- What Is Cloud Native?
- What Is Threat Modeling?
- What Is CNAPP?
- CSP-Built Security Vs. Cloud-Agnostic Security
- What Are Microservices?
- What Is Cloud-Native Security?
- What Is CSPM? | Cloud Security Posture Management Explained
- What Is Cloud Network Security?
- What Is Microsegmentation?
-
Core Tenets of a Cloud Native Security Platform (CNSP)
- What Is a Cloud Native Security Platform?
- CSPM Tools: How to Evaluate and Select the Best Option
- What is Platform as a Service (PaaS)?
What Is Serverless Security?
Serverless refers to a cloud-native development model in cloud computing that allows developers to build and run applications and services without needing to manage infrastructure, or server-side IT. Applications in the serverless model rely on a combination of managed cloud services and functions as a service (FaaS) that abstract away the need to manage, patch, and secure infrastructure and virtual machines.
Benefits of Serverless Architecture
By 2020, 40% of organizations said they had fully adopted serverless architecture, according to O’Reilly. In the years since, serverless has become a dominant application execution environment. The State of Cloud Native Security Report 2023 shows further growth on the horizon, as 70% of survey respondents reported planned use increases in the next 24 months.
Adopting a serverless model benefits application development in several ways:
- Reduced operational overhead: With no servers to manage, developers and DevOps don’t need to worry about scaling infrastructure, installing and maintaining agents, or other infrastructure-related operations.
- Increased agility: Since serverless applications rely heavily on managed services for things like databases and authentication, developers are free to focus on the actual business logic of the application, which will typically run on a FaaS, such as AWS® Lambda or Google Cloud Functions.
- Reduced costs: With most services used in serverless applications, the customer only pays for usage. For example, with AWS Lambda, customers pay for the executions of their functions. This typically has a significant impact on cost, as they don’t have to pay for unused capacity like they would with virtual machines.
Figure 1: Components of the severless model
Serverless Applications Require Serverless Security
With every major advancement in software development and IT operations comes a shift in attack vectors and security risks. In the early days of virtualization to containers, security professionals had to adapt and find new ways of hardening, defending and governing their infrastructure. The concept of a serverless application presents one of the biggest paradigm shifts ever seen when it comes to application security.
Traditionally, organizations would protect their applications by relying on infrastructure and network-based tools. They would inspect traffic with a firewall, try to detect malicious activity with an intrusion detection system, or protect applications with runtime application self-protection, or RASP, technology. Even with containers, organizations could still rely on the security of the underlying infrastructure to a certain degree.
A serverless application consists of distributed cloud services working together, such as an S3 bucket that triggers a Lambda Function, which in turn triggers DynamoDB®. In this architecture, there’s no room for firewalls, IDS/IPS tools, or any kind of instrumentation agents or server-based protection methods. Instead of focusing on network inspection and access control lists, the serverless model shifts the focus of security to IAM permissions, behavioral protection and strong code.
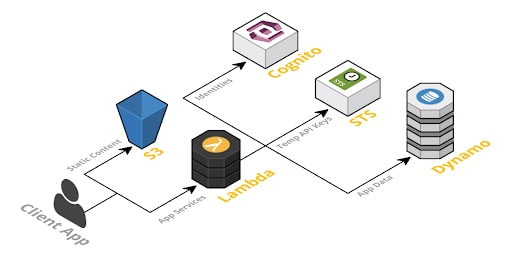
Figure 2: Application in severless model
Serverless Attack Vectors
Adopting serverless security gives applications a strong headstart from a security perspective since organizations no longer have to worry about infrastructure, network or host security. However, new attack vectors have emerged, and familiar attacks have been reimagined for serverless environments. Let’s take a look at one example (for the full list, refer to the Cloud Security Alliance’s Top 12 Risks for Serverless Applications):
Event Data Injection
Injection flaws in applications, among the most common risks to date, have been thoroughly covered in many secure coding best practice guides. At a high level, injection flaws occur when untrusted input is passed directly to an interpreter before being executed or evaluated. In the context of serverless architecture, though, function event-data injections are not strictly limited to direct user input (such as input from a web API call). Most serverless architectures provide a multitude of event sources that can trigger the execution of a serverless function.
Event data injection source examples include:
- Cloud storage events (e.g., AWS S3®, Azure Blob Storage, Google Cloud Storage)
- NoSQL database events (e.g., AWS DynamoDB, Azure Cosmos DB®)
- SQL database events
- Stream processing events (e.g., Amazon Kinesis®)
- Code changes and new repository code commits
- HTTP API calls
Each event input might include different message formats, and various parts of these event messages can contain attacker-controlled or otherwise dangerous inputs. The rich set of event sources increases the potential attack surface and introduces complexities when attempting to protect serverless functions against event-data injections. This is especially true because serverless architectures aren’t as well understood as web environments where developers know which message parts shouldn’t be trusted (e.g., GET/POST parameters, HTTP headers, etc.).
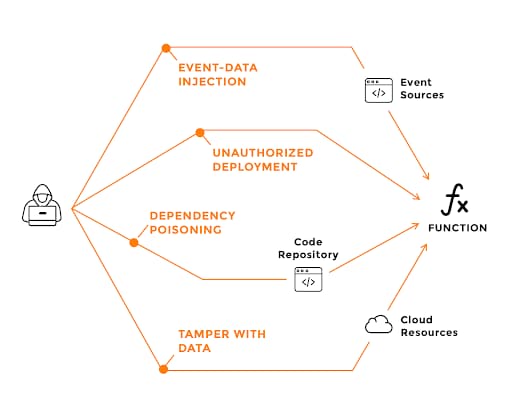
Figure 3: Event data injection attack surface
Protecting Serverless Applications
Effective serverless security focuses on ensuring code integrity, tight permissions and behavioral analysis.
- Access and permissions: Maintain least-privileged access for serverless functions and other services. For example, if an AWS Lambda function needs to access a DynamoDB table, make sure it can only perform the specific action the business logic requires.
- Vulnerability scanning: Ensure code and infrastructure-as-code template integrity by regularly scanning for vulnerable third-party dependencies, configuration errors, and over-permissive roles.
- Runtime protection: Use runtime protection to detect malicious event inputs and anomalous function behavior, and limit as necessary each function’s ability to access files, hosts, the internet and spawn child processes.
Serverless FAQs
Q: What is serverless computing?
A: Serverless computing, also known as serverless architecture, is an approach to software design that allows engineers to build and run applications without having to manage the underlying infrastructure. Instead, cloud providers provision servers to run applications, databases, and storage systems for digital or cloud-native organizations.
Q: What is function as a service (FaaS)?
A: Function-as-a-Service, is a cloud-computing service that allows customers to execute code in response to events, without managing the complex…
Q: What is serverless architecture?
A: Serverless architecture is a FaaS that involves developers writing application code as sets of unique functions designed to perform specific tasks in response to HTTP requests or similar events. Once functions are deployed to the cloud provider account, the cloud provider executes the function on a server provided by the cloud provider.
Q: What are examples of serverless computing services?
A: Examples of serverless services offered by cloud providers include Google Cloud Functions, AWS Lambda, and Microsoft Azure Functions.