- What Is a Workload?
- Agentless vs Agent-Based Security
- What is the Difference Between Web Application Firewall (WAF) and Next-Generation Firewall (NGFW)?
- What Is Layer 7?
-
What Is Web Application and API Protection?
-
What Is an API Gateway?
- API Gateway Explained
- API Gateways for Microservices Architectures
- What Is the API Gateway Pattern?
- Challenges of API Gateways Potential Response Time Increases
- Use Cases and API Gateway Benefits
- Service Mesh Vs. API Gateway
- API Gateway Vs. Load Balancer
- API Gateways Security and WAFs
- API Gateway Solutions
- Industry Practices and Standards
- API Gateway FAQs
What Is a Cloud Workload Protection Platform (CWPP)?
A cloud workload protection platform (CWPP) is a security solution engineered to address the unique requirements of protecting workloads in cloud environments. Workloads can be hosted on a range of infrastructures, from traditional virtual machines to modern containers and serverless functions, across public, private and hybrid clouds. Through various security controls, CWPPs preserve the integrity, confidentiality and availability of workloads.
The cloud workload protection platform will continue to play a critical role in cloud security, evolving alongside technological advancements and shifting security paradigms as the future of the cloud unfolds.
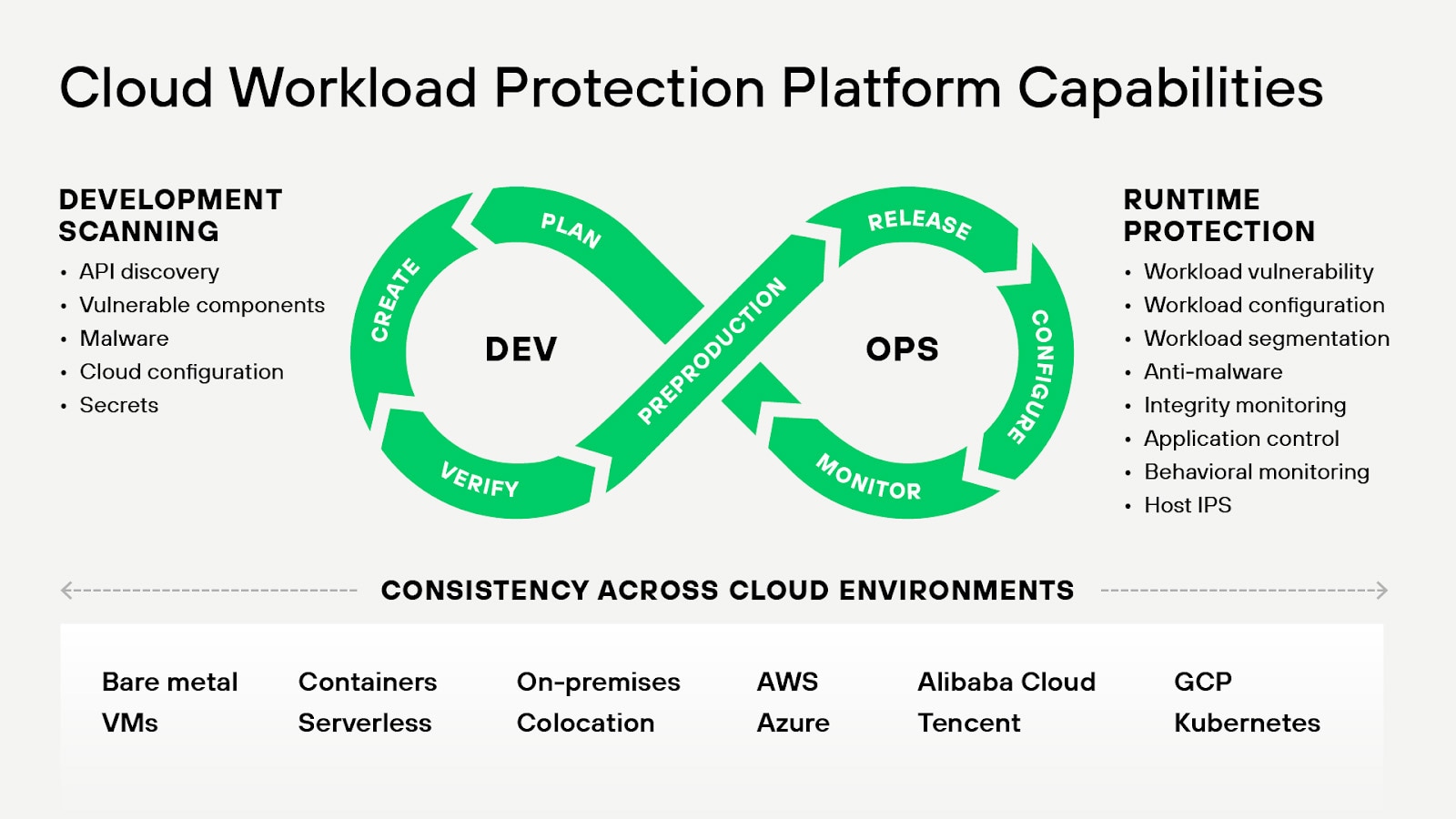
Figure 1: A workload-centric security solution that focuses on protecting workloads within modern environments, as Gartner defines a CWPP
Cloud Workload Protection Platform (CWPP) Explained
The cloud workload protection platform, or CWPP, is a solution developed to secure workloads. In cloud computing, workloads refer to the amount of processing that a cloud service has been contracted to handle. Workloads — applications, databases, batch jobs, user requests — can be hosted on various platforms, such as Amazon Web Services’ Elastic Compute Cloud (AWS EC2), Microsoft Azure’s Virtual Machines, or Google Cloud’s containerized applications.
