- What Is Access Management?
- What Is Access Control?
- What Is Passwordless Authentication?
- What Is CIAM (Customer Identity and Access Management)?
-
Authentication and Authorization Explained
- Authentication and Authorization Explained
- Differentiating Authentication from Authorization
- Authorization Models: RBAC, ABAC, and Policy Enforcement
- Lateral Movement and Attacker Workflow
- Cloud Security Implications for Authorization
- Zero Trust Alignment with Access Control
- Authentication and Authorization FAQs
- What Is Single Sign-On (SSO)?
- What is BeyondCorp?
- What is the Evolution of Multifactor Authentication
- What Is the Principle of Least Privilege?
- What is Multifactor Authentication (MFA) Implementation?
- What Is Identity and Access Management (IAM)?
What Is Cloud Infrastructure Entitlement Management (CIEM)?
Cloud infrastructure entitlement management (CIEM) is the process of managing identities and privileges in cloud environments. The purpose of CIEM is to understand which access entitlements exist across cloud and multicloud environments, and then identify and mitigate risks resulting from entitlements that grant a higher level of access than they should.
With CIEM solutions, security teams can manage cloud identities, entitlements, and enforce the principle of least-privileged access to cloud infrastructure and resources. CIEM solutions help companies reduce their cloud attack surface and mitigate access risks posed by excessive permissions.
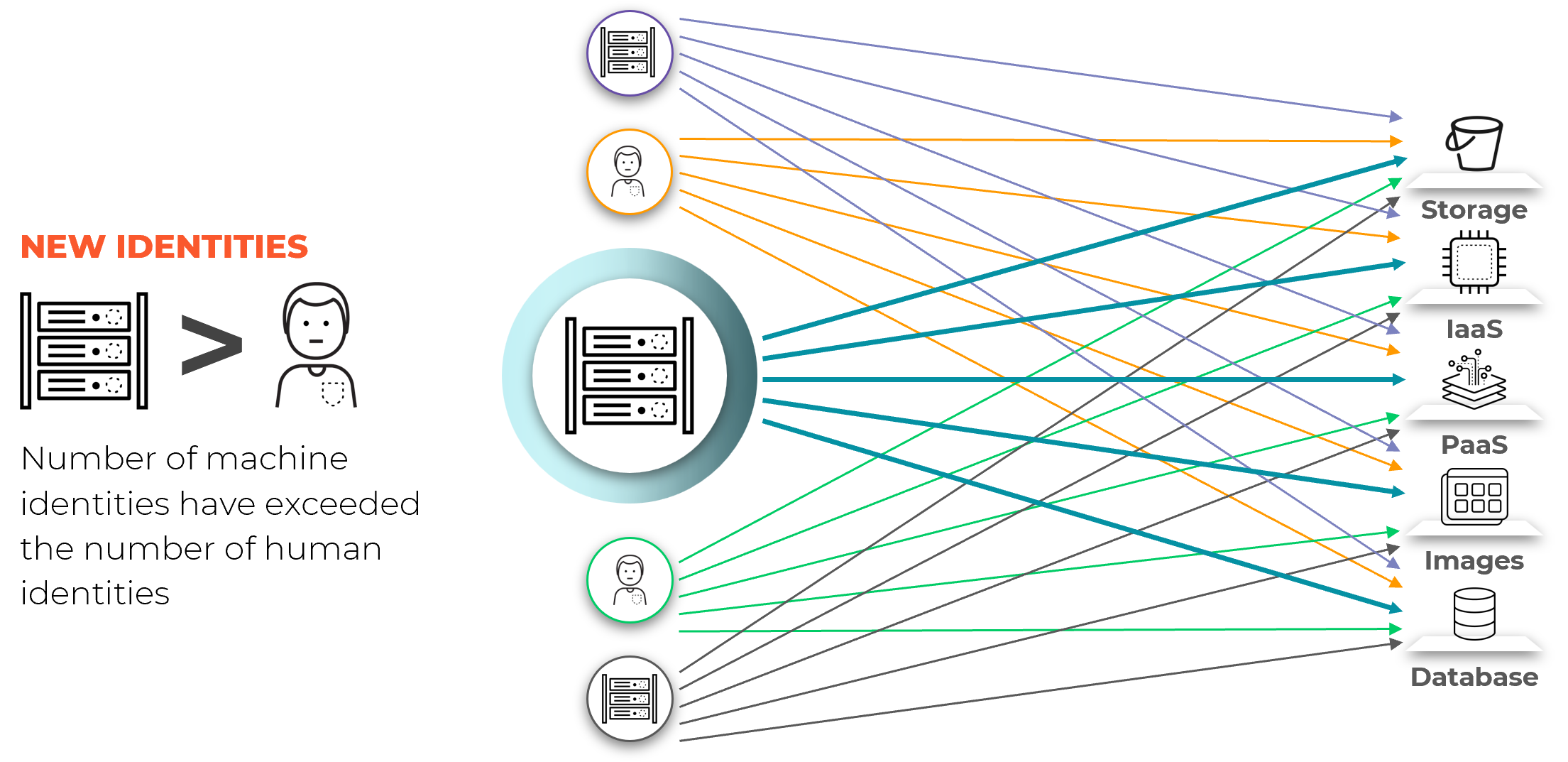
Figure 1: The number of identities in a cloud account multiplied by the number of entitlements each identity has makes for a massive attack surface.
