- What Is CI/CD Security?
- What Is the CI/CD Pipeline?
- What Is Insecure System Configuration?
- What Is Shift Left Security?
- What Is DevOps?
-
What Is Cloud Software Supply Chain Security?
- What is DevSecOps?
-
What Is Insufficient Flow Control Mechanisms?
- CICD-SEC-1: Insufficient Flow Control Mechanisms Explained
- Importance of Robust Flow Control Mechanisms in CI/CD
- Preventing Insufficiency in Flow Control Mechanisms
- Best Practices to Ensure Sufficient Flow Control in CI/CD
- The Impact of New Technologies on Flow Control
- Insufficient Flow Control Mechanisms FAQs
- What Is Poisoned Pipeline Execution (PPE)?
- What Is Ungoverned Usage of Third-Party Services?
- What Is Insufficient Pipeline-Based Access Controls?
- What Is Insufficient Logging and Visibility?
- What Is Insufficient Credential Hygiene?
- What Is Inadequate Identity and Access Management?
- What Is Improper Artifact Integrity Validation?
- What Is Dependency Chain Abuse?
-
Anatomy of a Cloud Supply Pipeline Attack
What Is Executive Order 14028?
Executive Order 14028, "Improving the Nation's Cybersecurity," issued on May 12, 2021, by President Joe Biden, is a sweeping directive designed to fortify the United States' cybersecurity framework. Its implementation is an ongoing process, as EO 14028 requires collaboration among multiple stakeholders and federal agencies, setting deadlines for specific actions and reports. As a result, while the EO has been signed and initiated, the full implementation of its provisions is still underway.
The order recognizes the growing threats posed by cyber adversaries to public and private sectors. EO 14028 takes steps to modernize federal cybersecurity, enhance software supply chain security, establish a cybersecurity review board, improve incident detection and response, standardize federal response protocols, and strengthen the cybersecurity workforce.
What's the Purpose of EO 14028?
The purpose of Executive Order 14028, "Improving the Nation's Cybersecurity," is to strengthen the United States' cybersecurity posture by addressing the increasing cyberthreats and attacks targeting both public and private sectors.
EO 14028 aims to prioritize prevention, detection, assessment, and remediation of cyber incidents, ultimately safeguarding national and economic security. Key initiatives outlined in the order include modernizing federal government cybersecurity, enhancing software supply chain security, establishing a cybersecurity review board, improving incident detection and response, standardizing federal response protocols, and strengthening the cybersecurity workforce.
Modernizing Federal Government Cybersecurity
The order directs federal agencies to adopt best practices like Zero Trust architecture and multifactor authentication and to migrate to secure cloud services.
Modernizing federal government cybersecurity in EO 14028 refers to the directive for federal agencies to adopt advanced security practices and technologies to bolster their defenses against cyberthreats. This modernization process includes implementing Zero Trust architecture, which assumes no implicit trust within networks and requires continuous verification of users, devices, and resources.
Additionally, agencies are expected to employ multifactor authentication to enhance access control, as well as migrate to secure cloud services, which offer improved scalability and security features. By embracing these modern cybersecurity measures, federal agencies aim to mitigate risks, protect sensitive data, and strengthen the overall security posture of the U.S. government's digital infrastructure.
Enhancing Software Supply Chain Security
The intention of enhancing software supply chain security in EO 14028 involves establishing guidelines and standards for software development and cybersecurity practices. The initiative is designed to increase transparency about the origins and composition of software components to ensure that potential security issues can be tracked and effectively addressed.
By implementing rigorous security practices throughout the software supply chain, including secure coding, vulnerability management, and patch management, the federal government seeks to minimize risks associated with third-party software and software components.
Establishing a Cybersecurity Safety Review Board
The board will review significant cybersecurity incidents and provide recommendations to improve the nation's cybersecurity posture.
The Cybersecurity Safety Review Board will be established under EO 14028 to analyze significant cybersecurity incidents and provide recommendations to improve the nation's cybersecurity posture. Comprising representatives from public and private sectors, this board aims to facilitate collaboration, knowledge sharing, and best practice implementation.