But each of these workloads presents a potential attack vector for threat actors. In other words, every workload that performs a service, regardless of how briefly it’s operational, could be targeted for attack. Here’s where cloud workload protection platforms come in.
CWPPs provide security measures to protect workloads from threats, not just when they’re operational, but also during their transit stages — when they’re being moved, copied or modified, which can expose them to additional vulnerabilities.
CWPP provides comprehensive protection via a range of cloud workload security capabilities, including:
- Vulnerability management
- Host intrusion detection/prevention
- Compliance management
- Image analysis
- Runtime protection
- Behavioral monitoring of workload
CWPPs help security teams to ensure consistent security control across cloud environments and are also incorporated into continuous integration/continuous deployment (CI/CD) pipelines to enhance the security of DevOps practices.
Types of CWPP Solutions
CWPP solutions can be broadly categorized into two types:
1. Agent-based solutions require the installation of security agents on each workload. The agent communicates with the CWPP’s central management console, providing real-time information about the workload’s security state. Agent-based solutions are known for their deep visibility and control but can be more resource-intensive.
2. Agentless solutions don’t require the installation of security agents. Instead, they integrate with the cloud provider’s API or hypervisor to monitor workloads. Agentless solutions can be less resource-intensive and easier to deploy but may offer less visibility and control than agent-based solutions.
The Importance of a CWPP
Traditional security solutions can’t protect modern enterprises. The cloud workload protection platform emerged with the adoption of cloud services — and quickly became essential as the era of single-cloud deployments gave way to multicloud and hybrid cloud models.
Although these models provide enterprises with enumerable opportunities, they also usher in complexities and unique risks. Virtual machines (VMs), containers, serverless and other diverse workload types — alongside the varying configurations of public, private and hybrid clouds — heighten the dynamism and heterogeneity of cloud environments.
The CWPP brings much needed simplicity to the cloud ecosystem. It provides comprehensive visibility in a unified platform capable of securing diverse workloads. By implementing a CWPP that aligns with their needs, organizations can maximize the benefits of the cloud with confidence.
Key Features of a CWPP
A well-rounded CWPP brings a multitude of security components under one roof, providing an omnibus suite of integrated capabilities to secure cloud workloads.
Vulnerability Management
The CWPP supports continuous vulnerability assessment to identify and prioritize vulnerabilities in cloud workloads. Incorporating vulnerability databases like CVE (Common Vulnerabilities and Exposures), the CWPP applies threat intelligence to assess the risk posed by vulnerabilities. The platform also supports vulnerability remediation, either by providing patching tools or integrating with existing patch management solutions. The CWPP aids in prioritizing mitigation based on the severity of vulnerabilities, contextual risk factors with the workload, and the sensitivity of the data and services affected.
Configuration Management
The CWPP allows for configuration management, monitoring and enforcement of security best practices. It aligns with industry standards like CIS Benchmarks and provides automated compliance checks against these standards. The platform also offers remediation advice or automates the enforcement of secure configurations.
Compliance Management
Compliance management ensures that cloud workloads align with regulatory standards such as PCI DSS, HIPAA and GDPR. To help organizations maintain compliance, CWPPs provide automated monitoring and offer compliance-oriented security configurations. The platform also generates compliance reports detailing the compliance status of cloud workloads, as well as dashboards to visualize security posture and compliance status. In the event of a security incident, CWPPs help ensure a swift and compliant response, minimizing potential regulatory penalties.
