by continuously monitoring and responding to threats.
Creating and Testing an Incident Response Plan
A comprehensive incident response plan that includes immediate steps to isolate infected systems, communication strategies, and data recovery processes should be developed, tested, and regularly updated to ensure readiness when responding to ransomware incidents.
Essential components of a ransomware incident response plan include:
- Immediate Isolation and Assessment: Quickly disconnect infected systems from the network and assess the extent of the infection.
- Communication Strategy: Maintain clear communication channels and guidelines for informing stakeholders, employees, and customers.
- Forensic Analysis: Investigate the root cause of the infection and document the ransomware variant involved.
- Data Recovery Procedures: Outline steps for restoring data from backups and utilizing decryption tools.
- Post-Incident Review: Evaluate the response and identify areas of improvement.
- Regular Testing: Conduct drills and simulations of ransomware attacks to test the effectiveness and preparedness of the response plan.
Understanding if You Have a Ransomware Infection
Symptoms of a ransomware infection can include:
- Sudden inability to access files
- Unusual encryption messages appearing on the screen
- System slowness and unresponsiveness
- Presence of strange file extensions, especially following a phishing attempt or installation of unauthorized software
Responding promptly to these symptoms is critical to lessen the impact of the attack.
Difference Between Malware and Ransomware
While all ransomware is considered malware, not all malware is ransomware. Malware and ransomware are different in the following ways:
- Malware includes various malicious software, including viruses, worms, and trojans, designed to cause harm or unauthorized access.
- Ransomware specifically encrypts data and demands a ransom, focusing on financial gain and data integrity.
What is Multi-Extortion Ransomware?
Multi-extortion ransomware is a more advanced and sophisticated attack where cybercriminals use multiple extortion methods to pressure victims into paying the ransom. In addition to encrypting the victim's files and demanding payment for decryption, attackers often engage in one or more of the following tactics:
- Data Theft and Leak: The attackers exfiltrate sensitive data before encrypting it and threaten to release or sell this data if the ransom is not paid. This adds a layer of pressure, as victims fear the loss of valuable or sensitive information.
- Denial of Service (DoS) Attacks: Some ransomware groups launch DoS or DDoS attacks alongside encryption, further disrupting the victim’s ability to operate by overwhelming their network or servers.
- Threats to Expose or Harm: Attackers may also threaten to cause physical damage or expose embarrassing or compromising information, targeting the victim’s reputation and business integrity.
Popular examples of multi-extortion ransomware include REvil and Clop, which employ these tactics to increase the likelihood of the victim paying the ransom. The goal is to increase the pressure on victims by making the consequences of not paying far more severe than just losing access to data.
Why Ransomware Is Illegal
Ransomware is illegal because it involves unauthorized access to computer systems, extortion, and data theft. Legal systems worldwide prosecute individuals involved in developing and deploying ransomware and hold them accountable for the damages caused.
Recovery from Ransomware Attacks
Can Ransomware Be Removed?
Ransomware response and recovery is complex. While ransomware can be removed from a system, recovering encrypted files without a backup is nearly impossible without the decryption key. Specialized ransomware removal tools can clean the infection, but prevention remains the best approach.
Ransomware can indeed be removed from a system, but the process depends on the specific type of ransomware and the extent of the infection. Here are some steps and tools that can aid in the removal process:
- Identify the Ransomware Variant: Knowing the specific type of ransomware can help find the proper removal tools and techniques.
- Isolate the Infected Systems: Disconnect infected machines from the network to prevent the spread of ransomware to other systems.
- Use Anti-Malware Tools: Utilize reputable anti-malware and anti-ransomware software to scan the system and remove the malicious components. Examples include Malwarebytes, Emsisoft, and Bitdefender.
- Update Signatures and Software: Ensure all anti-malware tools are up-to-date with the latest signatures to effectively identify and remove ransomware.
- Manual Removal: In some cases, system administrators might need to delete ransomware files and registry entries manually. To avoid further system damage, this should only be done by experienced professionals.
- Restore Systems: If malware removal tools cannot fully clean the system, reinstall the operating system or restore systems from a clean backup.
Specialized ransomware removal tools can clean the infection, but prevention remains the best approach to avoid reinfection and mitigate future risks.
Can You Recover Encrypted Files?
Recovering encrypted files after a ransomware attack can be challenging and typically depends on whether backups are available and their integrity. Here are the methods for recovering files:
- Restore from Backups:
- Cloud Backups: If data is backed up to a cloud service, restore the files from the last clean backup before the ransomware infection.
- Offline Backups: Data backed on external drives or offline systems can be restored.
- Regular Backup Practices: Ensure backups are performed frequently to minimize the data loss window.
- Decryption Tools:
- No More Ransom Project: This initiative offers free decryption tools for certain ransomware strains. Users can check if a decryptor is available for their specific infection.
- Vendor Solutions: Some security vendors may develop decryptors for specific ransomware families.
- Ransom Payment: Paying the ransom to obtain the decryption key is generally not recommended due to the risk of non-receipt and moral implications.
- Data Recovery Services:
- Specialized data recovery firms may assist in recovering encrypted data, although success rates can vary and costs can be high.
- Shadow Copies:
- Windows Volume Shadow Copy Service (VSS) may provide previous versions of files if ransomware did not disable or delete shadow copies.
Is Ransomware Still a Threat?
Ransomware continues to evolve with sophisticated attack vectors and new variants, such as double extortion and RaaS. Its persistence as a threat necessitates ongoing vigilance and updated cybersecurity strategies to defend against it.
Understanding ransomware is crucial for maintaining cybersecurity awareness. Educating yourself about its operation, prevention, and recovery mechanisms can create a safer online environment for individuals and organizations. Continual vigilance and adherence to best practices in cybersecurity are essential to mitigate the ongoing threat posed by ransomware.
Future-Proofing Against Ransomware
To mitigate the impact and recurrence of ransomware, organizations must adopt a proactive approach to cybersecurity:
- Education and Training: Regular training sessions to educate employees about the latest phishing tactics and safe computing practices.
- Advanced Security Measures: Implement multi-layered security approaches, including zero trust models, micro-segmentation, and endpoint detection and response (EDR) tools.
- Regular Updates: Ensure systems, software, and applications are patched with the latest security updates.
- Robust Backup Solutions: Invest in reliable backup solutions, offline and cloud-based, and frequently test their integrity.
Keeping your organization safe from a ransomware attack requires a fundamental shift away from detection and remediation toward prevention. This means reducing the attack surface, preventing known threats, and identifying and preventing unknown threats.
Ransomware FAQs
Ransomware is a type of malicious software designed to block access to a victim's files or system by encrypting data. Attackers demand a ransom, often in cryptocurrency, in exchange for the decryption key. It typically spreads through phishing emails, malicious websites, or software vulnerabilities.
To protect your computer from ransomware, use up-to-date antivirus software, enable firewalls, and regularly back up your data. Be cautious when opening email attachments or clicking on links from unknown sources. Ensure your system and software are updated to close any security vulnerabilities.
If infected with ransomware, disconnect your device from the internet immediately to prevent the malware from spreading. Avoid paying the ransom, as it does not guarantee that your files will be decrypted. Instead, report the incident to authorities and try restoring files from backups if available.
Yes, ransomware can be removed without paying the ransom in some cases. Many cybersecurity tools and decryption software can help remove the ransomware. If the ransomware is known, there may be a decryption tool available. If not, consulting with a cybersecurity professional may be necessary.