By conducting thorough reviews of major cyber incidents, the board can identify patterns, vulnerabilities, and systemic issues that require attention. The insights gained from these reviews will help inform policy, in addition to enhancing security measures and better prepare the nation to defend against cyberthreats.
Improving Detection and Response to Cyber Incidents
Federal agencies are directed to implement endpoint detection and response (EDR) solutions and share information about incidents with the Cybersecurity and Infrastructure Security Agency (CISA).
Improving detection and response to cyber incidents in EO 14028 refers to the enhancement of federal agencies' capabilities to identify, analyze, and remediate cyberthreats in a timely and effective manner. To achieve this goal, agencies are directed to implement EDR solutions, which provide real-time monitoring and analysis of potential threats at the device level.
What’s more, federal agencies are required to share information about incidents with the CISA to facilitate cross-agency collaboration and improve collective defense. By strengthening detection and response capabilities, EO 14028 aims to minimize the impact of cyber incidents on national and economic security.
Standardizing the Federal Government's Incident Response Playbook
Standardizing federal response protocols in EO 14028 involves creating a set of unified procedures for federal agencies to follow in the event of a cyber incident. The purpose of standardization is to ensure a consistent, effective, and coordinated approach to managing cyberthreats across the government.
The intent of establishing a common playbook is to enable agencies to streamline their response efforts, reduce confusion, and minimize the potential impact of cyber incidents. Standardized protocols also promote information sharing and collaboration between agencies, facilitating a more cohesive and resilient cybersecurity posture for the nation.
Strengthening the Cybersecurity Workforce
EO 14028 addresses the need to strengthen the cybersecurity workforce by expanding and improving the pool of skilled cybersecurity professionals. The order emphasizes the importance of education, training, and workforce development initiatives to cultivate a talent pipeline and equip professionals with the skills required to protect the nation's critical infrastructure.
By fostering partnerships between academia, the private sector, and government, EO 14028 seeks to create a sustainable workforce development strategy that addresses the demand for cybersecurity expertise, ensuring the U.S. is prepared to face cyberthreats.
The initial timeline for implementing EO14028 is as follows:
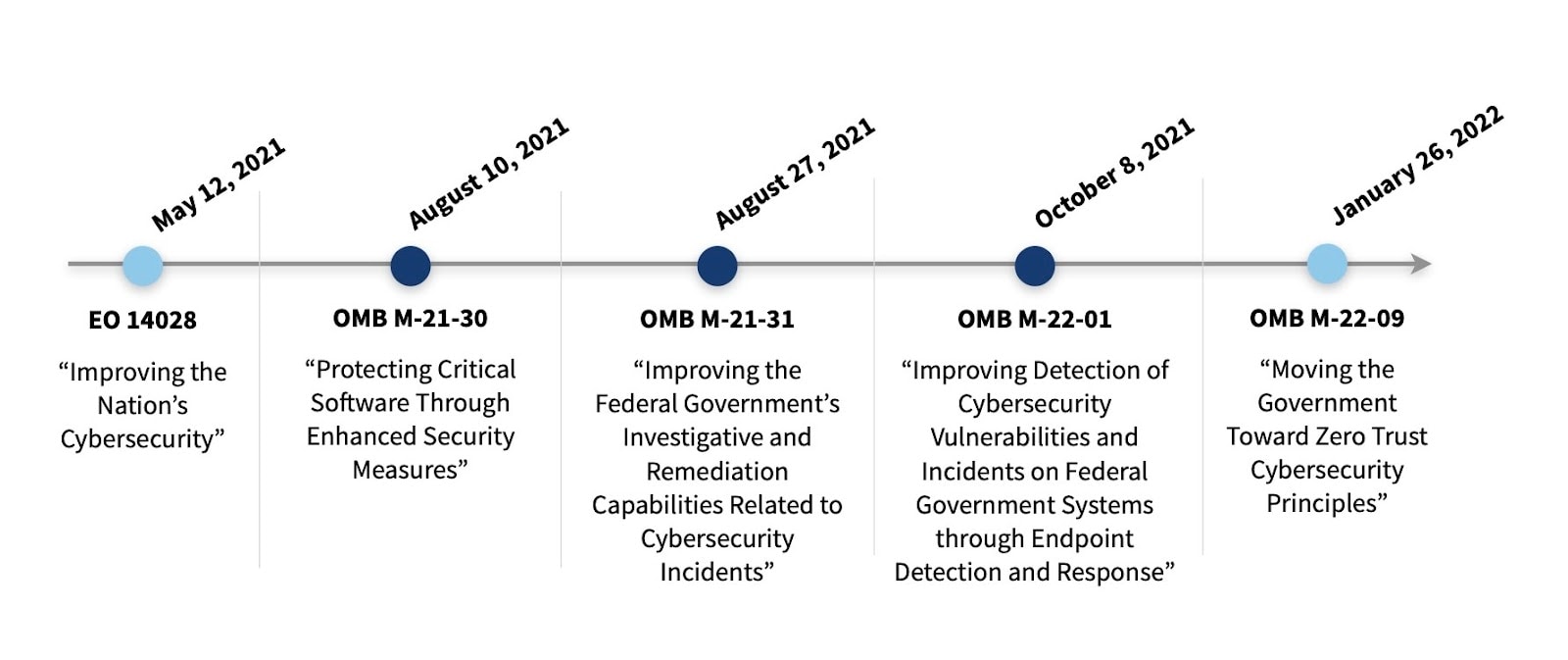
Source: GSA.gov
NIST's Responsibilities Under Executive Order 14028
Under Executive Order 14028 the National Institute of Standards and Technology (NIST) has several critical responsibilities, all of which center on enhancing software supply chain security and establishing guidelines for federal agencies.
Develop Guidelines for Secure Software Development
NIST is tasked with creating guidelines for secure software development practices. These guidelines are meant to ensure that software products used by the federal government are developed securely and minimize vulnerabilities. They will cover areas such as risk management, access control, secure coding, vulnerability management, patch management, and provide for transparency about the composition of software products and cover.