Image Analysis
Image analysis involves scrutinizing container images for potential security issues and pulling those that possibly contain outdated, vulnerable packages or embedded malware before they enter the runtime environment. The CWPP also allows you to implement policies that define which registries, repositories and images you can trust. By using trusted images, organizations can ensure that application components only originate from authorized sources.
Consistency Across Cloud Environments
CWPPs ensure that security policies and controls are consistently applied across all cloud environments. This encompasses public clouds like Amazon Web Services, Google Cloud Platform and Microsoft Azure, as well as private clouds and on-premises infrastructure.
CI/CD Pipeline Integration
The CWPP integrates with existing security tools and processes — including SIEMs and SOAR platforms and DevOps tools. By integrating with CI/CD pipelines, the CWPP can provide security feedback early in the software development lifecycle and help facilitate shift-left security practices to catch and fix security issues before they make it to production. In doing so, it helps teams align with the principles of DevSecOps.
Runtime Protection
Runtime protection involves monitoring and protecting workloads as they run in the cloud computing environment, defending against attacks and unauthorized activities in real time. The CWPP commands runtime protection with robust threat detection capabilities, using techniques such as behavioral analysis, machine learning (ML) and signature-based detection. It integrates with cyber threat intelligence feeds for up-to-date threat detection. For response, the CWPP supports incident response automation, like automated quarantine or workload shutdown, and provides detailed forensics to investigate incidents.
Microsegmentation
Many CWPP's offer microsegmentation capabilities that allow developers and security teams to isolate workloads and limit lateral movement within the environment. This feature, when present, integrates seamlessly with native cloud networking and container networking solutions.
Web Application and API Security (WAAS)
Some CWPPs incorporate elements of web application and API security (WaaS), especially as they pertain to containerized and cloud-native applications. For instance, regarding API security, a CWPP may include functionalities to ensure secure communication between microservices in a microservices architecture, which is often implemented in cloud-native applications.
Web Application Firewall (WAF)
Some advanced CWPPs offer security features typically part of a web application firewall (WAF). WAFs protect against OWASP Top 10 security risks, such as injection, broken authentication and cross-site scripting (XSS) vulnerabilities.
It’s important to note that while CWPPs can have overlapping functionalities with WAFs and API Security solutions, they should complement and not replace these solutions.
Benefits of a CWPP
Essential for safeguarding cloud-hosted workloads, cloud workload protection platforms offer a multitude of benefits, significantly enhancing the security posture of the cloud network.
Granular Visibility
Providing granular visibility into workloads across cloud service providers (CSP), as well as private and hybrid cloud environments, CWPPs eliminate blind spots in the environment. Detailed insights into applications, databases and computing tasks allow for the prompt detection of anomalies and potential security threats. Enhanced visibility also enables security teams to maintain an updated inventory of workloads, while increasing their understanding and management of the attack surface.
Efficient Compliance
Compliance management is an area where CWPPs bring extraordinary value. The platform streamlines the compliance process, monitoring adherence to a myriad of regulations. Their automated compliance reporting capabilities not only save time but also provide auditable evidence of compliance and help enterprises avoid penalties and reputational damage that could result from compliance breaches.
Improved Security Posture
Through features like system hardening, microsegmentation and threat detection, CWPPs minimize the attack surface and restrict lateral movement of threats within the cloud environment. Vulnerability management capabilities identify potential weak points, providing remediation recommendations or patches to secure these vulnerabilities. In addition, CWPPs employ advanced technologies such as AI and ML to detect and proactively respond to threats to enhance the organization’s security resilience.
Scalability and Agility
As organizations grow, their cloud environments often need to scale, which introduces new workloads and possibly new vulnerabilities. CWPPs, with their scalable architectures, efficiently adapt to changes, providing protection regardless of the size or complexity of the environment. Their capacity to secure diverse workload types leaves organizations free to adopt VMs, containers, serverless, or on-prem servers to accommodate evolving needs.
Additionally, because CWPPs support DevOps practices, integrating with CI/CD pipelines and enabling shift left security, teams can accelerate the pace of software delivery without compromising security.
Reduced Complexity
Despite the intricacies of cloud security, CWPPs help to reduce the overall complexity for DevOps and security teams. By consolidating multiple security controls in a single platform, CWPPs eliminate the need to manage disparate security tools. Consolidation not only simplifies security management but also ensures a unified security strategy across all workloads.
