What is Cortex XSIAM? AI-Driven Platform
Extended security intelligence and automation management, or XSIAM, is a new approach to security operations that drives dramatically better security outcomes by closely integrating and automating the capabilities and processes of a modern security operations center (SOC).
Cortex XSIAM: AI-Driven Security Platform
XSIAM is designed to be the center of SOC activity, replacing SIEM and specialty products by unifying broad functionality into a holistic solution. XSIAM capabilities include data centralization, intelligent stitching, analytics-based detection, incident management, threat intelligence, automation, attack surface management, and more – all delivered within an intuitive, task-oriented user experience.
XSIAM maintains your security posture, building upon the proven threat detection and response capabilities of XDR. With a centralized data store and unified SOC functions, XSIAM provides a clear migration path away from traditional security information and event management (SIEM) solutions.
Deep dive into Security Information and Event Management by reading our article, “What Is SIEM?”.
First introduced by Palo Alto Networks in 2022, XSIAM is a novel category that's designed to deliver the autonomous security platform of the future.
Why Do I Need XSIAM Security?
The present demands of Security Operations Centers (SOCs) have shifted, yet the structure of Security Information and Event Management (SIEM) and SOCs has remained stagnant.
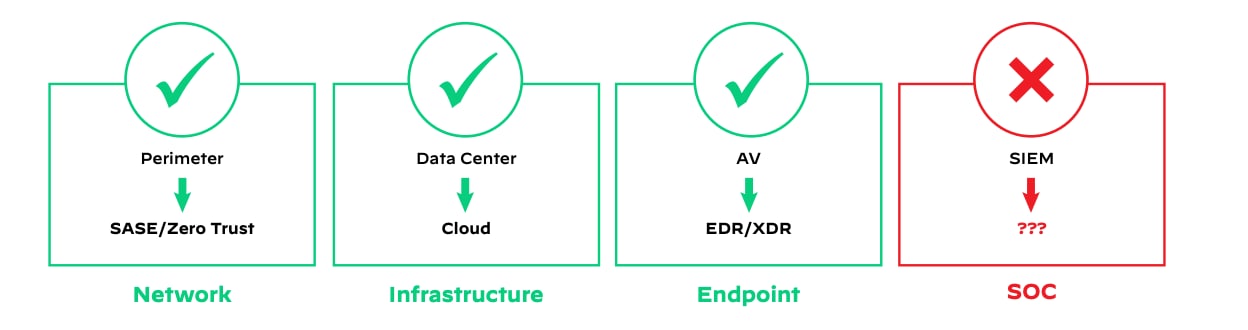
While other vital components of security systems have undergone modernization - such as endpoints transitioning from antivirus to endpoint detection and response (EDR) and extended detection and response (XDR); networks moving from traditional "hard shell" perimeters to Zero Trust and secure access service edge (SASE); and runtime relocating from data centers to the cloud - SOCs continue to operate on a SIEM model conceived two decades ago.
As adversaries automate attacks against infrastructures defended by poorly integrated security products, security operations teams are required to respond faster than ever. Meanwhile the ephemeral nature of container workloads and continuous integration/continuous deployment (CI/CD) environments has challenged security teams to maintain their security posture from moment to moment.
A byproduct of this is the growth of managed services offerings to scalably deliver additional resources in defense of the organization, but even with this added expense, many organizations feel overwhelmed.
An important shift for defenders in respect to these challenges over the past decade has been the evolution of endpoint detection and response (EDR) and extended detection and response (XDR) solutions to provide improved threat detection and response capabilities through improved security analytics and visibility into environments.
While many organizations are benefiting from these capabilities today, many other organizations are still using a SIEM for centralizing log data and aggregating additional logs that are frequently used for security and compliance use cases. Unfortunately, SIEMs often depend on manual configuration of log ingest and detection rules, as well as triage and remediation of alerts.
XSIAM seeks to alleviate the reliance on manual processes by productizing these processes and integrating them to deliver near-real-time security operations outcomes.