The goal of the least privilege model is to reduce the amount of cloud entitlements an identity has to only the exact ones they need.
Why Is CIEM Important to Your Cloud Security Strategy?
Traditional identity and access management (IAM) tools deliver access controls to static self-hosted or on-premises infrastructure. As companies move to the cloud, the cloud infrastructure, services and applications they leverage become more ephemeral and dynamic than their on-premises environments.
Video: Using CIEM to manage permissions, identities, and entitlements within cloud environments.
Cloud service providers – Amazon Web Services (AWS), Microsoft Azure and Google Cloud – provide unique, native, cloud-based controls to help businesses enforce granular IAM policy.
According to Gartner, 81% of organizations report working with two or more public cloud providers. Because different cloud environments don’t natively integrate, companies employing a multicloud strategy can find managing entitlements for each cloud environment overwhelming. A CIEM solution helps cloud security teams understand access risk and manage all entitlements across multicloud environments.
The Managing Privileged Access in Cloud Infrastructure document provides guidance for security and risk management professionals on deploying tools that enable the effective management of cloud infrastructure entitlements. Together, the documents define the core meaning of CIEM and explain how security teams should use it to identify and prioritize access control risks across public clouds as well as other infrastructure resources.
What Are the Components of CIEM?
The main components of CIEM are entitlement visibility, rightsizing permissions, advanced analytics and compliance. The first step in managing entitlements and mitigating entitlement risks is to understand which entitlements exist within your environment. CIEM tools do this by automatically scanning access control policies, rules and configurations to determine:
- Which entitlements exist.
- What each human or machine user can do based on those entitlements.
- Which human and machine users can access each cloud resource based on those entitlements.
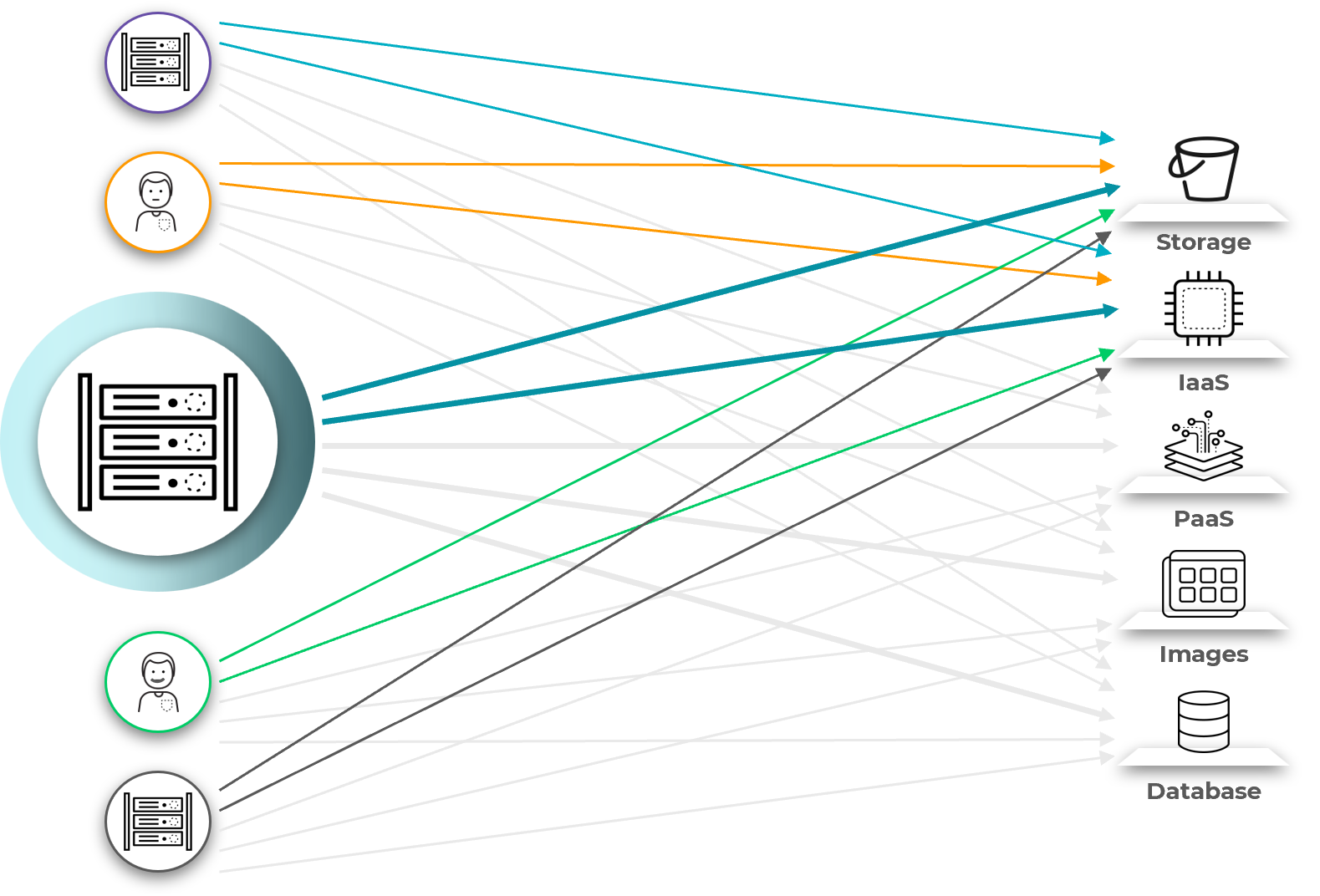
Figure 2: Using the least privilege model exponentially reduces the attack surface.
After identifying an entitlement, CIEM tools assess it to determine whether the access privileges it grants are the least necessary for achieving a workload’s intended purpose. If the entitlement provides too much access, CIEM tools alert administrators so they can address the problem manually. The tools can also adjust entitlements automatically, which allows teams to work efficiently in large-scale environments.
Rather than using generic rules and conditions, entitlement assessments performed by CIEM tools rely on advanced analytics powered by machine learning, along with user and entity behavior analytics (UEBA). While compliance is not the sole focus of CIEM, CIEM tools can align entitlements with compliance requirements by automatically assessing whether entitlements conform with compliance needs. They can also detect instances of “drift” in which entitlements that were once compliant come out of compliance as a result of configuration changes. The end goal is to have a more secure platform for enforcing least-privileged access credentials across cloud resources and providers.