Create a Software Bill of Materials (SBOM)
NIST is responsible for defining the elements to be included in a software bill of materials (SBOM), which is a comprehensive inventory of software components, their sources, and dependencies. The SBOM aims to provide transparency about the origin of software elements and to ensure that potential vulnerabilities can be tracked and addressed effectively.
Develop Guidelines for Software Supply Chain Security
NIST will work on developing guidelines that outline the minimum requirements for software supply chain security. These guidelines will address areas such as the secure handling of software artifacts, the use of automation in building and deploying software, and the verification of the integrity of software components throughout the supply chain.
Establish Performance Goals for Critical Software
NIST is tasked with developing performance goals, measures, and indicators for evaluating the security of critical software used by federal agencies. These performance goals will help agencies assess the security of the software they use and make informed decisions about procurement and risk management.
Collaborate with Other Agencies
To ensure that its guidelines and standards are effectively implemented across the federal government, NIST works closely with federal agencies. These include the Office of Management and Budget (OMB), the Department of Homeland Security (DHS), and CISA.
A Platform Approach to Securing Software Development
Security teams often experience fatigue trying to keep up with the rapid pace of application production. Although security measures may seem to hinder the software development process, integrating security earlier in the software development lifecycle can prevent issues that might slow down a product later in development. Early integration of security also facilitates communication among development, operations, and security teams, reducing the friction that often serves as the primary cause of development slowdowns and decreased application velocity.
The biggest benefit of a platform approach securing software development within national defense systems is that it helps agencies improve efficiency by connecting insights across the application lifecycle to prioritize and fix risks. Only through a platform approach can you combine multiple risk factors across an applications lifecycle to visualize interconnected risks and prioritize alerts, helping security teams understand how several factors can form attack paths.
Tracing Vulnerabilities Through SBOMs
An SBOM is a comprehensive inventory of all components, dependencies, and related metadata within a software product. It serves as a detailed record of the software's composition, including open-source libraries, third-party dependencies, frameworks, and proprietary code. An SBOM typically contains information such as component names, version numbers, and licensing information. By providing transparency into a software product's composition, SBOMs help organizations identify, track, and manage potential vulnerabilities, thereby enhancing software supply chain security and facilitating compliance with industry standards and regulations.