How Does XSIAM Work?
XSIAM is unique in the way it operates, using intelligent automation to break from the analyst-driven model of today’s security products. The system continually collects deep telemetry, alerts and events from any source. It then automatically prepares and enriches the data, uniquely stitches it into security intelligence and immediately applies machine learning detection analytics.
Alerts are grouped to incidents, fully enriched with relevant context. Routine incidents are recognized, handled and closed. Dashboards bring together all relevant aspects of affected users, assets and infrastructure. Embedded automation and inline playbooks speed actions, self-learning over time. In every respect, XSIAM helps minimize analyst tasks so they can focus only on activities the system cannot perform itself.
Key Integrated Capabilities of Cortex XSIAM
Cortex XSIAM combines these key SOC product capabilities into a single unified platform:
- Security Information and Event Management (SIEM) Delivers all common SIEM functions, including log management, correlation and alerting, reporting, and long-term data retention.
- Threat Intelligence Platform (TIP) Aggregates, scores, and distributes threat intelligence data, including the industry-leading Unit 42® threat feed, to third-party tools and enriches alerts for context and attribution.
- Extended Detection and Response (XDR) Gathers telemetry from any source for unrivaled detection coverage and accuracy, with the highest number of technique-level detections in the 2022 MITRE ATT&CK evaluations.
- Endpoint Protection Platform (EPP) Prevents endpoint attacks with a proven endpoint agent that blocks exploits, malware, and fileless attacks and collects full telemetry for detection and response.
- Attack Surface Management (ASM) Provides embedded attack surface management (ASM) capabilities for an attacker’s view of your organization, with asset discovery, vulnerability assessment, and risk management.
- Identity Threat Detection and Response (ITDR) Uses machine learning and behavioral analysis to profile users and entities and alert on behaviors that may indicate a compromised account or malicious insider.
- Security Orchestration, Automation, and Response (SOAR) Automates nearly any use case with hundreds of built-in playbooks and offers customization with a visual drag-and-drop playbook editor.
- Cloud Detection and Response (CDR) Analyzes cloud audit, flow, and container host logs together with data from other sources for holistic detection and response across your hybrid enterprise.
- Management, Reporting, and Compliance Simplifies operations, centralizing all configuration, monitoring, and reporting functions, including endpoint policy management, orchestration, and response.
Cortex XSIAM | The Platform for the Modern SOC
Cortex XSIAM helps the modern SOC evolve from a reactive and human-first approach – that cannot scale to keep up with ever-increasing threats—toward the vision of an AI-driven, autonomous SOC. XSIAM embeds automation and analytics wherever possible to reduce SOC costs and make SecOps processes self-sustainable.
Cortex® XSIAM™ will transform SecOps by enabling organizations to benefit in the following ways:
Simplify Security Operations with a Converged Platform - Bring all of your data and SOC capabilities into one platform. The convergence of SOC capabilities, such as XDR, SOAR, ASM and SIEM, into a single platform eliminates console switching and streamlines security operations.
Stop Threats at Scale with AI-Driven Outcomes - Out-of-the-box AI models go beyond traditional detection methods, connecting events across various data sources to accurately detect and stop threats at scale.
Accelerate Incident Remediation with an Automation-First Approach - Take actions automatically before your analyst even has to look at the incident. Automate security tasks to reduce manual work and accelerate incident response and remediation.
When we say AI-driven, we mean it just works, and does so in real time.
Cortex XSIAM FAQs
Stop breaches with dramatically better security:
- Builds an Intelligent Data Foundation. Cortex XSIAM lets you turn widespread telemetry into an intelligent data foundation ready to power advanced analytics while allowing you to utilize data at half the cost of legacy solutions.
- Accelerates Response. Cortex XSIAM leverages the data foundation to detect new adversary tactics with self-learning cloud-delivered AI and natively automates key steps of incident investigations.
- Outpaces Threats. Cortex XSIAM continuously discovers vulnerabilities through native attack surface management and integrated threat intelligence.