Cloud Workload Protection Vs. Application Security
Both cloud workload protection and application security (AppSec) play crucial roles in cloud security. While they share the goal of protecting cloud-native assets, they do so from different angles and at different stages of the application lifecycle.
Cloud workload protection aims to secure workloads against threats that could lead to data breaches. It does this by homing in on the environment where the application runs (the workload), which includes securing the underlying infrastructure and monitoring runtime activities.
AppSec is a broader term that encompasses measures taken to improve the security of an application. It involves identifying, fixing and preventing security vulnerabilities within the application. While cloud workload protection focuses on the runtime environment of workloads, AppSec focuses on the application code, its dependencies and the way it interacts with users and systems.
Application security includes practices such as static application security testing (SAST), dynamic application security testing (DAST), software composition analysis (SCA), and interactive application security testing (IAST). AppSec also enters the development process with security requirements definition, threat modeling, secure coding practices and security testing.
Security for the Stage of the Software Lifecycle
Cloud workload protection is primarily concerned with the deployment and operation stages, while AppSec starts from the early stages of software development and continues through deployment and operation. Starting with application code, often referred to as shifting security left, can’t be understated in terms of importance to the resilience of the software development lifecycle.
Teams that understand the differences between cloud workload protection and AppSec can help their organizations to implement a more comprehensive and effective cloud security strategy. It’s not a matter of choosing one over the other but understanding how they complement each other.
CWPPs and the Cloud-Native Application Protection Platform
The cloud workload protection platform and the cloud-native application protection platform (CNAPP) are two security solutions designed to protect cloud-based workloads. The CNAPP, however, is a broader security solution that comprises several security modules, one being the CWPP.
In other words, when you have a CNAPP, you also have a CWPP. In addition to integrating the complete functionality of the cloud workload protection platform, CNAPPs provide comprehensive code-to-cloud security by seamlessly integrating the full functionality of:
- Code Security
- Cloud Security Posture Management (CSPM)
- Web Application & API Security (WAAS)
- Cloud Infrastructure Entitlement Management (CIEM)
- Cloud Network Security (CNS)
The result of true integration within the CNAPP is end-to-end visibility and control. Though some organizations begin their cloud journey with the CWPP or CSPM, only the CNAPP addresses the spectrum of security issues, providing a robust, layered defense to secure cloud-native applications from development through runtime.
CWPP Considerations for Security Leaders
Security leaders should take several key considerations into account when contemplating the implementation of a cloud workload protection platform.
Coverage
Does the CWPP solution support all the types of cloud infrastructures the organization uses — including virtual machines, containers and serverless functions, across private and public clouds?
Compatibility
Is the CWPP compatible with your existing tech stack? It should be able to integrate seamlessly with your cloud service providers, container orchestrators and existing security tools and processes, such as CI/CD pipelines and ITSM tools.
Automation
Will the platform support the growth of your organization? As the scale and dynamism of cloud environments can overwhelm manual security processes, the CWPP solution should support automation, equipping your teams to respond quickly and effectively to security incidents.
Regulatory Compliance
Does the CWPP solution help ensure compliance with regulatory standards and internal policies? The cloud workload protection platform you choose should help your organization meet its regulatory compliance requirements. This includes features to support compliance reporting and the enforcement of compliance-related controls.
Usability
How steep is the learning curve? You’ll want the platform to be user-friendly, with intuitive interfaces and workflows. A user-friendly platform will accelerate adoption and minimize the extent of staff training needed to gain proficiency.
Vendor Reputation and Stability
Is the vendor a recognized leader in the field of cloud security? Is their platform and solutions portfolio well regarded by peers and analysts? The vendor you choose should have a proven track record and a stable financial position to ensure the ability to provide continued platform development and support in the future.
Vendor Support
What type of support can you expect from the vendor? In addition to the vendor’s reputation, inquire about the quality of their customer support. As the threat landscape evolves, they should provide routine updates to the platform to address emerging threats and vulnerabilities. They should also offer robust support to assist with implementation, troubleshooting and other issues.
Deploying a CWPP
The deployment of a CWPP involves several steps:
- Planning: Develop a deployment plan, considering factors such as the order of workload protection, rollback procedures and potential downtime.
- Testing: Before full deployment, conduct a pilot test to identify potential issues and assess the CWPP’s effectiveness.
- Deployment: Deploy the CWPP according to your plan, ensuring all workloads are protected and the platform is correctly configured.
- Monitoring and Adjusting: After deployment, continuously monitor the CWPP’s performance and adjust as necessary to ensure optimal protection.