Tracing vulnerabilities through a software bill of materials involves generating comprehensive records of software components, maintaining a centralized repository, and cross-referencing with vulnerability databases. Organizations must prioritize risks, develop remediation strategies, and continuously monitor and update SBOMs to ensure software security. Engaging with vendors and suppliers, as well as investing in training and awareness programs, further supports a secure software supply chain and fosters a culture of security vigilance within the organization.
Improving Software Supply Chain Security
Supply chain risk management (SCRM) involves systematically identifying, assessing, and mitigating risks within a supply chain to safeguard operations, finances, and reputation. It includes risk identification, assessment, mitigation, monitoring, collaboration, compliance management, and leveraging technology.
Securing a CI/CD pipeline begins with obtaining a comprehensive inventory of languages, frameworks, and executables in its ecosystem. Cloud attacks often target these pipelines, exposing organizations to code injection, credential theft, and intellectual property theft. New security practices are essential.
To enhance software supply chain security, identify missing branch protection rules, insecure pipeline configurations, and potential for poisoned pipelines proactively. Implement critical security guardrails to strengthen delivery pipelines over time, preventing bad actors from exploiting weaknesses.
Additionally, identify exposed credentials in pipelines, such as cleartext credentials in webhooks and logs, to prevent theft and abuse. Adopting SCRM strategies helps organizations enhance supply chain resilience, maintain business continuity, and ensure compliance with relevant laws and standards.
Federal EO 14028 FAQs
NIST is a nonregulatory agency within the U.S. Department of Commerce, responsible for developing and promoting measurement, standards, and technology to enhance productivity, facilitate trade, and improve the quality of life. NIST conducts research in various fields, including information technology, cybersecurity, and physical sciences.
In the realm of cybersecurity, NIST is known for its development of the NIST Cybersecurity Framework, which provides guidelines and best practices for organizations to manage and reduce cybersecurity risk. Additionally, NIST publishes a wide range of documents, such as the NIST Special Publication (SP) series, that offer in-depth guidance on aspects of information security, privacy, and risk management.
NIST guidelines cover a range of cybersecurity and information security topics. Areas include:
- Risk management: NIST provides guidance on identifying, assessing, and managing risks, as well as creating risk management frameworks and processes for organizations.
- Access control: NIST guidelines cover best practices for controlling and managing access to information systems and resources, including authentication and authorization mechanisms.
- Incident response: NIST offers guidance on creating and maintaining incident response plans, as well as effectively handling and recovering from security incidents. Security awareness and training: NIST provides recommendations for developing and implementing security awareness and training programs to educate employees about cybersecurity threats and best practices.
- Encryption and cryptography: NIST standards include guidelines for encryption algorithms, key management, and cryptographic protocols to ensure secure communication and storage of sensitive data.
- Configuration management: NIST guidelines address the secure configuration of information systems, including setting baseline security configurations and monitoring for unauthorized changes.
- Security assessment and testing: NIST provides guidance on conducting security assessments and testing of information systems to identify and remediate vulnerabilities.
- Privacy: NIST addresses privacy considerations and best practices for protecting personal information within information systems.
- Business continuity and disaster recovery: NIST offers guidance on developing business continuity and disaster recovery plans to ensure the resilience of information systems and operations in the event of disruptions or disasters.
- Cloud computing: NIST guidelines cover security and privacy considerations for organizations adopting cloud services, including recommendations for selecting and implementing secure cloud solutions.
Executive Order 14028 will be enforced by various U.S. government agencies and departments, including:
- Office of Management and Budget (OMB)
- Department of Homeland Security (DHS)
- National Institute of Standards and Technology (NIST)
- Department of Defense (DoD)
- Department of Justice (DOJ)
- Federal Acquisition Regulatory Council.
These entities will collaborate with each other and with private sector organizations and critical infrastructure owners to implement the provisions of the order.
Security posture refers to the overall effectiveness of an organization's cybersecurity measures in protecting its information systems, networks, and data from threats. It encompasses the organization's ability to identify, prevent, respond to, and recover from cyberattacks and incidents.
A strong security posture is achieved through a combination of technical controls, well-defined policies, comprehensive security awareness and training, and proactive risk management strategies.