How Is CIEM Used?
CIEM allows organizations to leverage advanced techniques, such as machine learning, to recommend least privileges for a particular kind of work.
For example, a user might request SSH access to a production machine for verifying some configuration value or checking out an environment variable. The user can request temporary SSH key pair access to perform the work. The security team grants the user’s request and prompts them to use an SSO provider to acquire the keys. Once the user performs the required work, the resource access is revoked, and the user can’t access the machine with those keys again. The security team knows the effective permissions of each user at all times, and they can compare permissions with the minimal requirements for each type of task.
Had they used a more relaxed entitlement model, such as granting the unlimited use of the keys for an indefinite period of time, they would have created a much greater security risk. Granting more than the minimum entitlements required exposes the system to insider threats, the misuse of access keys, and other potentially malicious user activity.
How Does CIEM Improves Cloud Security?
Entitlements consist of effective permissions that are assigned to users, workloads and data via the cloud provider (IAM policies) to perform necessary tasks following the principle of least privilege. Without proper entitlement monitoring and security enforcement, permissions can be easily over-allocated to users or workloads.
Fortifying Cloud Security Posture
To achieve a stronger cloud security posture, you’ll need a solution like CIEM that gives you:
- Visibility into the net effective permissions to resources in your cloud accounts.
- Governance for monitoring excess and unused privileges.
- A responsive framework that automatically adjusts effective IAM permissions — and takes actions in case of misalignment.
Video: Learn how to how to enforce least-privilege permissions with a better understanding of CIEM functions and benefits
Key Security Benefits of CIEM
The main benefits of cloud infrastructure entitlement management are summarized below:
- Multicloud visibility into entitlements: Gain a complete view of identities, net effective cloud permissions, policies and access risks across multicloud environments.
- Improved identity and access management: According to Gartner, more than 95% of accounts in IaaS use less than 3% of the entitlements they are granted. Many companies have inactive identities from former employees or proof-of-concept labs. CIEM solutions continuously monitor access activity to identify outdated identities and rightsize the net effective permissions.
- Automatic detection and remediation: CIEM calculates the baseline activity and can detect events like account compromise, insider threats, stolen access keys and other potentially malicious user activities.
- Audit-ready: Monitoring and securing entitlements across your cloud platforms helps you adhere to compliance regulations and standards related to user permissions.
Discover CIEM | Prisma Cloud
Learn how you can enforce least-privilege permissions across workloads and clouds with Cloud Infrastructure Entitlement Management from Prisma Cloud.